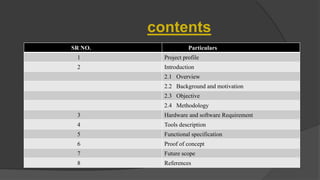
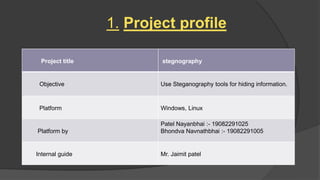
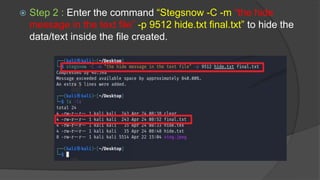
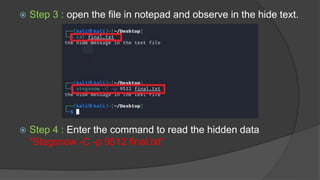
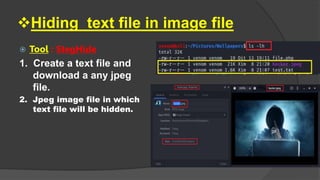
Steganography is the practice of hiding secret information within ordinary files like images, videos, and audio. The document discusses various steganography tools that can be used to hide text, images, audio, and video files within carrier files. It provides examples of using tools like Stegsnow and StegHide to hide messages in images and text files. The document also gives a live demo of hiding an audio file within a text file to showcase steganography techniques. The goal of the project is to reliably transfer secret messages while hiding their presence from third parties.