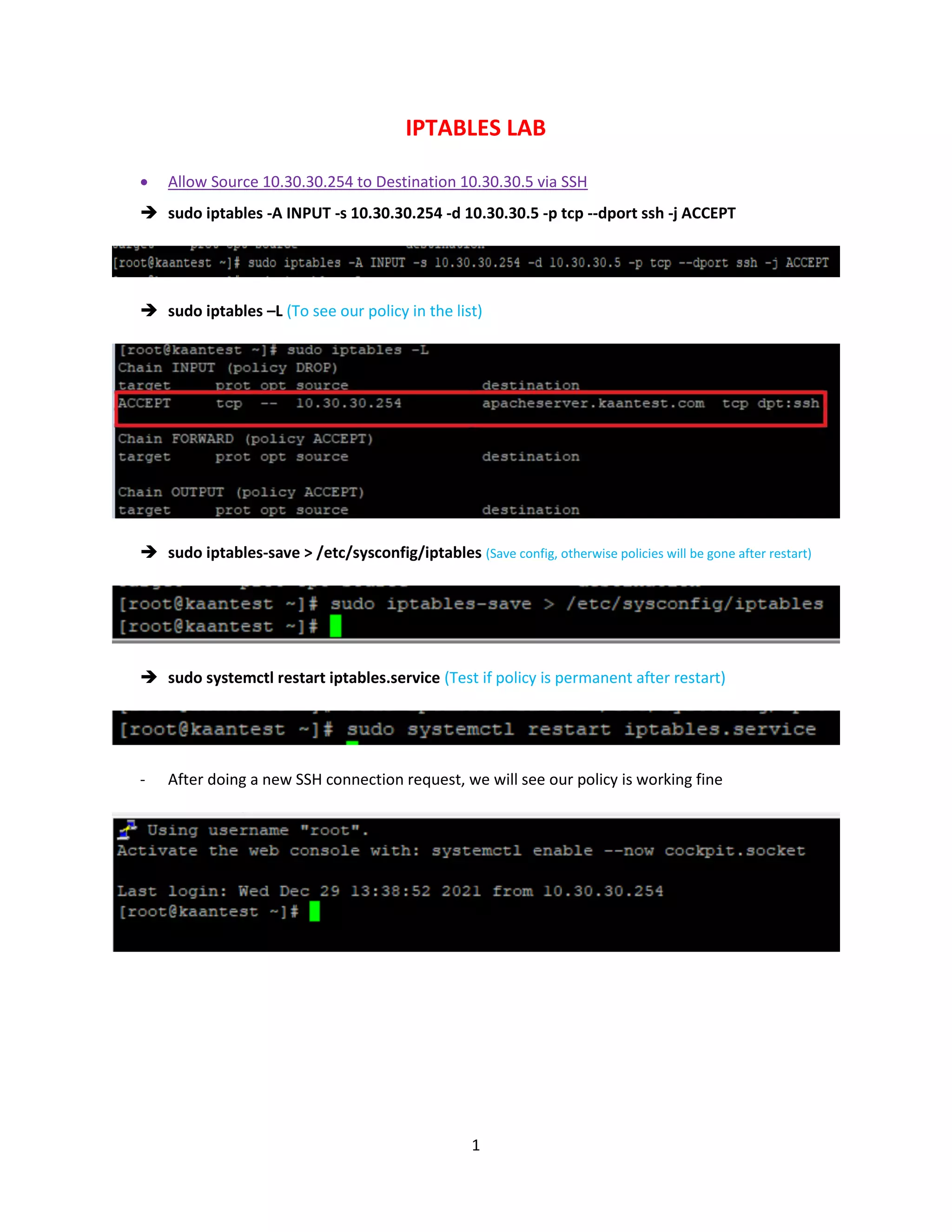
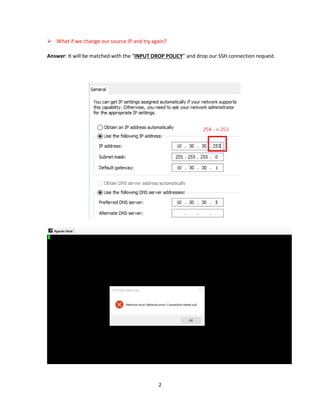
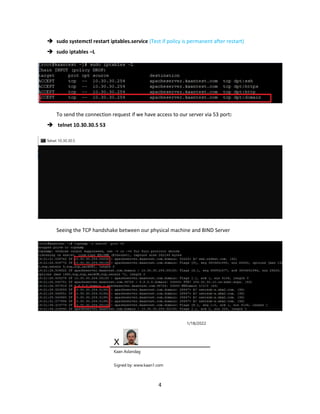
The document summarizes steps taken in an iptables lab to configure firewall rules allowing specific traffic. It shows how to allow SSH from 10.30.30.254 to 10.30.30.5, then add rules for DNS, HTTP and HTTPS. One rule is deleted without saving, so it will not persist after a restart. Testing connection attempts confirm the active rules.