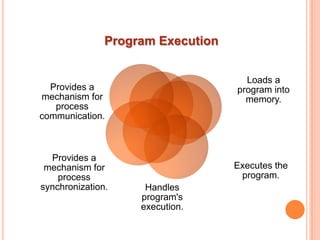
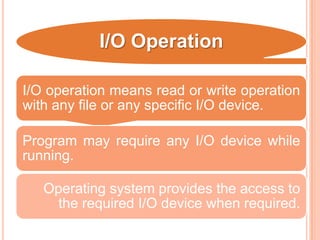
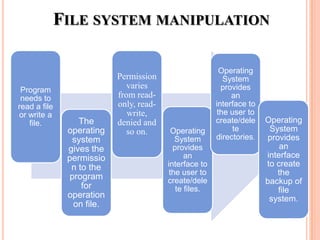
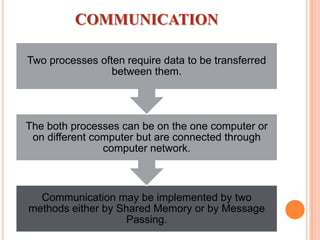
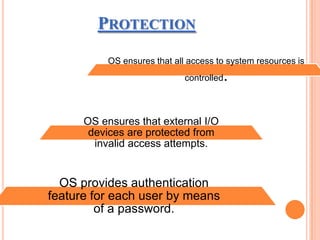
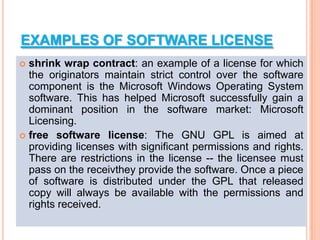
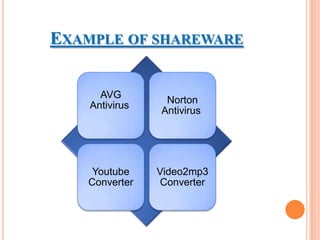
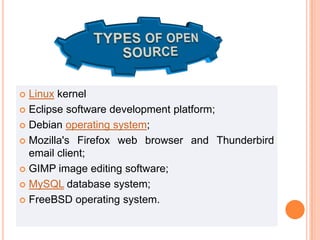
The document discusses different types of operating systems and software licenses. It describes how operating systems coordinate hardware resources, provide user interfaces and manage programs. It also defines standalone, real-time, multi-user and multi-tasking operating systems. Common services provided by operating systems include program execution, I/O operations, file manipulation, communication, error handling and protection. The document also discusses copyright, different software licenses like freeware, shareware and open source, and provides examples of each.