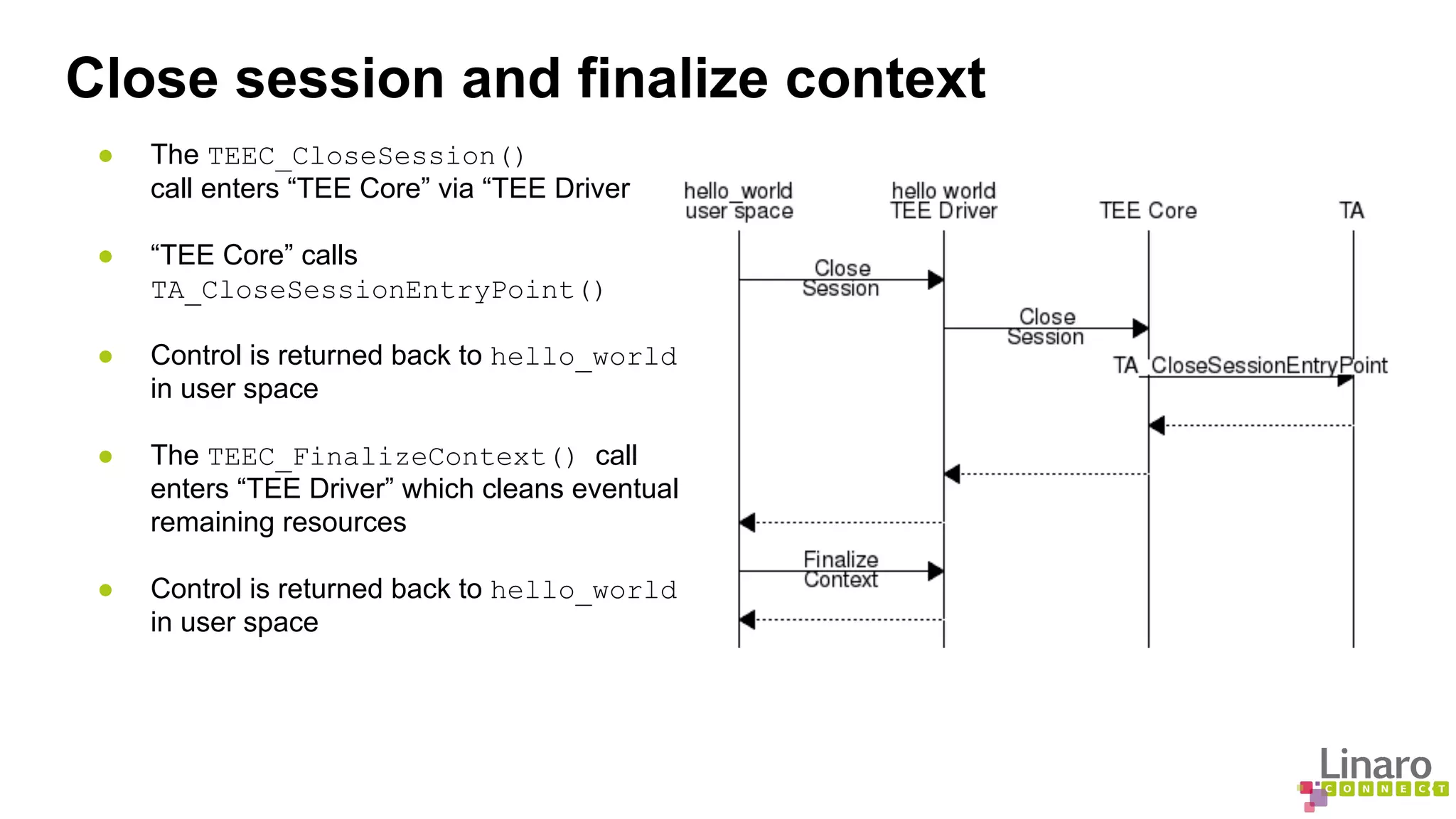
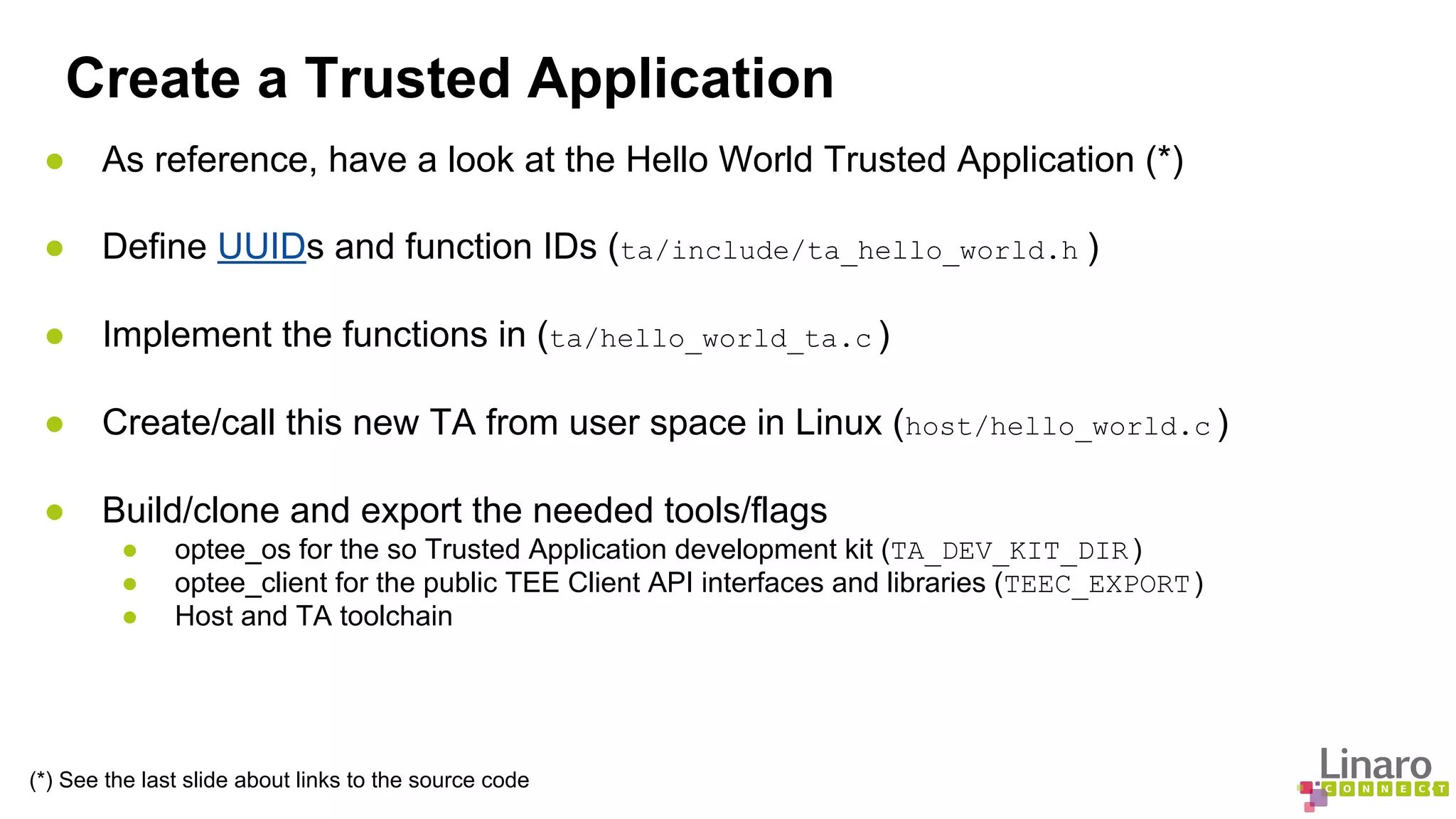
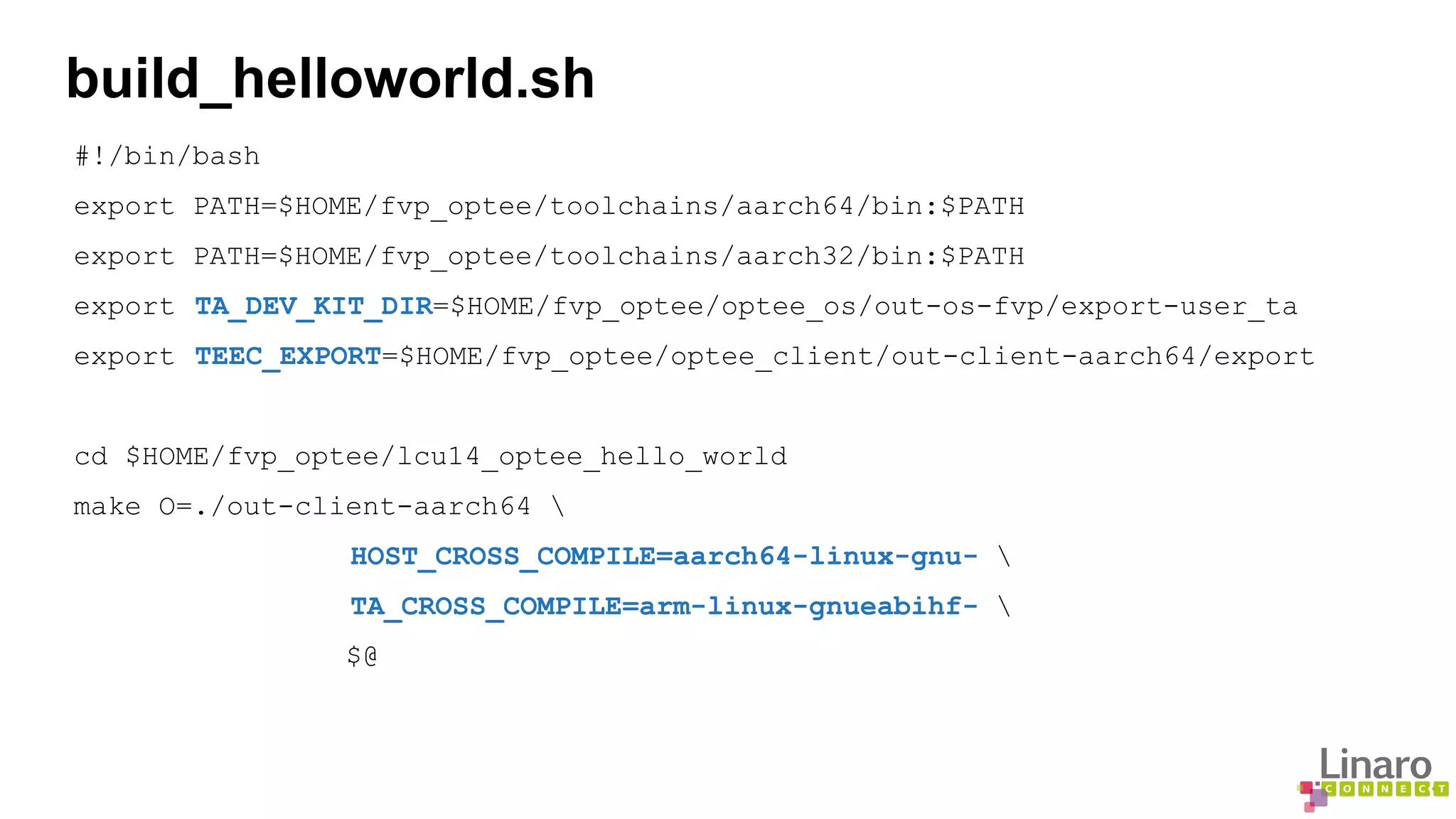
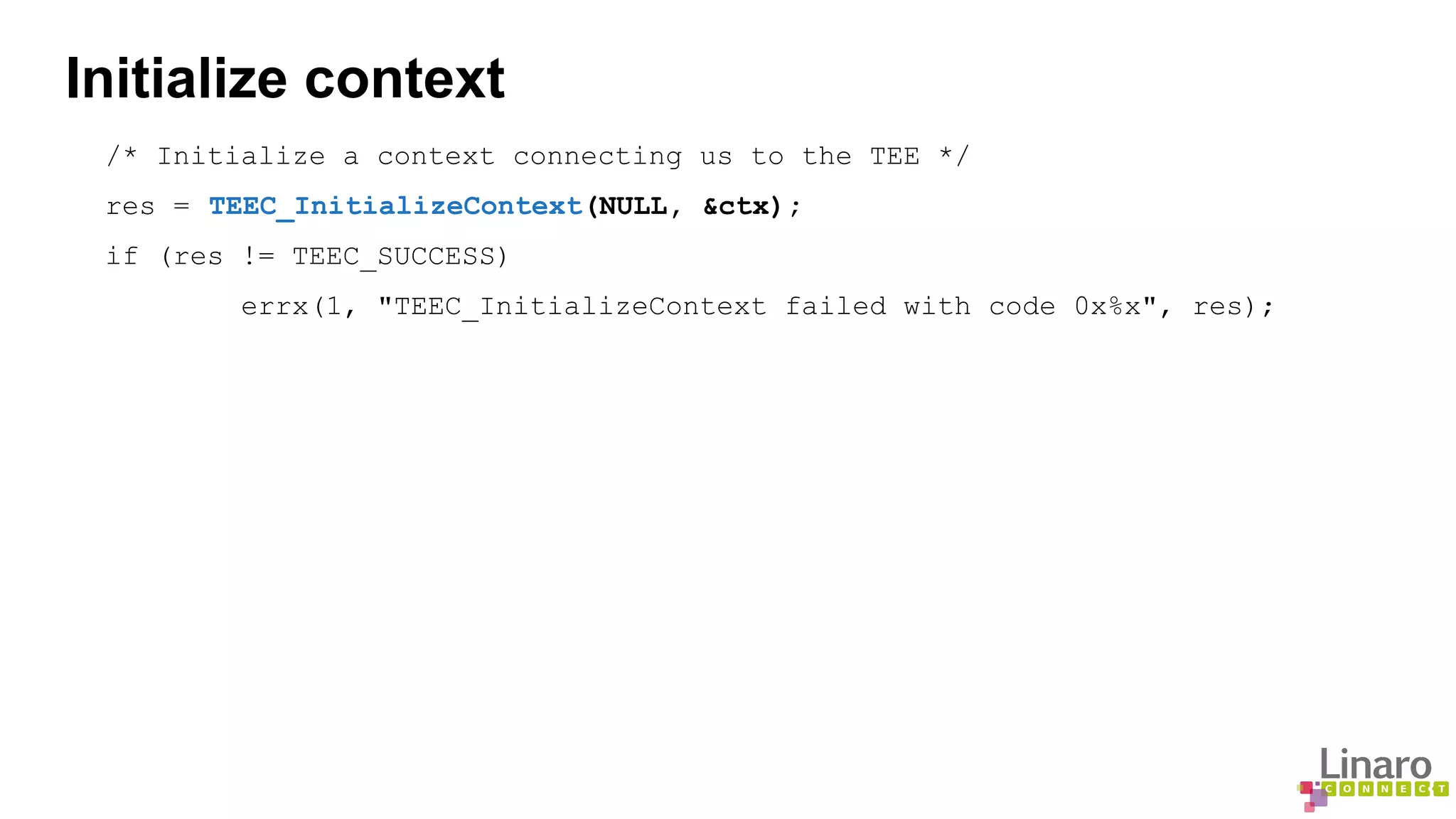
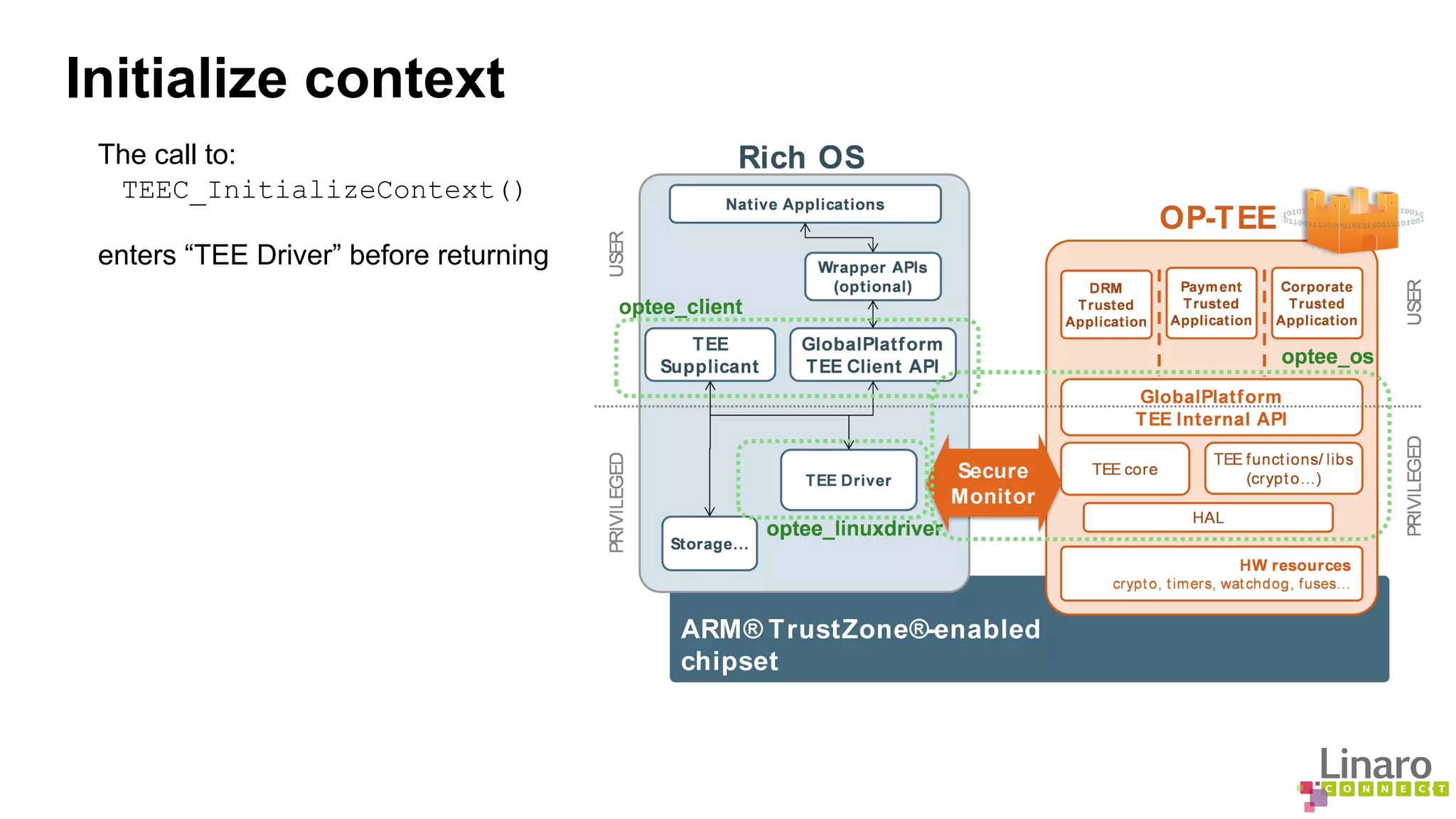
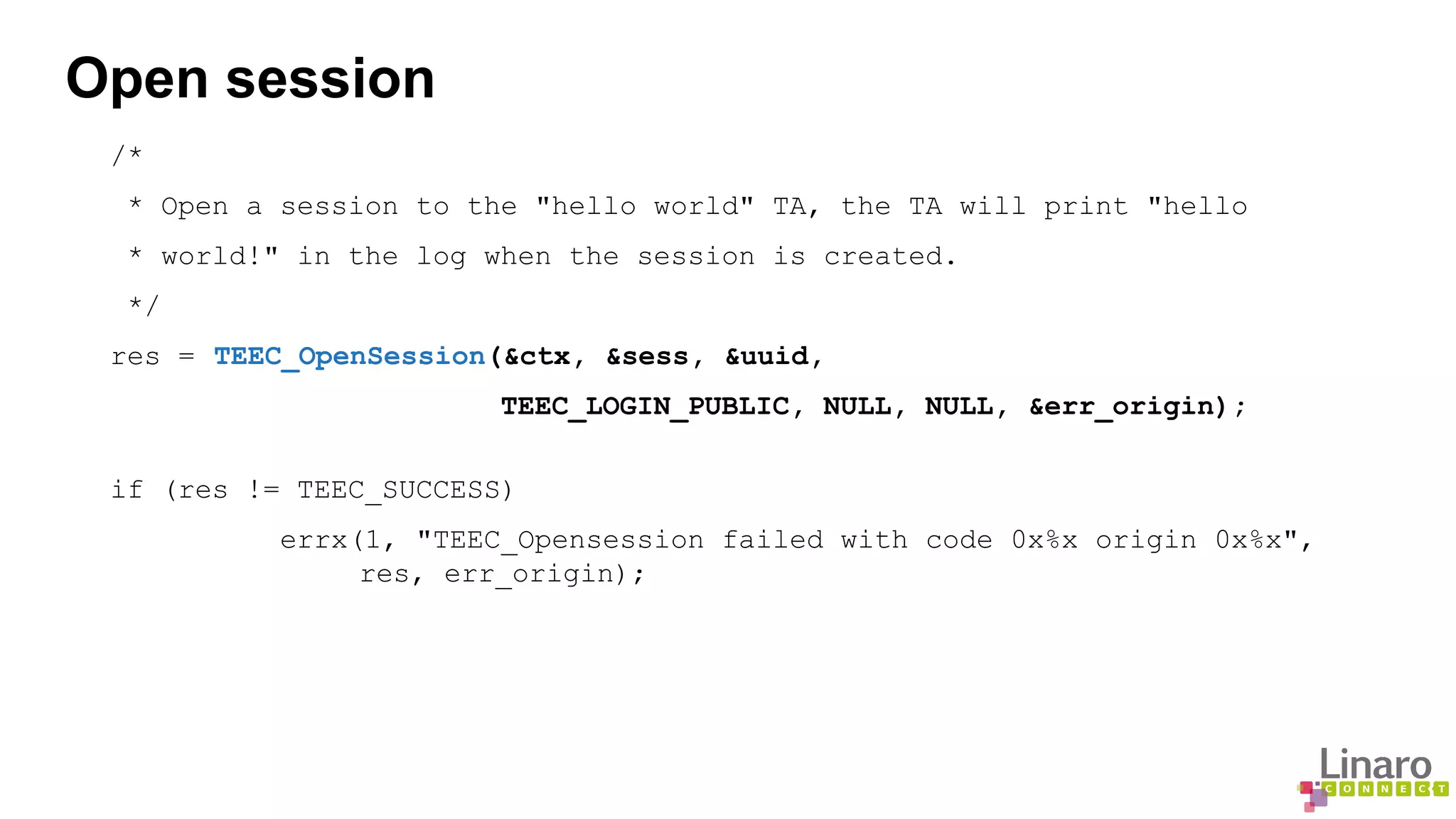
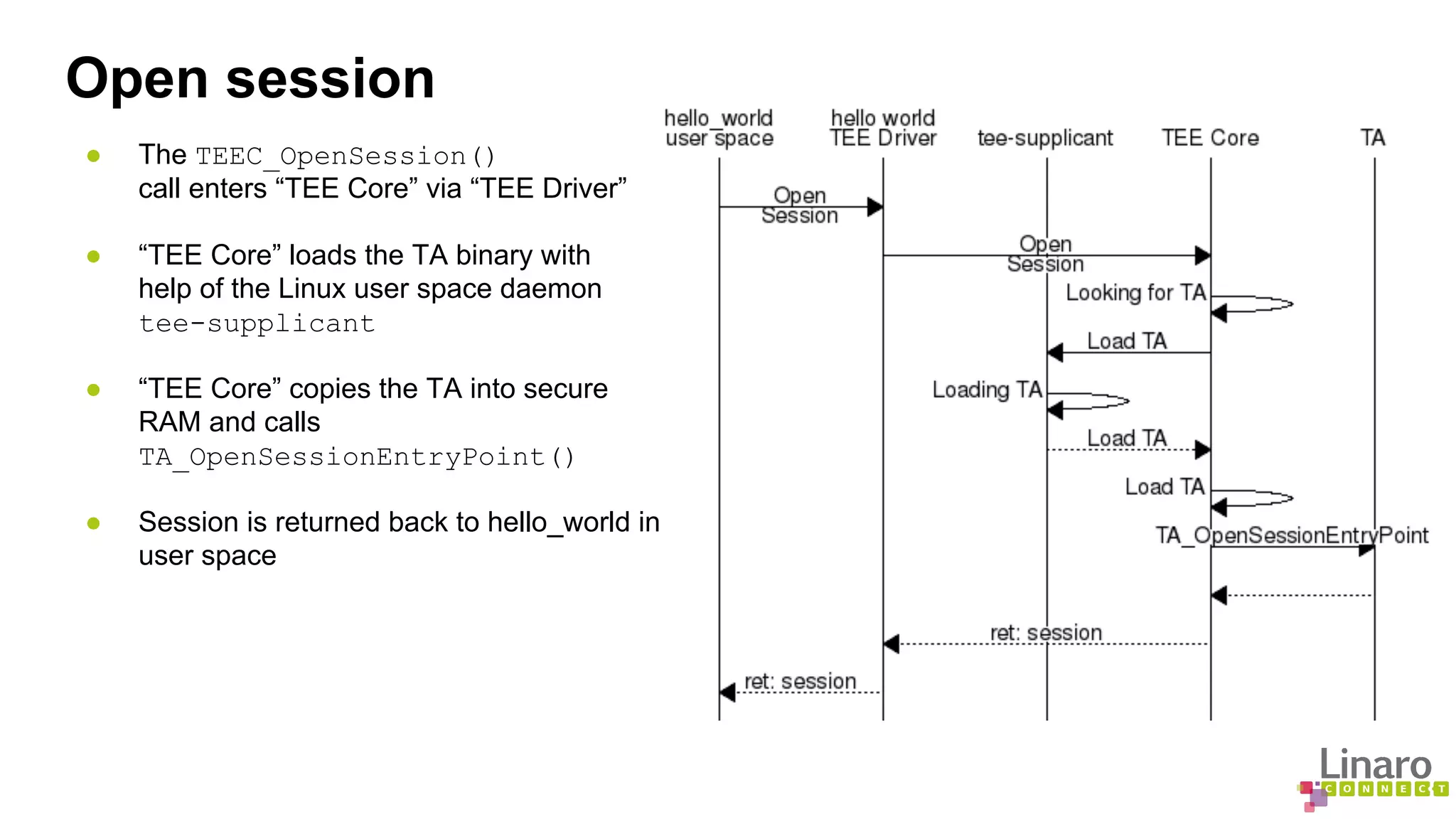
The document provides a comprehensive guide on creating and running trusted applications using OP-TEE, an open-source trusted execution environment developed through collaboration between STMicroelectronics and Linaro. It outlines the initialization process, session management, command invocation, and the necessary tools for development while referencing a 'Hello World' example application. Additionally, it includes links to source code and further resources for understanding OP-TEE and its components.

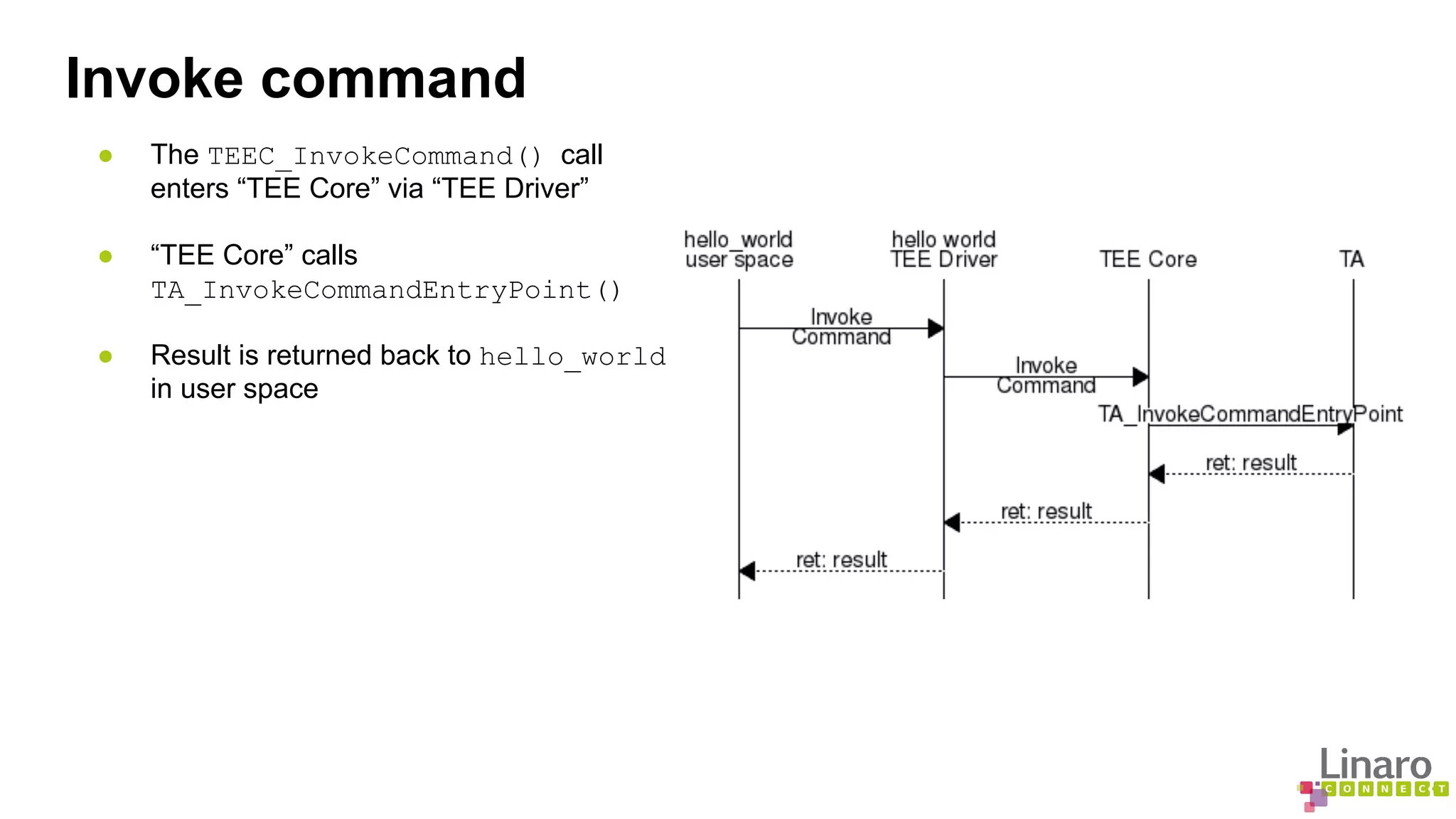
![Invoke command
memset(&op, 0, sizeof(op));
op.paramTypes = TEEC_PARAM_TYPES(TEEC_VALUE_INOUT, TEEC_NONE,
TEEC_NONE, TEEC_NONE);
op.params[0].value.a = 42;
printf("Invoking TA to increment %dn", op.params[0].value.a);
res = TEEC_InvokeCommand(&sess, TA_HELLO_WORLD_CMD_INC_VALUE, &op,
&err_origin);
if (res != TEEC_SUCCESS)
errx(1, "TEEC_InvokeCommand failed with code 0x%x origin 0x%x",
res, err_origin);
printf("TA incremented value to %dn", op.params[0].value.a);](https://image.slidesharecdn.com/lcu14-103-howtocreateandruntrustedapplicationsonop-tee-140916115614-phpapp01/75/LCU14-103-How-to-create-and-run-Trusted-Applications-on-OP-TEE-8-2048.jpg)