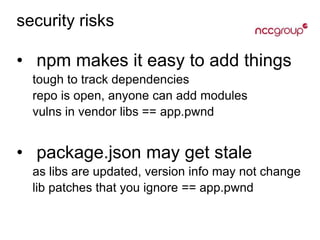
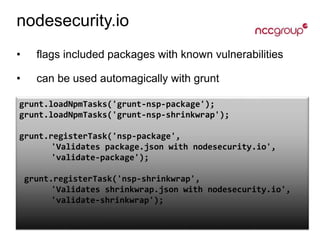
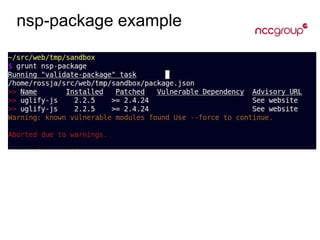
The document provides an overview of Node.js, a JavaScript runtime built on Google's V8 engine, emphasizing its non-blocking I/O model and its role as an application server, distinct from web frameworks. It discusses various frameworks like Express.js, Koa, and Hapi, along with their functionalities, and highlights security risks associated with npm dependencies. Additionally, it mentions security tools like Helmet.js and nodesecurity.io for enhancing application safety through various protective measures.