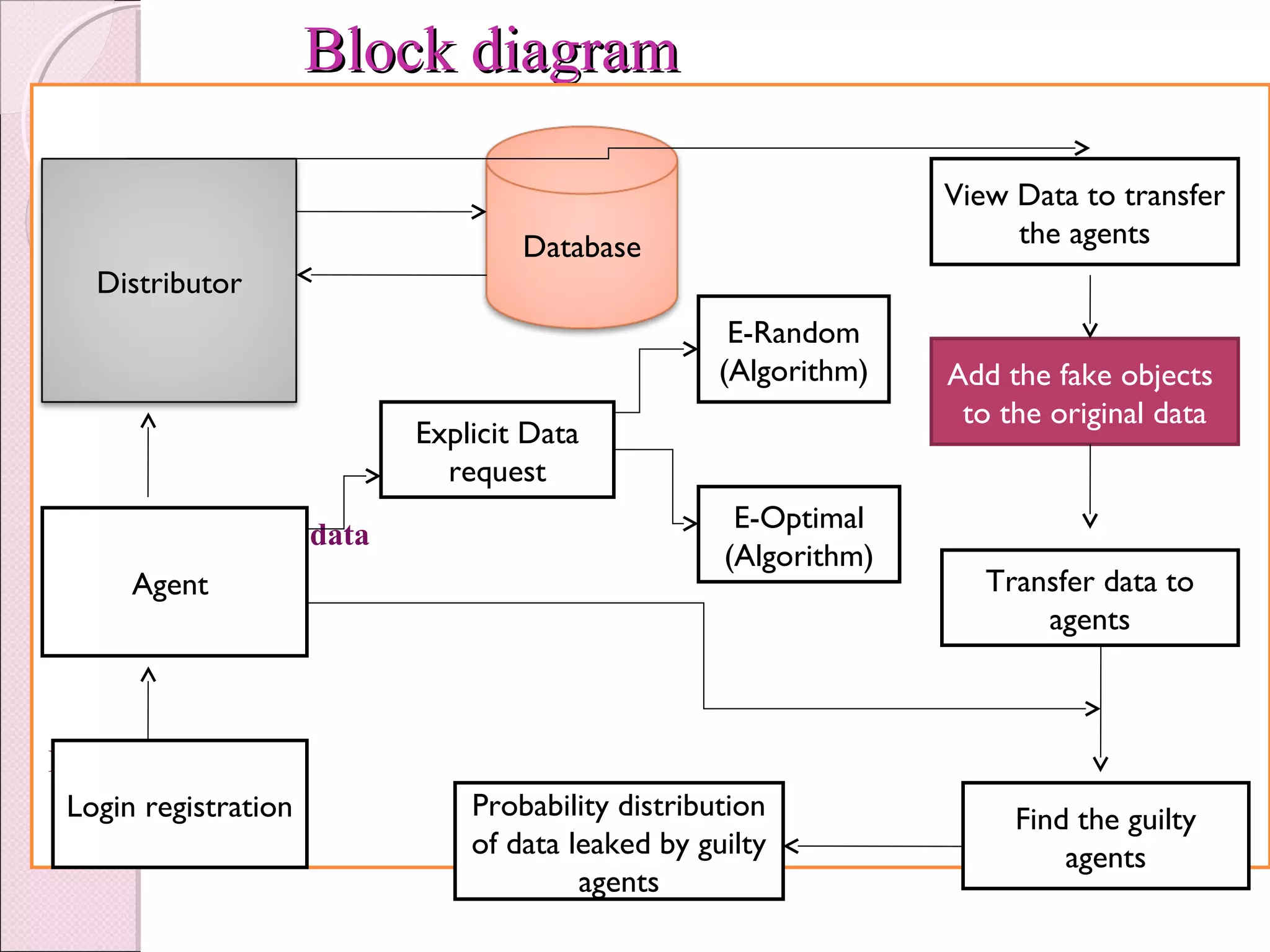
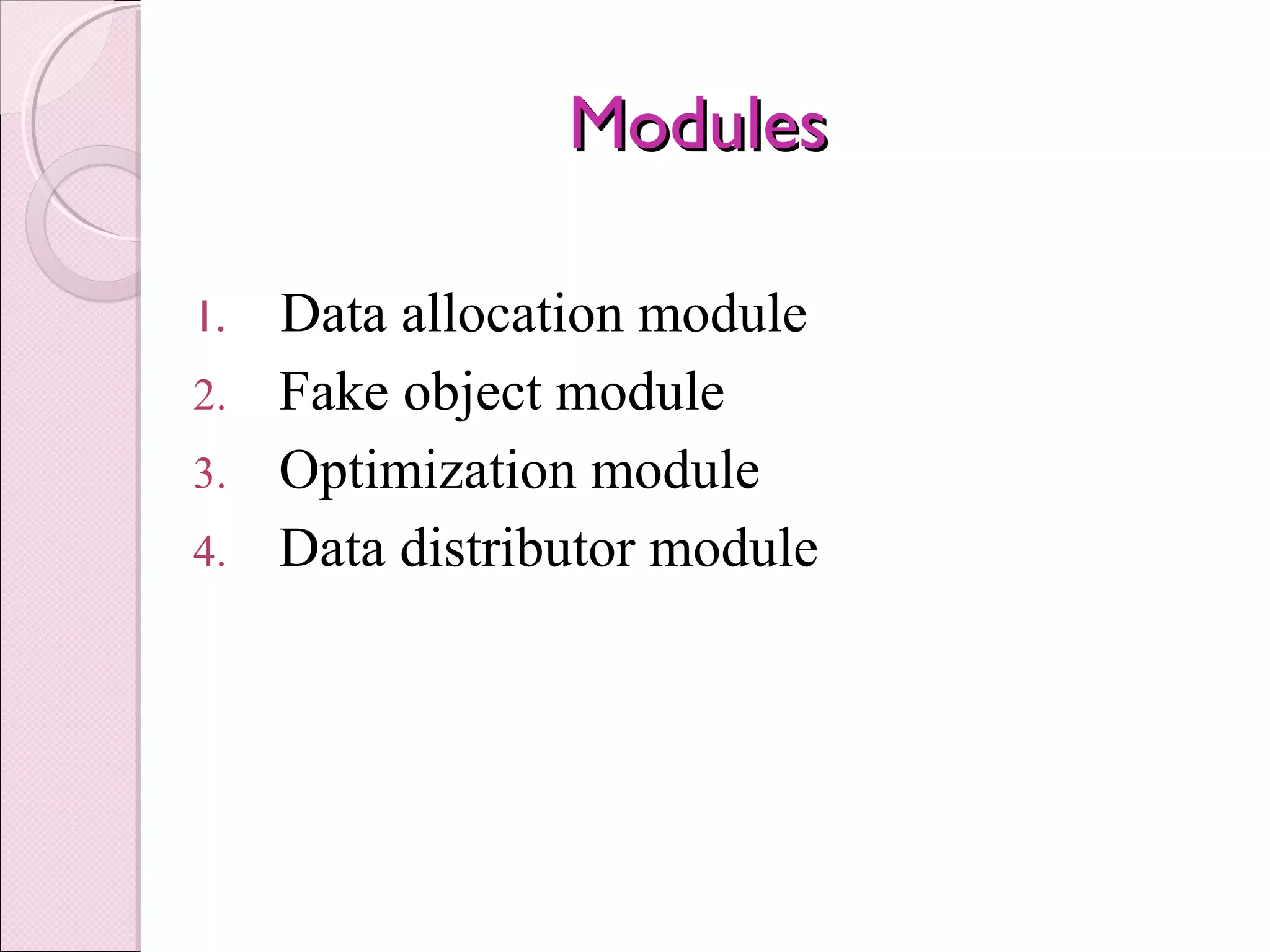
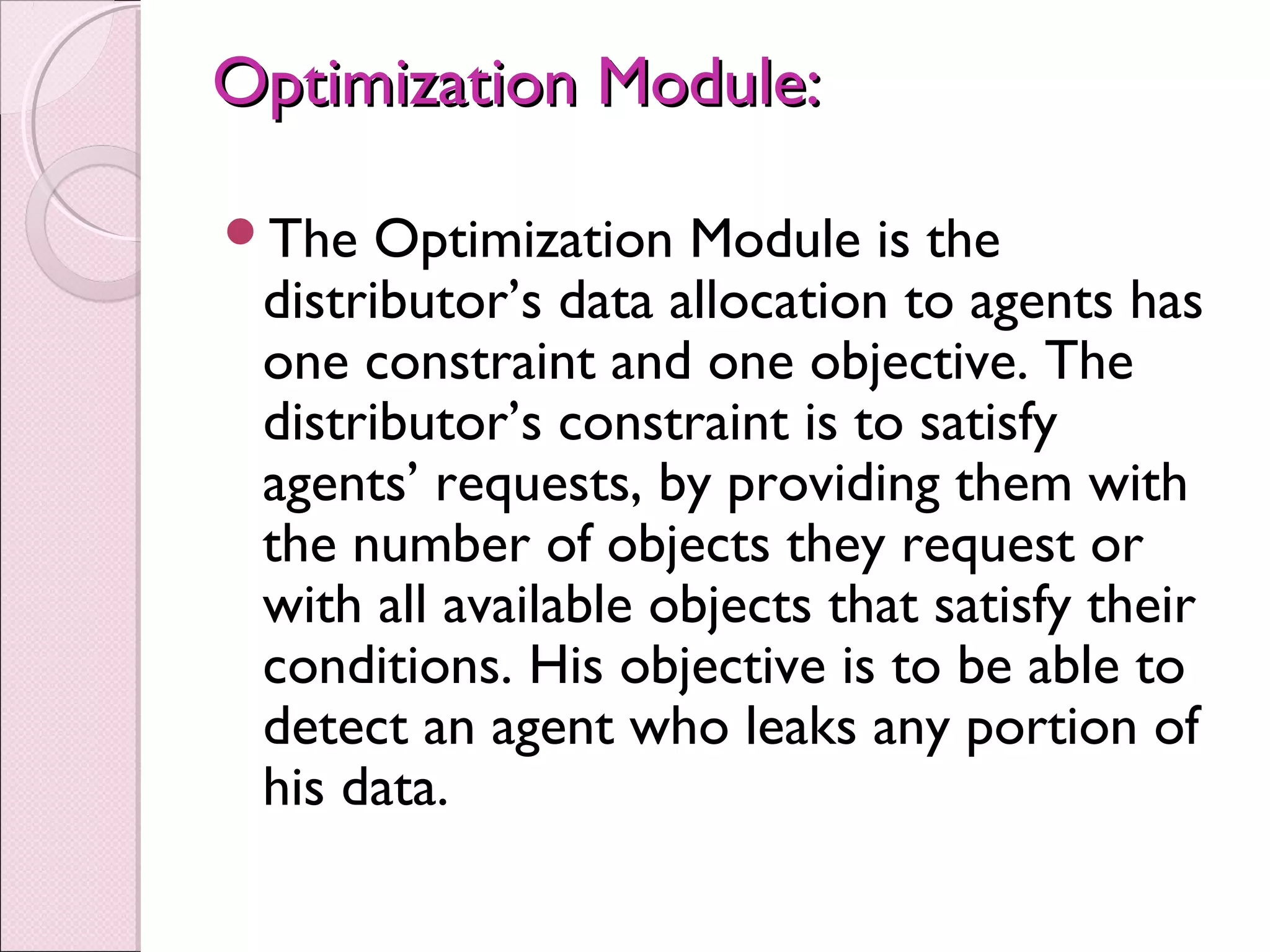
This document proposes a system to detect data leakage from agents by improving data allocation strategies and injecting fake records. The objective is to identify guilty agents that leak data by giving them enough evidence. It describes how current systems can detect hackers but lack sufficient evidence. The proposed system addresses this by using algorithms to intelligently distribute data and add fake objects, allowing accurate tracing of leakers. It outlines the modules for data allocation, fake objects, optimization, and distribution. The goal is to satisfy agent requests while enabling detection of any agents that leak portions of distributed data.