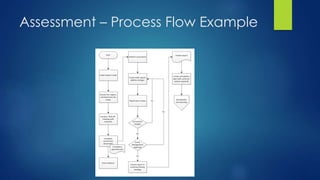
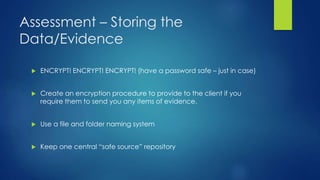
The document provides guidance on creating a compliance assessment program on a tight budget. It outlines steps to prepare such as creating policies and socializing them, determining assessment scope and methods, developing assessment forms and reporting templates, and improving the program over time. The preparation phase involves creating policies, standards, and guidelines. Assessment involves mapping processes, using forms to evaluate adherence, and creating reports on findings. Findings are then reviewed and the program is refined through cycles.