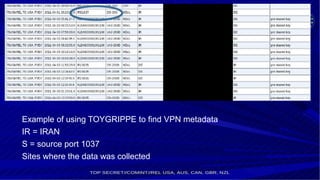
The NSA has a program called OTP that targets VPN users. It has a team called OTTERCREAK that looks up VPN metadata of targets in repositories like TOYGRIPPE to define attacks. The team works with other NSA groups like TAO to decrypt traffic if they have exploits for the VPN protocols (e.g. recovering PSKs for IPsec) or can implant devices. They have decrypted traffic from services like PPTP, IPSec and SSH tunnels in the past by exploiting routers, protocols or gaining private keys. Running your own private VPN or using a service like PIA provides some protection but risks being targeted if the VPN is popular or if your ISP/network is exploited.

![NSA and VPNs
A recent article on [Der Spiegel] show lots of new attacks
SSL/TLS
PPTP
IPSEC
SSH
http://www.spiegel.de/international/world/nsa-documents-attacks-on-
vpn-ssl-tls-ssh-tor-a-1010525.html](https://image.slidesharecdn.com/nsaandvpn-150603153215-lva1-app6891/85/Nsa-and-vpn-2-320.jpg)