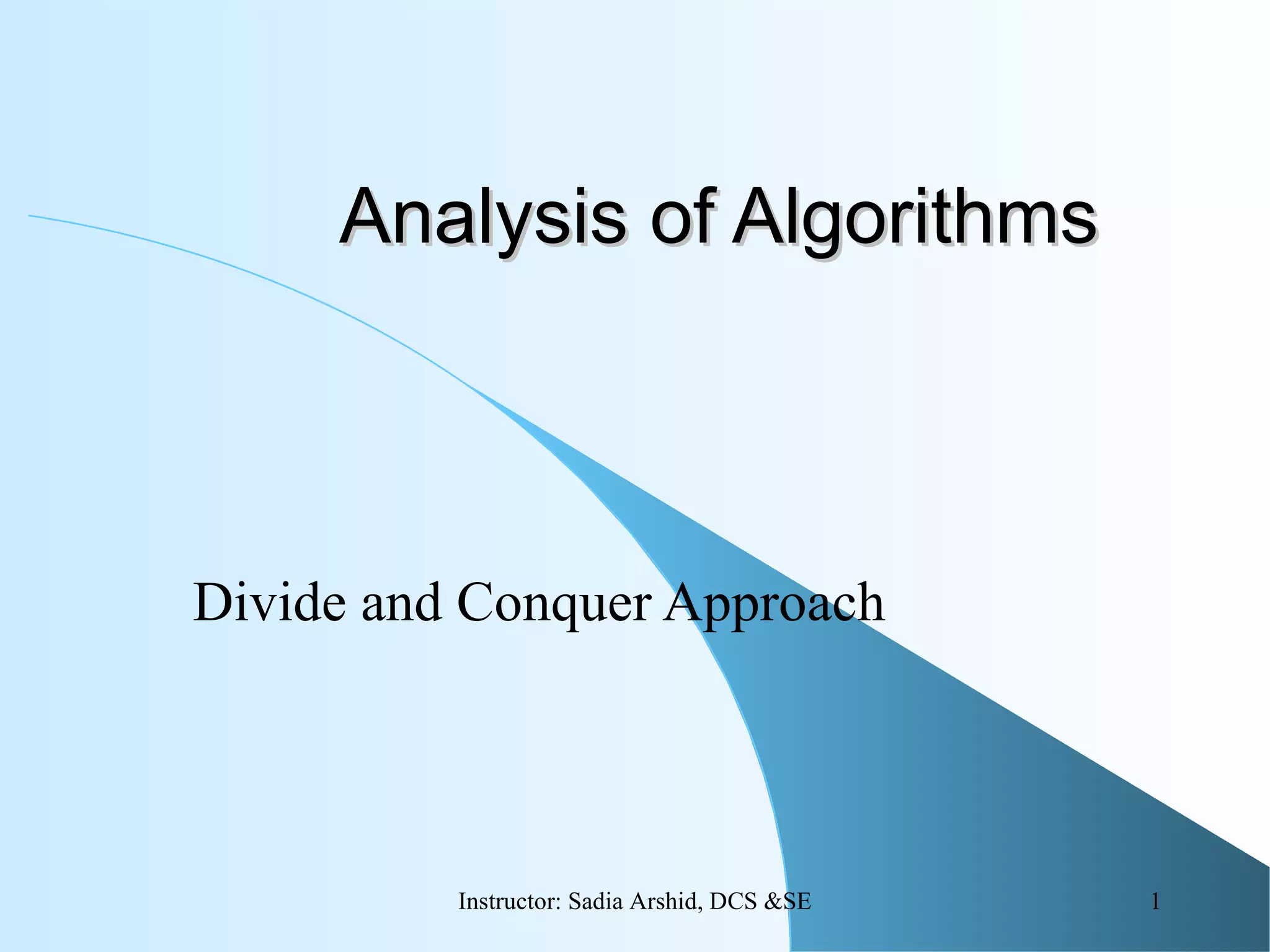
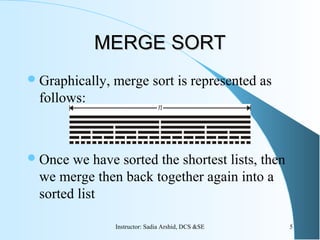
The document discusses the merge sort algorithm. It explains that merge sort uses a divide and conquer approach by recursively dividing an array into smaller sub-problems until single elements are reached, then merging the sorted sub-arrays back together into a fully sorted array. The time complexity of merge sort is O(n log n) as it divides the problem space in half at each step and requires linear time to merge the sub-arrays. While efficient, merge sort requires additional storage space proportional to n log n to perform the sorting in place.




![Merge Sort AlgorithmMerge Sort Algorithm
procedure MergeSort(n,s)
h=n/2, m=n-h
u=array[1..h], v=array[m..n]
if n>1
copy s[1] through s[h] to u
copy s[h+1] through s[n] to v
mergesort(h,u)
mergesort(m,v)
merge(h,m,u,v,s] 7Instructor: Sadia Arshid, DCS &SE](https://image.slidesharecdn.com/05-dc1-150601060842-lva1-app6891/85/05-dc1-7-320.jpg)
![procedure merge(h,m,u,v,s)
i=1,j=1,k=1
while i<=h and j<=m
if u[i]<v[j]
s[k]=u[i], i=i+1
else s[k]=v[j],j=j+1
k=k+1
if i>h
copy v[j] through v[m] to s[k] through s[h+m]
else
copy u[i] through u[h] to s[k] through s[h+m]
8Instructor: Sadia Arshid, DCS &SE](https://image.slidesharecdn.com/05-dc1-150601060842-lva1-app6891/85/05-dc1-8-320.jpg)
![Merge Sort AnalysisMerge Sort Analysis
T(n)=T[h]+T[m]+complexity of merge
Complexity of merge: worst case, h+m-1
Suppose n is a power of two, so that we always split
into even halves.
– h=n/2, m=n-n/2=n/2
– w(n)=w[n/2]+w[n/2]+n-1
For n = 1 the time to merge sort is1 otherwise
The time to merge sort n numbers is equal to the
time to do two recursive merge sorts of size n/2, plus
the time to merge, which is linear.
Solve this recurrence to find out running time. 10Instructor: Sadia Arshid, DCS &SE](https://image.slidesharecdn.com/05-dc1-150601060842-lva1-app6891/85/05-dc1-10-320.jpg)
![w(1) = 0
w(n) = 2w(n/2) + n-1
W[n]=2w[n/2]+n-1
W[n/2]=2w[n/4]+n/2-1
W[n/4]=2w[n/8]+n/4-1
By backward substitution
W[n]=2(2w(n/4)+n/2-1)+n-1
=22
w(n/4)+n-2+n-1
=22
(2w(n/8)+n/4-1)+n-2+n-1
=23
w[n/8]+n-22
+n-2+n-1
11Instructor: Sadia Arshid, DCS &SE](https://image.slidesharecdn.com/05-dc1-150601060842-lva1-app6891/85/05-dc1-11-320.jpg)
![ By generalizing equation
=2i
w[n/2i
]+in-2i-1
-2i-2
-…..-20
=2i
w[n/2i
]+in-(2i
-1)
By taking n=2i
=nw[n/n]+nlgn-(n-1)
=nlgn-(n-1)єO(nlgn)
12Instructor: Sadia Arshid, DCS &SE](https://image.slidesharecdn.com/05-dc1-150601060842-lva1-app6891/85/05-dc1-12-320.jpg)
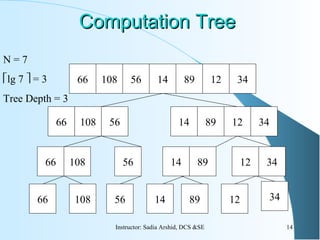

![Other version of MERGEOther version of MERGE
SORTSORT
procedure MergeSort2(low,high,n,s)
if low<high
mid=(low+high)/2
mergesort2(low,mid)
mergesort2(mid+1,high)
merge2(low,mid,high]
16Instructor: Sadia Arshid, DCS &SE](https://image.slidesharecdn.com/05-dc1-150601060842-lva1-app6891/85/05-dc1-16-320.jpg)
![procedure merge2(low,mid,high)
i=low,j=mid,h=low
while h<=mid and j<=high
if s[h]<s[j]
u[i]=s[h], h=h+1
else u[i]=s[j], j=j+1
i=i+1
if i>h
copy s[h] through s[mid] to u[i] to u[high]
else
copy s[j] through s[high] to u[i] to u[high]
17Instructor: Sadia Arshid, DCS &SE](https://image.slidesharecdn.com/05-dc1-150601060842-lva1-app6891/85/05-dc1-17-320.jpg)
