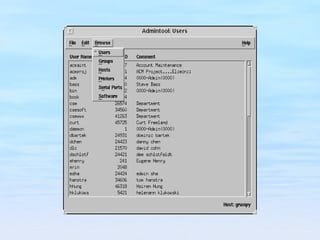
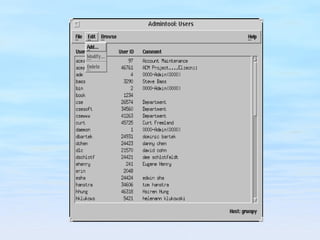
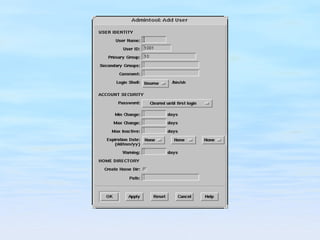
The document discusses user account management tasks for system administrators, including creating login names, assigning home directories and user IDs, setting passwords and password policies, and tools for managing user accounts. It covers challenges around reusable passwords and approaches to improve security such as password aging, lockouts for failed attempts, and one-time password tokens.











![Users Password file fields User - the login name assigned to the user. Password - may be one of the following: NP - No password assigned [xX] - Look in some alternate location encrypted password UID - the UID assigned to this user GID - the login group this user belongs to Users may be in other groups (see /etc/group)](https://image.slidesharecdn.com/ch10systemadministration-120209005509-phpapp02/85/Ch10-system-administration-12-320.jpg)