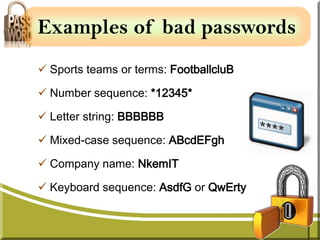
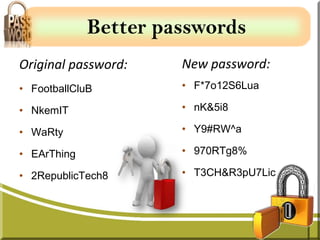
Passwords are secret codes that allow users to access files, computers, and programs. They are important for security and preventing unauthorized access. However, passwords can be stolen internally if overheard, seen over someone's shoulder, or found written down. The document provides tips for creating strong passwords that are long, complex, varied between accounts, and changed often. It warns against weak passwords that are short, repetitive, or use personal details. Creating secure passwords is key to protecting personal and organizational resources.