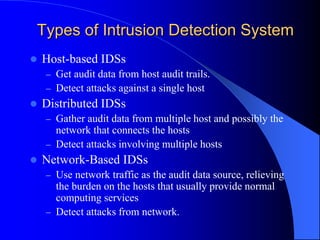
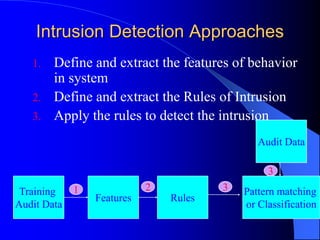
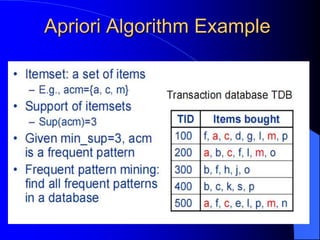
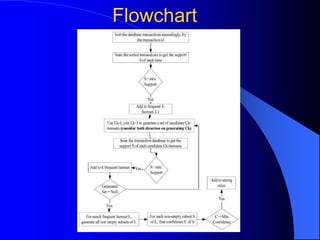
The document discusses intrusion detection systems (IDS) using a data mining approach, classifying them into host-based, distributed, and network-based systems. It explains the detection techniques of misuse and anomaly detection along with the apriori algorithm for generating rules from data patterns. The document also cites multiple references related to intrusion detection methodologies.