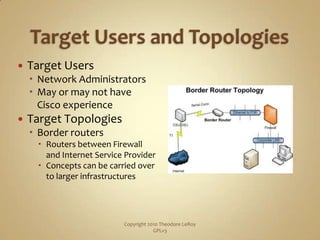
The BRST (Border Router Security Tool) is a web-based utility that asks questions and generates a secure configuration for border routers. It disables unneeded services, enables helpful ones like SSH, controls access, and configures anti-spoofing and logging. An example shows using the BRST to harden a Cisco router, closing ports revealed in an initial Nmap scan. The resulting configuration locks down services, access, and logging while enabling features like SSH and TCP keepalives.