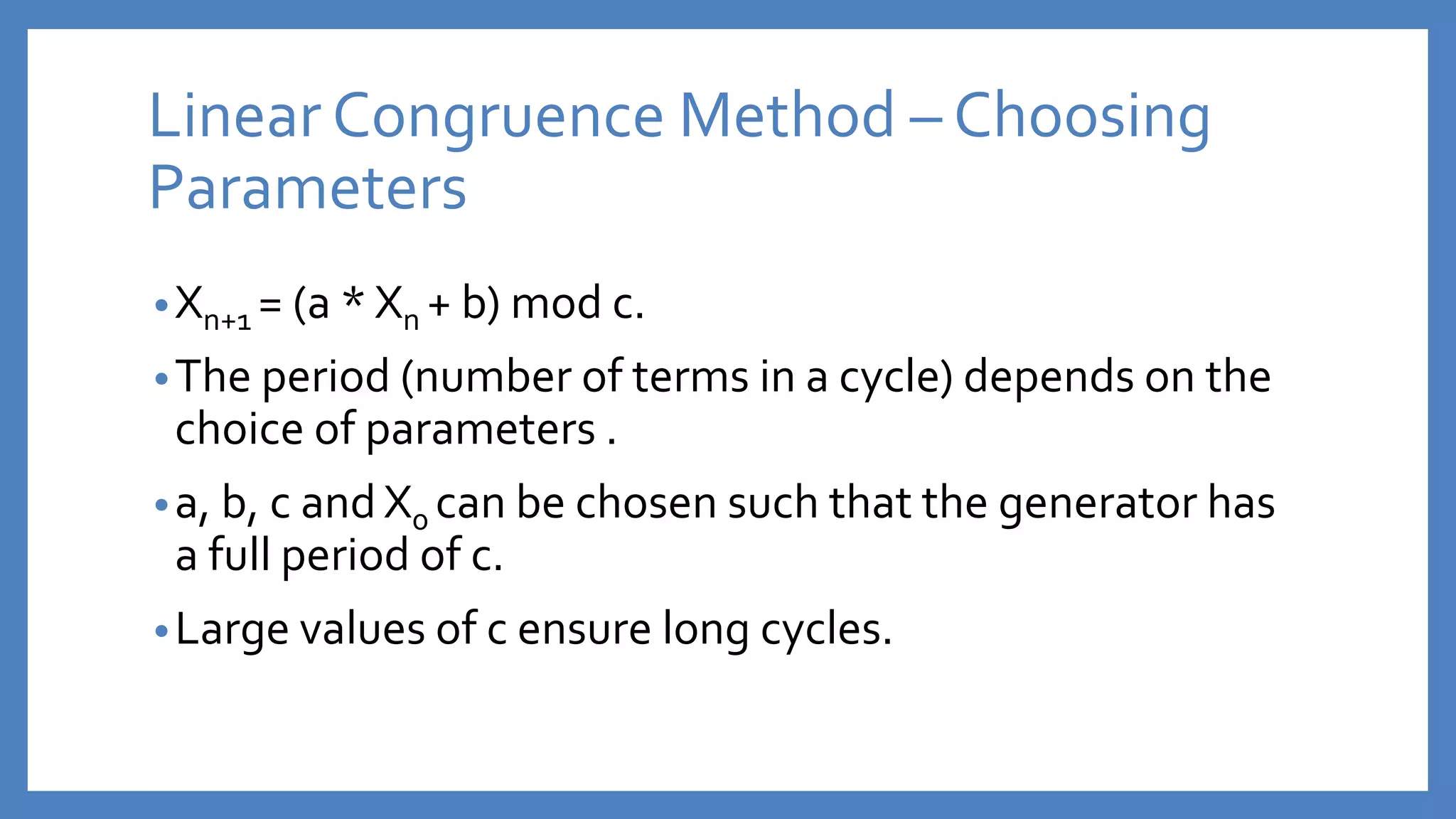
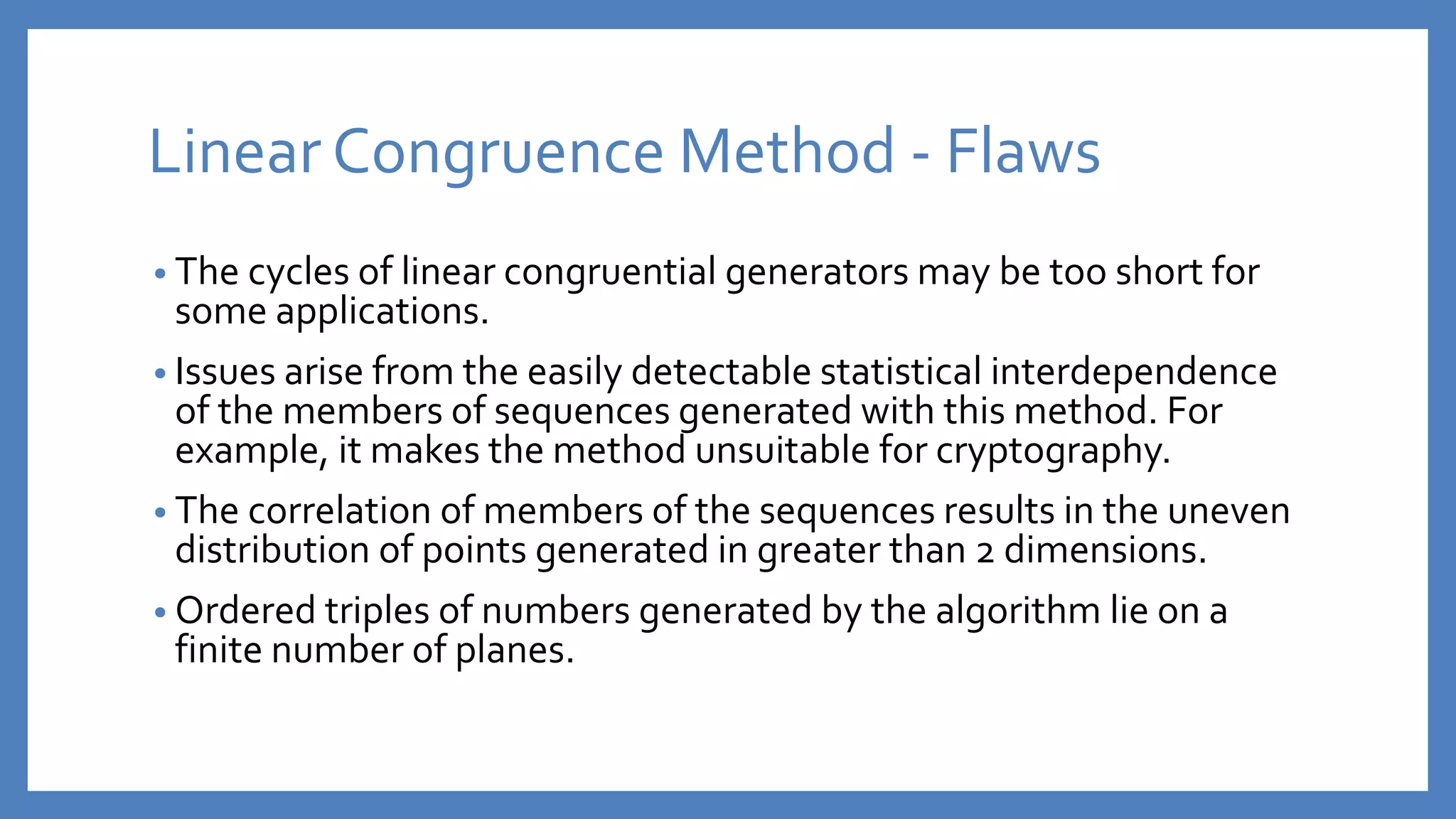
The document discusses pseudo-random number generators (PRNGs) and different algorithms used to generate pseudo-random numbers, including the middle-square method, linear congruence method, and MersenneTwister. PRNGs are useful for applications like cryptography, games, and statistics, but different algorithms have strengths best suited for different uses. Parameters must be carefully chosen for reliable sequences without repeats or quick degeneration.