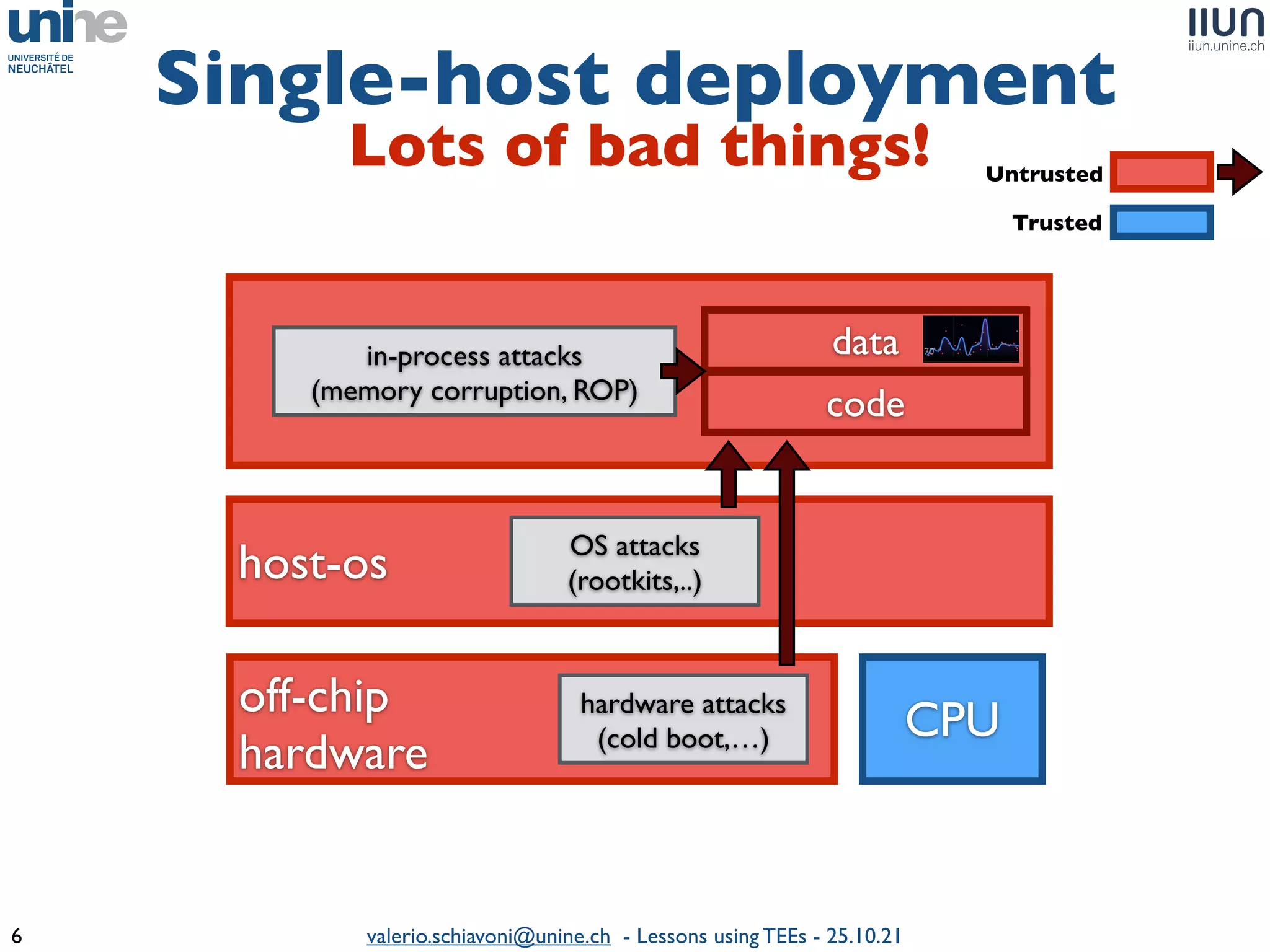
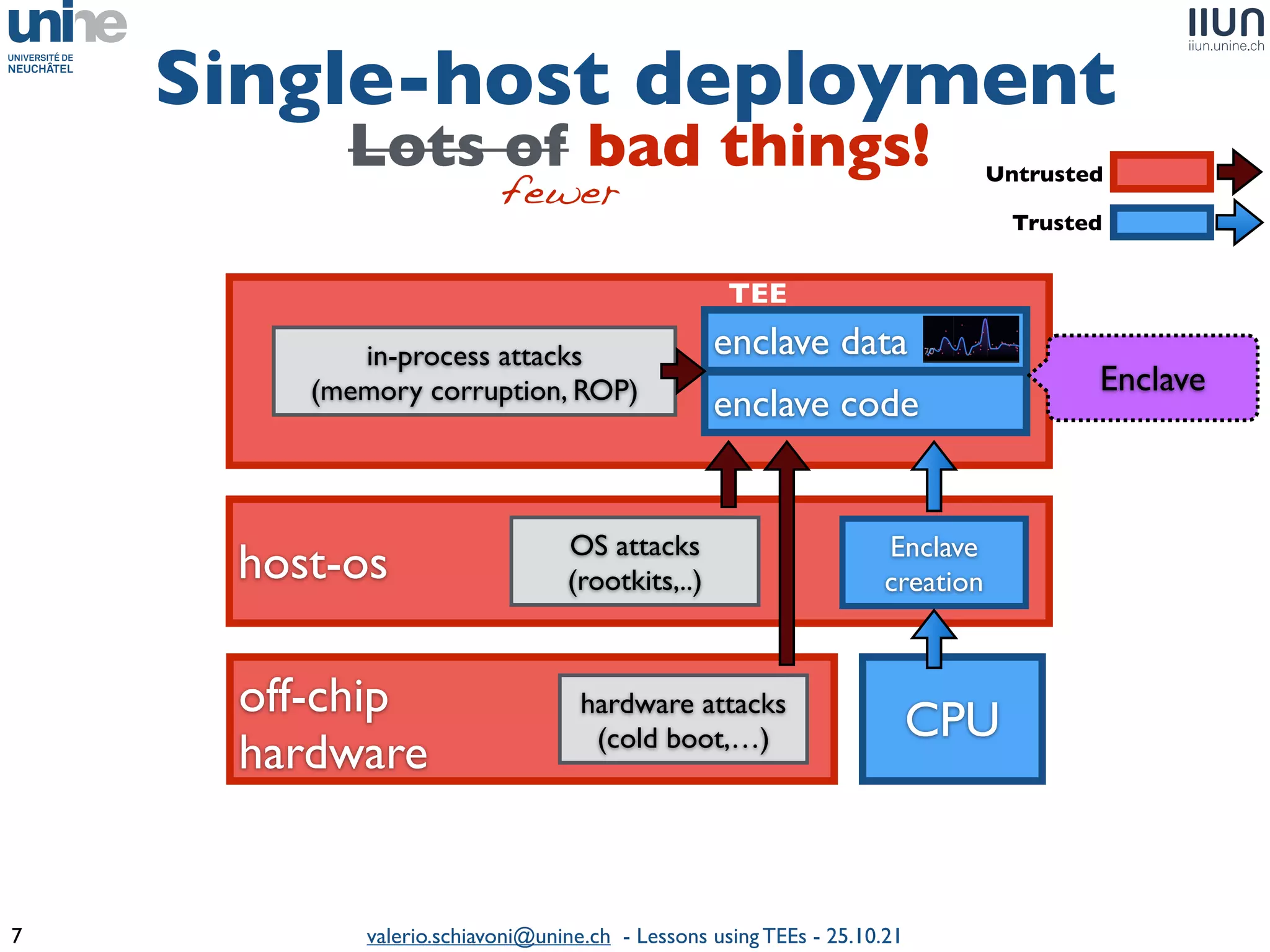
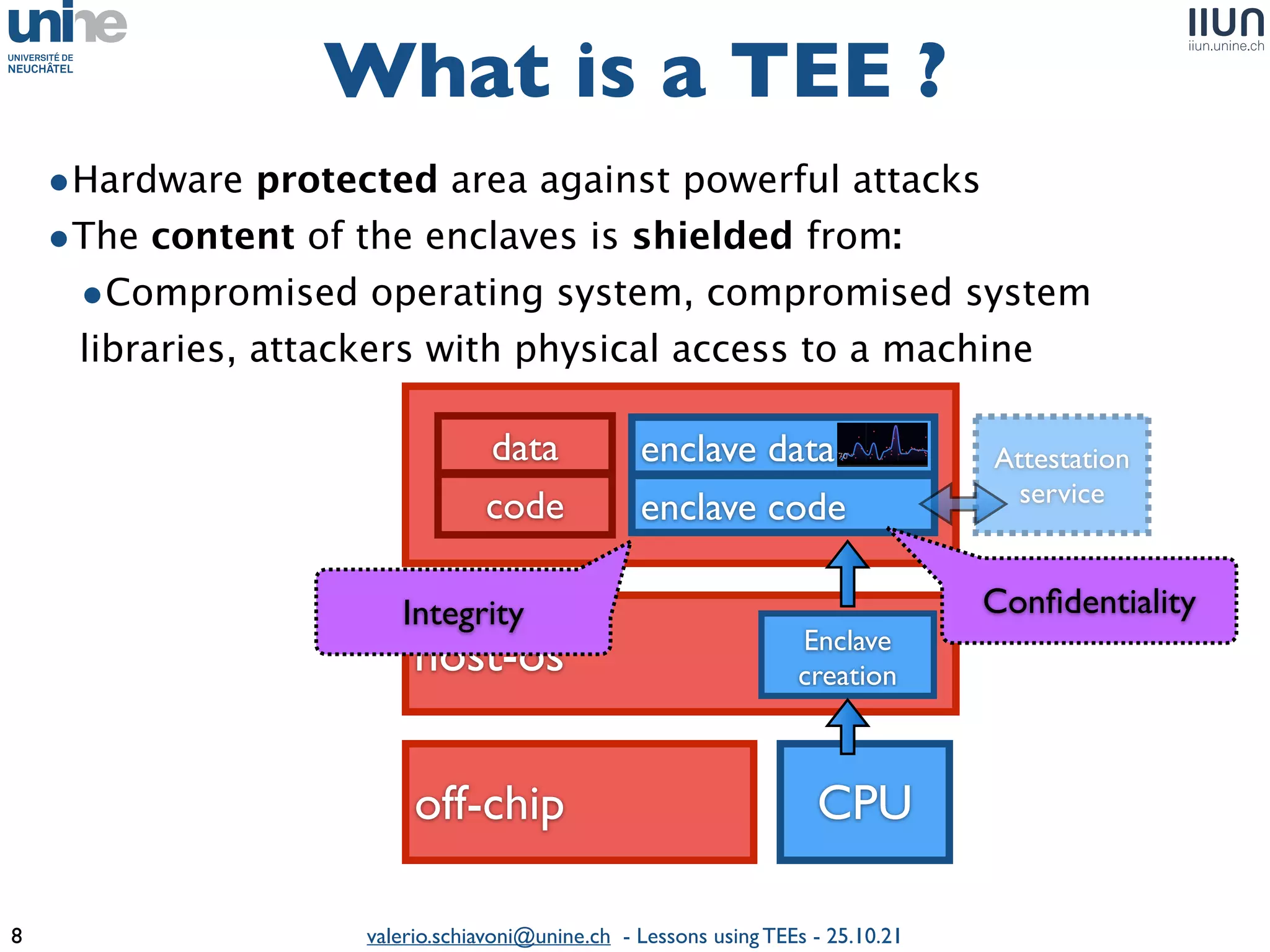
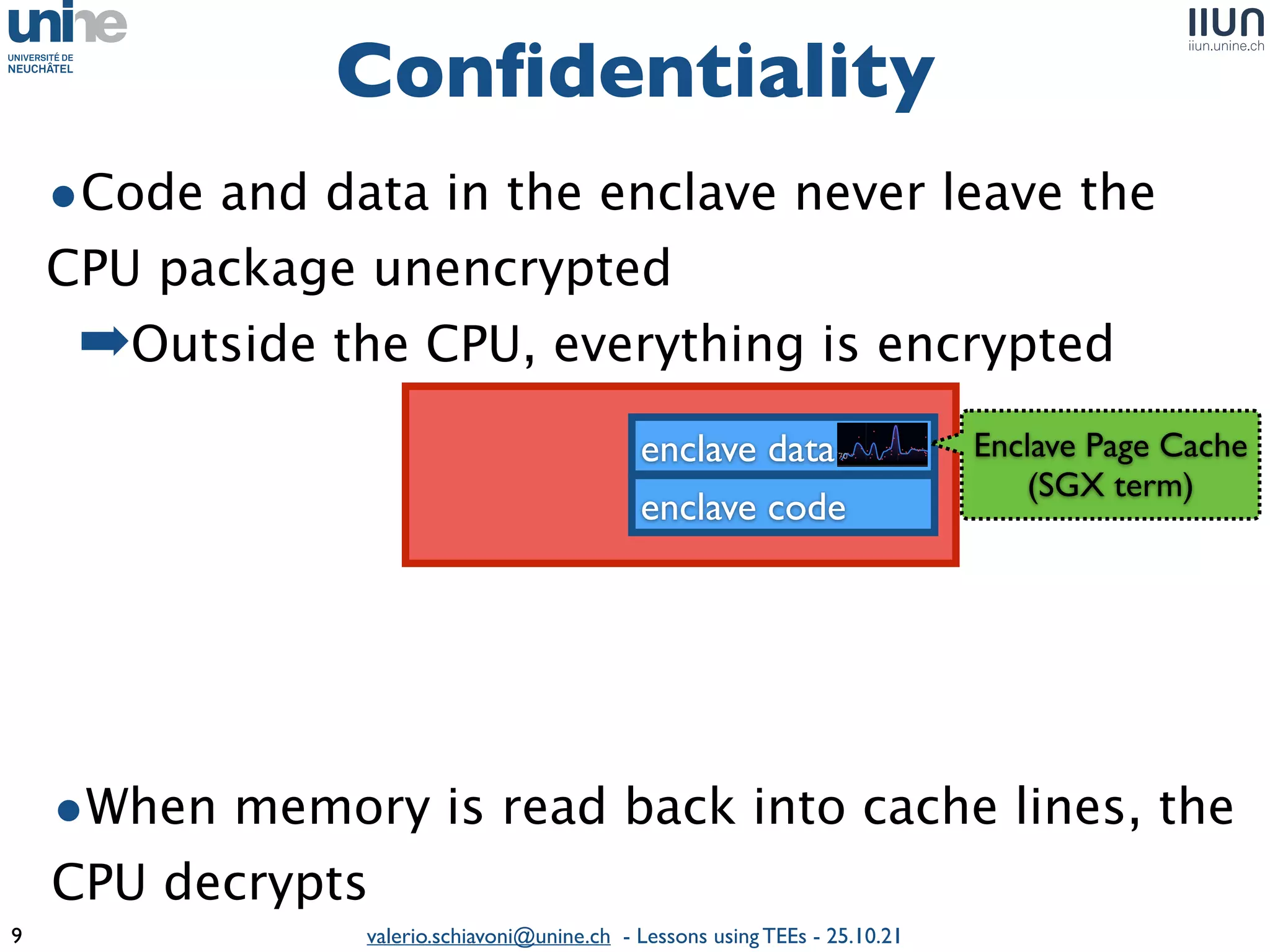
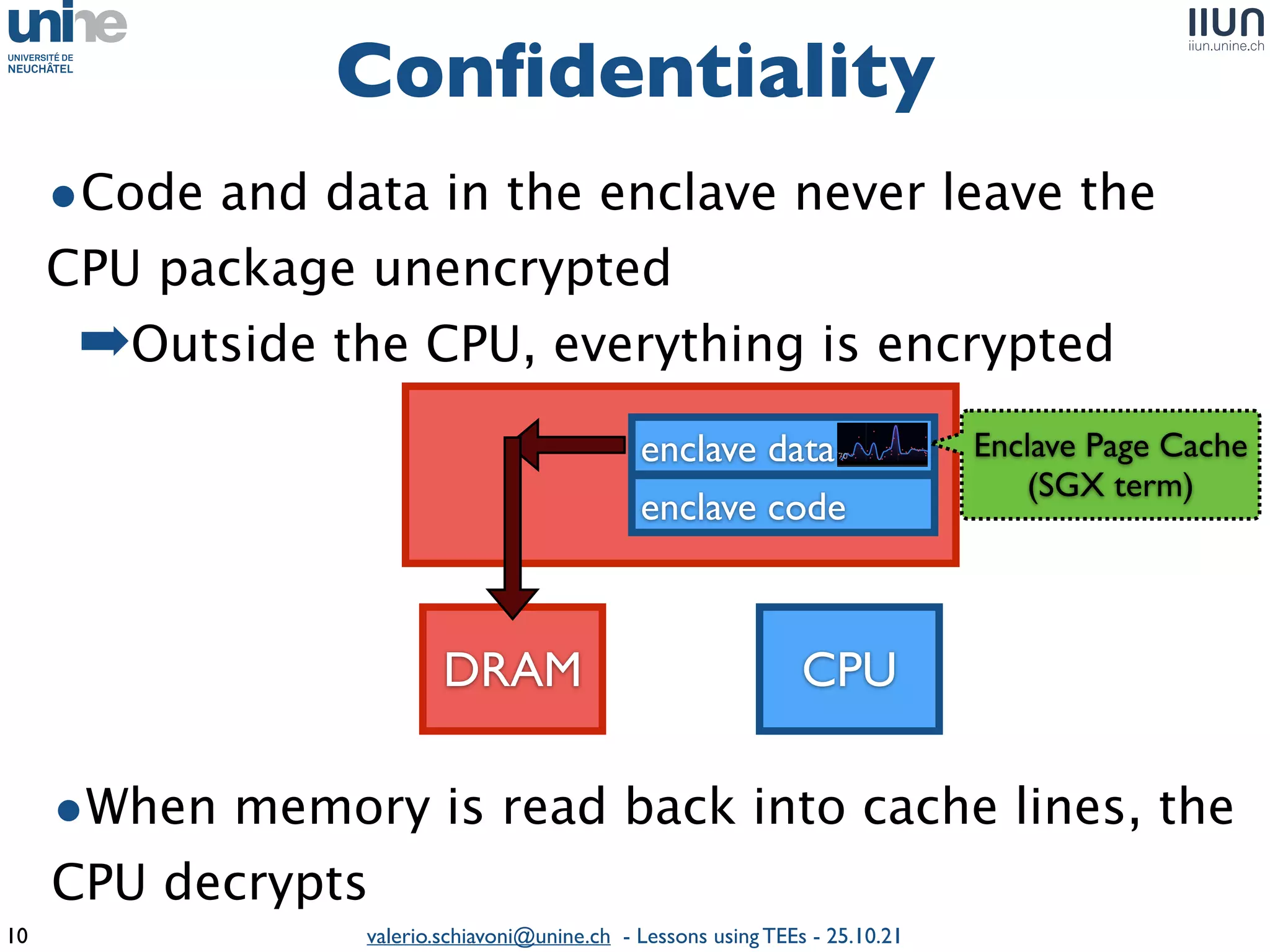
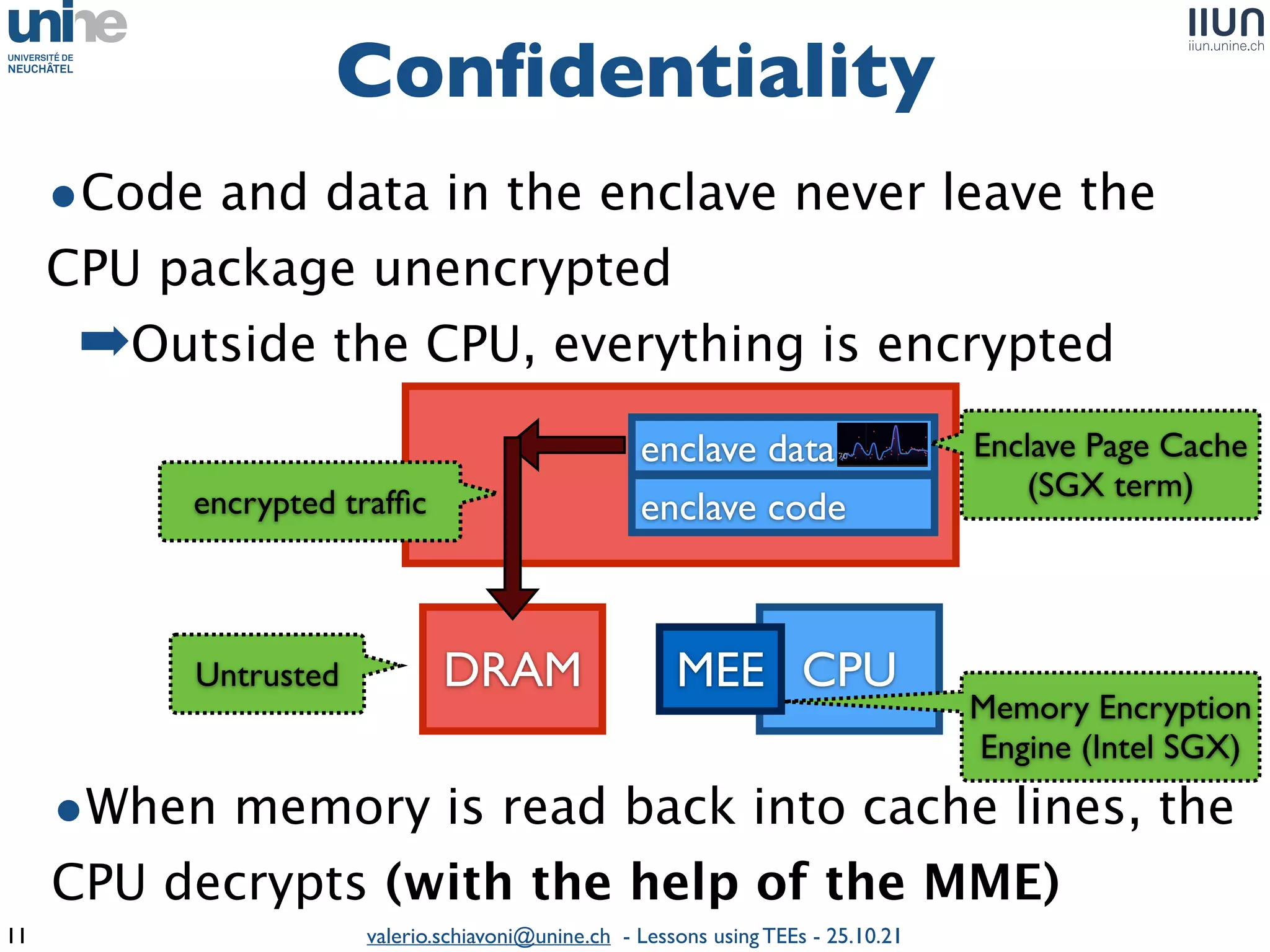
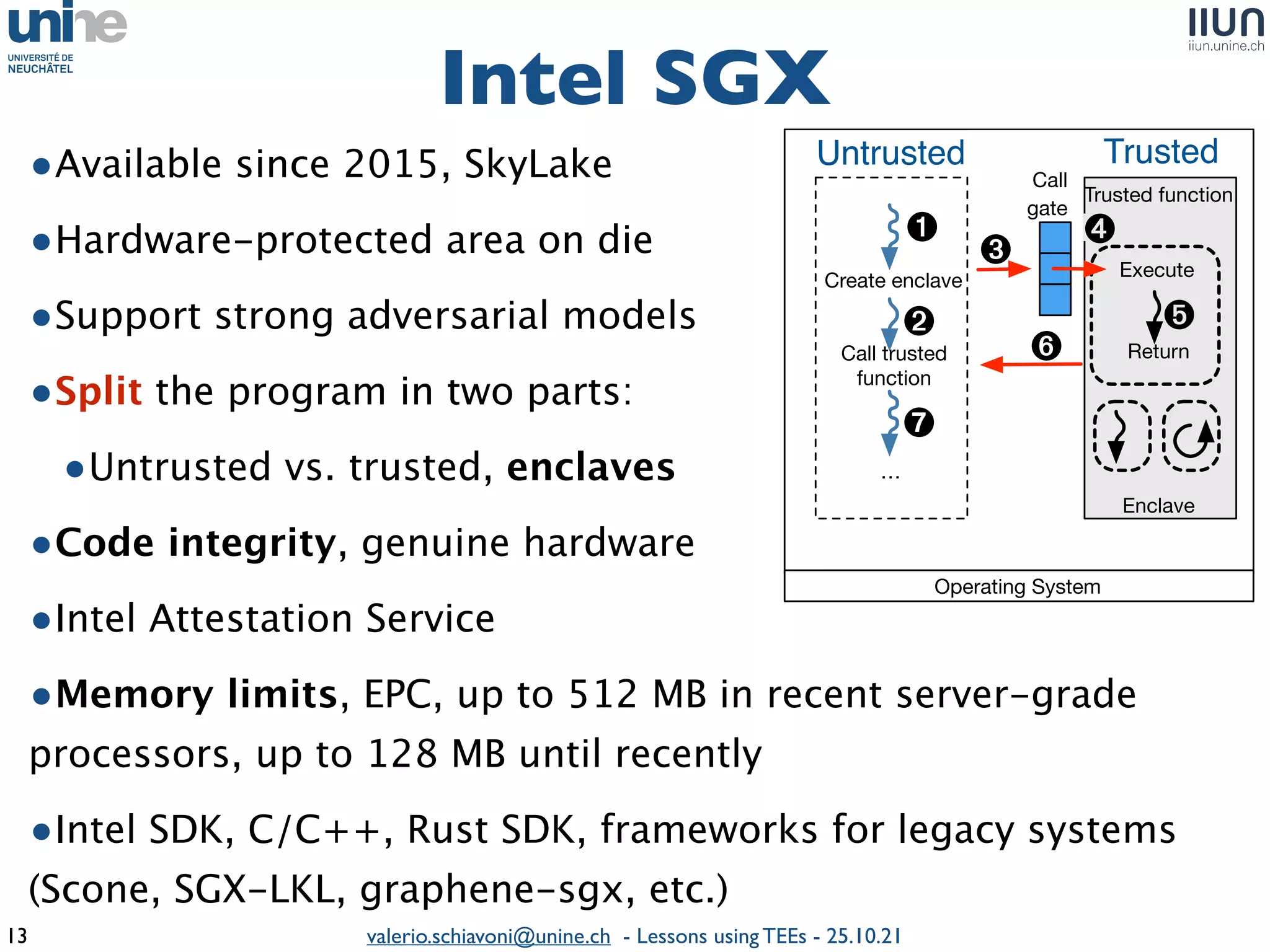
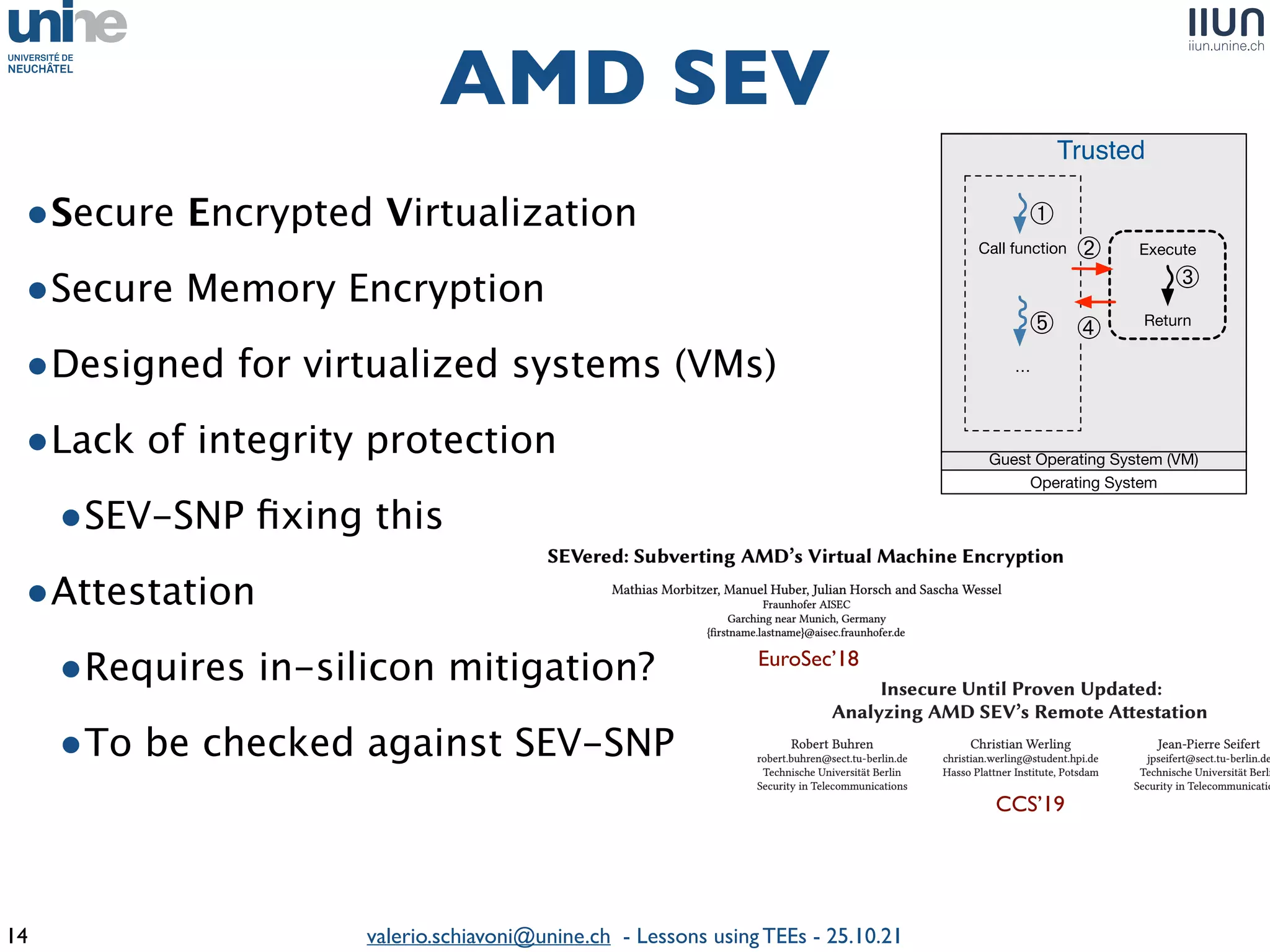
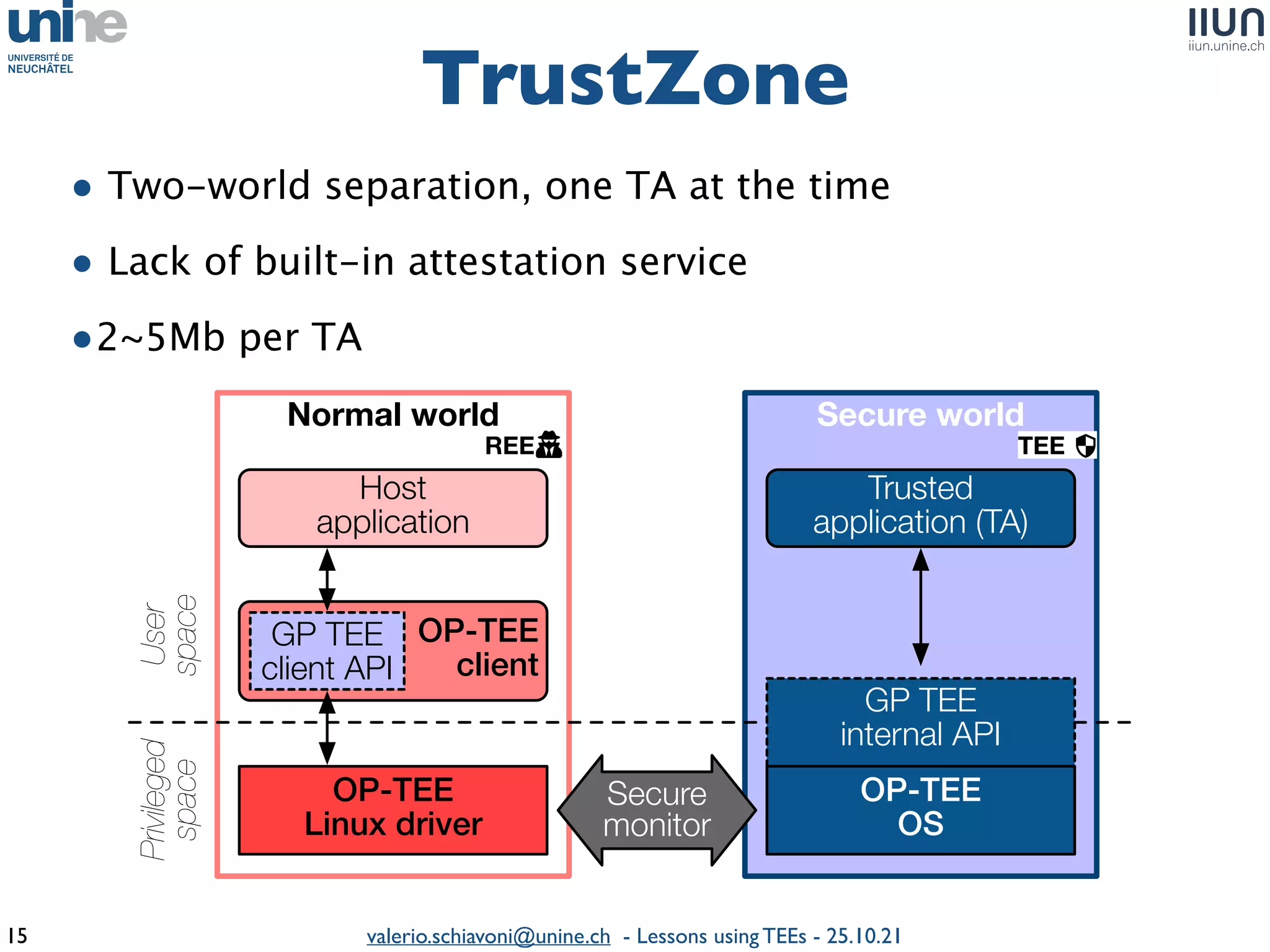
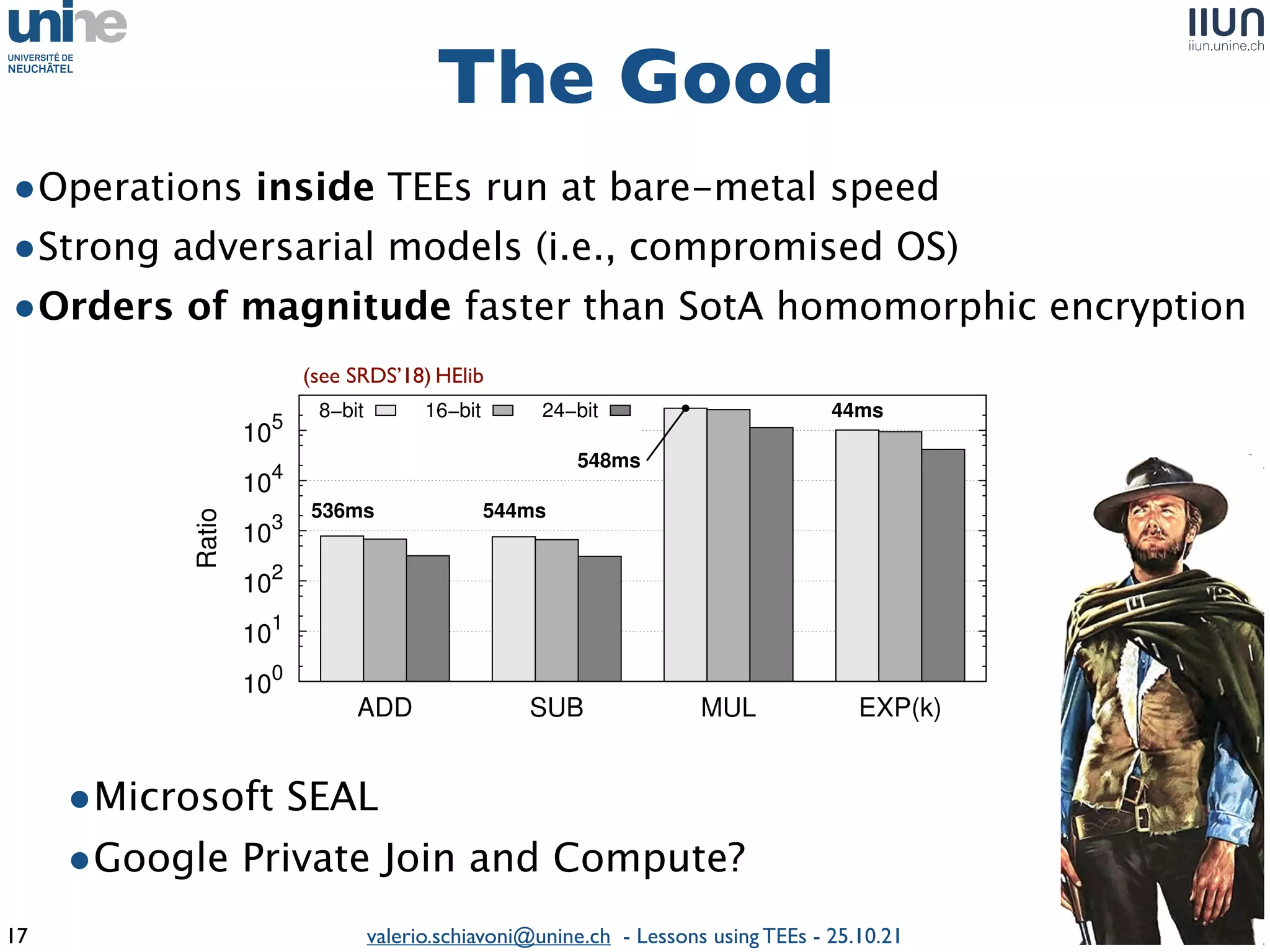
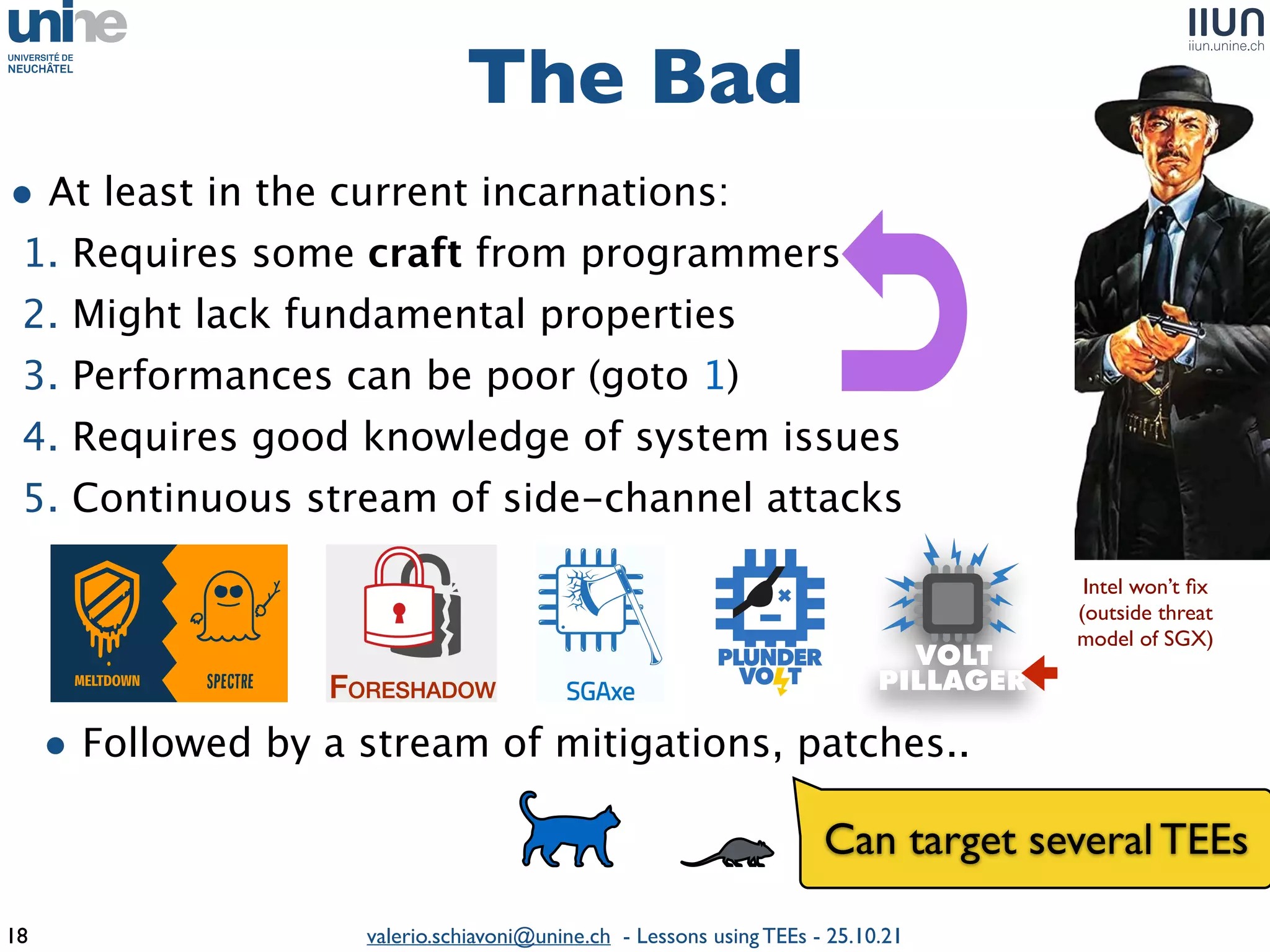
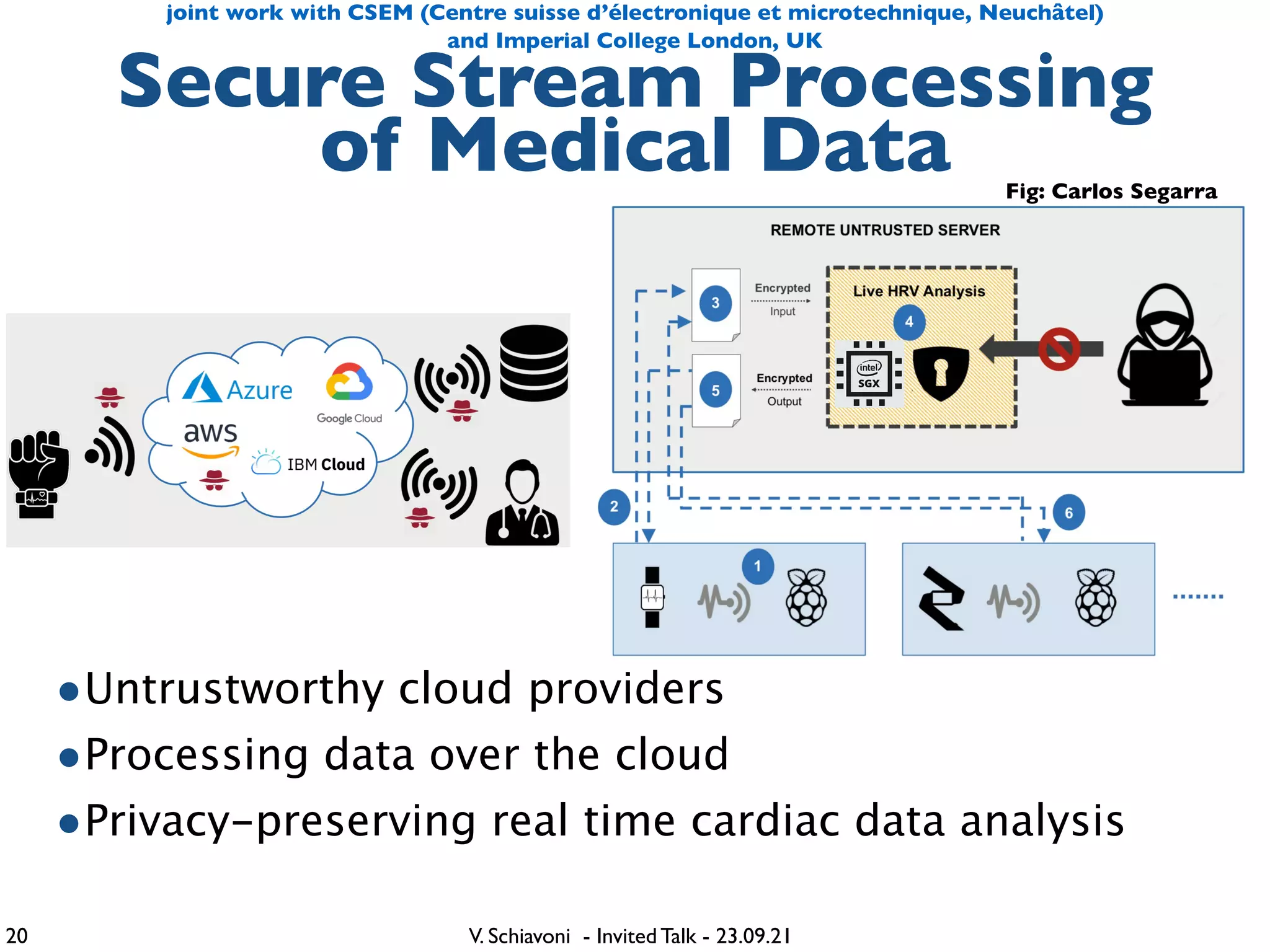
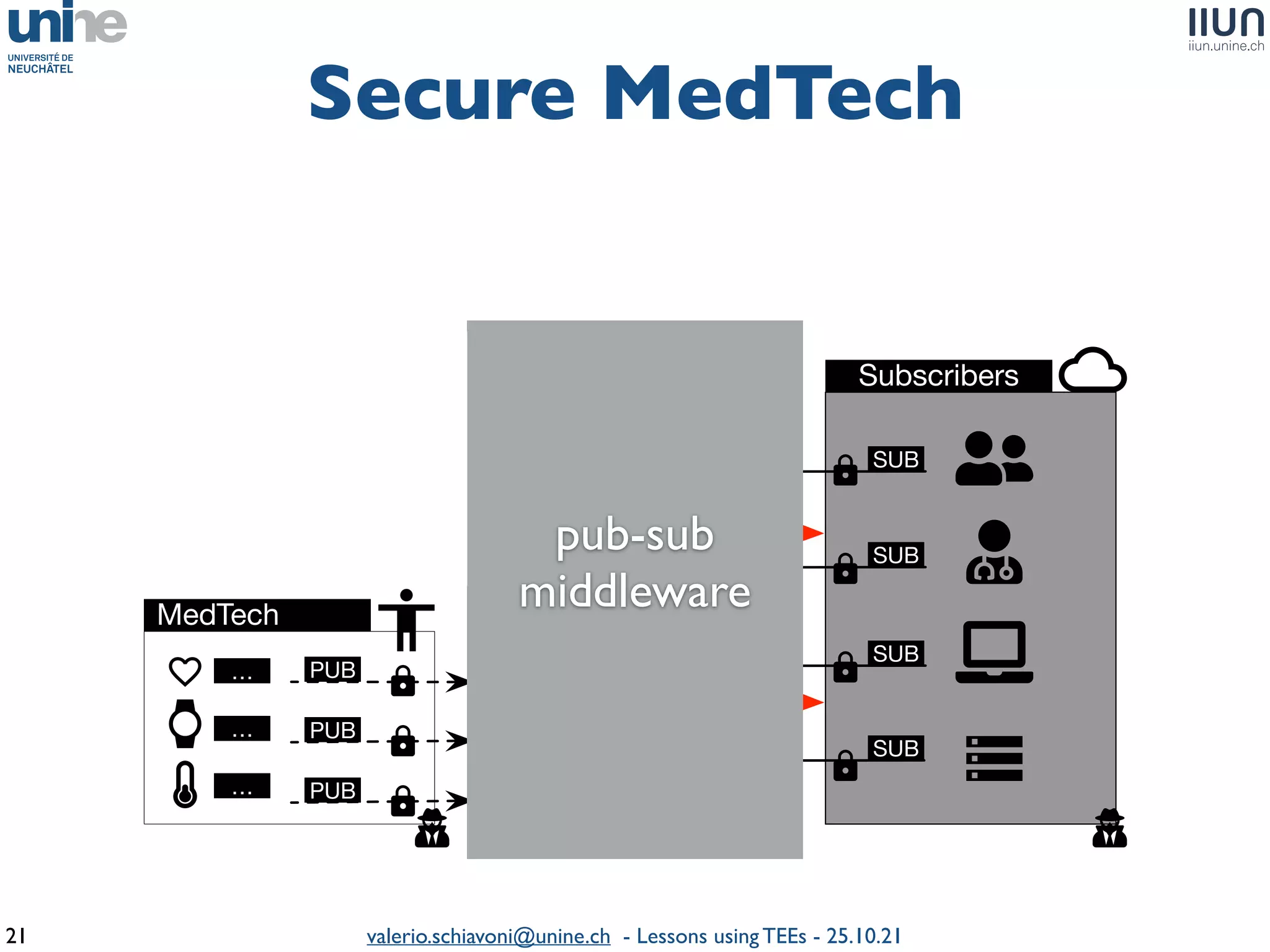
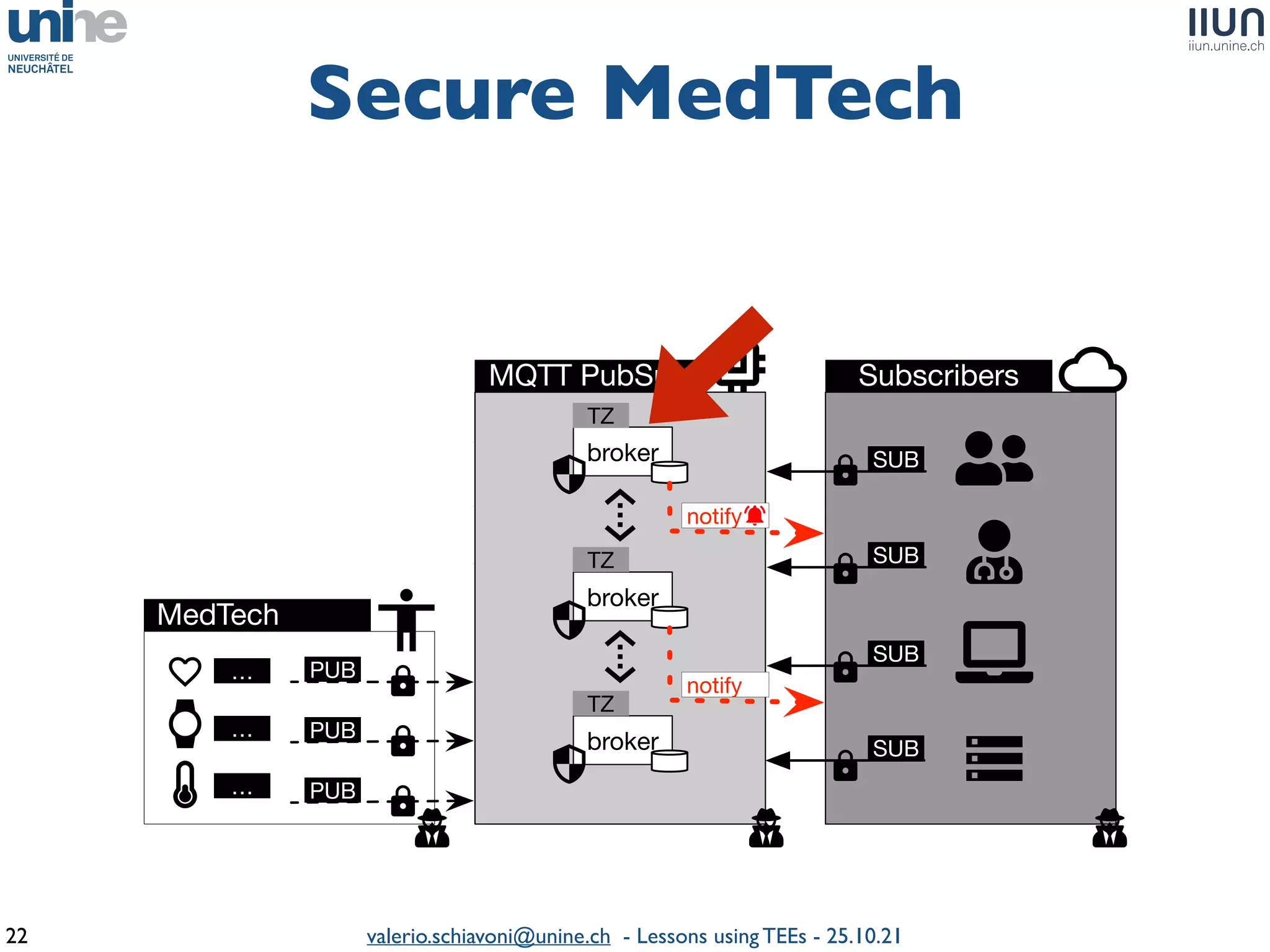
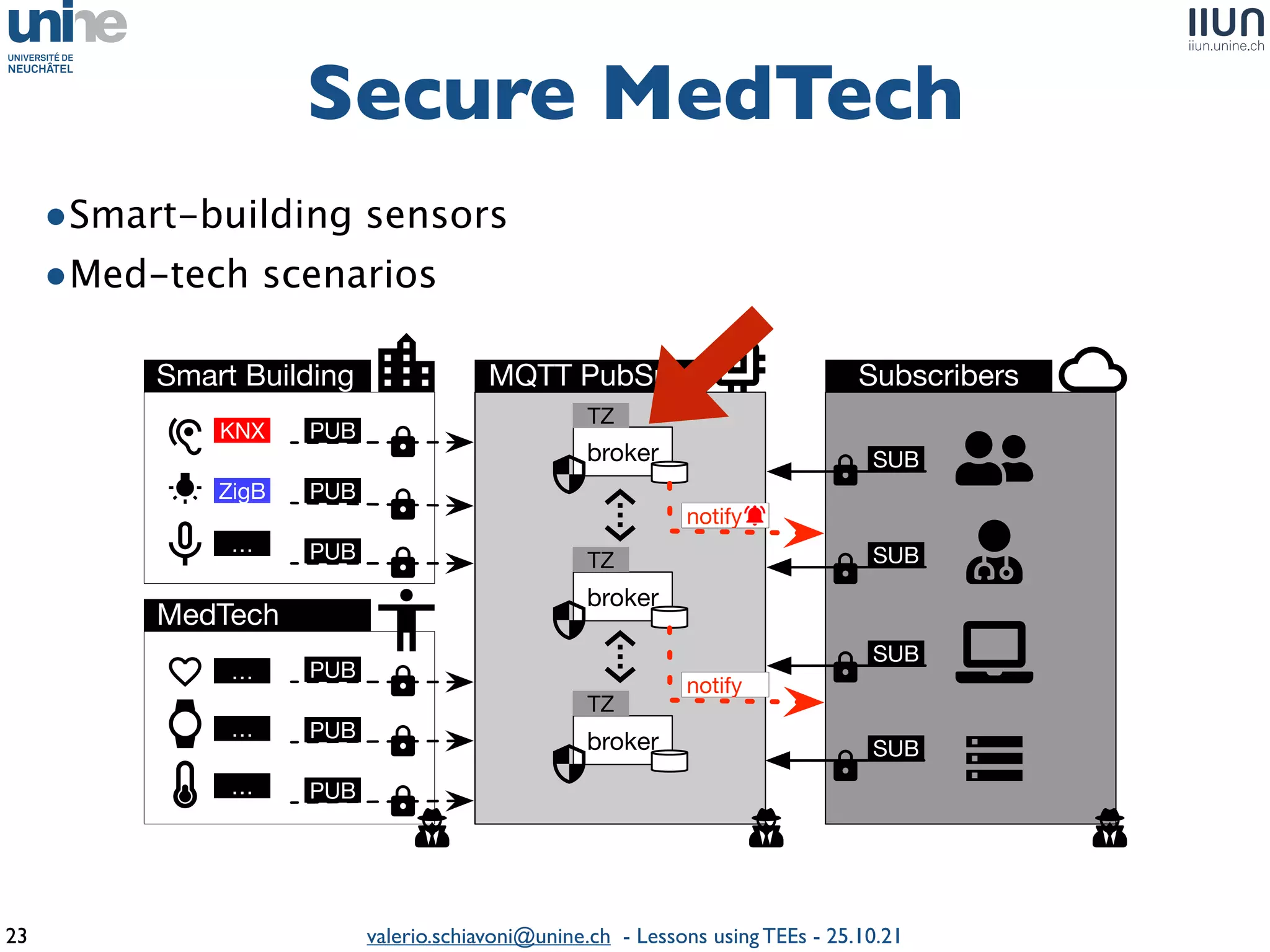
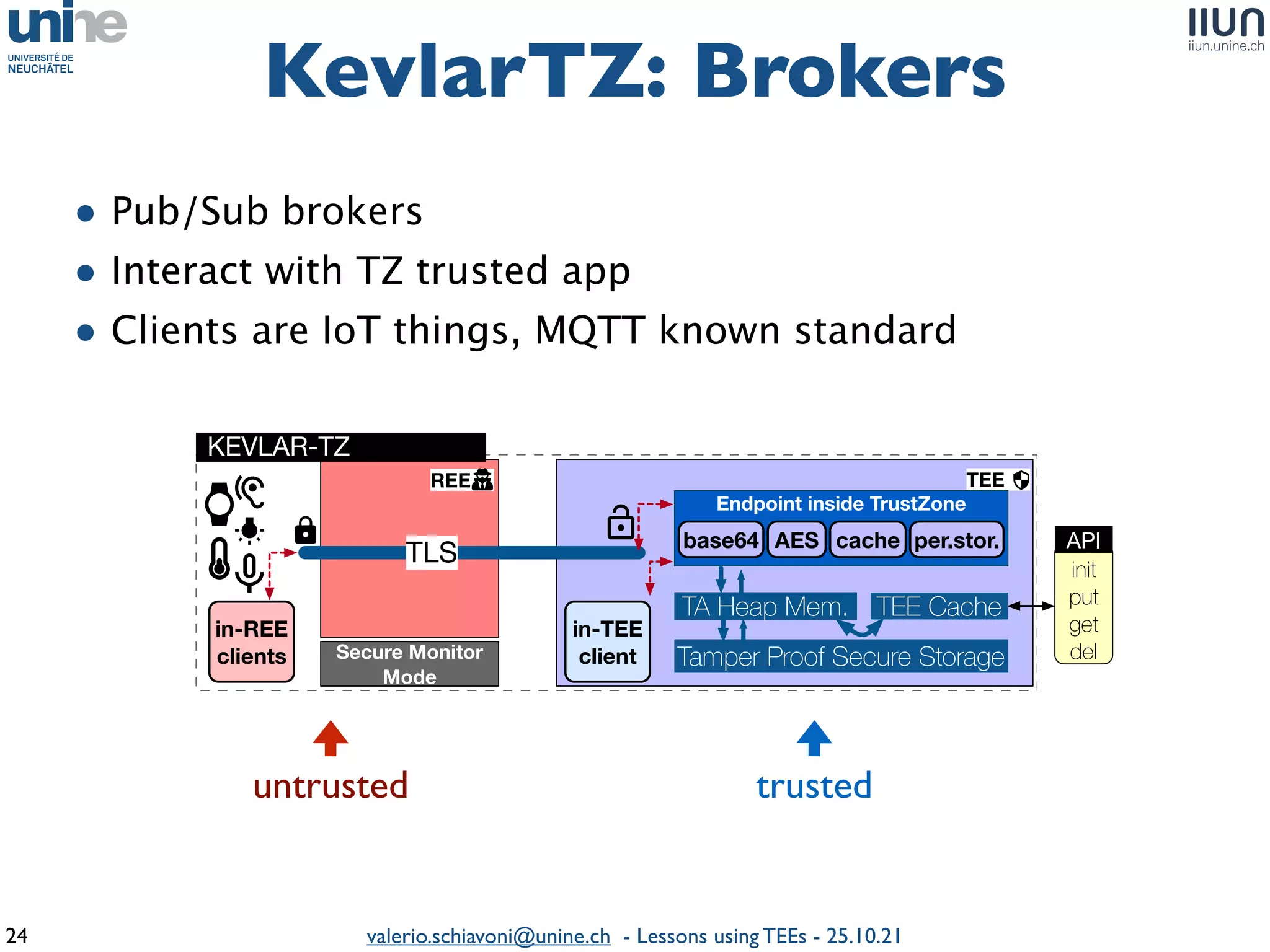
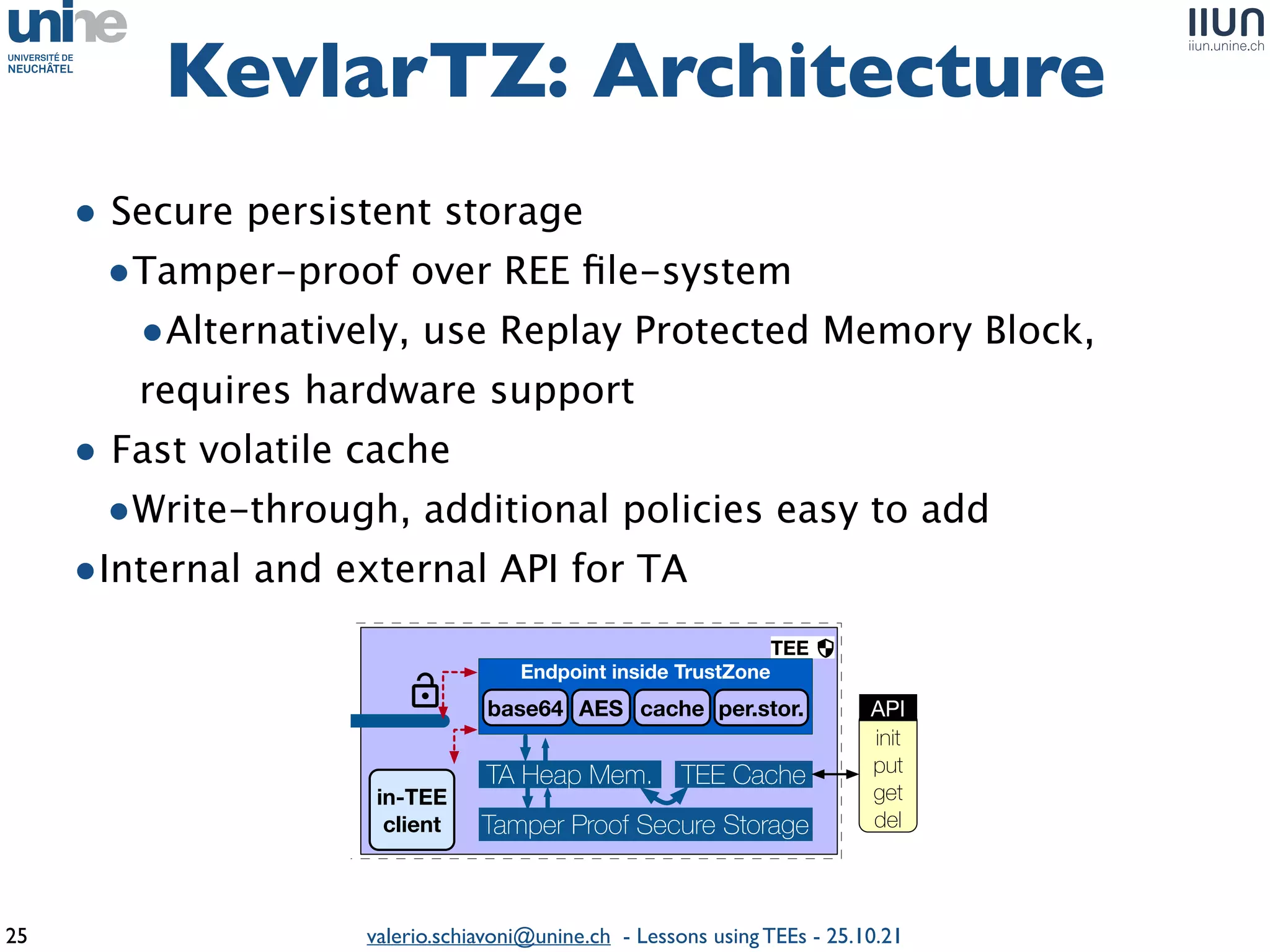
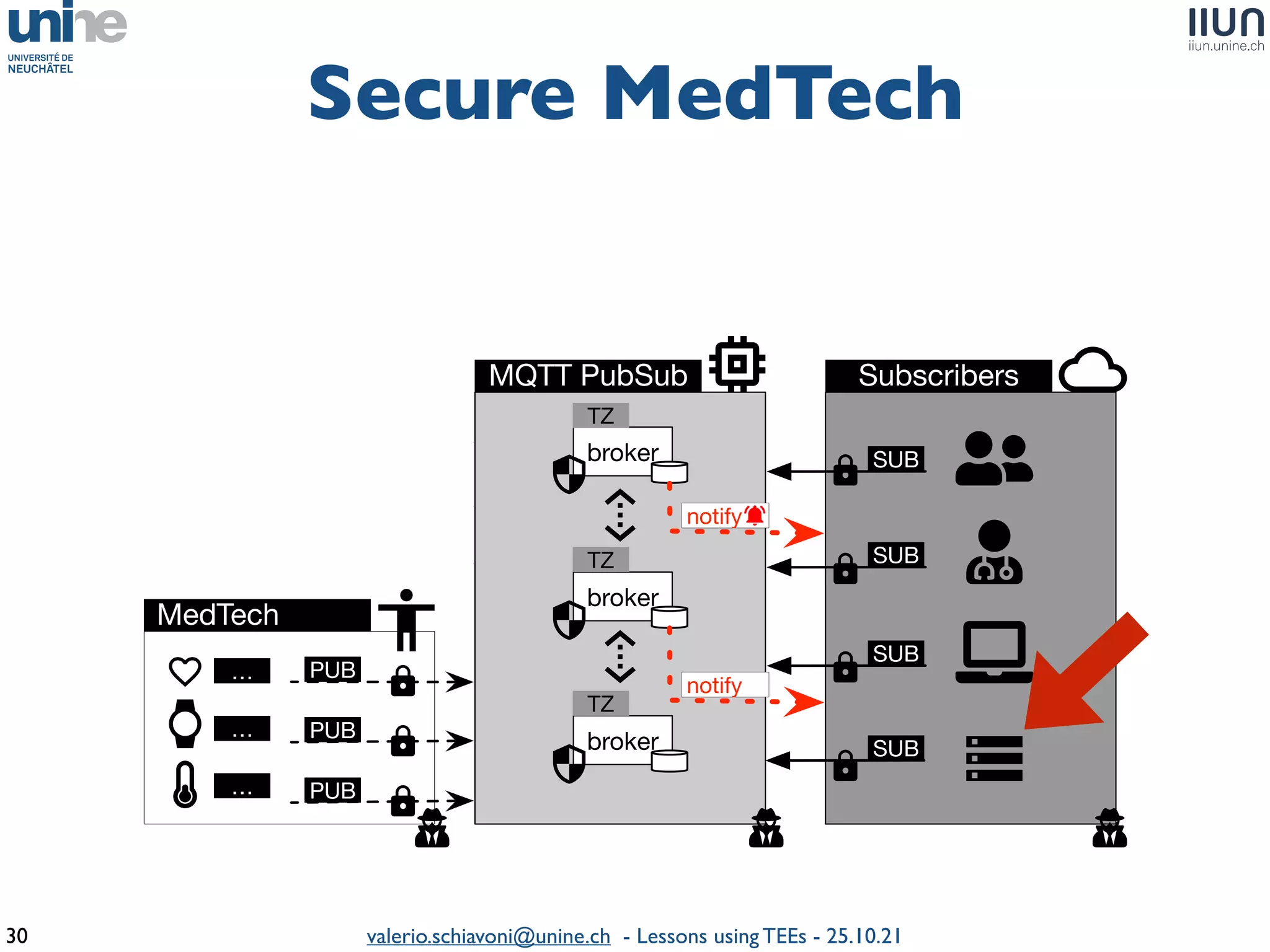
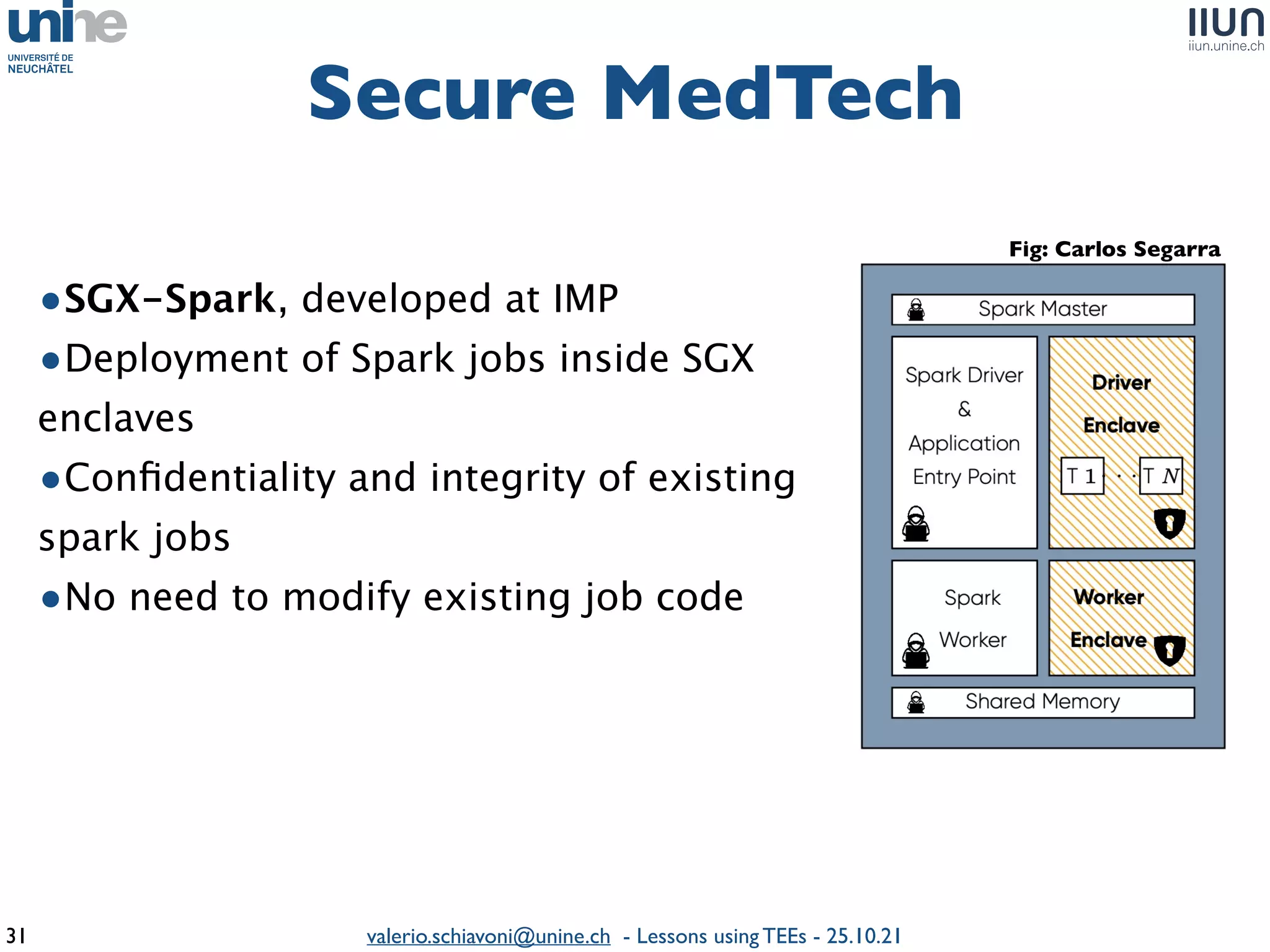
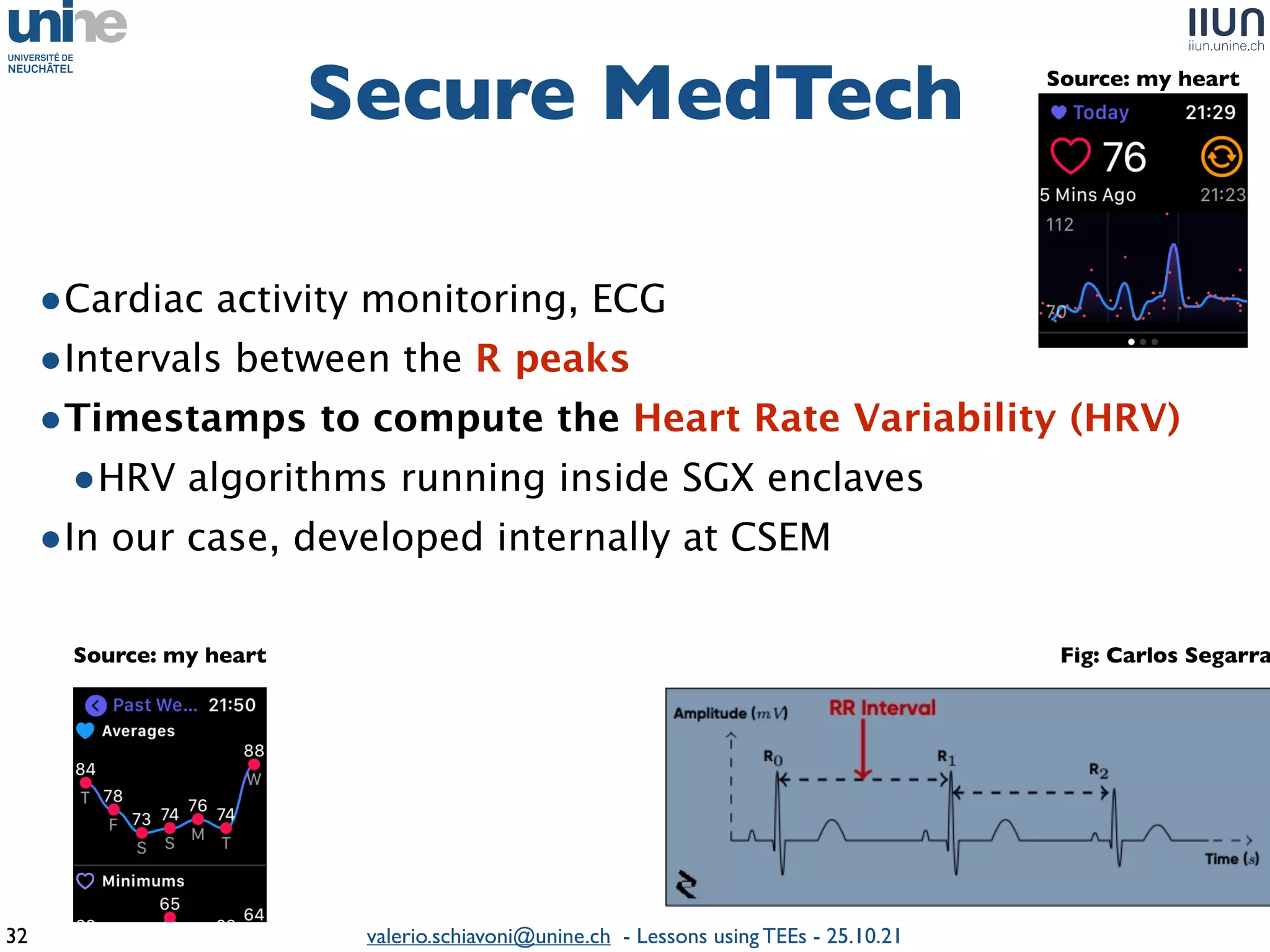
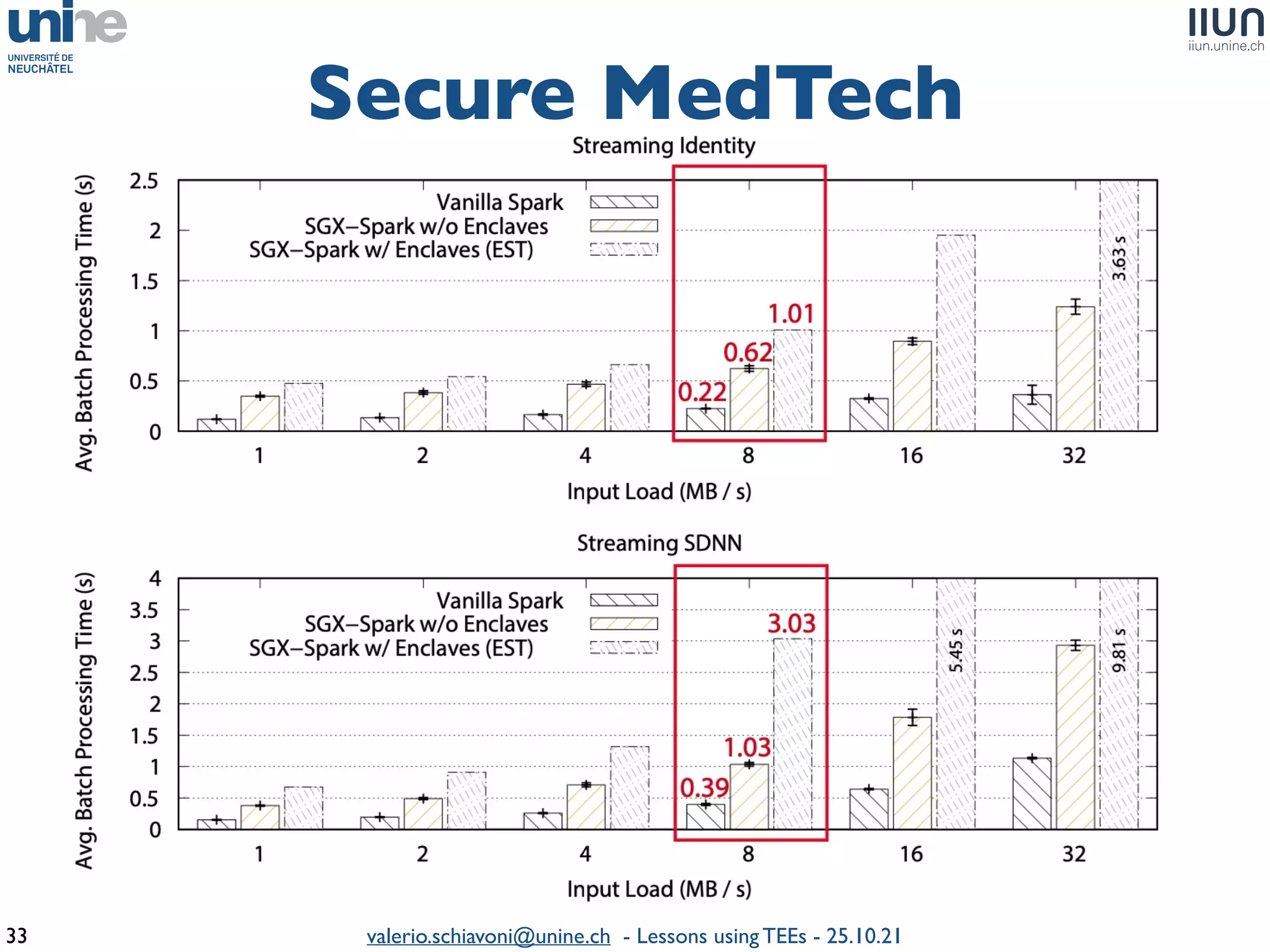
The document outlines lessons learned from building trustworthy systems using Trusted Execution Environments (TEEs), particularly in medical applications where data privacy and integrity are crucial. It describes the functionality and security features of Intel SGX and AMD SEV, along with various case studies and challenges encountered during implementation. The insights emphasize serious considerations in using TEEs, cautioning that they are not a panacea and require careful system design and understanding of limitations.