Embed presentation
Download as PDF, PPTX




















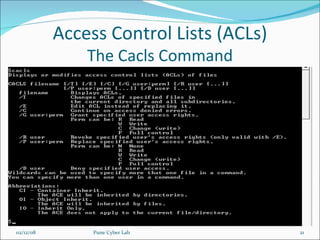



























This document discusses various techniques for hiding data in the Microsoft Windows operating system. It covers logical techniques like assigning hidden and system attributes, changing file extensions and icons. It also discusses more advanced techniques like using alternate data streams that allow hiding data in files, and using class identifiers (CLSIDs) meant for special folders for regular folders to disguise hidden data. The document provides an overview of the NTFS file system used by Windows and how its alternate data stream feature can be exploited for data hiding. It also recommends some tools that can be used to detect hidden data streams.















































