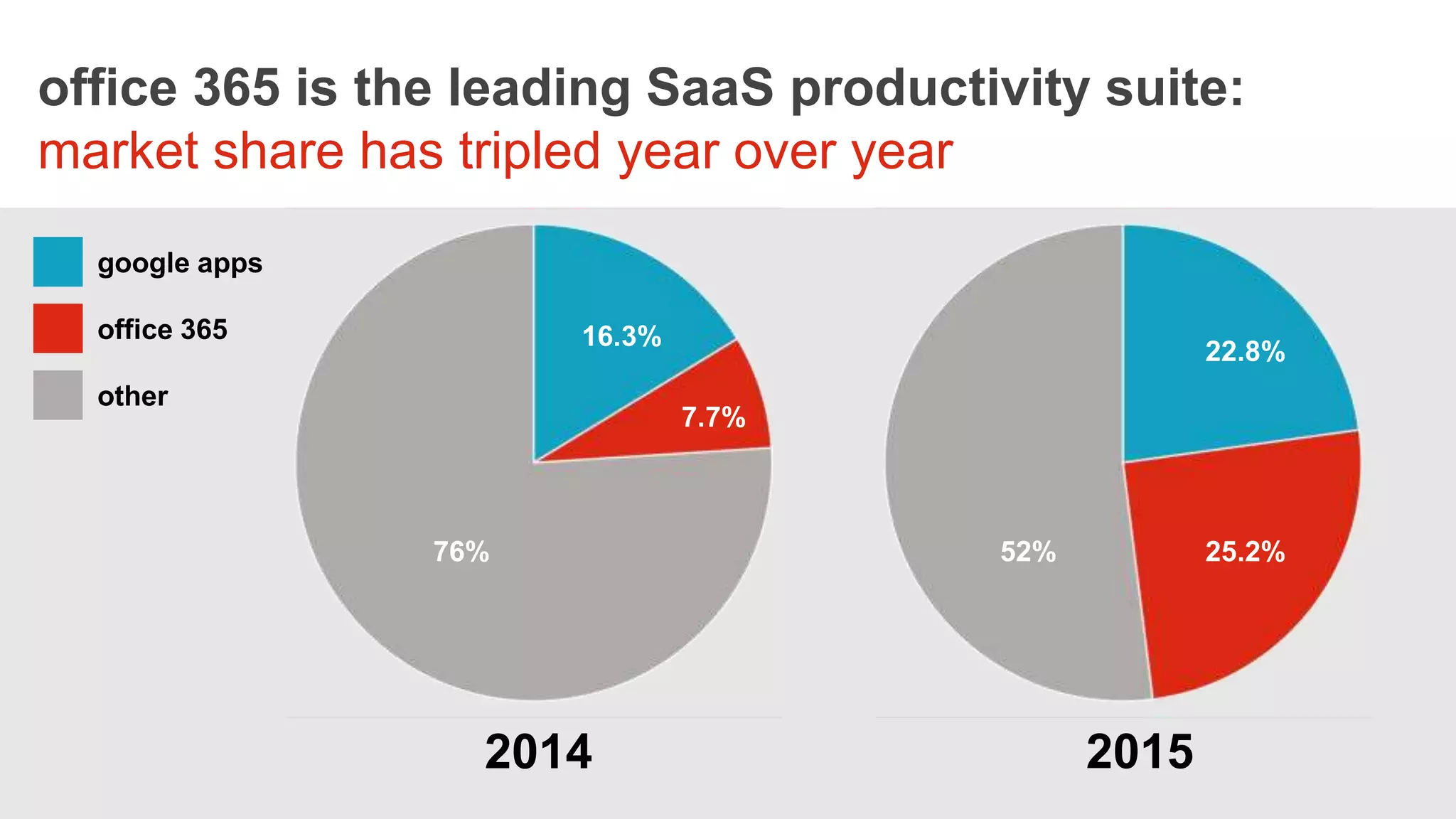
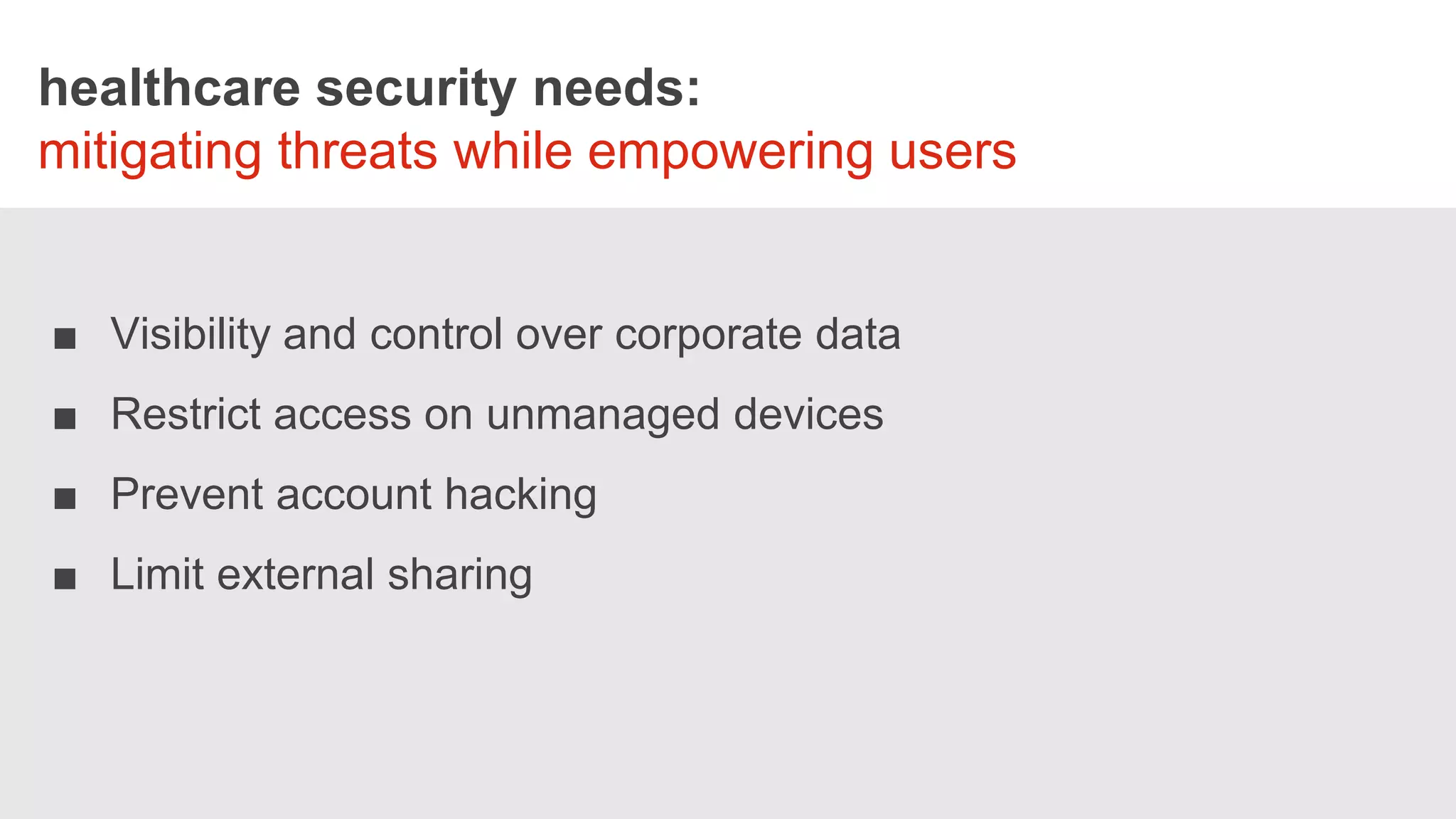
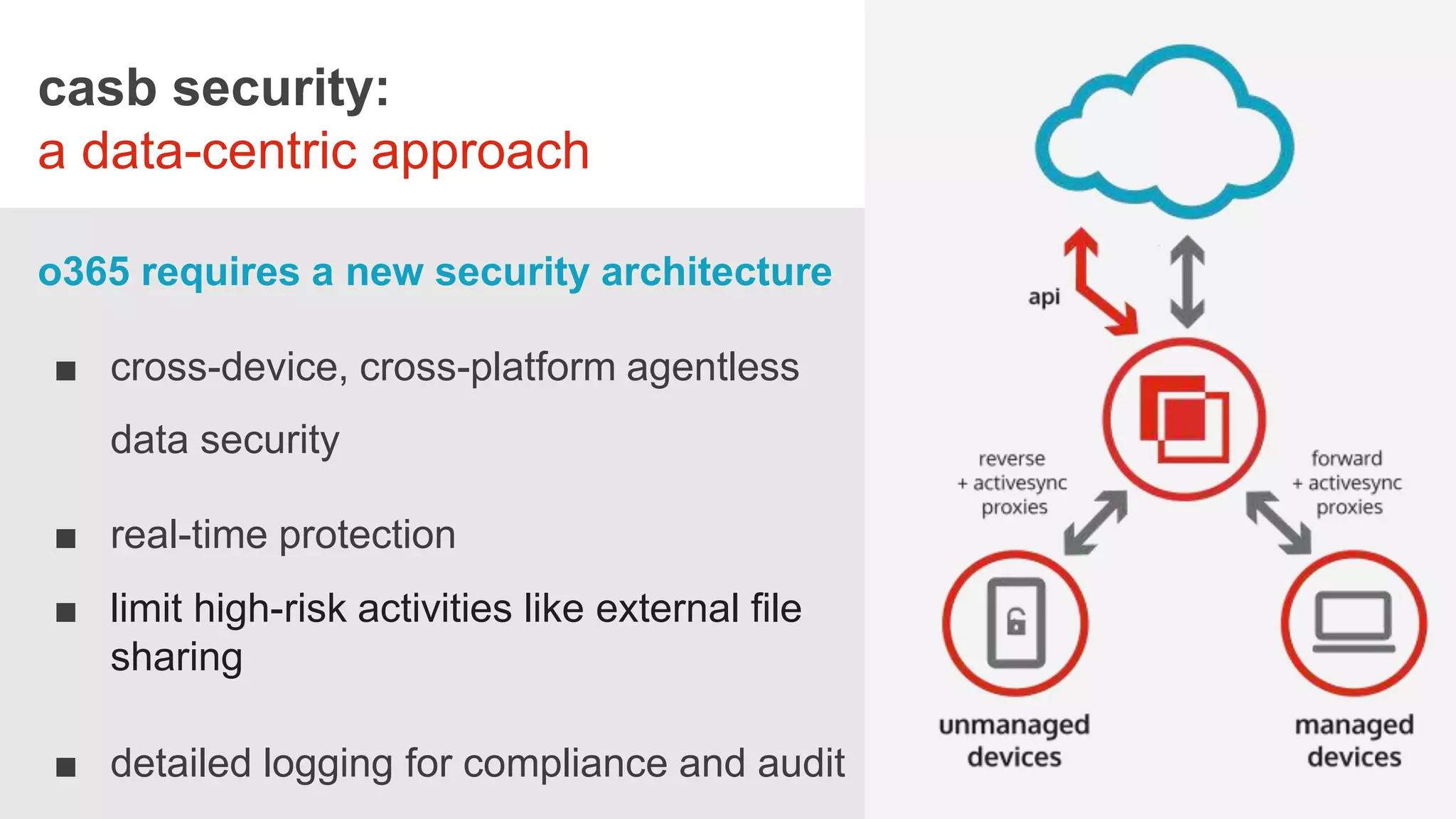
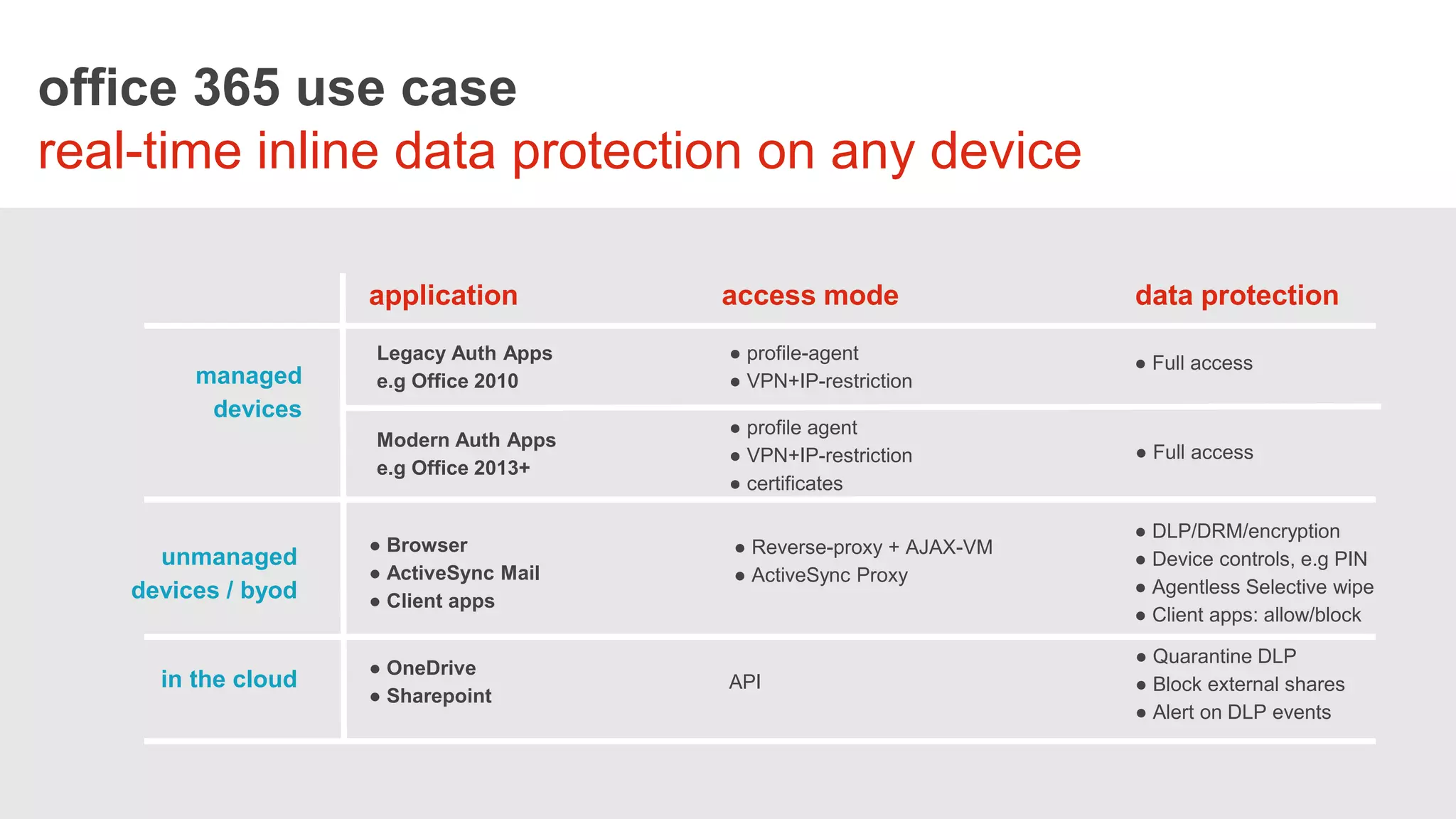
The webinar on August 17, 2016, discusses the challenges and needs of securing healthcare data in Office 365, emphasizing the limitations of its native security features. It highlights the importance of a comprehensive security approach, including data visibility and protection, especially concerning personal health information (PHI) and bring-your-own-device (BYOD) policies. Solutions suggested include implementing centralized identity management and data loss prevention (DLP) measures, along with the use of third-party security solutions to enhance protection across devices.