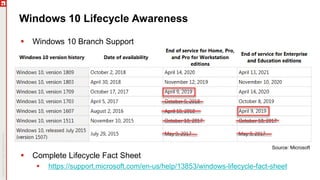
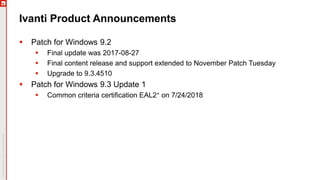
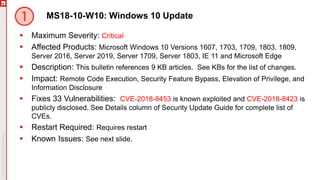
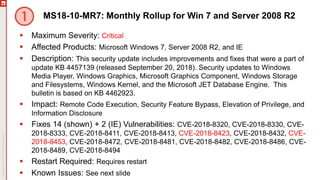
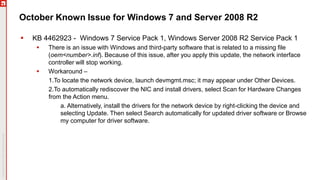
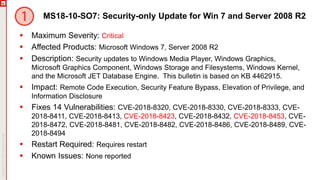
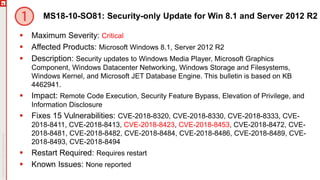
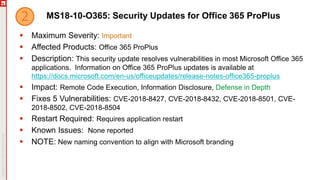
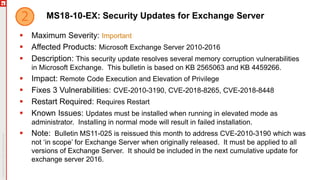
The document details an upcoming Patch Tuesday webinar scheduled for October 10, 2018, hosted by Brian Secrist and Todd Schell, which will cover an overview of the patch updates, recent news including a Google+ shutdown, and significant vulnerabilities in Microsoft products. It highlights key updates and security threats, including known issues related to Windows 10 and various vulnerabilities across different Windows versions, particularly concerning remote code execution and privilege escalation. Additionally, it provides insights on updating processes and security measures necessary for maintaining system integrity.




![New Microsoft Announcements
Server 2019 Released
https://cloudblogs.microsoft.com/windowsserver/2018/09/24/windows-server-
2019-announcing-general-availability-in-october/
Update released yesterday
Windows 10, Version 1809
Released October 2
https://techcommunity.microsoft.com/t5/Windows-IT-Pro-Blog/What-s-new-for-IT-
pros-in-Windows-10-version-1809/ba-p/263909
‘Paused’ October 6
Known Major Issues
Deletion of files in C:/Users/[username]/Documents/
Compatibility issue with Intel Display Audio device drivers
Incorrect CPU usage reported in Task Manager
New Latest Cumulative Update (LCU) update file](https://image.slidesharecdn.com/oct2018patchtuesdayivantifinal-181010212520/85/October-Patch-Tuesday-Analysis-2018-7-320.jpg)