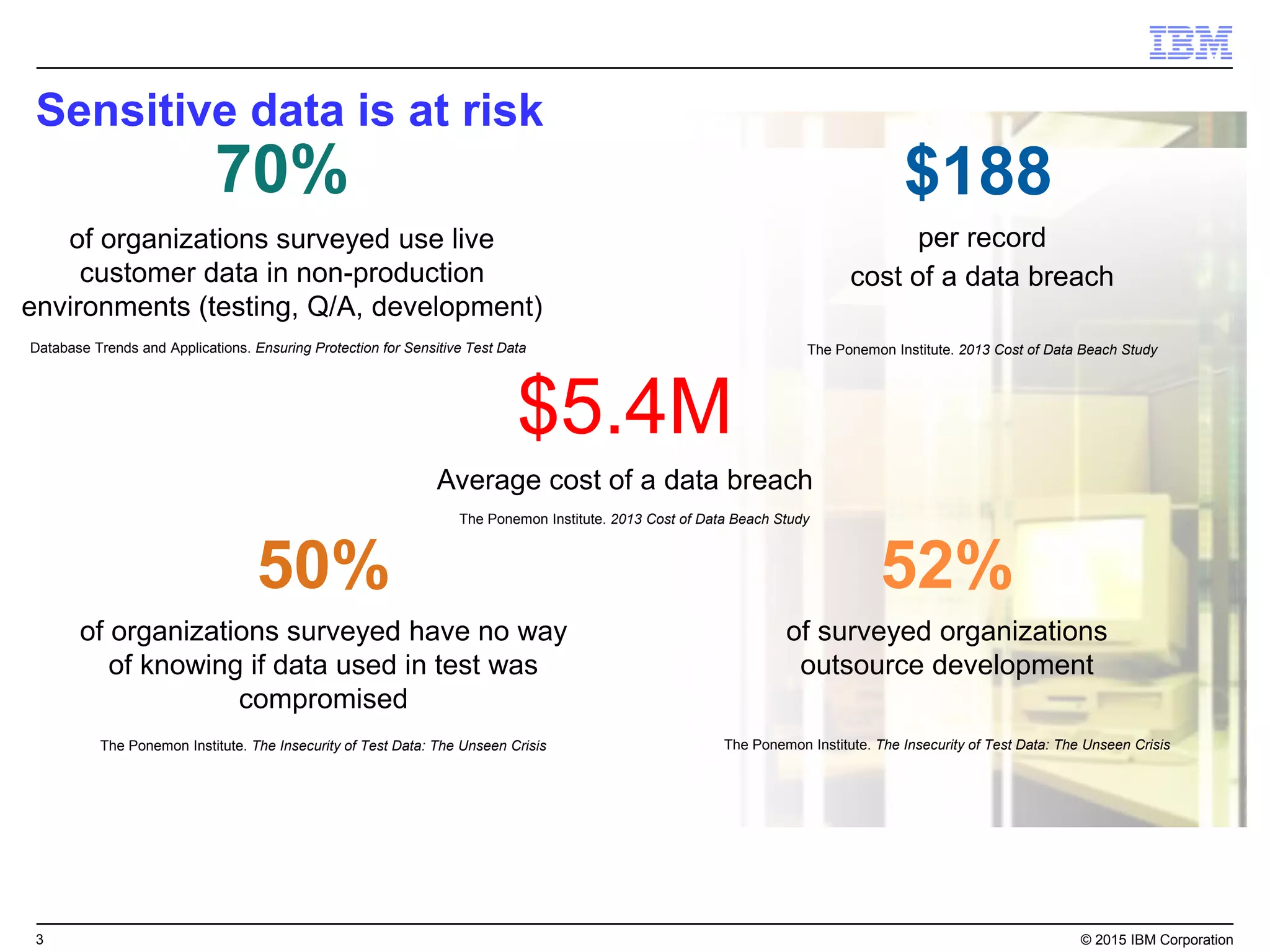
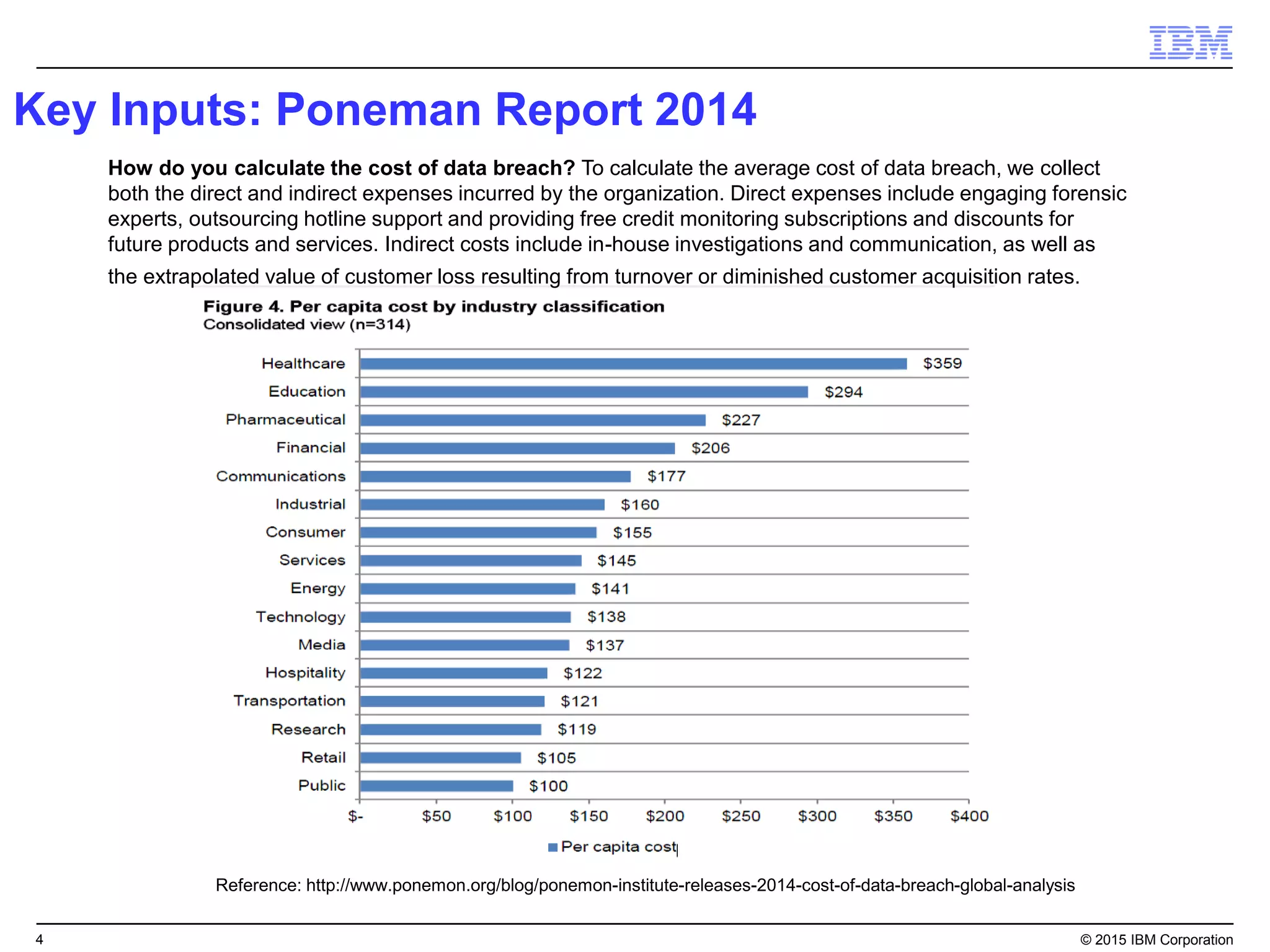
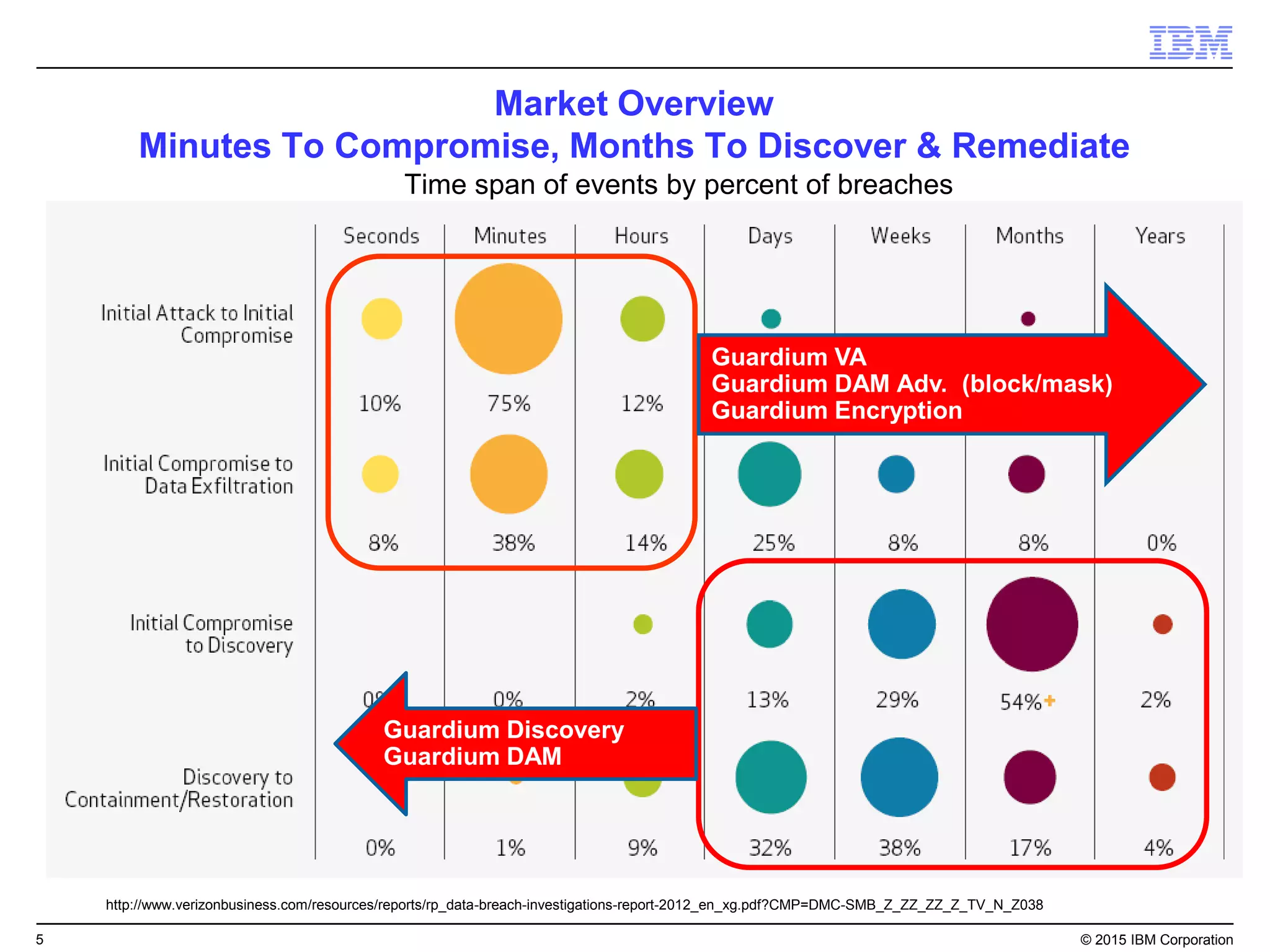
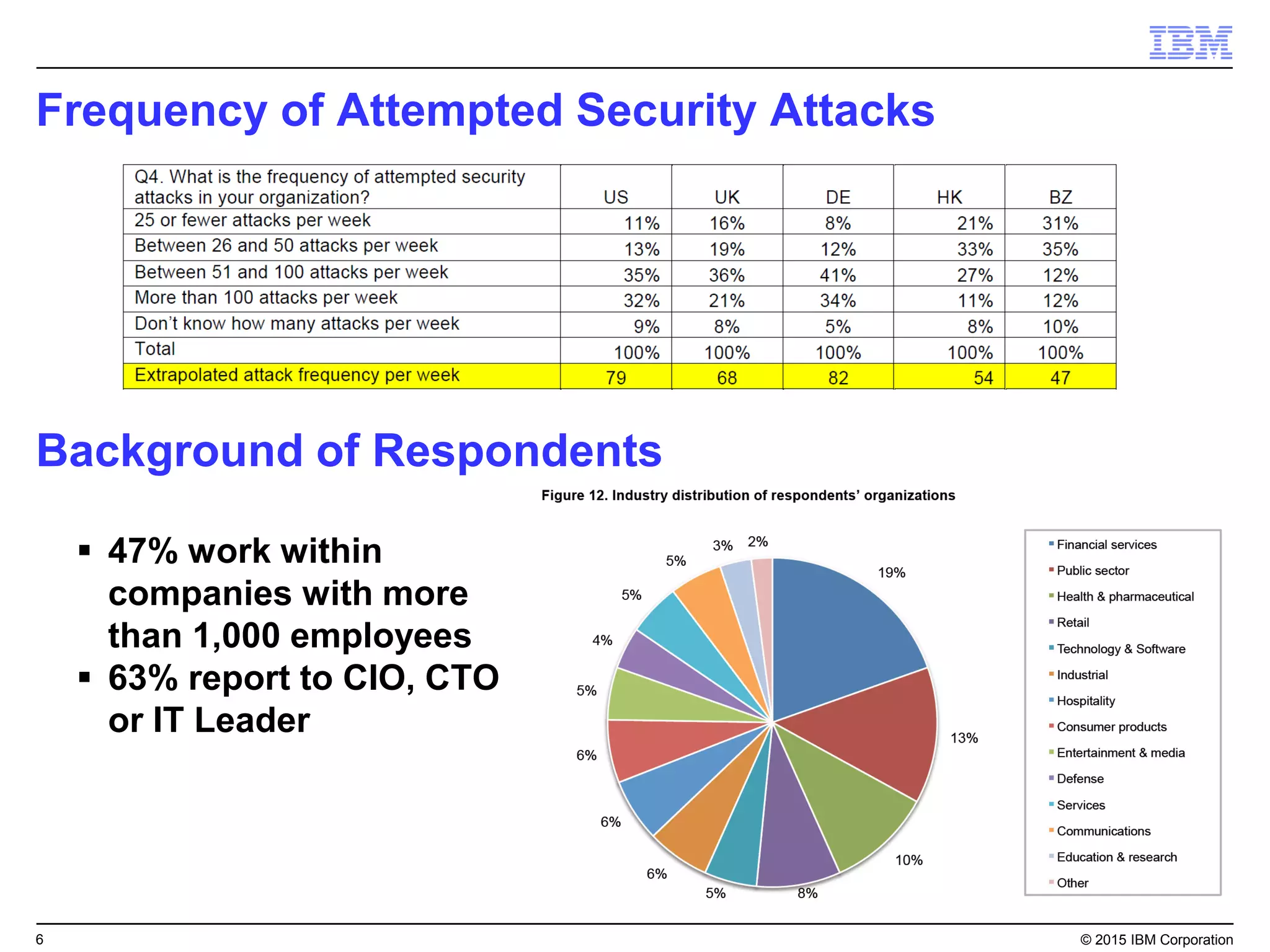
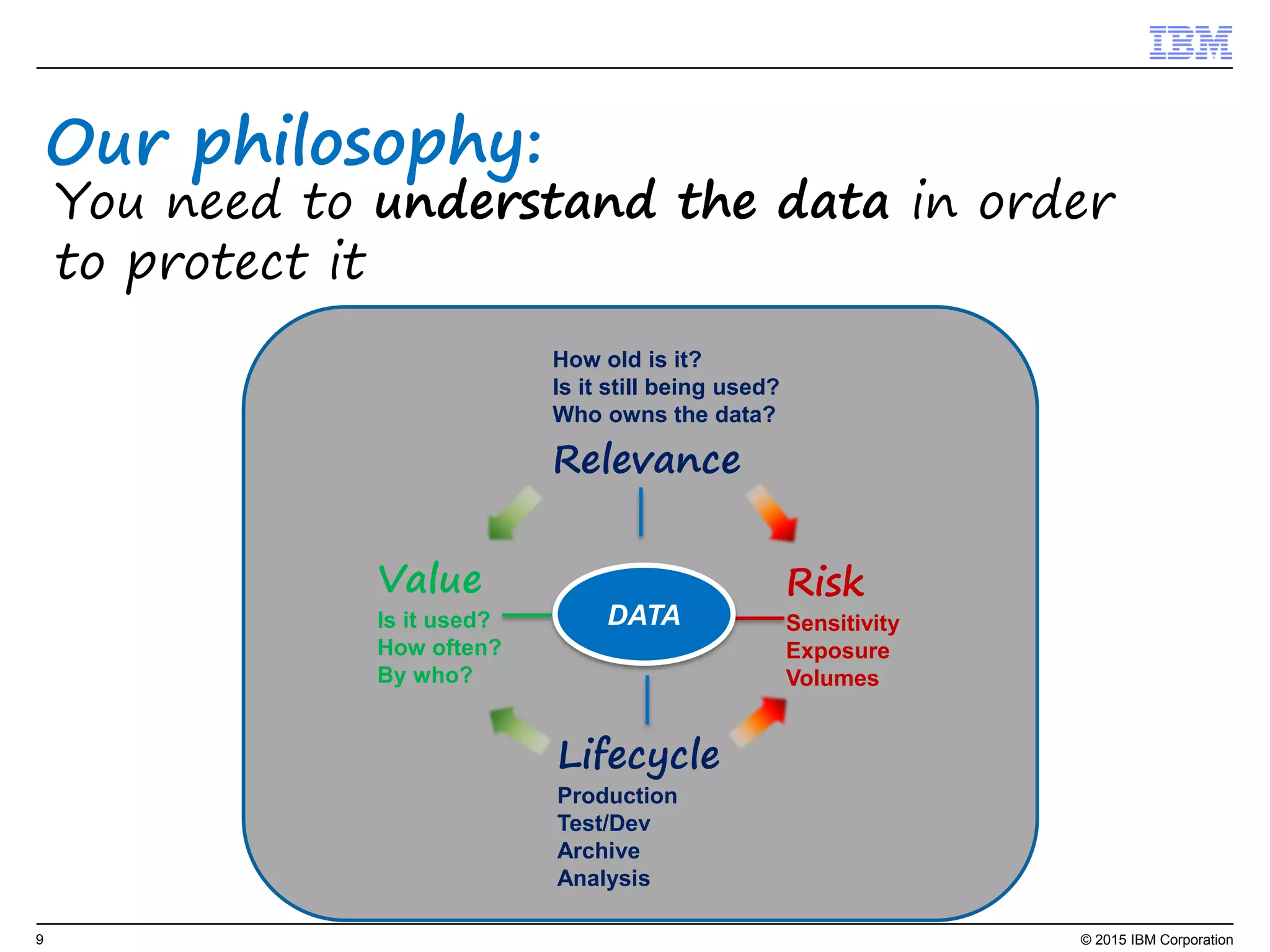
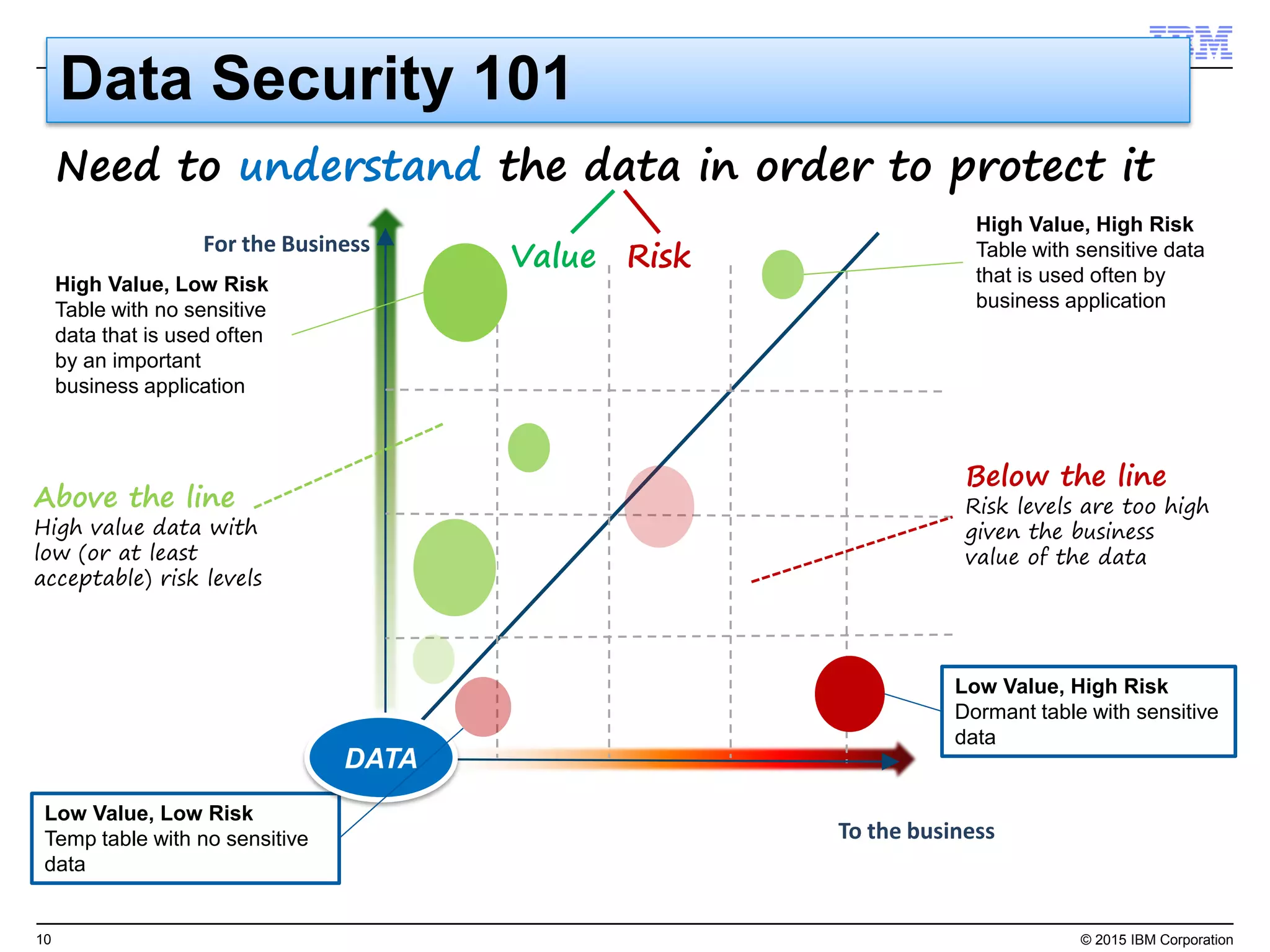
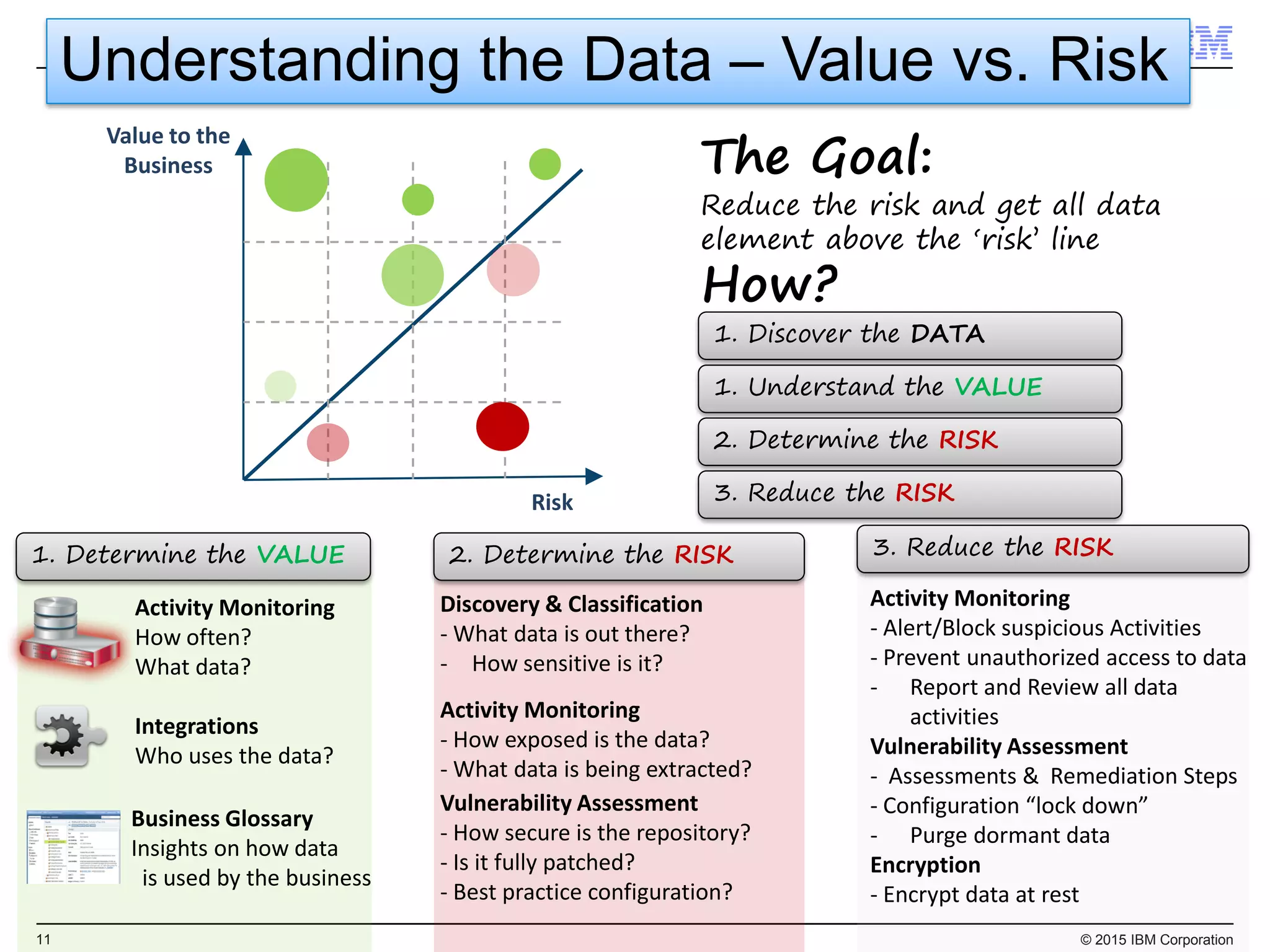
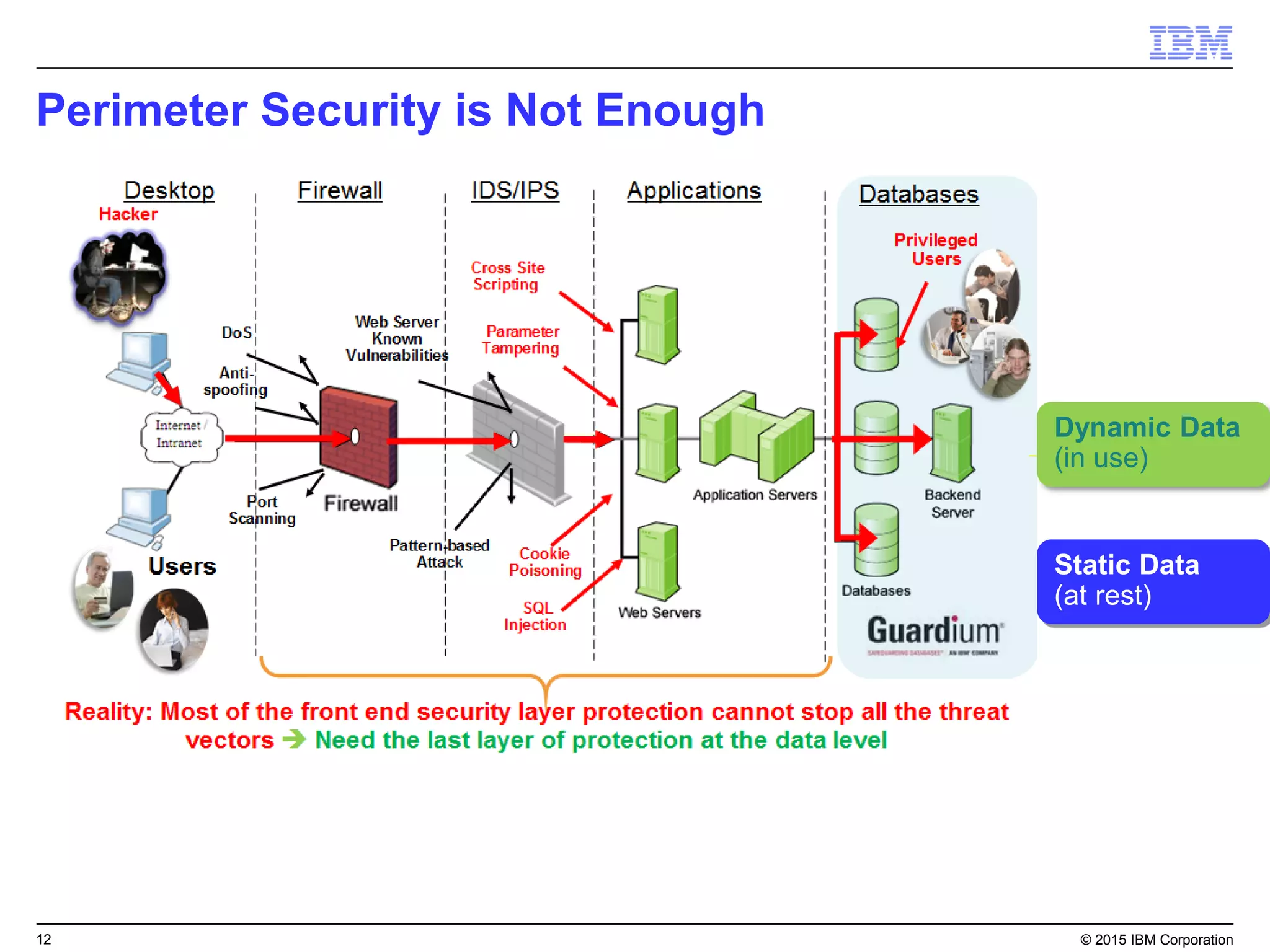
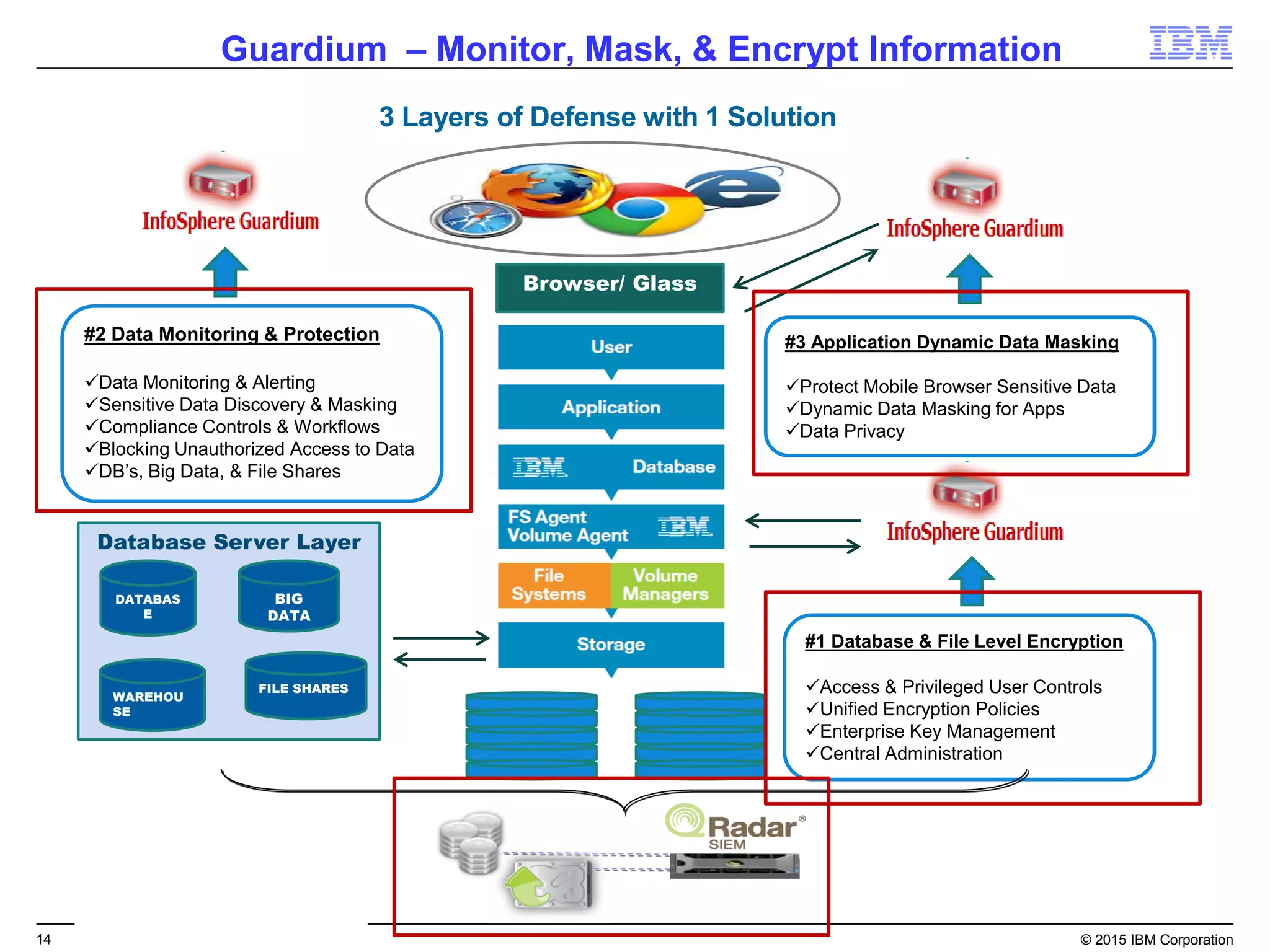
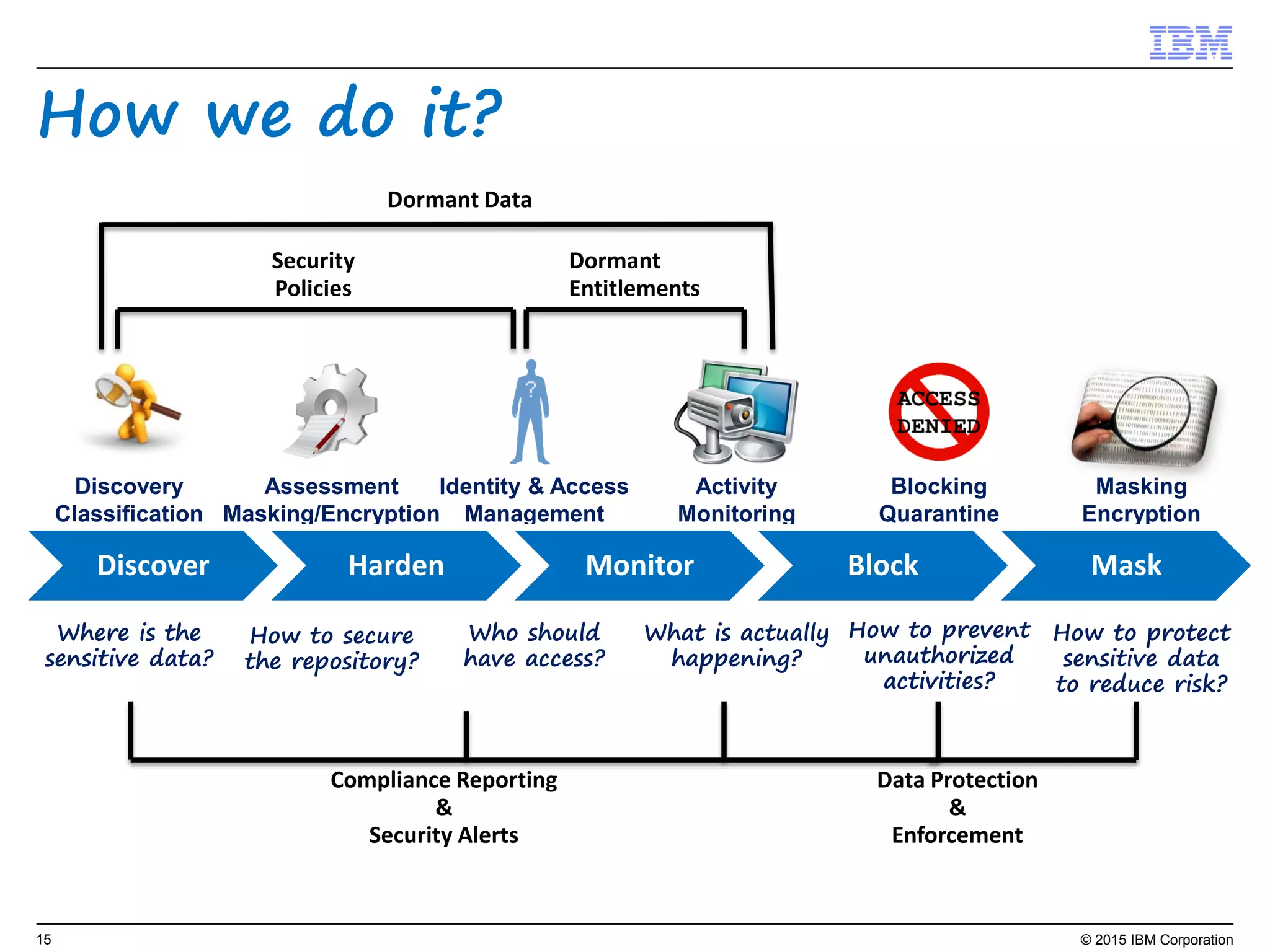
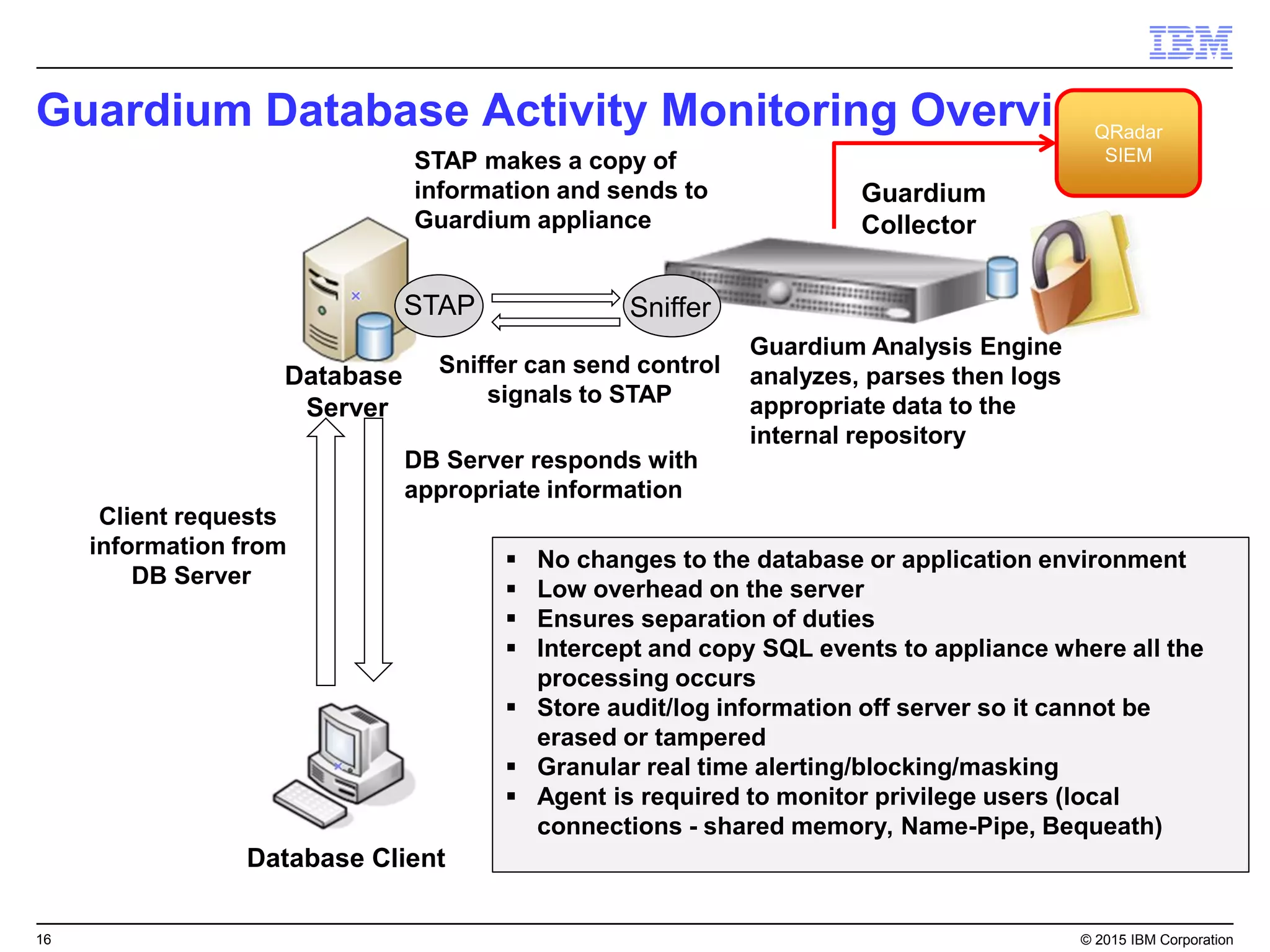
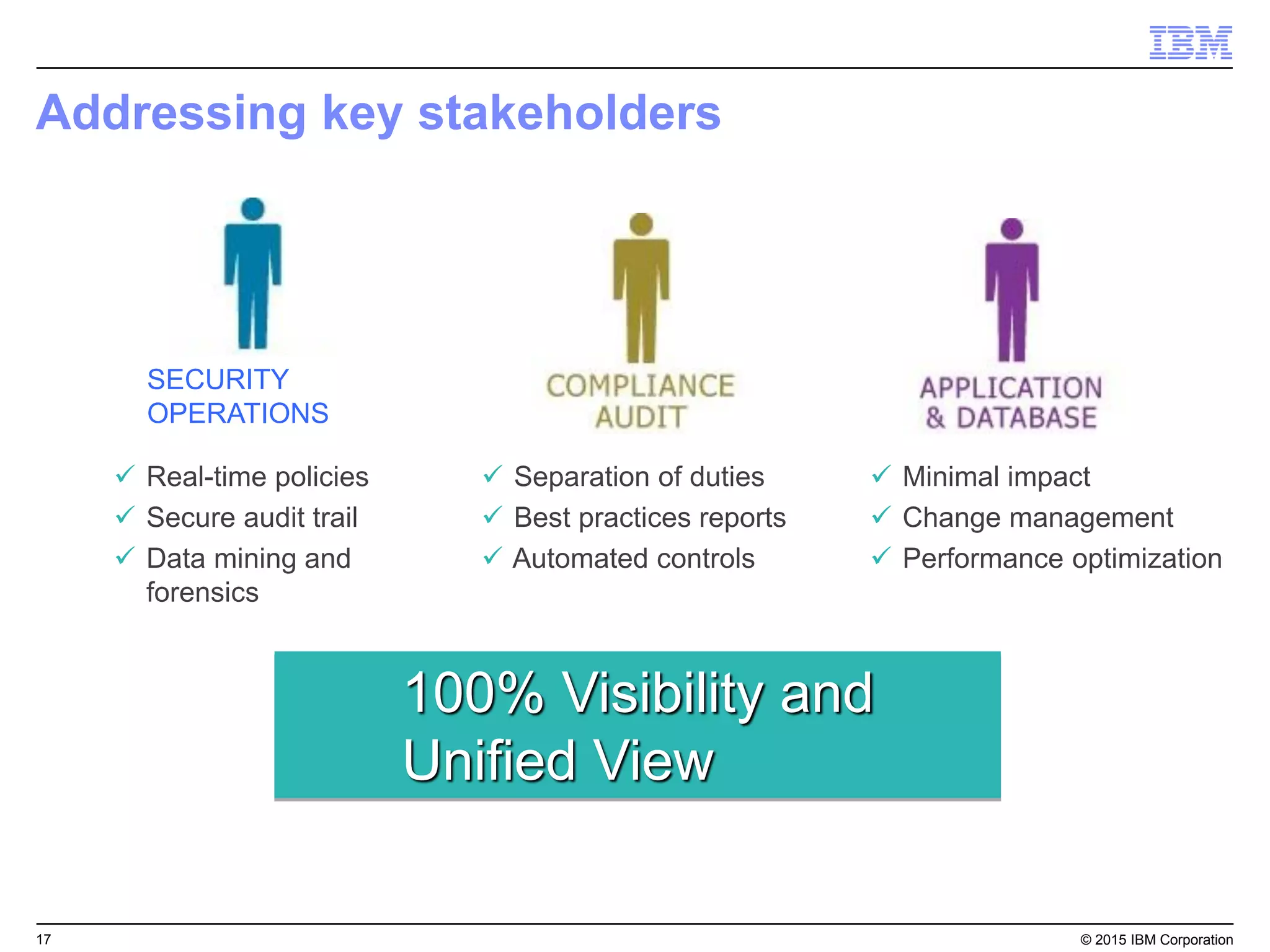
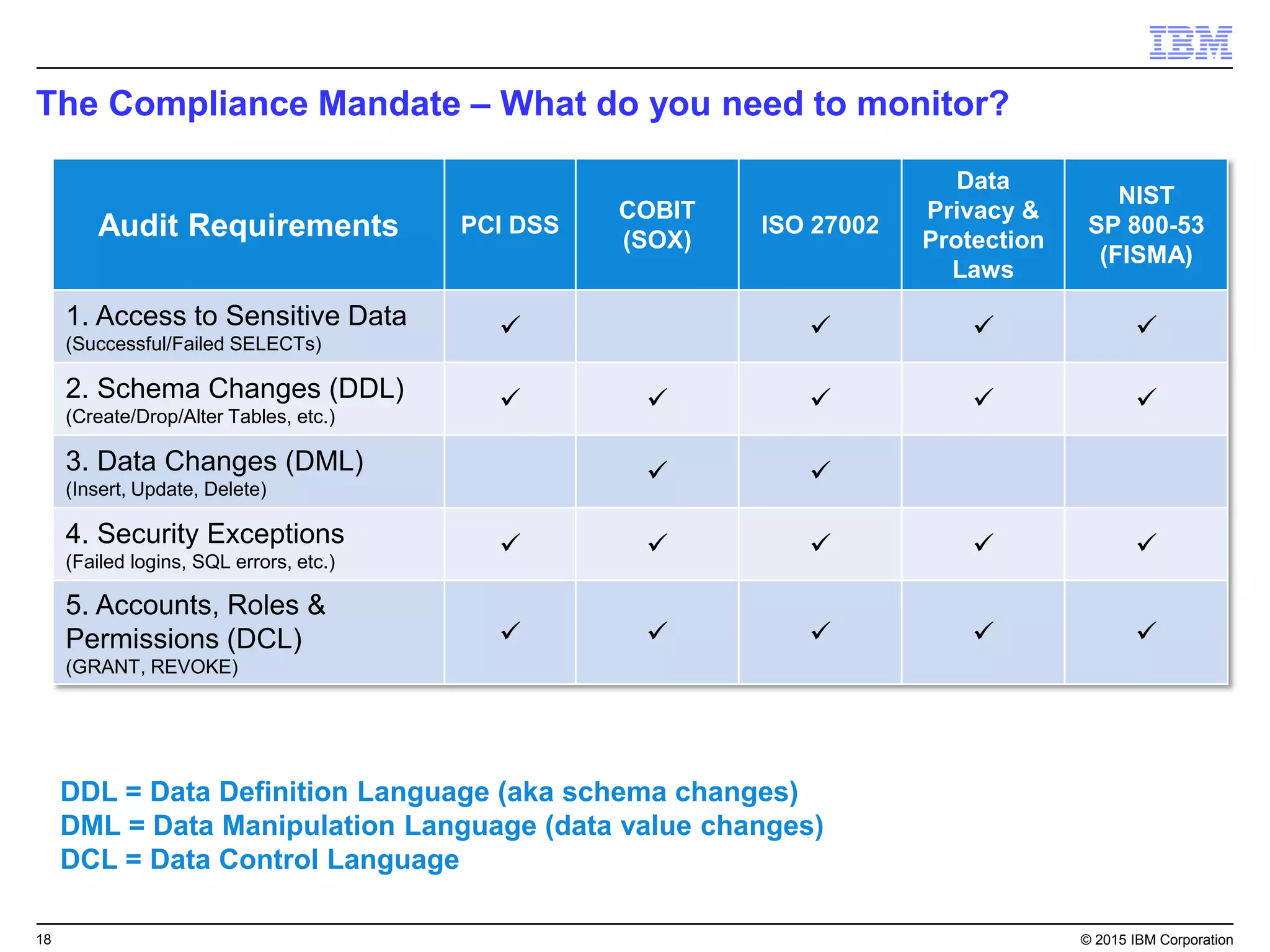
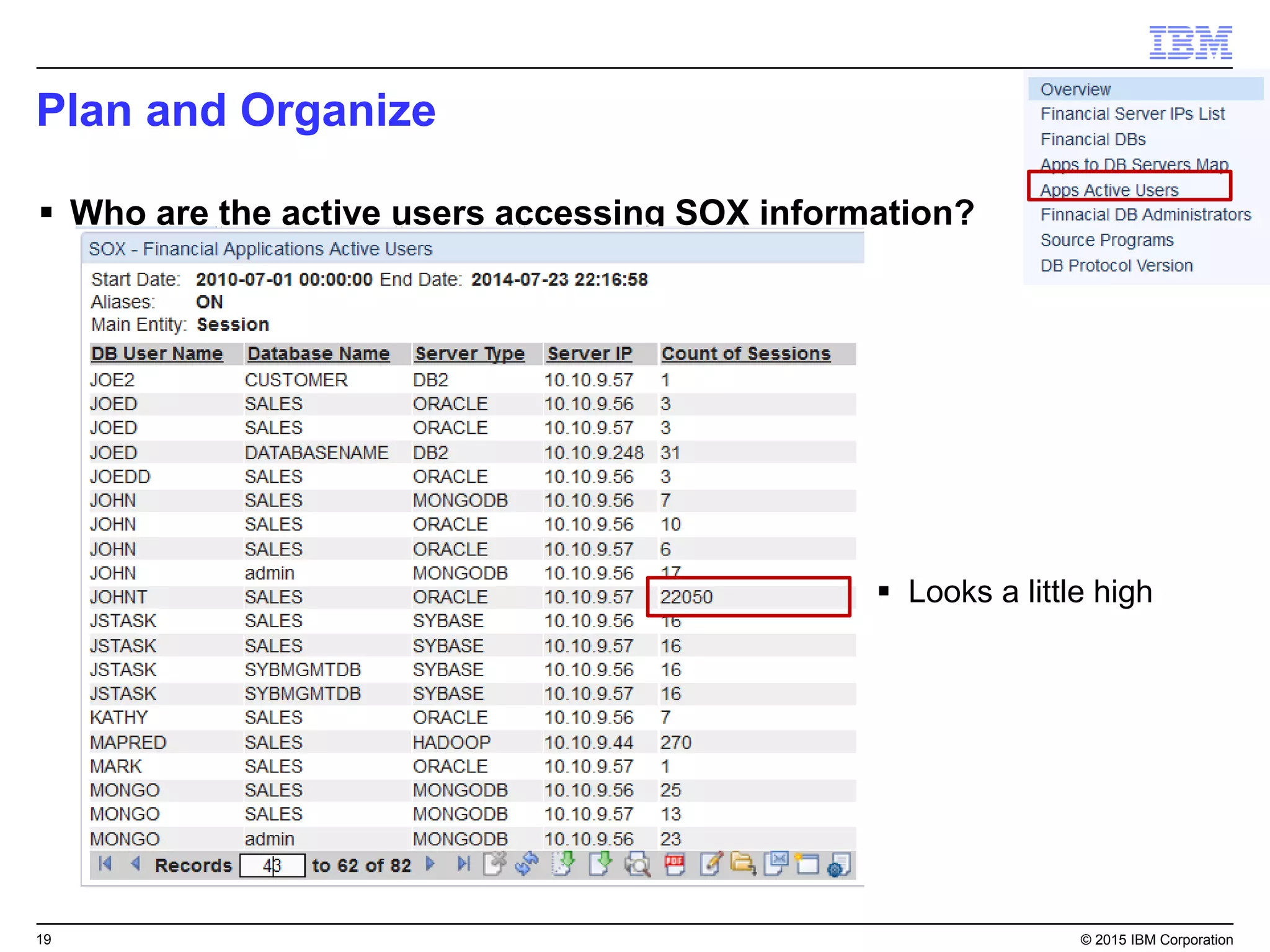
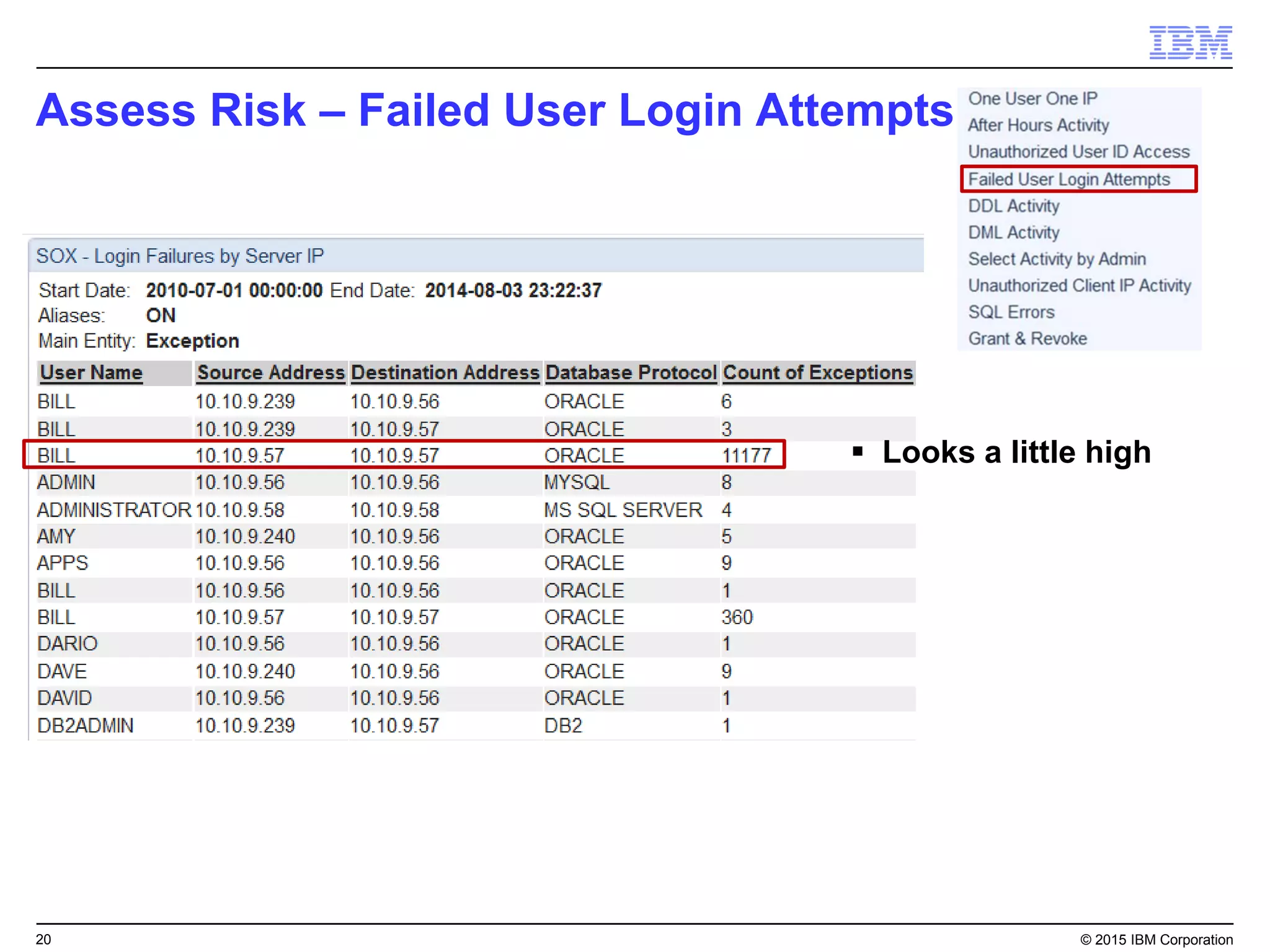
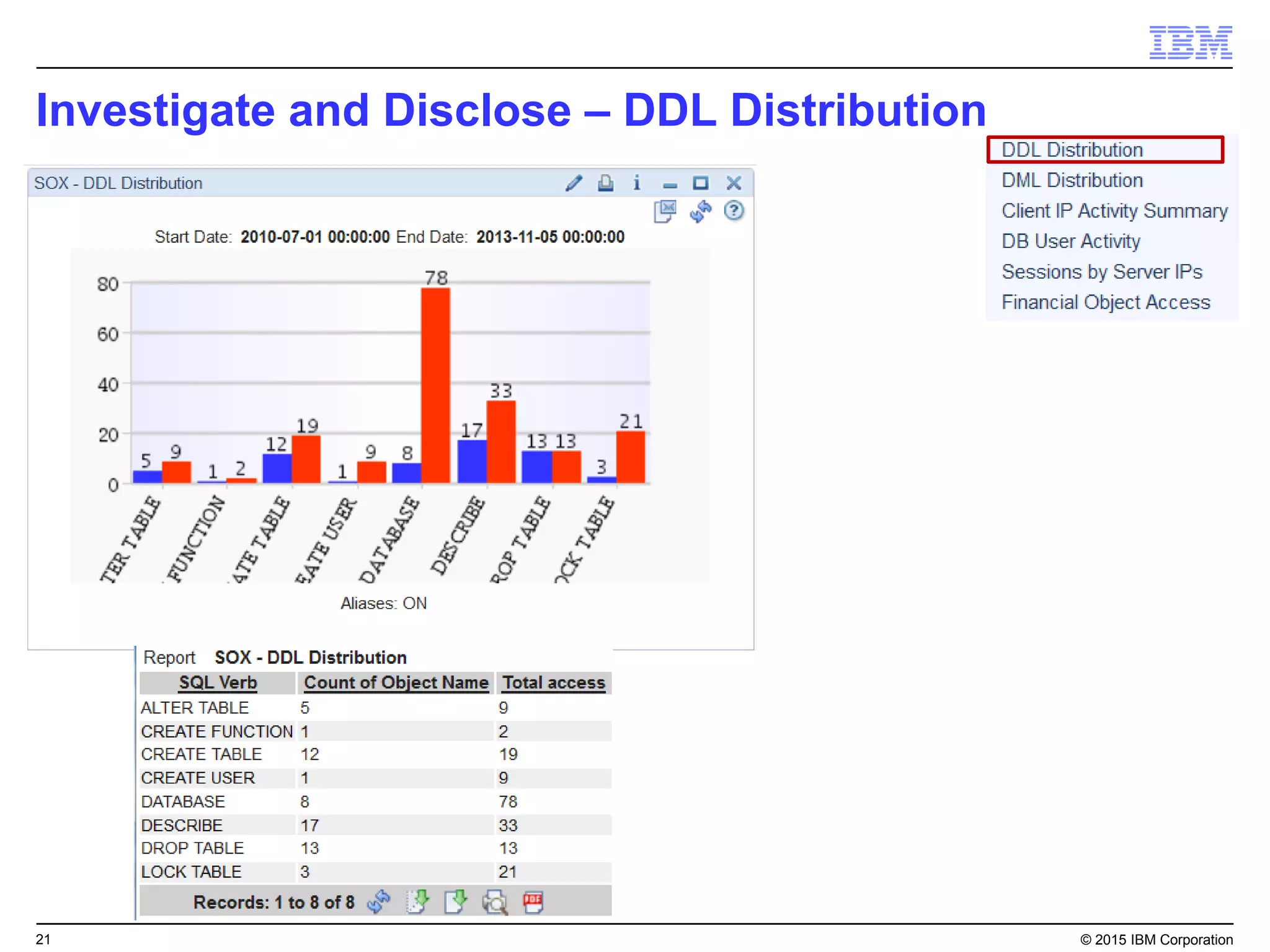
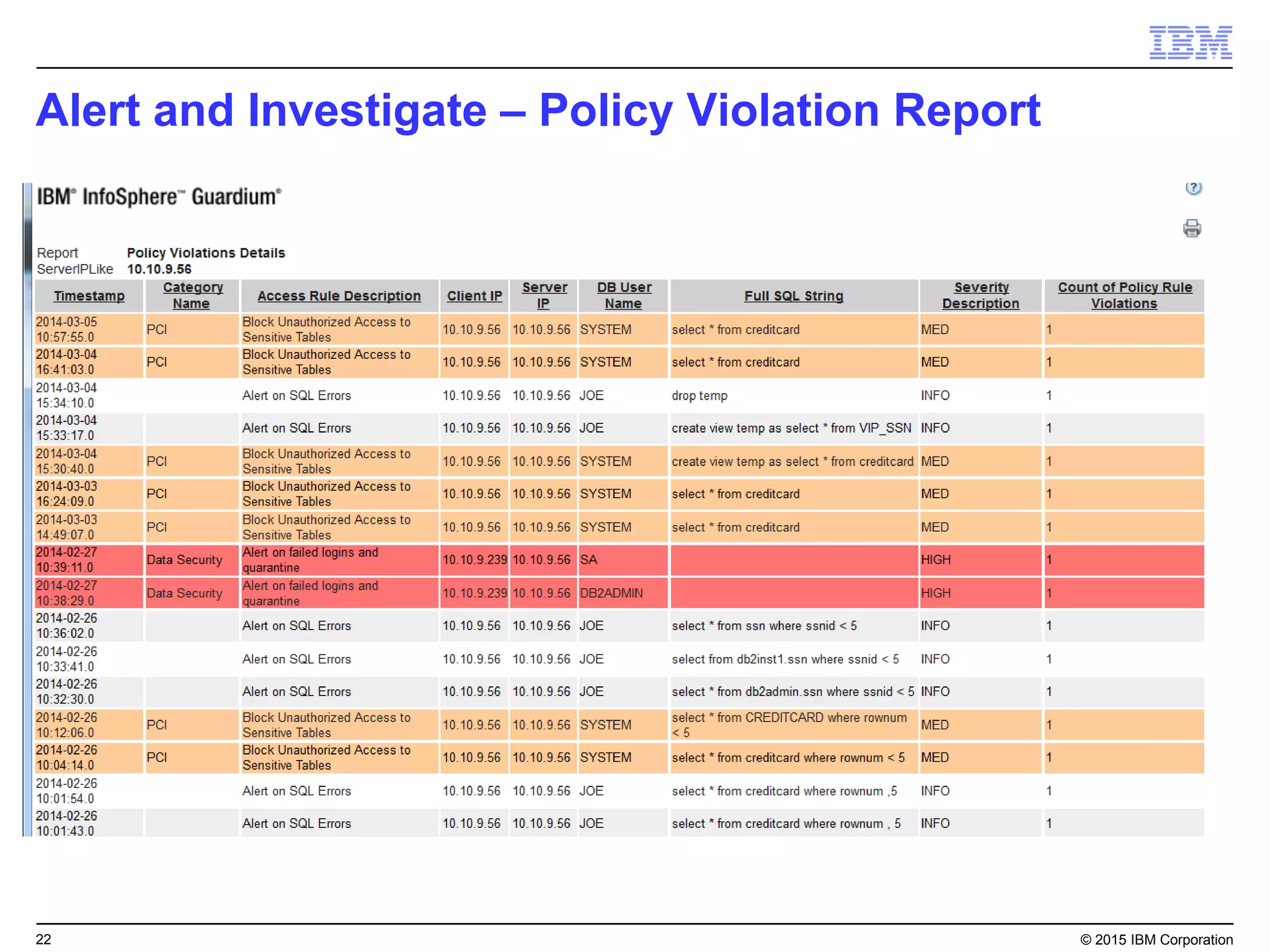
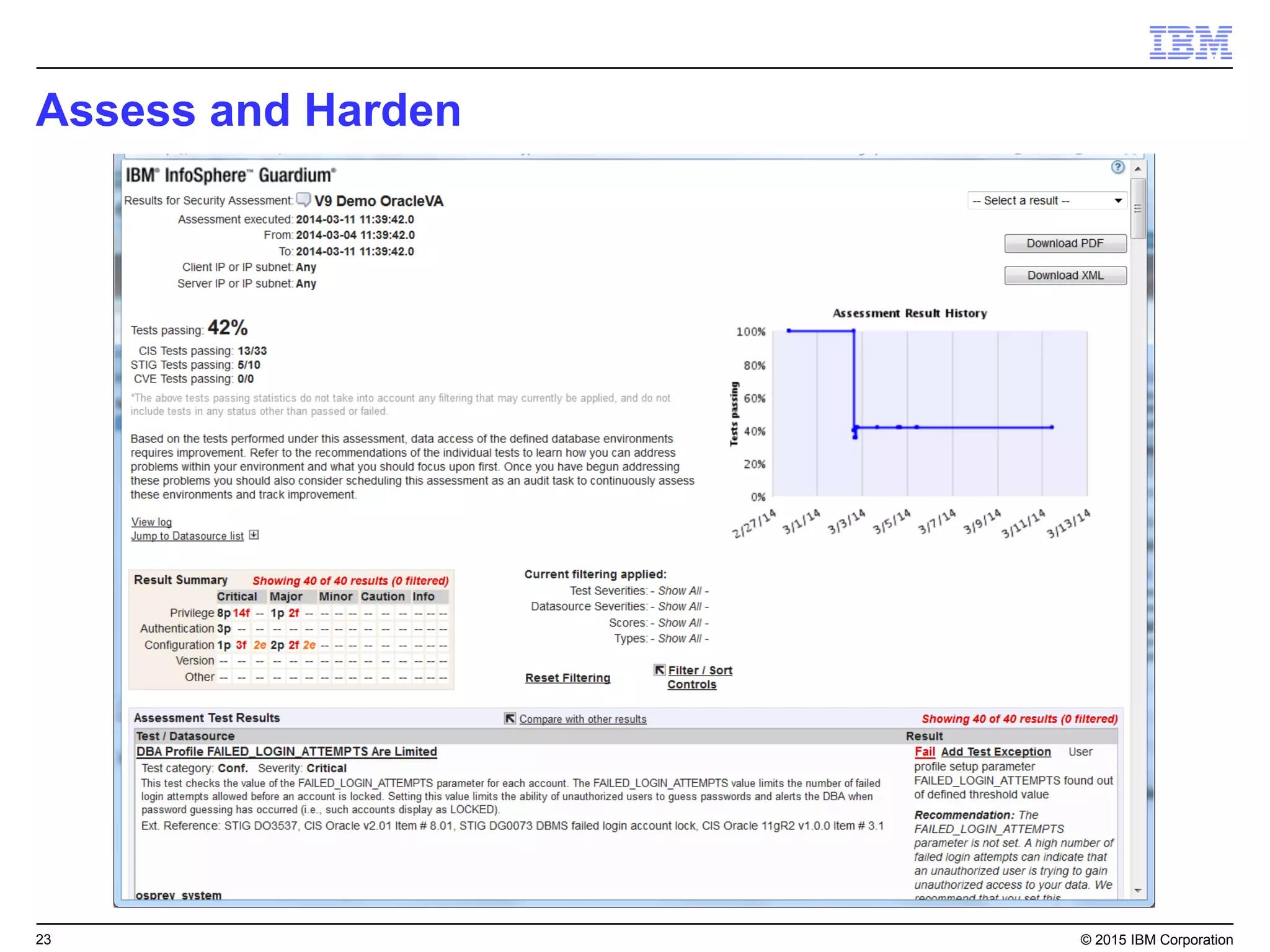
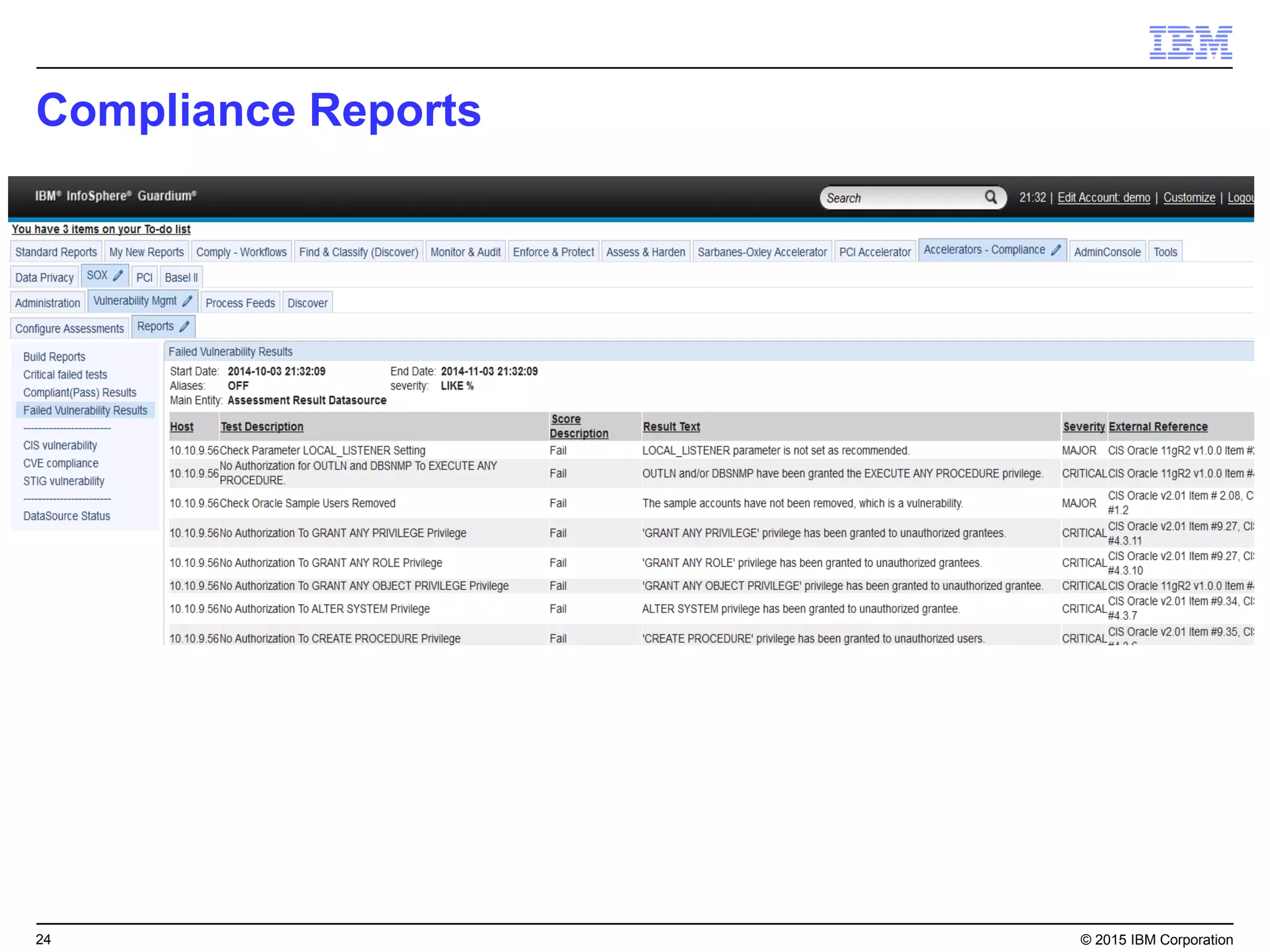
The document outlines IBM's security strategy focusing on bridging the gap between IT operations and security through IBM BigFix, which provides a comprehensive endpoint management solution. It addresses key security trends and challenges, such as visibility and compliance, while offering functionalities like discovery, patch management, incident response, and continuous monitoring. IBM BigFix aims to enhance security posture and reduce operational costs, leveraging a single intelligent agent for improved efficiency across diverse environments.