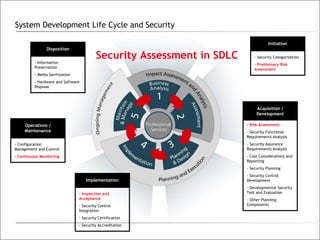
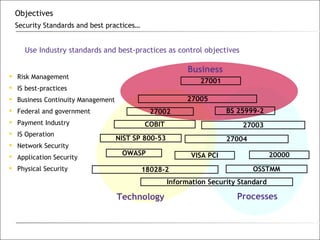
1. The document discusses the objectives, methodologies, and phases of performing an information systems audit.
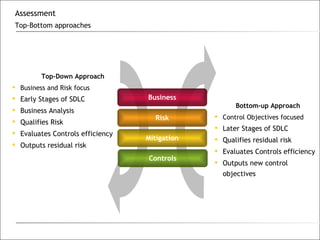
2. Key methodologies discussed include the top-down and bottom-up approaches, with the top-down being business and risk focused and the bottom-up focusing on control objectives.
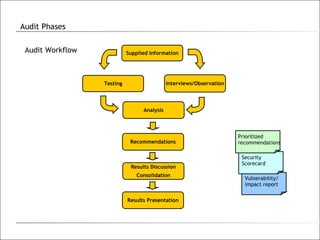
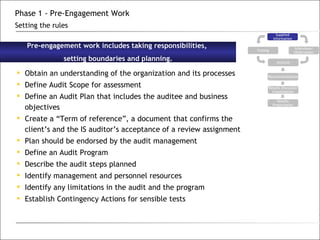
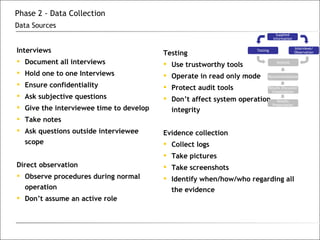
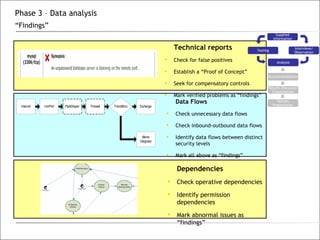
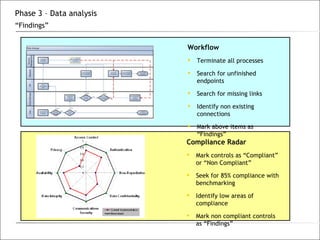
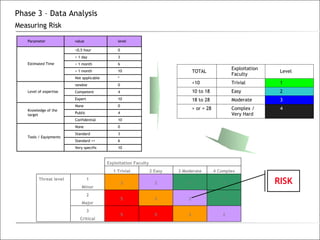
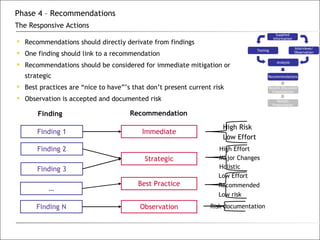
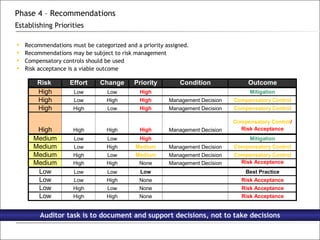
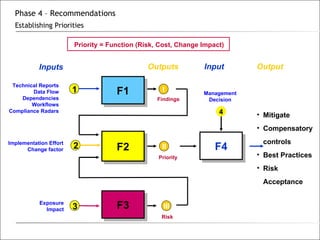
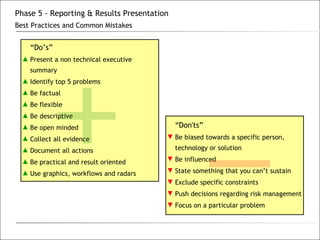
3. The phases of an audit include pre-engagement work, data collection through testing, interviews and documentation, data analysis to identify findings and risks, developing recommendations, and reporting results.