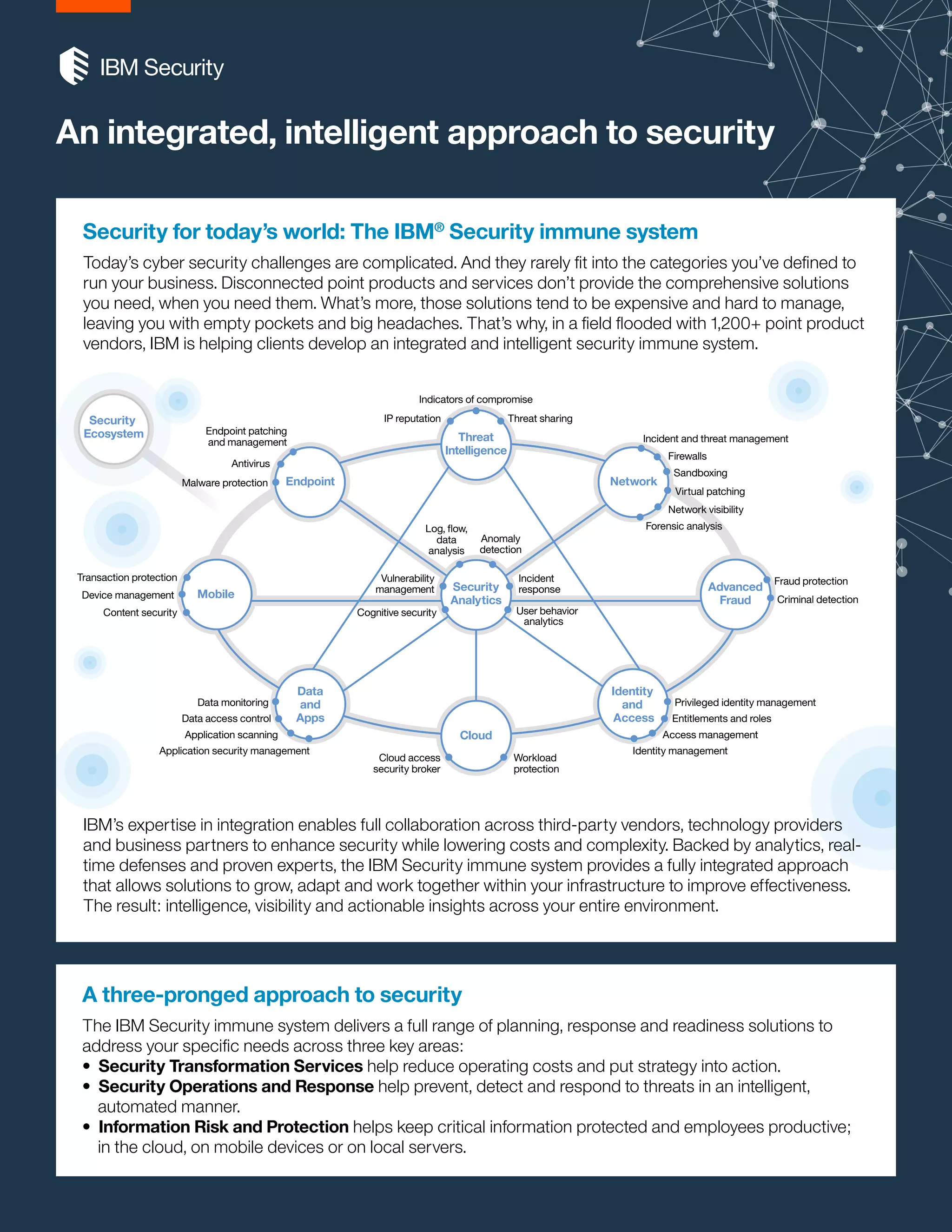
The IBM Security Immune System offers an integrated approach to cybersecurity, addressing the complexities of modern threats through a three-pronged strategy of security transformation, operations and response, and information risk management. This system emphasizes collaboration with third-party vendors and real-time analytics to enhance effectiveness while reducing costs. It leverages cognitive systems for data insights and an agile response to security challenges across various environments, including cloud and mobile.