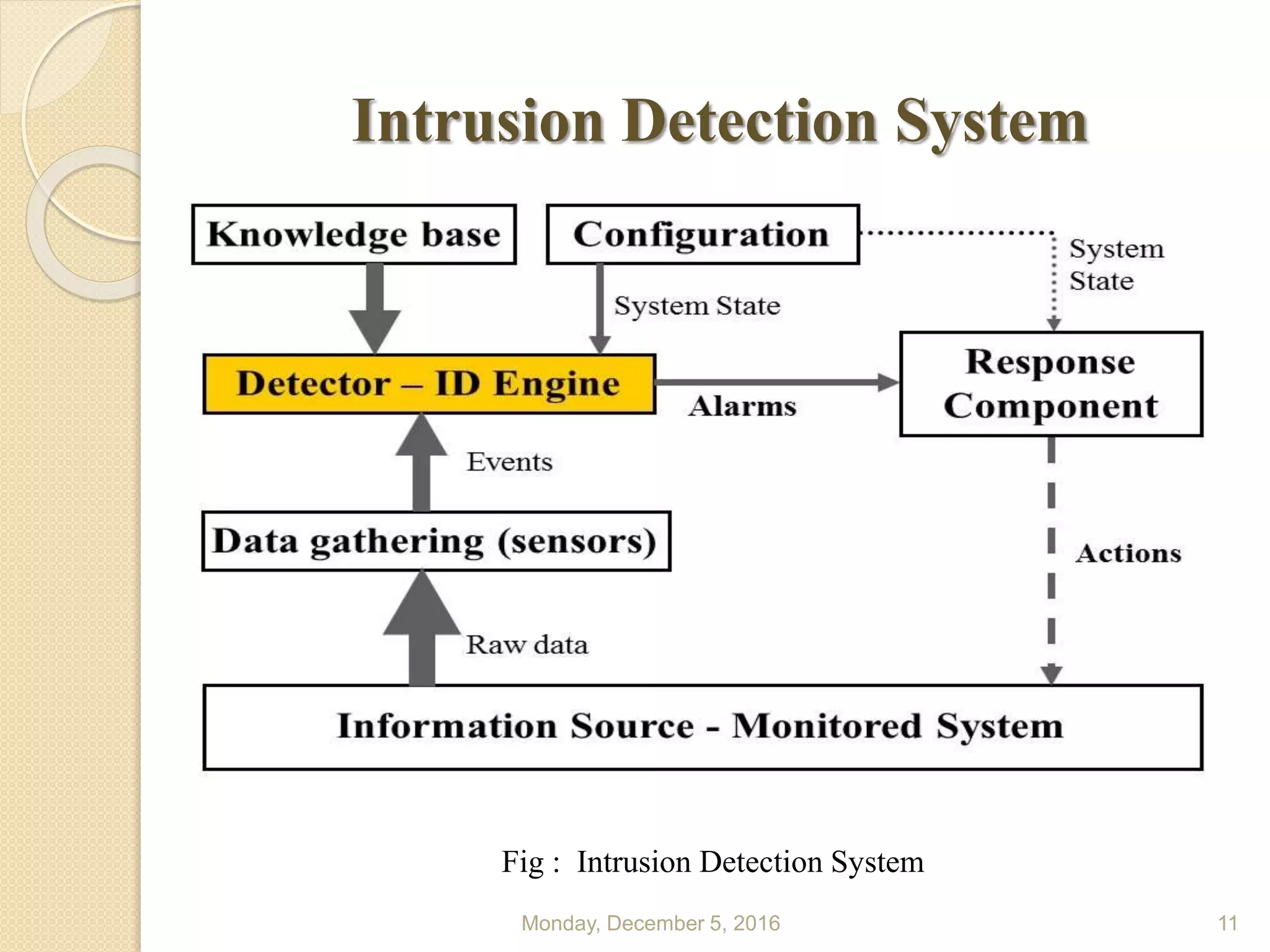
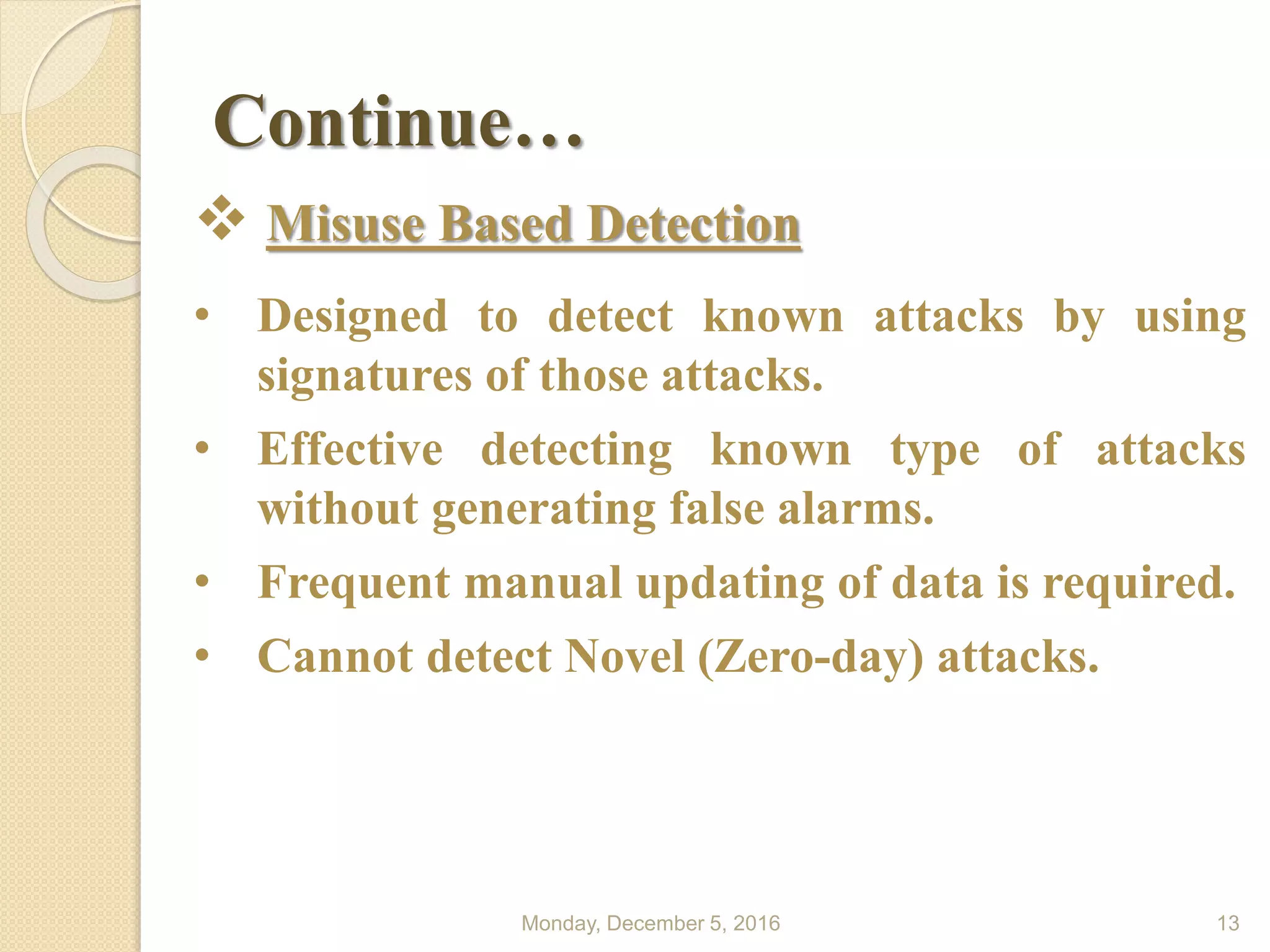
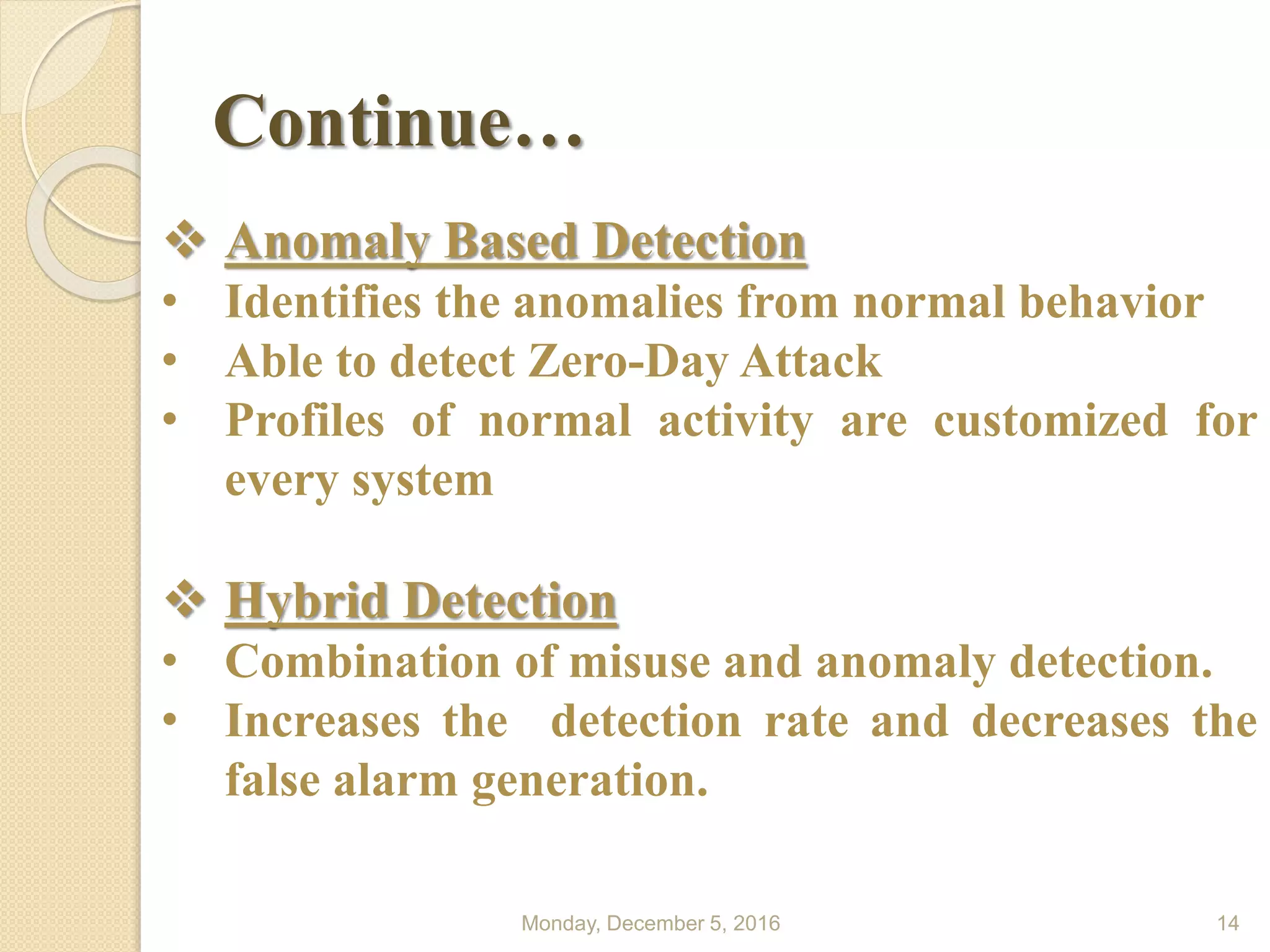
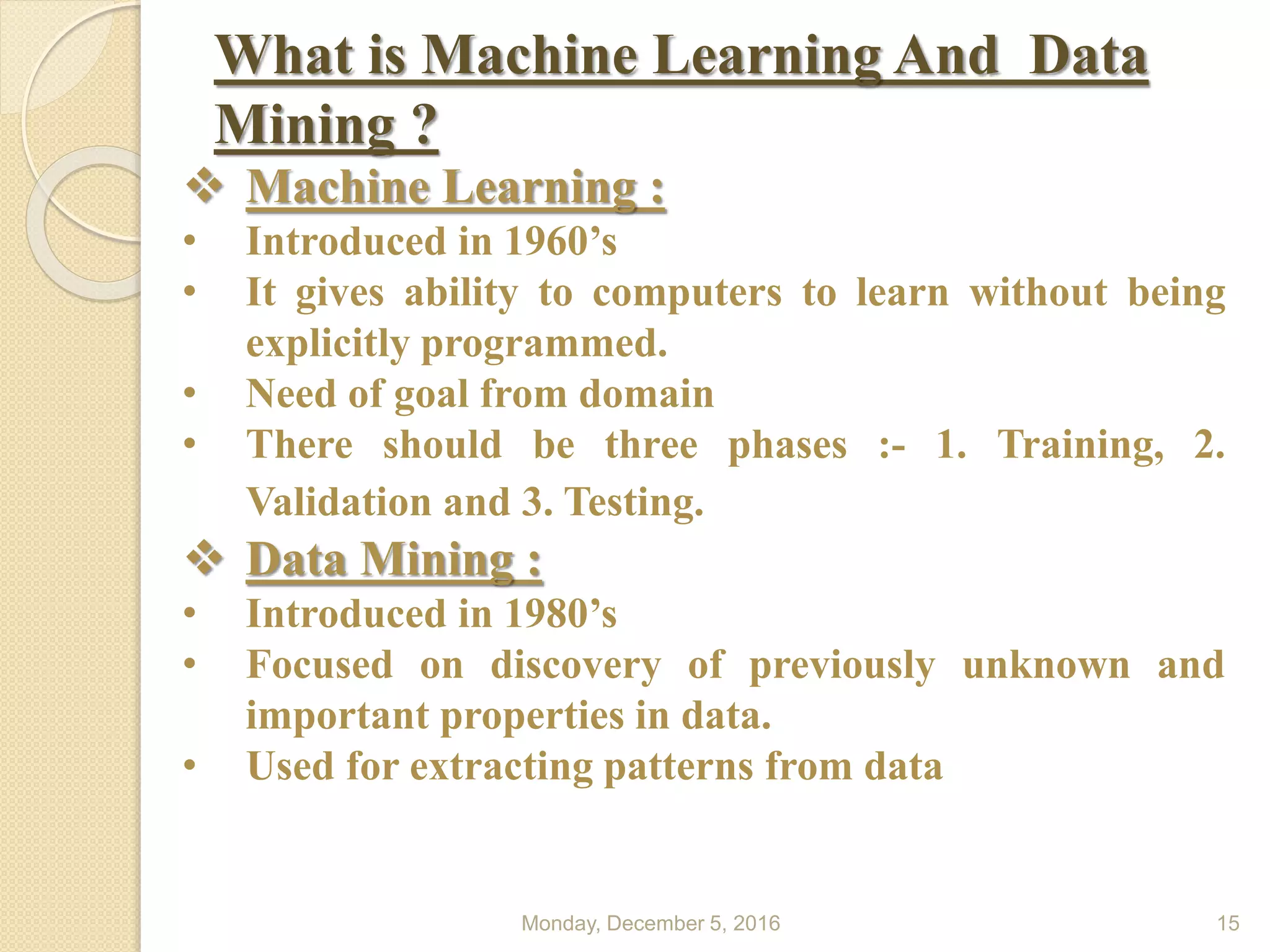
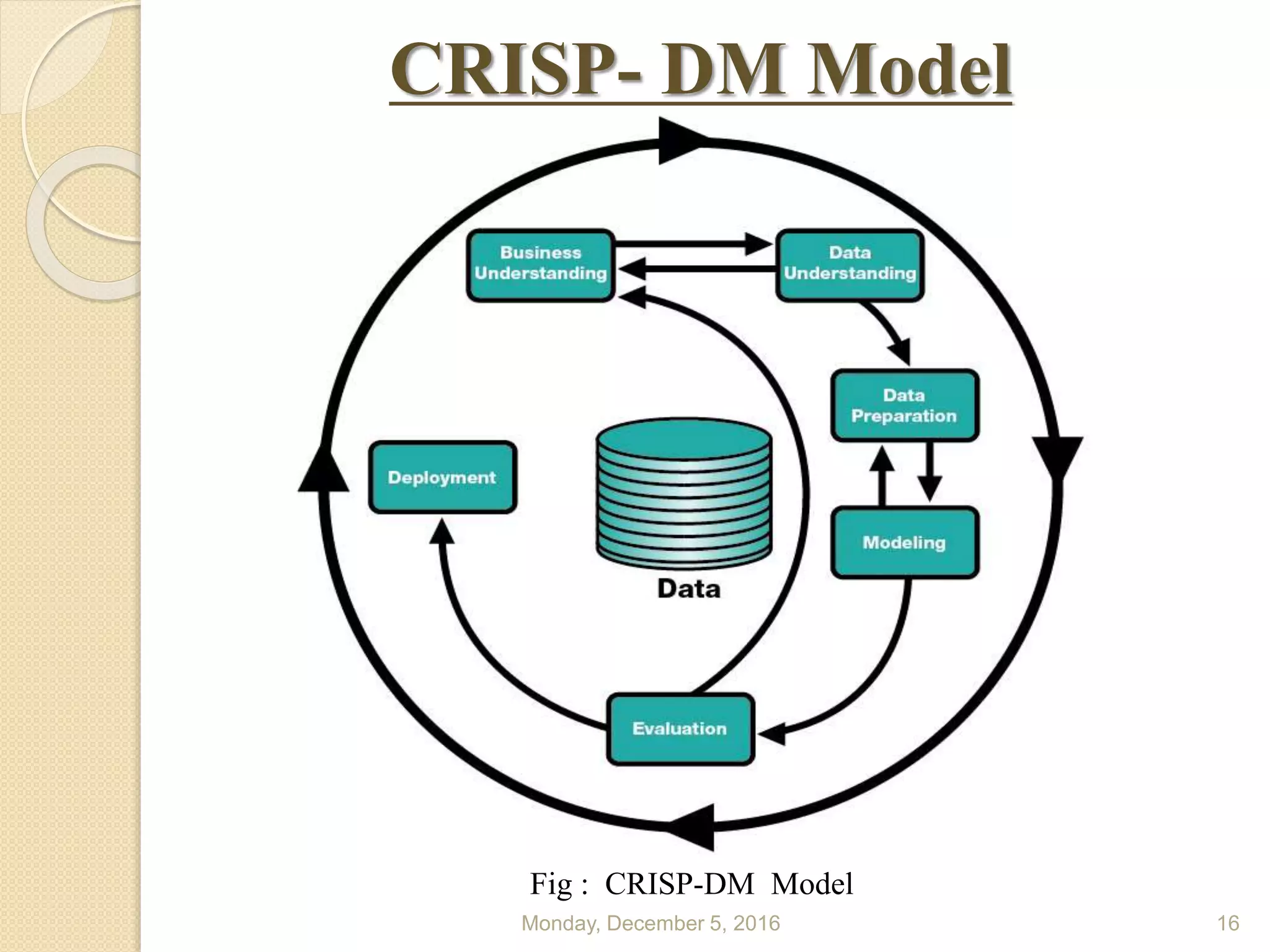
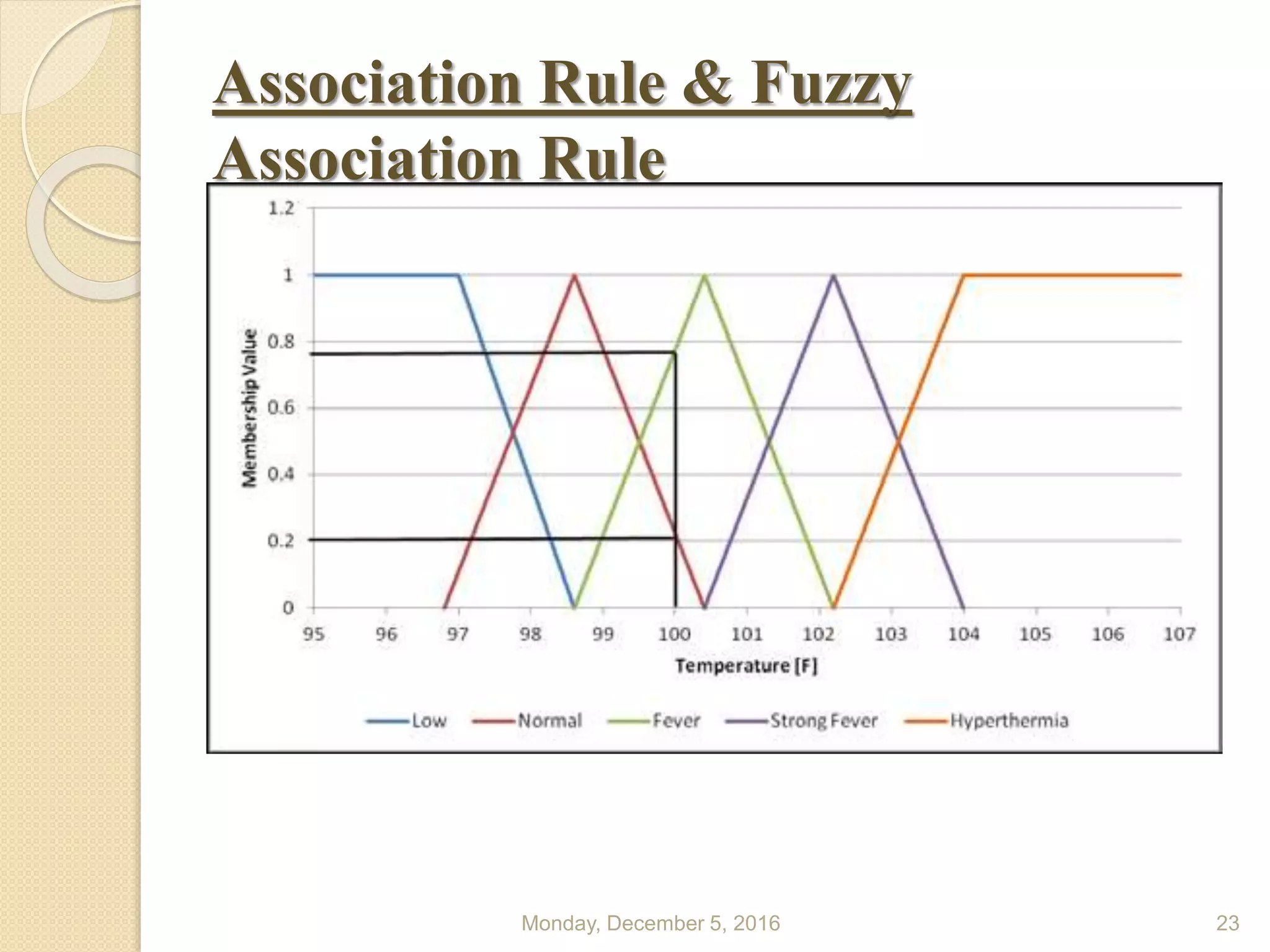
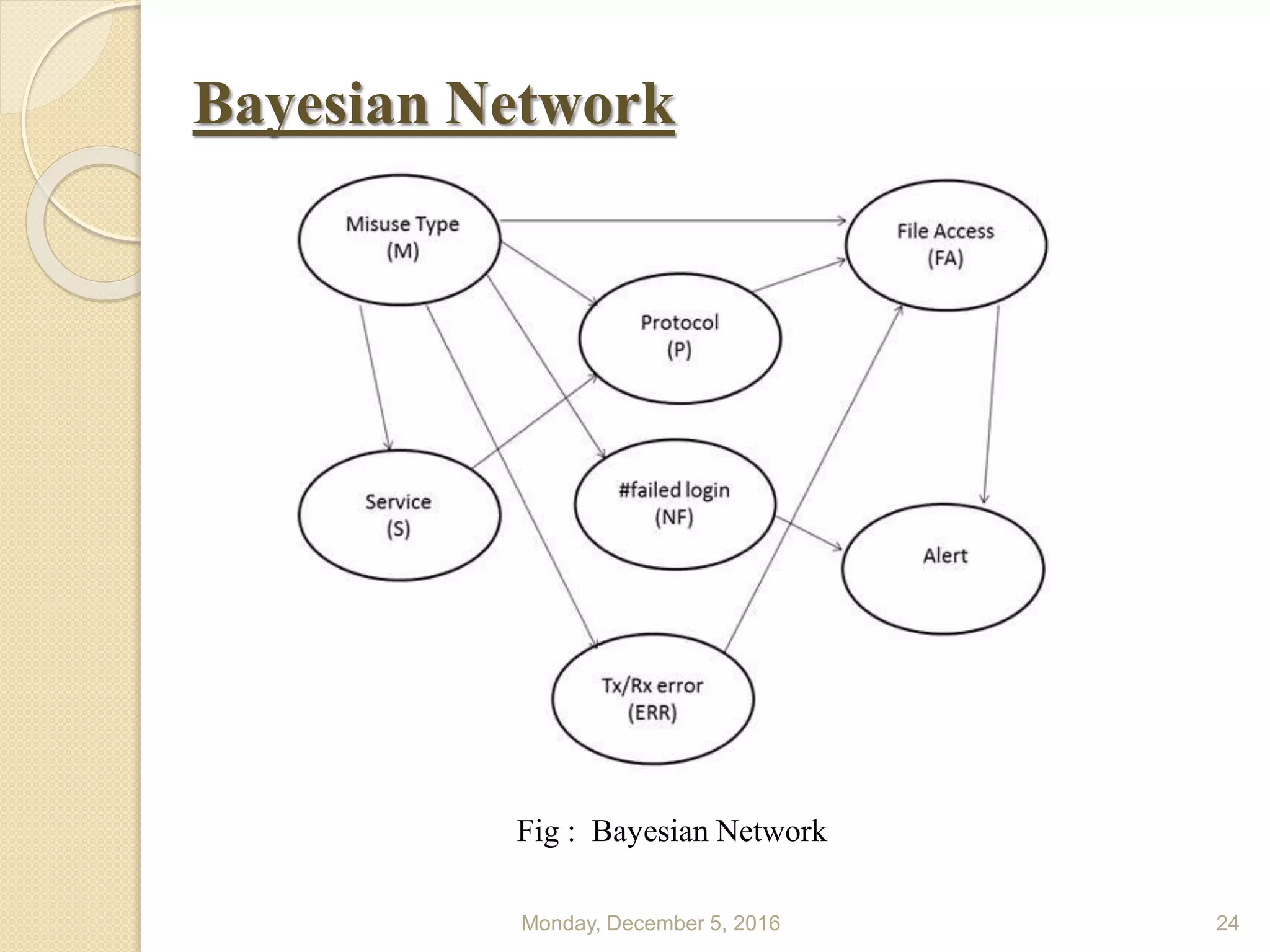
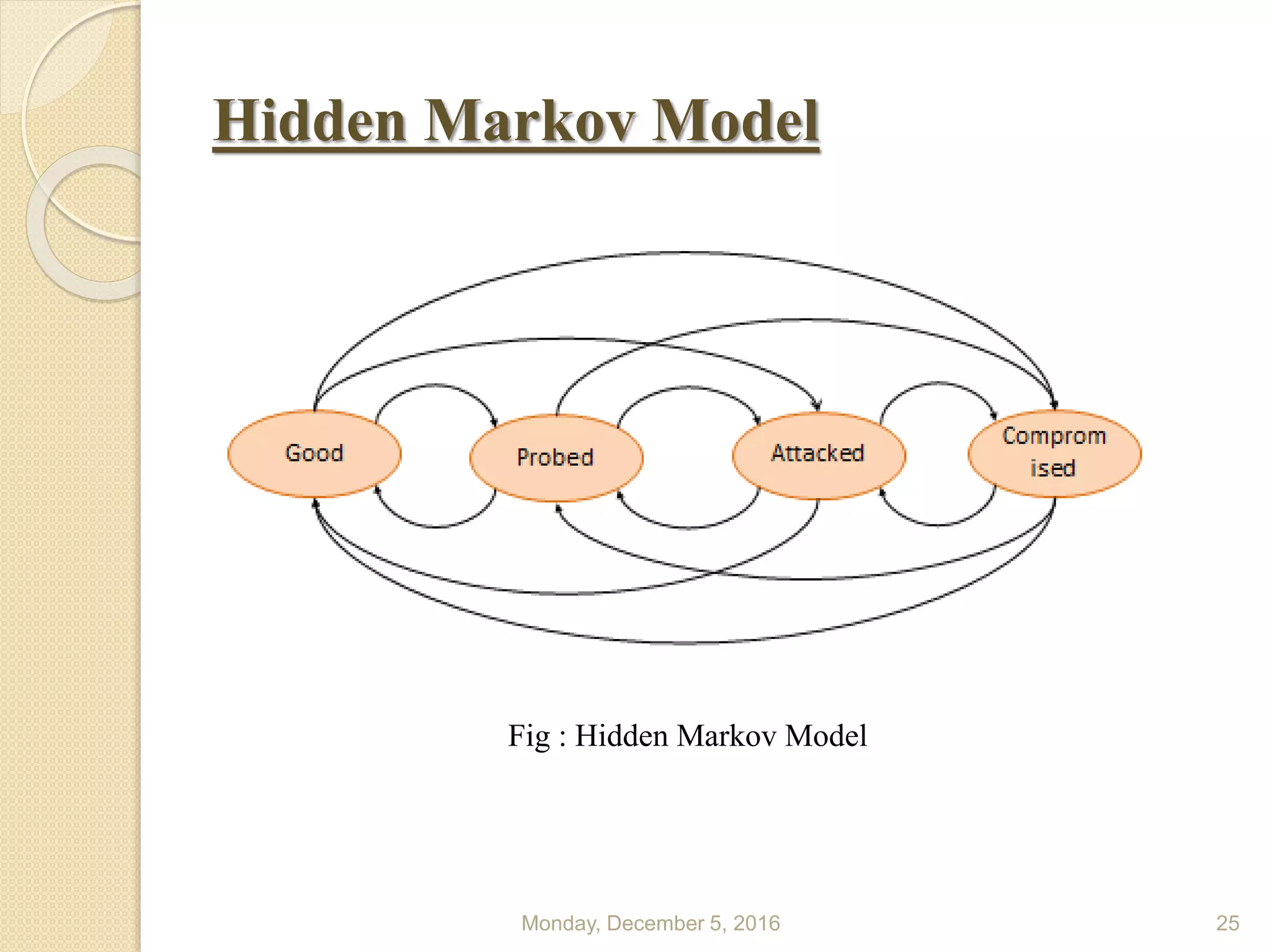
This document presents a seminar on using data mining and machine learning methods for cyber security and intrusion detection, highlighting the importance of these technologies in protecting against cyber attacks. It covers various types of intrusion detection systems, including misuse-based, anomaly-based, and hybrid approaches, along with a literature review of existing research in this area. The seminar concludes with recommendations for applying machine learning and data mining techniques effectively in cyber security.