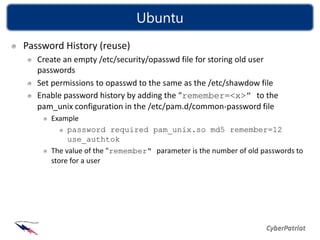
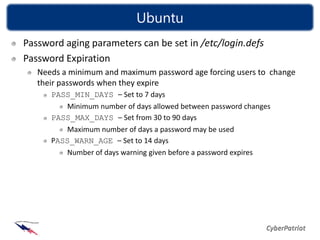
The document discusses password security, explaining authentication and authorization, how passwords are used to control access, the importance of strong password selection to prevent cracking, and provides guidelines for password policies and creating strong passwords to protect against attacks. It examines common authentication methods, why passwords should be complex and regularly changed, and tools that can crack passwords if they are weak.