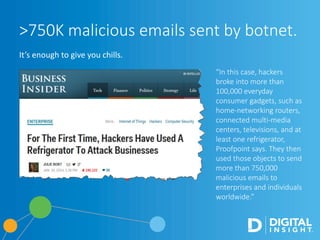
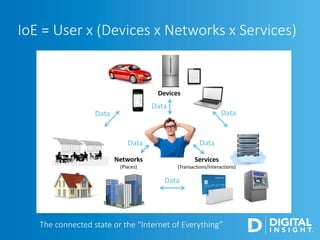
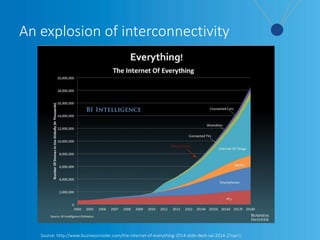
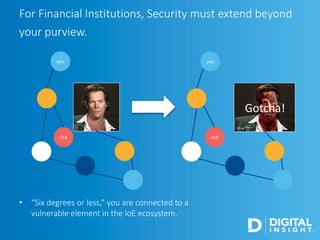
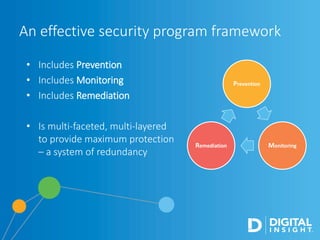
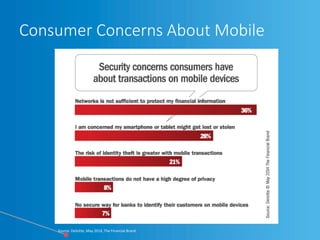
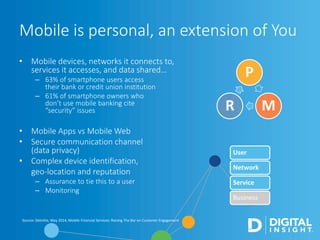
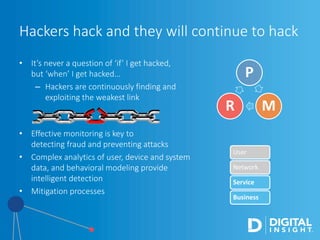
The webinar, led by Alan Akahoshi, discusses the challenges and strategies for security and compliance in the context of the Internet of Everything, emphasizing the importance of multi-layered security protocols and compliance with federal guidelines like the FFIEC. Key points include the rise in cyber threats, especially through connected devices, and the need for financial institutions to adopt more robust security measures, including identity verification and customer education. Emphasis is placed on balancing security with user experience while ensuring effective client protection against potential fraud and data breaches.