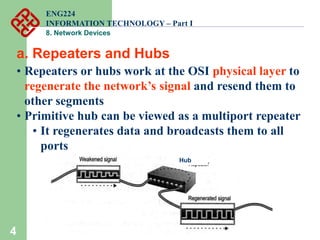
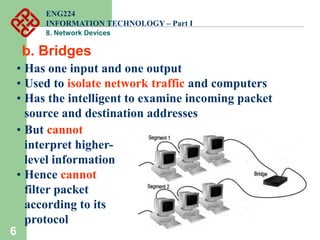
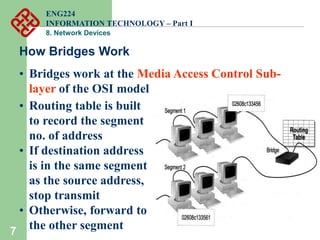
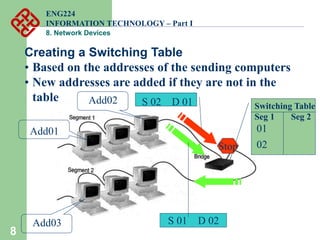
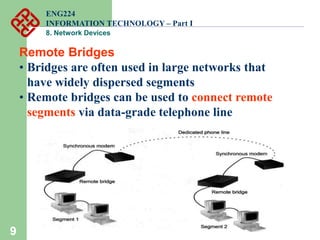
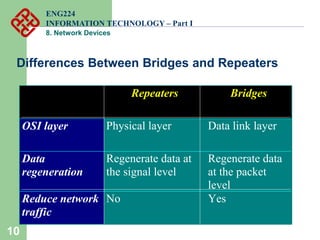
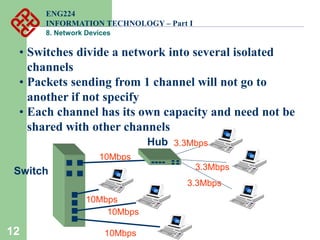
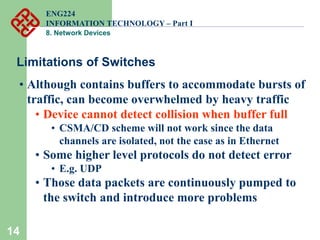
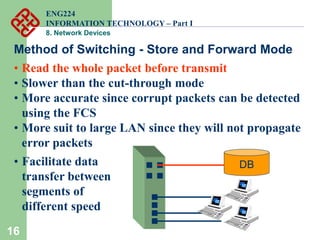
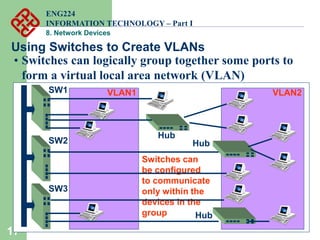
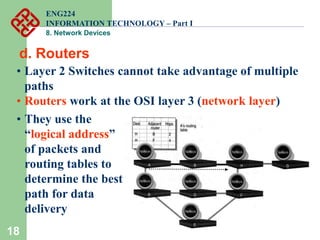
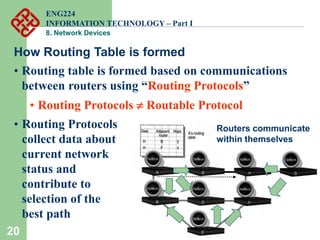
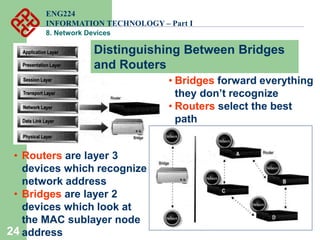
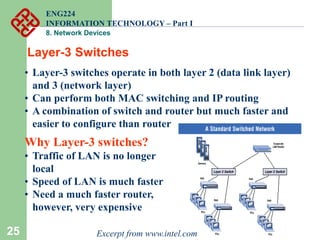
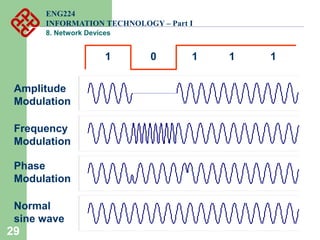
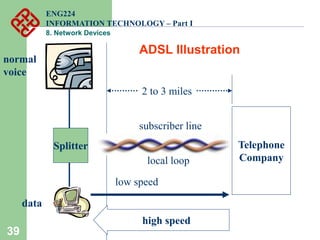
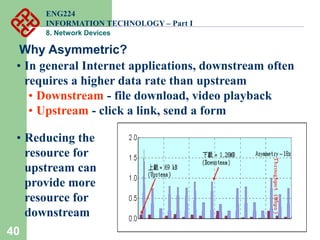
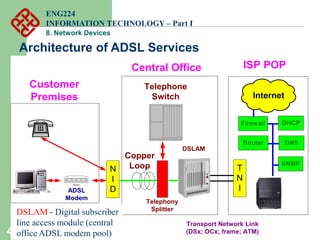
Network devices such as repeaters, bridges, switches and routers are used to connect and expand networks. Repeaters regenerate signals to expand small networks, while bridges and switches can understand node addresses to segment networks. Routers interconnect different networks and determine optimal routes using network layer addresses and routing protocols. Remote access devices like modems and ADSL modems allow computers to connect to networks over telephone lines by modulating digital signals into analog for transmission.