This document provides instructions on configuring Linux security features such as SSH key-based authentication, firewall rules using iptables, SELinux concepts, and the Fail2ban utility. It discusses generating SSH keys, editing SSH configuration files, setting default firewall policies and rules for input, output, and forwarding, as well as network address translation rules. It also covers SELinux file and process context types and restoring default contexts. Lastly, it explains how to install, configure, and check the status of Fail2ban to automatically ban IPs with too many failed login attempts.

















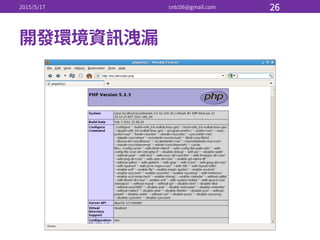





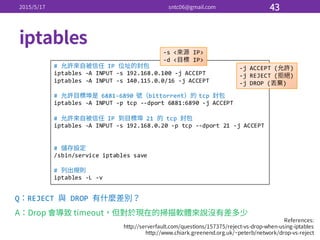
![• iptables-‐service
# systemctl enable iptables
• / / iptables
# systemctl [stop|start|restart] iptables
• iptable
# service iptables save
• iptables
# iptables -‐L
• ssh](https://image.slidesharecdn.com/3-150517174216-lva1-app6891/85/Linux-40-320.jpg)







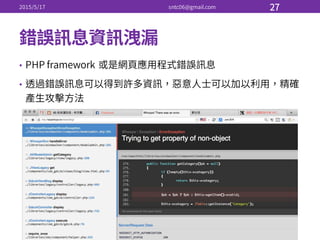
![•
•
# chcon [-‐R] [-‐t type] [-‐u user] [-‐r role]
•
# restorecon [-‐Rv]
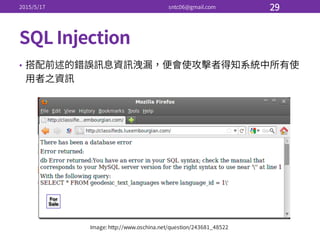
root:~/ # ls -‐Z
-‐rw-‐-‐-‐-‐-‐-‐-‐. root root system_u:object_r:admin_home_t:s0 anaconda-‐ks.cfg
-‐rw-‐r-‐-‐r-‐-‐. root root unconfined_u:object_r:admin_home_t:s0 latest.zip
-‐rw-‐r-‐-‐r-‐-‐. root root unconfined_u:object_r:admin_home_t:s0 number
-‐rw-‐r-‐-‐r-‐-‐. root root unconfined_u:object_r:admin_home_t:s0 phpmyadmin_4.4.0.zip
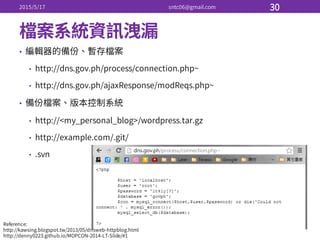
Identify : Role : Type
: :](https://image.slidesharecdn.com/3-150517174216-lva1-app6891/85/Linux-50-320.jpg)



