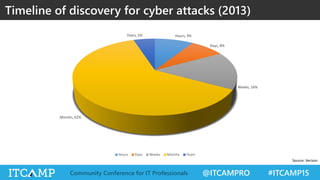
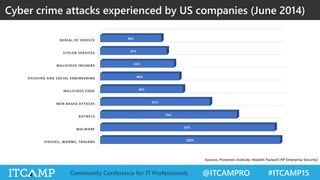
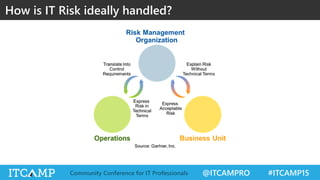
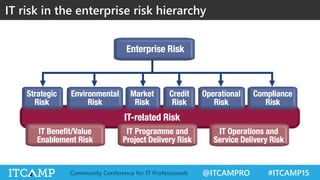
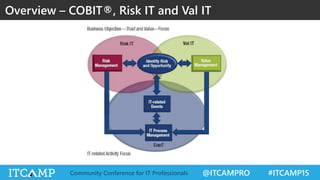
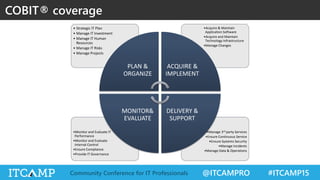
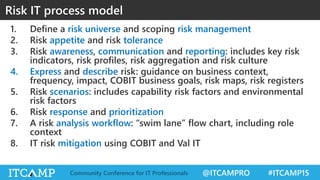
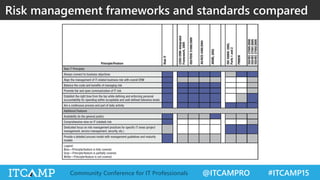
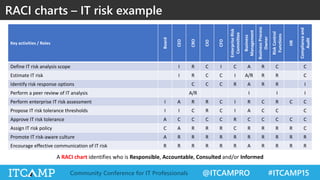
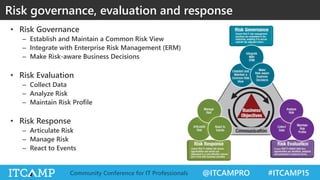
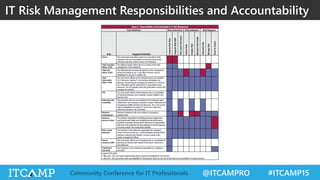
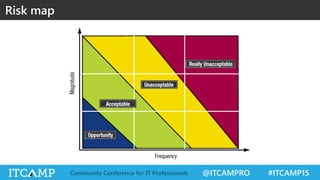
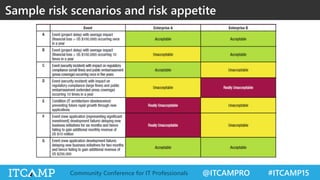
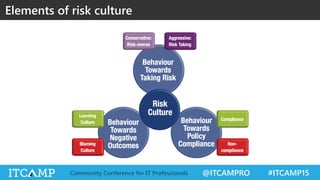
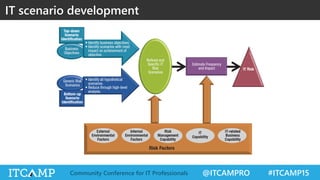
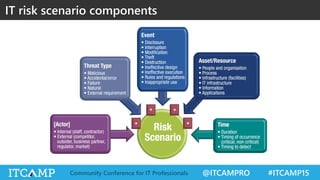
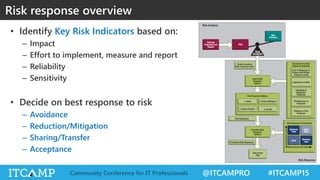
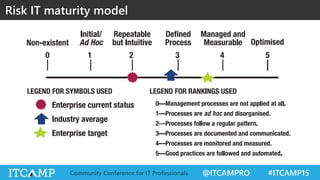
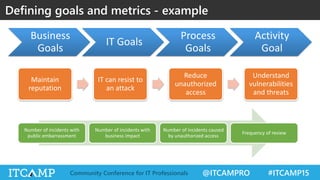
The document summarizes key concepts and frameworks related to IT risk management, highlighting the importance of understanding risk in business contexts and employing frameworks like COBIT and Risk IT for effective governance and management. It presents statistics on cybersecurity breaches and emphasizes the need for ongoing risk evaluation, response, and establishment of a risk-aware culture within organizations. Best practices for minimizing IT risks are outlined, recommending the implementation of strategic plans, allocation of resources, and regular assessment of risks.