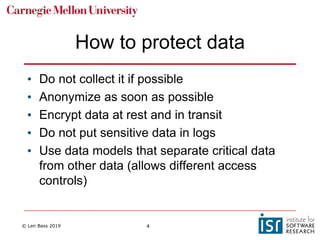
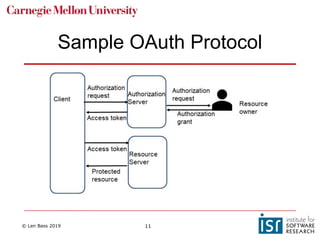
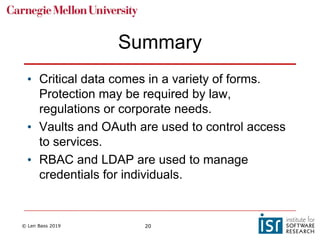
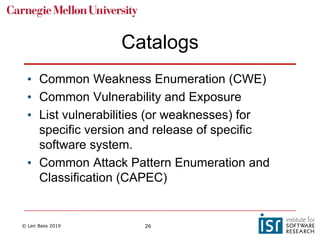
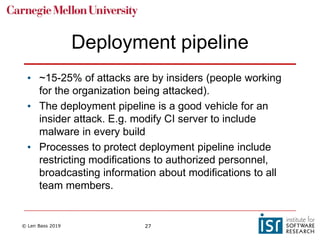
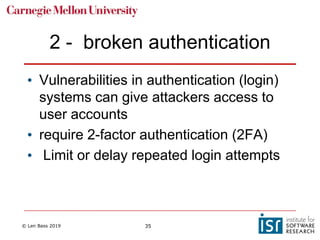
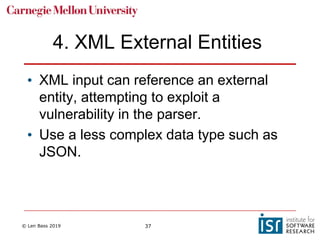
The document discusses securing software supply chains and operations. It covers identifying critical data and resources to protect, such as credentials, sensitive data, and hardware. Techniques for protection include encryption, access controls, and input validation. OAuth and vaults are described for managing credentials for services, while RBAC and LDAP help control individual access. Regularly patching vulnerabilities is important, but the process can be complex. The OWASP Top 10 list catalogs common web application security risks and mitigations.