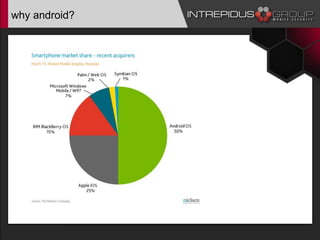
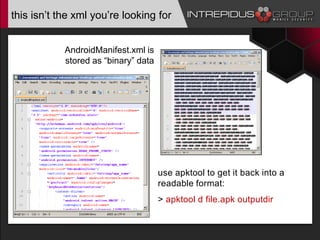
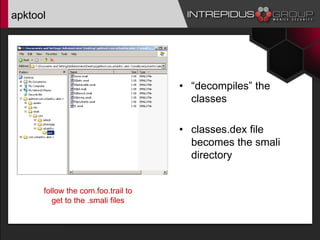
The document is a presentation by Jason Ross on Android malware analysis, highlighting the increasing prevalence and complexity of Android malware and the challenges it poses for security. It provides insights into various tools and methods for analyzing malware, including network, runtime, and static analysis techniques. Additionally, it discusses the importance of understanding mobile security in the context of corporate environments and presents a range of resources for effective malware analysis.



















![End
• contact info:
@rossja
jason.ross [at] intrepidusgroup [dot] com](https://image.slidesharecdn.com/androidmalwareanalysis-170117171256/85/Android-malware-analysis-38-320.jpg)