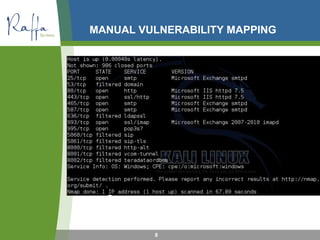
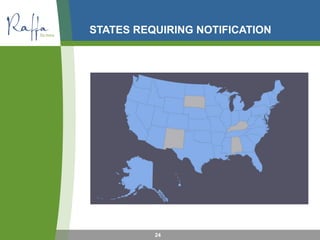
The document outlines an IT security training presented by Nate Solloway, covering key topics such as financial audit requirements, security risk definitions, and various security assessments. It emphasizes the importance of penetration testing, vulnerability mapping, and compliance with privacy laws, particularly in relation to personal data protection. Additionally, it highlights the necessity for organizations to implement security controls and maintain awareness of potential vulnerabilities and threats.