This document provides an introduction to firewalls using Linux iptables. It defines what a firewall and iptables are, describes common firewall usages, and explains how iptables is organized into tables and chains. It also provides examples of basic iptables commands for filtering, connection tracking, logging, and network address translation (NAT). The key points are that iptables is Linux's built-in firewall, it filters and mangles packets across various chains, and examples are given for allowing/denying traffic, NAT, and saving firewall rules.





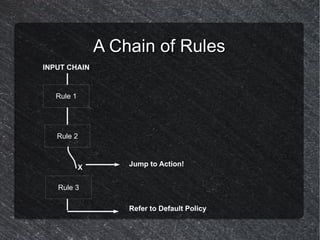


![Using iptables
Synopsis
iptables [table] [action] [chain] [option] [target]
table – {filter, nat, mangle}
action – {-A (add), -D (delete), -R (replace)}
chain – {INPUT, FORWARD, OUTPUT etc.}
options - {-s(source), -d(destination), --sport(source port,
--dport(destination port), -m (module), --sync (sync
packed) etc.}
target – {ACCEPT, DROP, REJECT, MASQUERADE,
DNAT etc.}](https://image.slidesharecdn.com/iptablesfirewall-110415090424-phpapp02/85/Introduction-to-firewalls-through-Iptables-9-320.jpg)







![Persistence
// Save rules
iptables-save > /etc/iptables.conf
// Restore rules
iptables-restore < /etc/iptables.conf
// If you have virtual service
/etc/init.d/iptables [stop|start|save]
// If you don't have virtual service to auto start add restore
command to /etc/rc.local or any other bootup script](https://image.slidesharecdn.com/iptablesfirewall-110415090424-phpapp02/85/Introduction-to-firewalls-through-Iptables-17-320.jpg)
