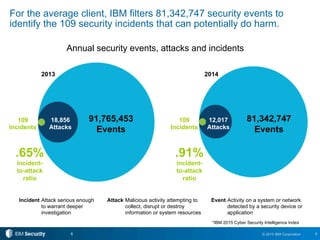
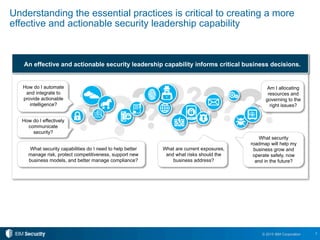
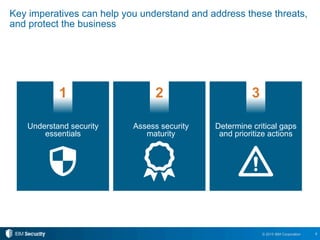
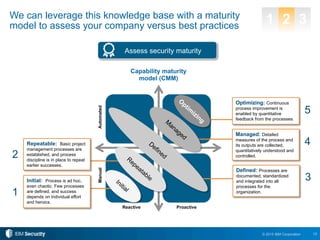
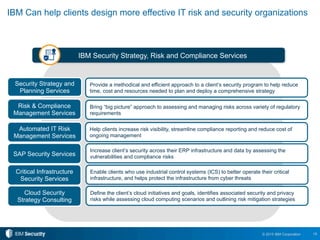
The document outlines 10 essential security practices for CXOs to enhance their organization's security posture amidst evolving cyber threats. Key points include understanding security essentials, assessing security maturity, and addressing risks tied to cloud services and third-party compliance. IBM also emphasizes the importance of automation and integration in security operations to inform business decisions and manage risks effectively.