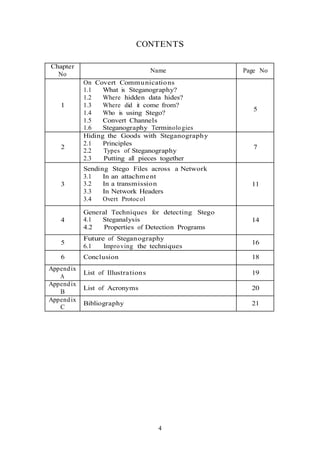
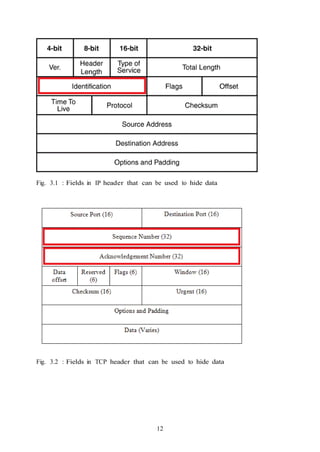
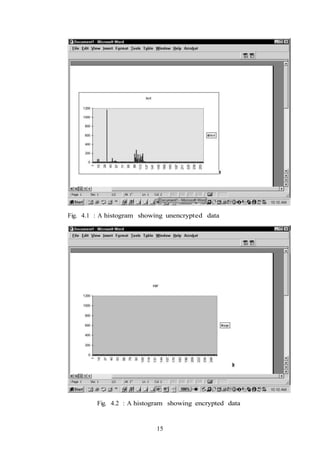
This document is a seminar report on steganography presented by Tumma Ashwin to fulfill requirements for a B.Tech degree in Computer Engineering. It includes an introduction to steganography, principles of hiding data, types of steganography techniques, and methods for sending stego files across a network. The report was guided by Prof. S. U. Ghumbre and certifies that Tumma Ashwin completed the project work.