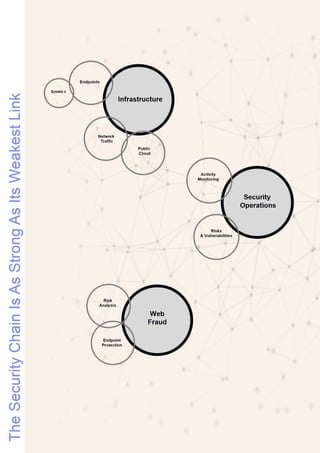
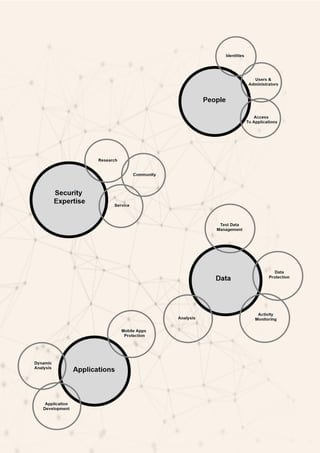
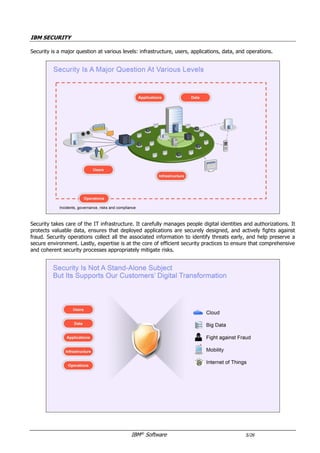
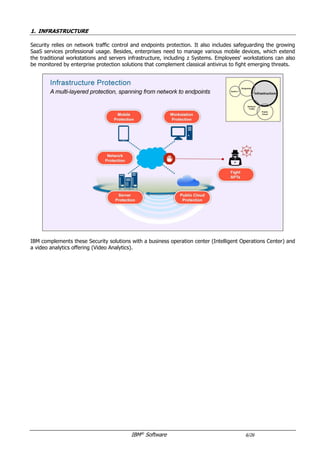
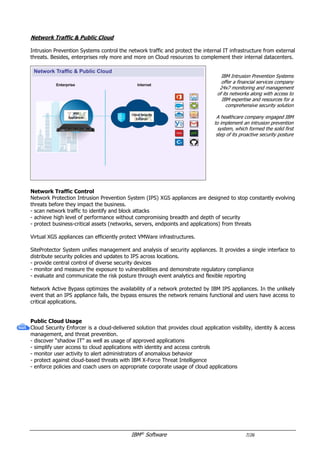
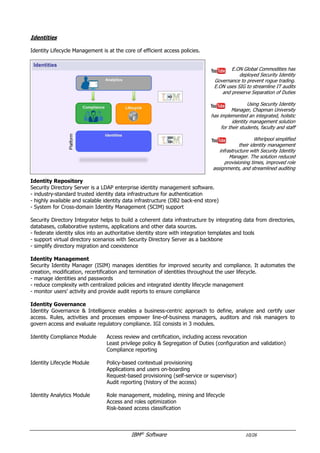
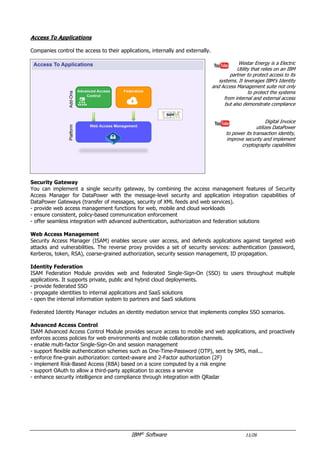
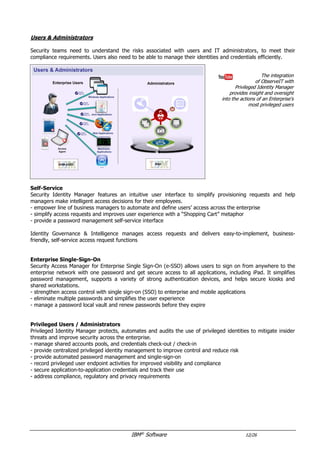
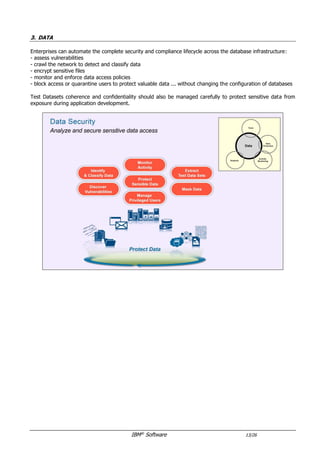
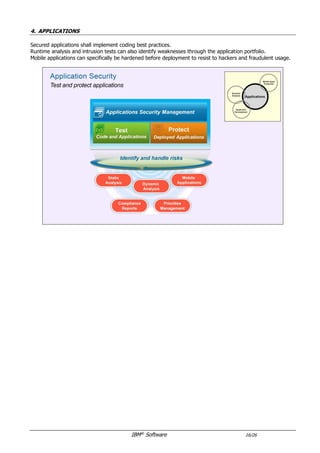
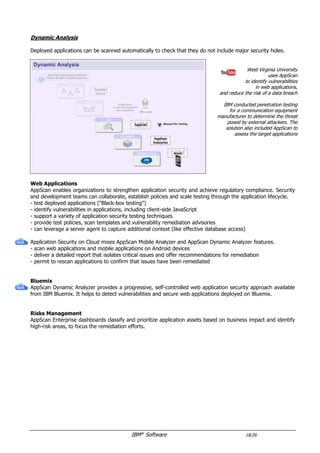
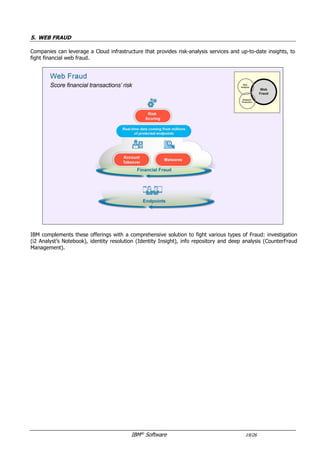
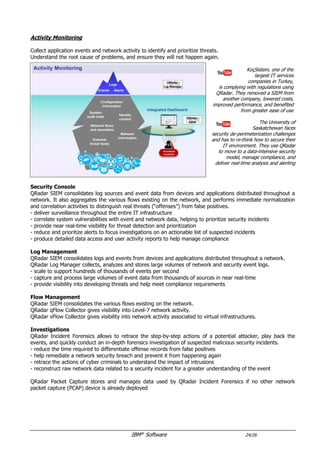
The document provides an overview of IBM's security software solutions as of June 2016, detailing the portfolio's offerings and how they add value for customers. It emphasizes security across infrastructure, user identities, data, and applications, while showcasing integrated solutions for managing threats, compliance, and operational efficiency. The document includes various resources and acknowledgments from the IBM security technical community.