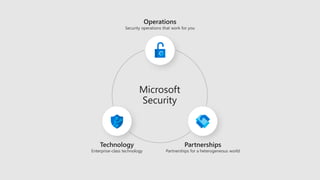
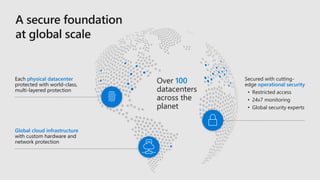
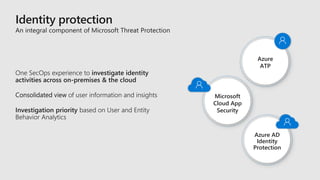
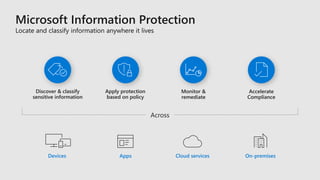
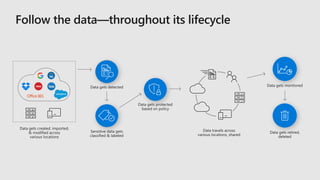
This document discusses how Microsoft's cloud security services help organizations be more secure. It provides an overview of Microsoft's security tools across threat protection, information protection, identity and access management, and security management. These include services like Azure Active Directory, Azure Security Center, Microsoft Threat Protection, and more. The document also emphasizes that Microsoft partners with other security vendors and organizations to provide a more comprehensive ecosystem of intelligent security solutions.