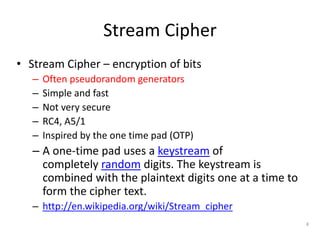
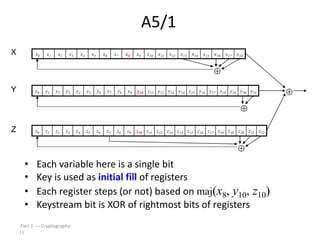
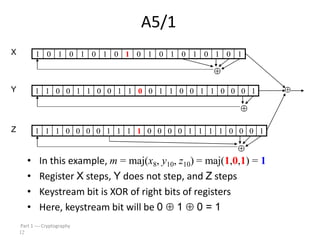
This document discusses symmetric key cryptography and stream ciphers. It explains that stream ciphers encrypt plaintext one bit or byte at a time using a pseudorandom keystream, whereas block ciphers encrypt fixed-length blocks. The document then describes the A5/1 stream cipher, which uses three shift registers to generate a keystream by XORing bits from each register. An example is provided to illustrate how the keystream is generated by updating the registers based on their bit values.