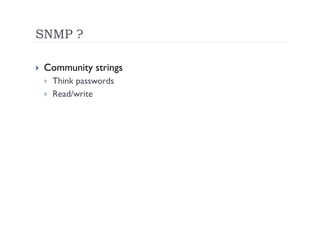
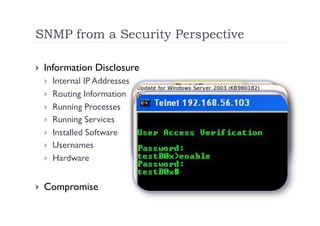
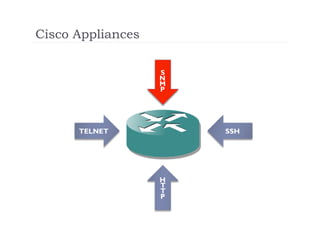
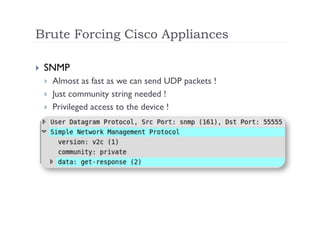
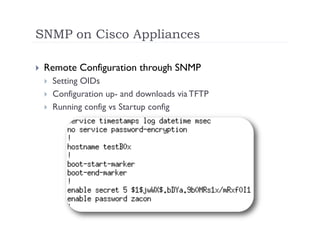
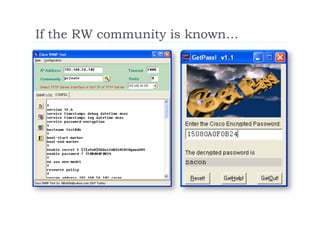
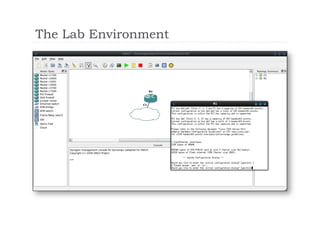
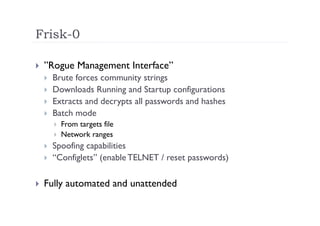
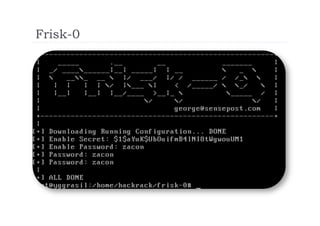
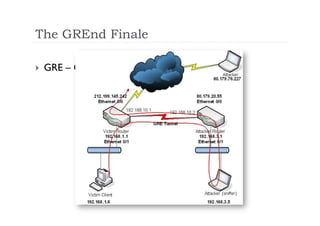
The document discusses the vulnerabilities of the Simple Network Management Protocol (SNMP) in Cisco devices, highlighting its use for network monitoring and management. It outlines potential security risks, including information disclosure and exploitation through misconfigurations, particularly focusing on weak community strings. The document also introduces a tool called Frisk-0 for exploiting these vulnerabilities and offers recommendations for securing SNMP-enabled devices.