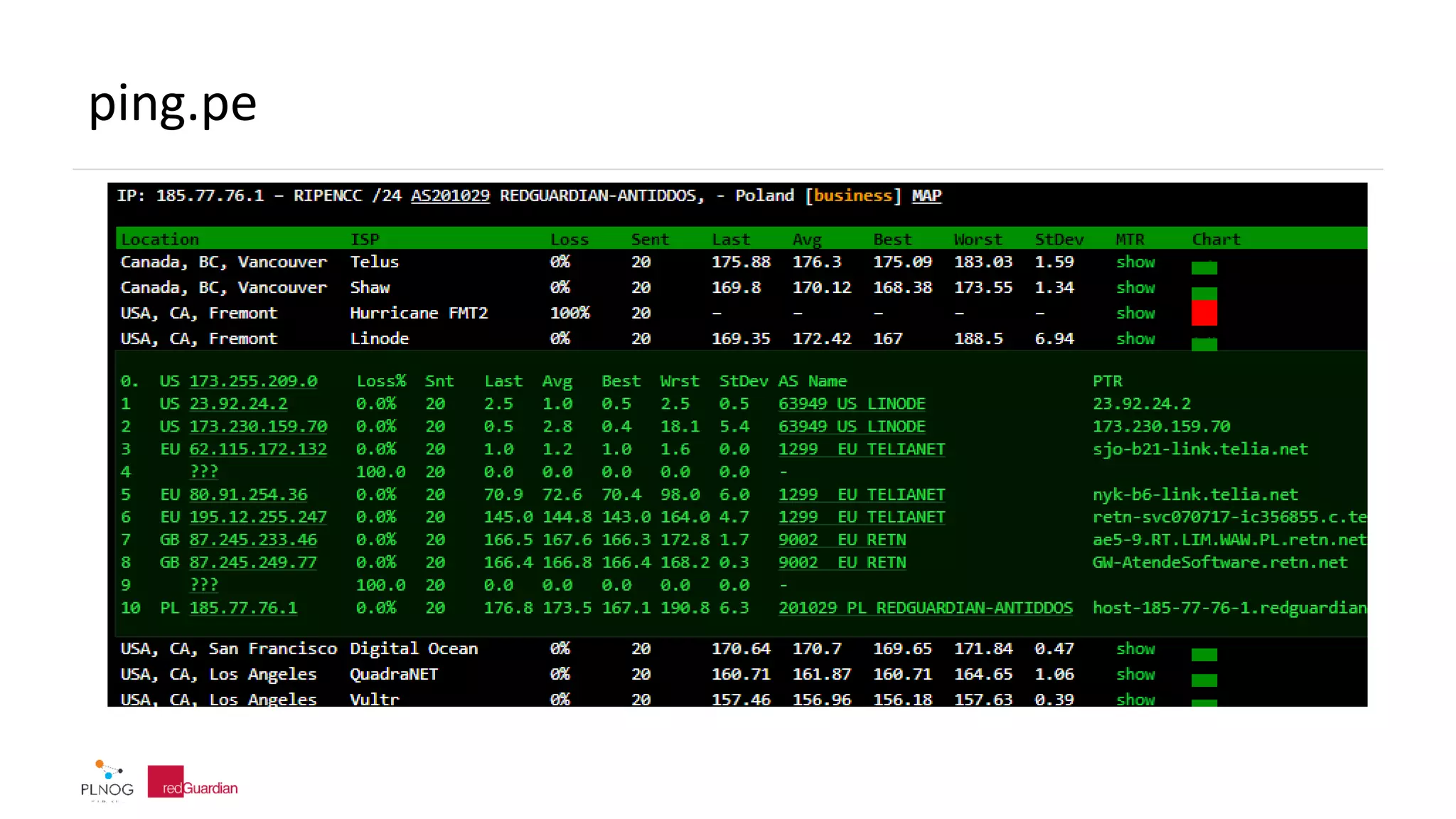
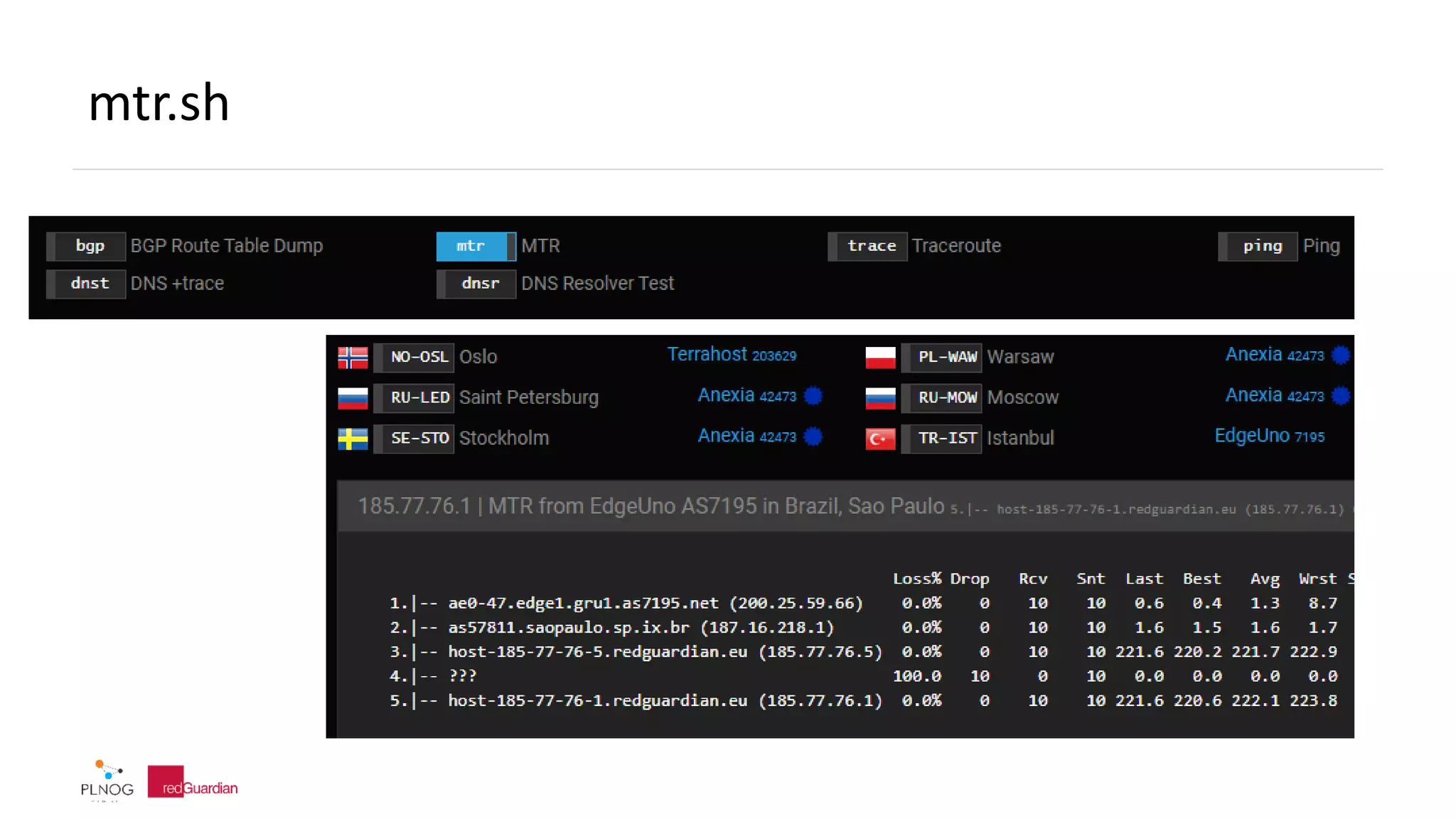
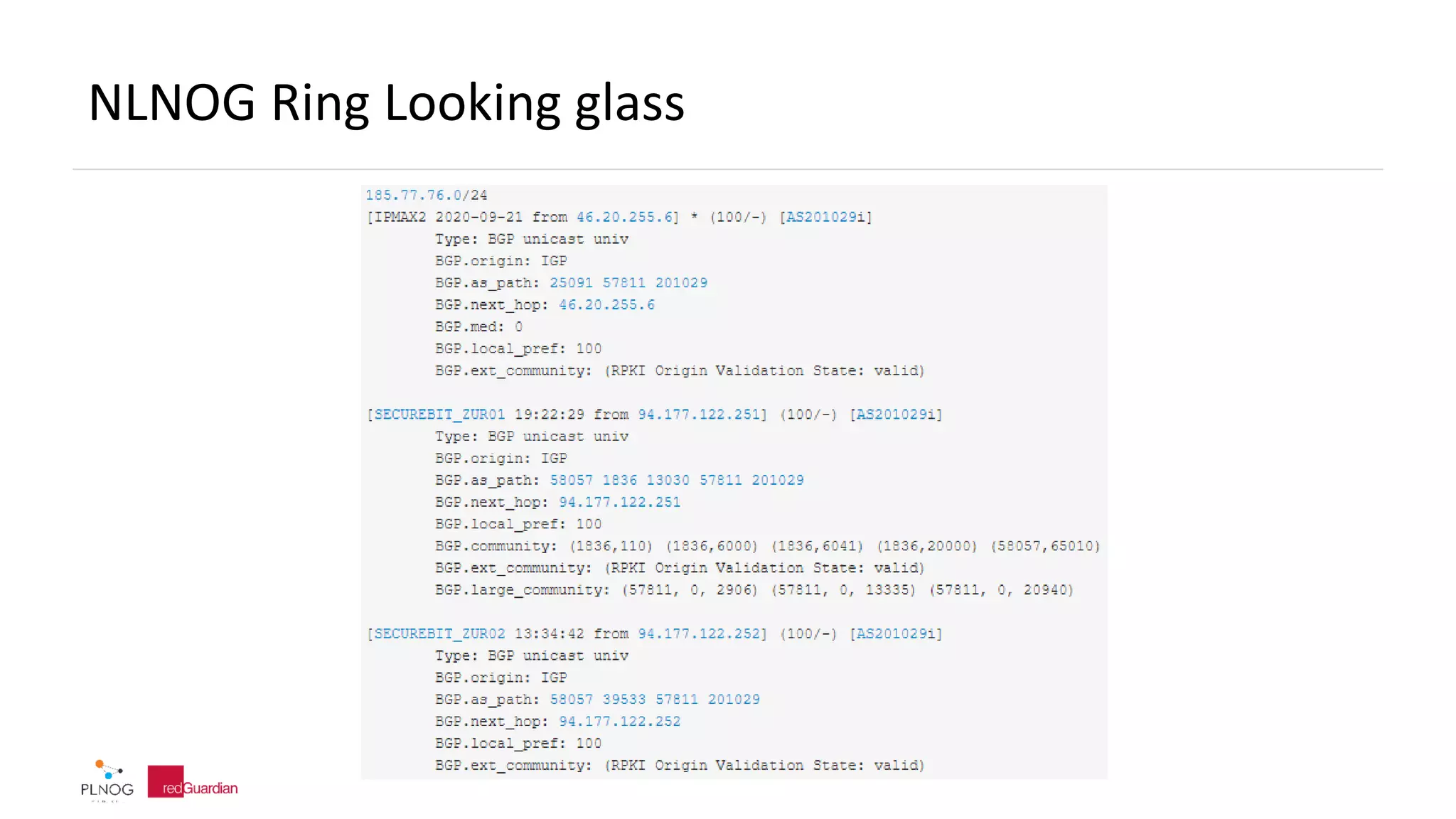
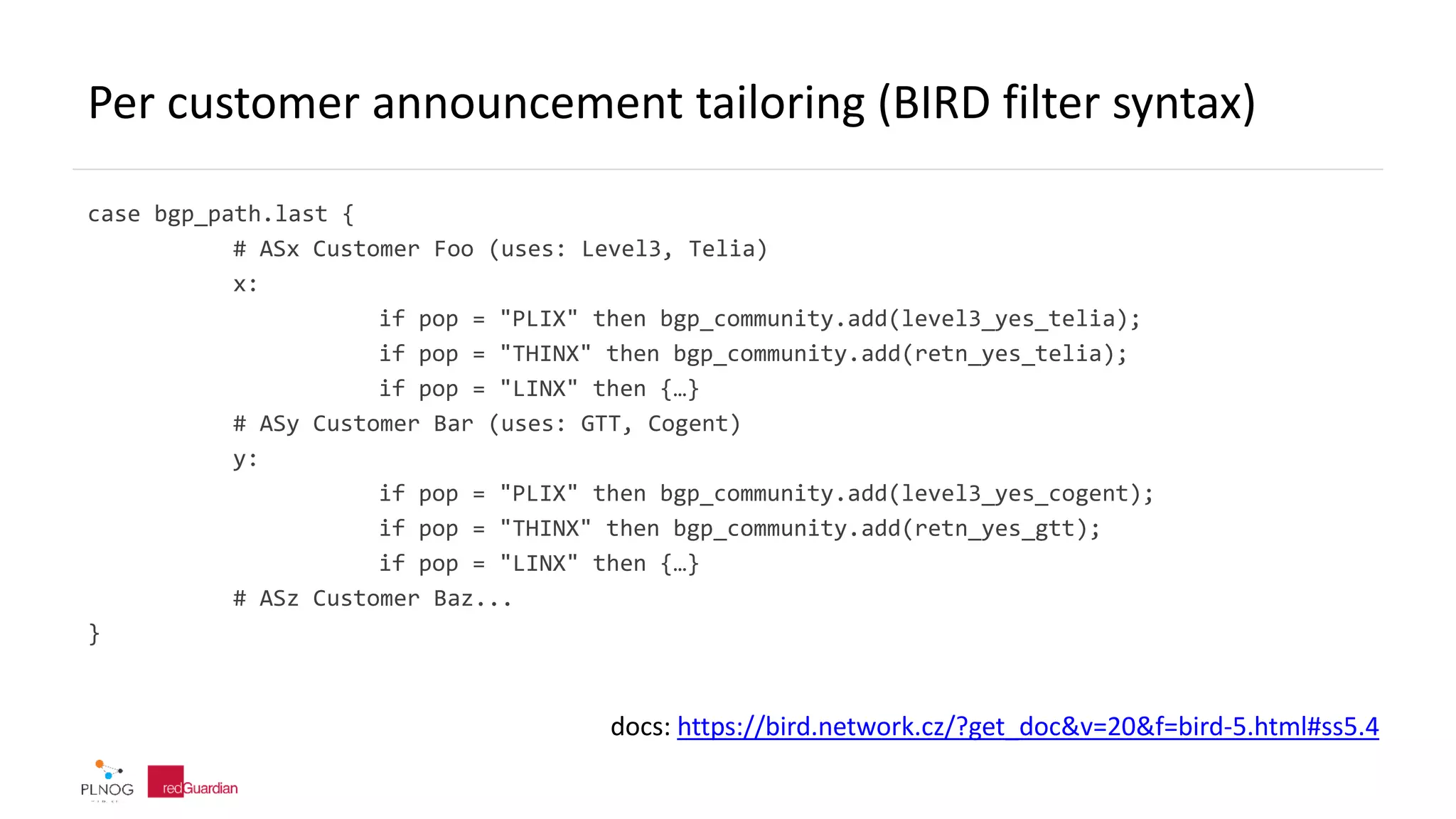
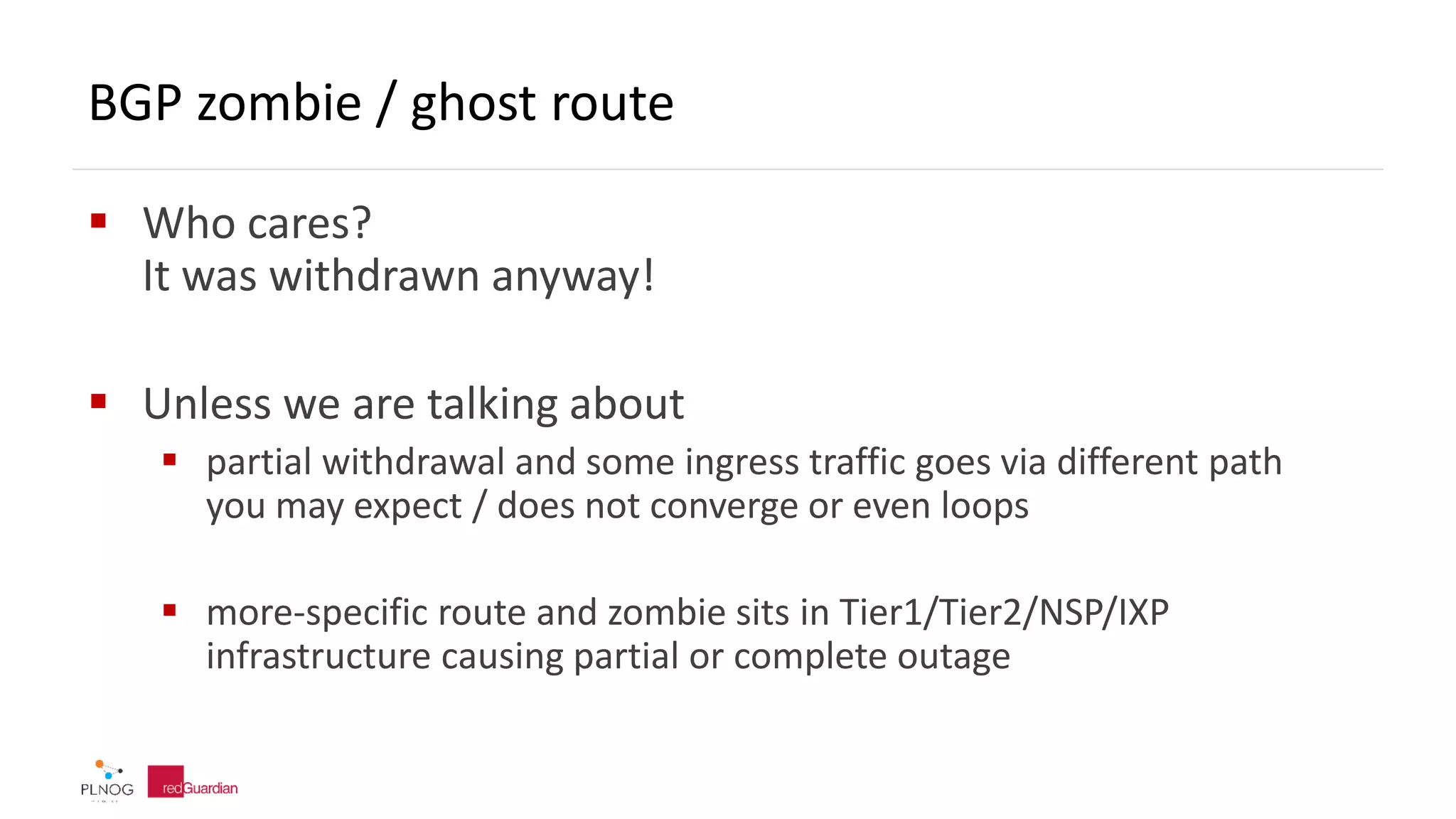
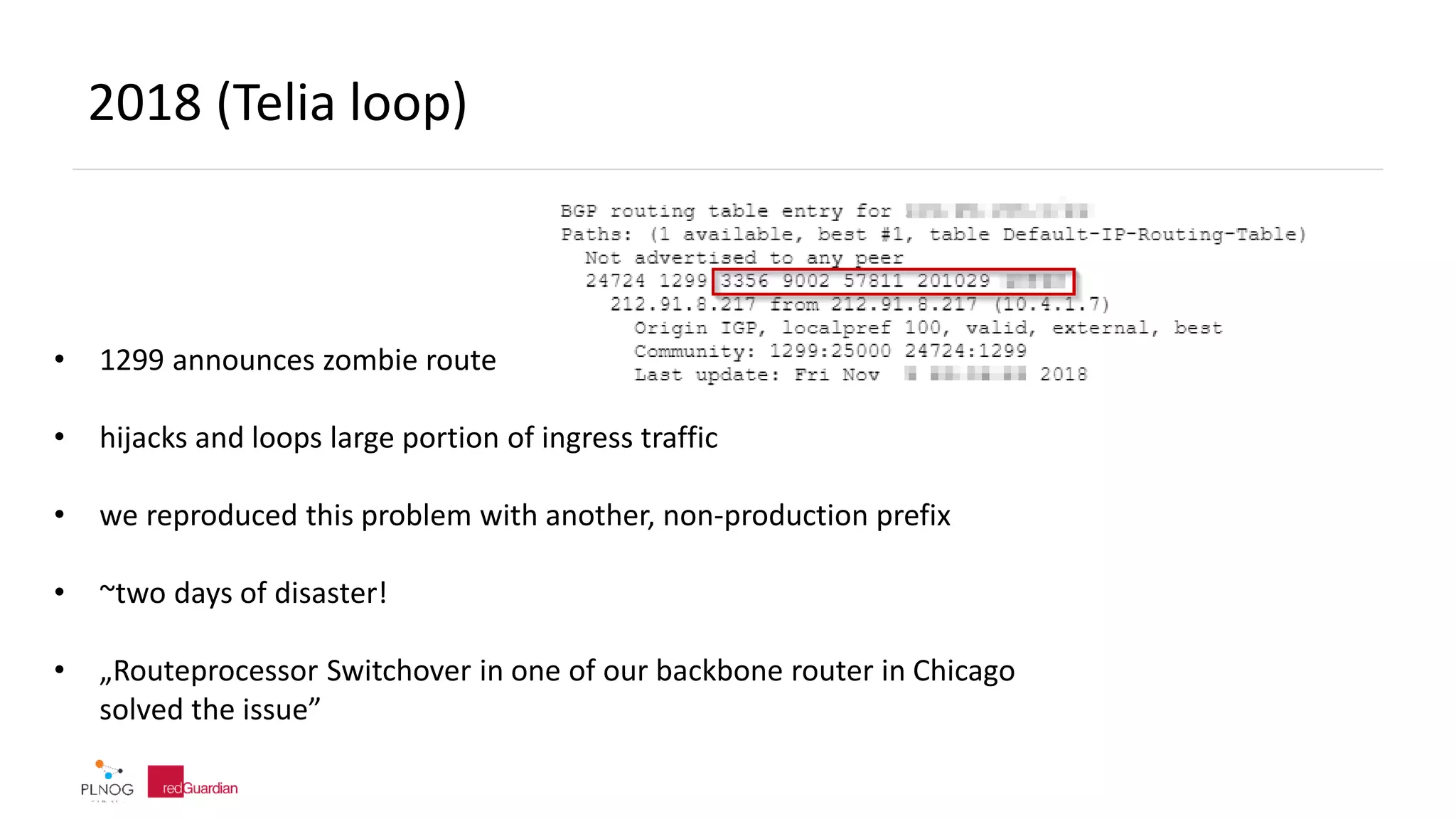
The document discusses BGP zombie routes, which occur when an active routing table entry remains for a prefix that has been withdrawn by its origin network. This can cause issues like partial outages or routing loops. The document provides examples of real-world incidents involving zombie routes, including outages at Telia, Interoute, and CenturyLink/Level3. It also covers ways to detect and debug zombie routes, such as looking for routing loops or inconsistencies using traceroute. Mitigation strategies are also discussed.











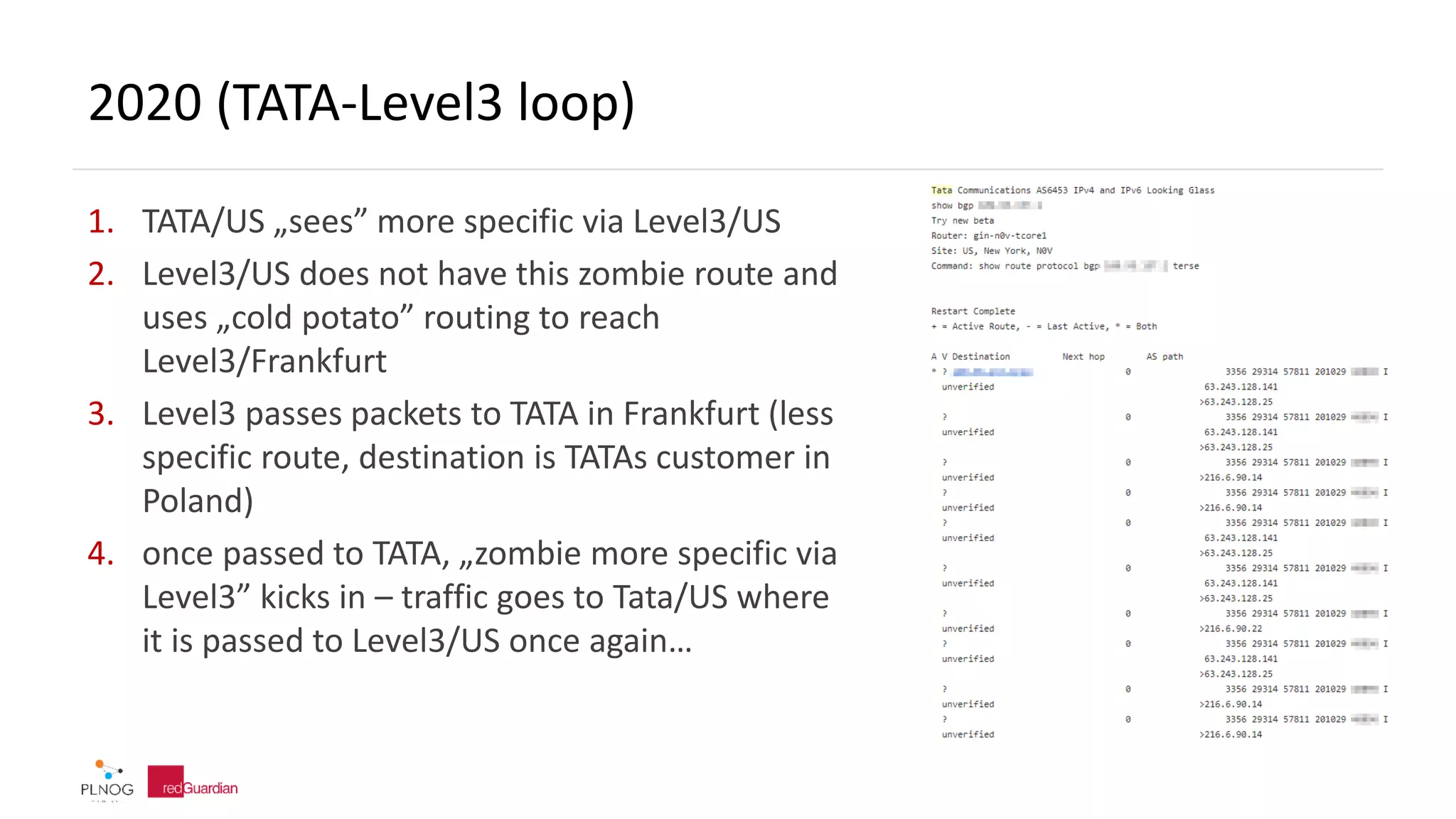
![2020 (TATA-Level3 loop)
Router: gin-n0v-tcore1
Site: US, New York, N0V
Command: traceroute inet4 x as-number-lookup
traceroute to x (x), 30 hops max, 52 byte packets
1 if-ae-7-5.tcore1.nto-newyork.as6453.net (63.243.128.141) 2.990 ms 1.545 ms 1.369 ms
MPLS Label=415563 CoS=0 TTL=1 S=1
2 if-ae-9-2.tcore1.n75-newyork.as6453.net (63.243.128.122) 1.653 ms 1.704 ms 1.439 ms
3 ae-7.edge2.NewYorkCity6.Level3.net (4.68.39.49) [AS 3356] 3.038 ms 1.118 ms 3.086 ms
4 ae-1-3103.ear3.Frankfurt1.Level3.net (4.69.163.86) [AS 3356] 82.672 ms 81.989 ms 82.221 ms
5 ix-ae-18-0.tcore1.fr0-frankfurt.as6453.net (195.219.50.49) 82.072 ms 81.949 ms 81.731 ms
6 if-ae-4-2.tcore2.fnm-frankfurt.as6453.net (195.219.87.17) 87.154 ms if-ae-59-2.tcore2.fnm-
frankfurt.as6453.net (195.219.87.194) 87.064 ms 87.038 ms
MPLS Label=486720 CoS=0 TTL=1 S=1
7 if-ae-30-2.tcore1.pvu-paris.as6453.net (80.231.153.89) 86.645 ms if-ae-9-3.tcore1.pvu-
paris.as6453.net (195.219.87.14) 87.036 ms if-ae-9-2.tcore1.pvu-paris.as6453.net (195.219.87.10)
87.412 ms
MPLS Label=345609 CoS=0 TTL=1 S=1
8 if-ae-11-2.tcore1.pye-paris.as6453.net (80.231.153.50) 87.357 ms 87.522 ms 86.774 ms
MPLS Label=525823 CoS=0 TTL=1 S=1
9 if-ae-3-2.tcore1.l78-london.as6453.net (80.231.154.143) 87.089 ms 86.984 ms 87.120 ms
MPLS Label=558832 CoS=0 TTL=1 S=1
10 if-ae-66-2.tcore2.nto-newyork.as6453.net (80.231.130.106) 86.711 ms 86.872 ms 87.689 ms
MPLS Label=300093 CoS=0 TTL=1 S=1
11 if-ae-12-2.tcore1.n75-newyork.as6453.net (66.110.96.5) 86.838 ms 86.749 ms 86.667 ms
12 ae-7.edge2.NewYorkCity6.Level3.net (4.68.39.49) [AS 3356] 87.039 ms 86.777 ms 108.465 ms
13 ae-1-3103.ear3.Frankfurt1.Level3.net (4.69.163.86) [AS 3356] 167.903 ms 167.436 ms 167.919
ms
14 ix-ae-18-0.tcore1.fr0-frankfurt.as6453.net (195.219.50.49) 167.316 ms 167.016 ms 167.156 ms
15 if-ae-4-2.tcore2.fnm-frankfurt.as6453.net (195.219.87.17) 172.082 ms 172.347 ms if-ae-59-
2.tcore2.fnm-frankfurt.as6453.net (195.219.87.194) 172.688 ms
MPLS Label=486720 CoS=0 TTL=1 S=1
16 if-ae-9-3.tcore1.pvu-paris.as6453.net (195.219.87.14) 172.403 ms if-ae-9-2.tcore1.pvu-
paris.as6453.net (195.219.87.10) 177.623 ms 172.588 ms
MPLS Label=345609 CoS=0 TTL=1 S=1
17 if-ae-11-2.tcore1.pye-paris.as6453.net (80.231.153.50) 173.956 ms 176.402 ms 172.581
ms
MPLS Label=525823 CoS=0 TTL=1 S=1
18 if-ae-3-2.tcore1.l78-london.as6453.net (80.231.154.143) 172.784 ms 172.592 ms 172.921
ms
MPLS Label=558832 CoS=0 TTL=1 S=1
19 if-ae-66-2.tcore2.nto-newyork.as6453.net (80.231.130.106) 172.660 ms 172.503 ms
172.937 ms
MPLS Label=300093 CoS=0 TTL=1 S=1
20 if-ae-12-2.tcore1.n75-newyork.as6453.net (66.110.96.5) 172.258 ms 172.540 ms 171.995
ms
21 ae-7.edge2.NewYorkCity6.Level3.net (4.68.39.49) [AS 3356] 183.732 ms 171.950 ms
172.068 ms
22 ae-1-3103.ear3.Frankfurt1.Level3.net (4.69.163.86) [AS 3356] 252.748 ms 252.855 ms
252.719 ms
23 ix-ae-18-0.tcore1.fr0-frankfurt.as6453.net (195.219.50.49) 253.215 ms 253.049 ms
252.474 ms
24 if-ae-59-2.tcore2.fnm-frankfurt.as6453.net (195.219.87.194) 258.598 ms if-ae-4-
2.tcore2.fnm-frankfurt.as6453.net (195.219.87.17) 258.467 ms 257.584 ms
MPLS Label=486720 CoS=0 TTL=1 S=1
25 if-ae-9-3.tcore1.pvu-paris.as6453.net (195.219.87.14) 257.906 ms 257.857 ms if-ae-9-
2.tcore1.pvu-paris.as6453.net (195.219.87.10) 258.308 ms
MPLS Label=345609 CoS=0 TTL=1 S=1
26 if-ae-11-2.tcore1.pye-paris.as6453.net (80.231.153.50) 257.546 ms 257.812 ms 268.691
ms
MPLS Label=525823 CoS=0 TTL=1 S=1
27 if-ae-3-2.tcore1.l78-london.as6453.net (80.231.154.143) 261.149 ms 257.873 ms 258.124
ms
MPLS Label=558832 CoS=0 TTL=1 S=1
28 if-ae-66-2.tcore2.nto-newyork.as6453.net (80.231.130.106) 257.746 ms 257.491 ms
258.035 ms
MPLS Label=300093 CoS=0 TTL=1 S=1
29 if-ae-12-2.tcore1.n75-newyork.as6453.net (66.110.96.5) 257.737 ms 258.226 ms 257.614
ms
30 ae-7.edge2.NewYorkCity6.Level3.net (4.68.39.49) [AS 3356] 257.587 ms 259.322 ms
258.347 ms](https://image.slidesharecdn.com/redguardianplnog202009zombieroutes-200929105151/75/BGP-zombie-routes-15-2048.jpg)
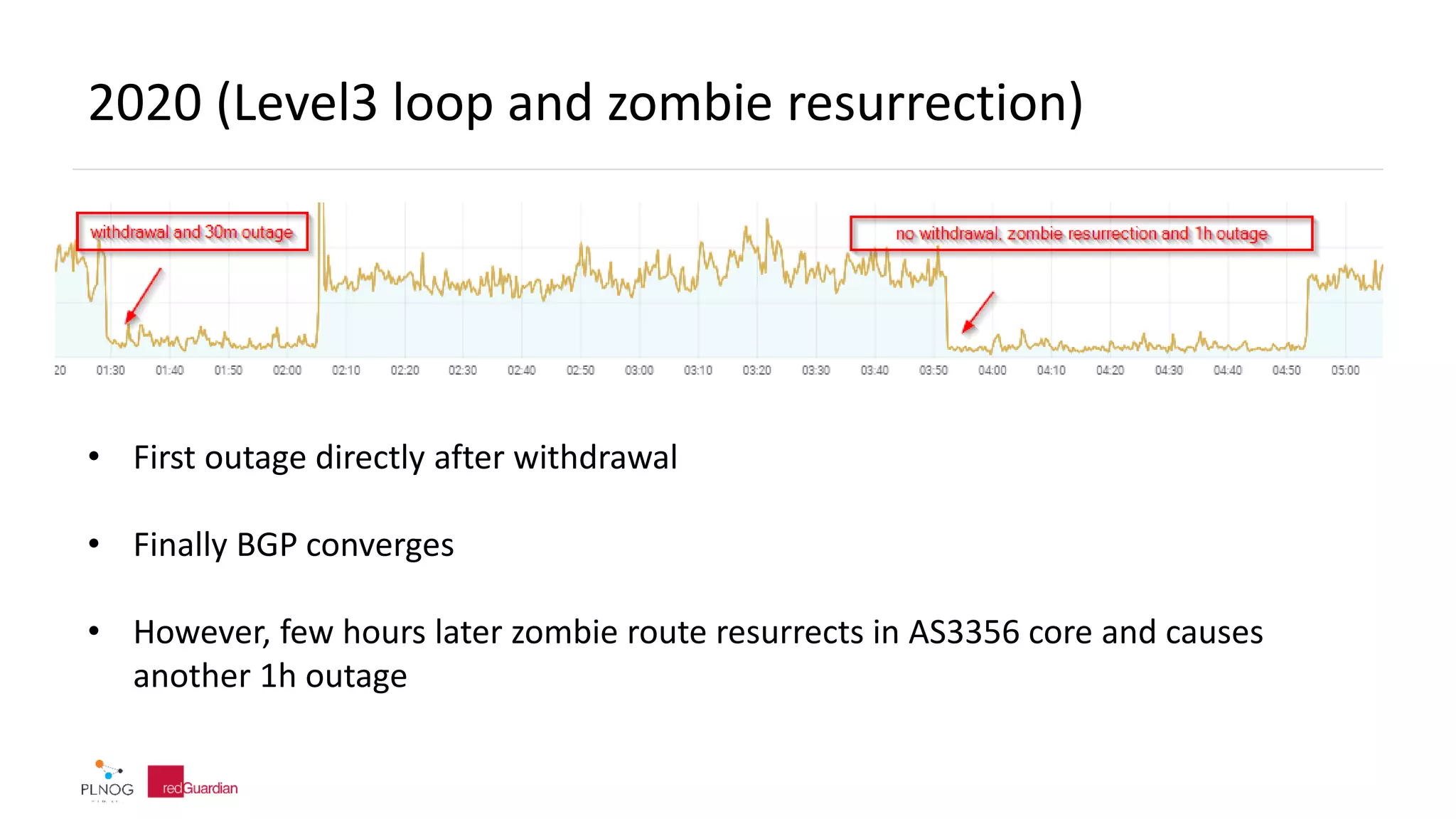
![2020 (TATA-Level3 loop)
…
20 if-ae-12-2.tcore1.n75-newyork.as6453.net (66.110.96.5) 172.258 ms 172.540 ms 171.995 ms
21 ae-7.edge2.NewYorkCity6.Level3.net (4.68.39.49) [AS 3356] 183.732 ms 171.950 ms 172.068 ms
22 ae-1-3103.ear3.Frankfurt1.Level3.net (4.69.163.86) [AS 3356] 252.748 ms 252.855 ms 252.719 ms
23 ix-ae-18-0.tcore1.fr0-frankfurt.as6453.net (195.219.50.49) 253.215 ms 253.049 ms 252.474 ms
24 if-ae-59-2.tcore2.fnm-frankfurt.as6453.net (195.219.87.194) 258.598 ms if-ae-4-2.tcore2.fnm-
frankfurt.as6453.net (195.219.87.17) 258.467 ms 257.584 ms
MPLS Label=486720 CoS=0 TTL=1 S=1
25 if-ae-9-3.tcore1.pvu-paris.as6453.net (195.219.87.14) 257.906 ms 257.857 ms if-ae-9-2.tcore1.pvu-
paris.as6453.net (195.219.87.10) 258.308 ms
MPLS Label=345609 CoS=0 TTL=1 S=1
26 if-ae-11-2.tcore1.pye-paris.as6453.net (80.231.153.50) 257.546 ms 257.812 ms 268.691 ms
MPLS Label=525823 CoS=0 TTL=1 S=1
27 if-ae-3-2.tcore1.l78-london.as6453.net (80.231.154.143) 261.149 ms 257.873 ms 258.124 ms
MPLS Label=558832 CoS=0 TTL=1 S=1
28 if-ae-66-2.tcore2.nto-newyork.as6453.net (80.231.130.106) 257.746 ms 257.491 ms 258.035 ms
MPLS Label=300093 CoS=0 TTL=1 S=1
29 if-ae-12-2.tcore1.n75-newyork.as6453.net (66.110.96.5) 257.737 ms 258.226 ms 257.614 ms
…](https://image.slidesharecdn.com/redguardianplnog202009zombieroutes-200929105151/75/BGP-zombie-routes-16-2048.jpg)

![2020 Aug (well known Centurylink/Level3-related outage)
NANOG mailing list threads:
„Centurylink having a bad morning?”
„[outages] Major Level3 (CenturyLink) Issues”
https://mailman.nanog.org/pipermail/nanog/2020-August/thread.html
https://mailman.nanog.org/pipermail/nanog/2020-September/thread.html
https://puck.nether.net/pipermail/outages/2020-August/013204.html](https://image.slidesharecdn.com/redguardianplnog202009zombieroutes-200929105151/75/BGP-zombie-routes-20-2048.jpg)