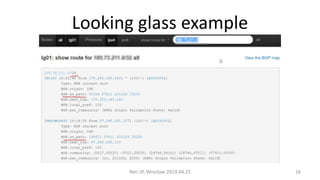
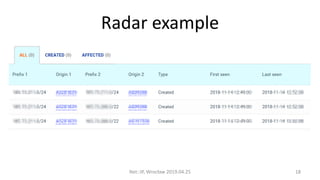
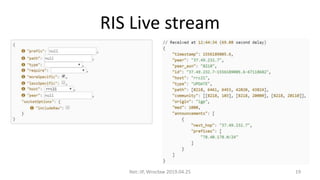
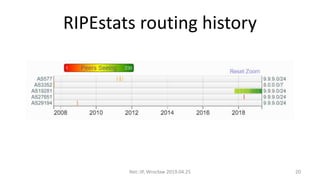
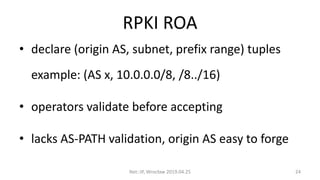
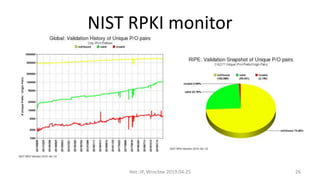
This document summarizes BGP hijacks and leaks, both malicious and unintentional. It provides examples of past hijacking incidents and explains how hijacks can occur due to factors like more specific routes, local preference, and AS path manipulation. Detection methods are discussed, including looking glasses, BGP monitoring tools, and RIPE resources. Prevention techniques are also covered, such as route validation using RPKI and BGPsec, as well as tools the speaker recommends for analyzing routing data. The presentation concludes with a proposed live demo of hijacking a third-party prefix.








![Howto, cont.
ExaBGP
route victim/24 next-hop self as-path [ foo ] community [ a:b ];
BIRD
bgp_path.empty;
bgp_path.prepend(foo);
Net::IP, Wrocław 2019.04.25 10](https://image.slidesharecdn.com/bgphijackingnetipmeetupwroclaw201904-190427203313/85/BGP-hijacks-and-leaks-10-320.jpg)