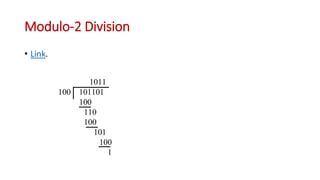
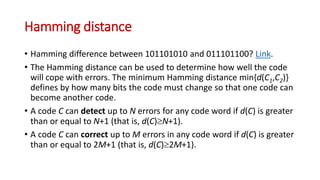
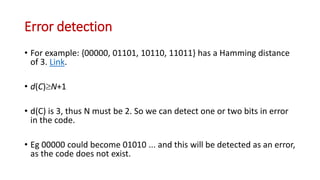
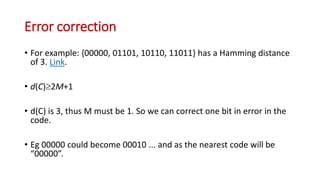
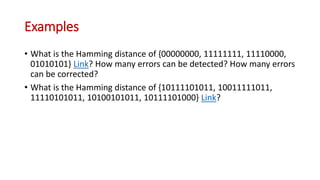
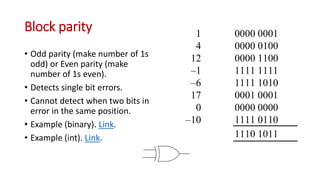
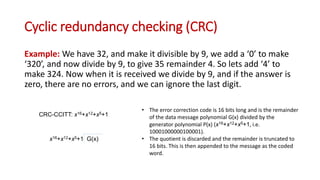
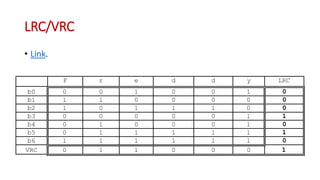
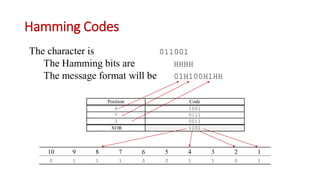
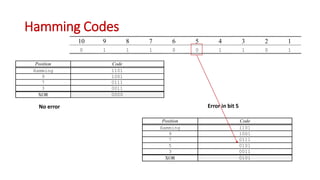
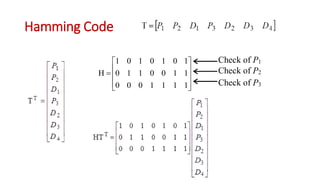
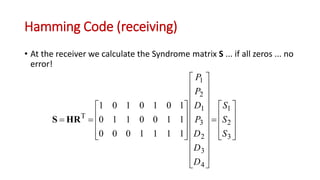
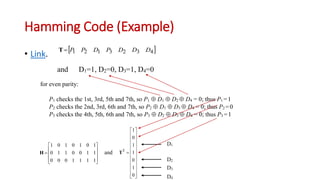
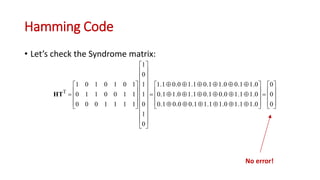
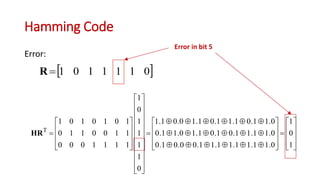
This document discusses error coding techniques used in digital communications. It begins by explaining modulo-2 arithmetic operations that are the basis for digital coding. It then covers binary manipulation of addition and multiplication. Various error detection and correction codes are described, including cyclic redundancy check (CRC), linear block codes, and Hamming codes. Hamming codes add redundant bits to allow detection and correction of bit errors during transmission.