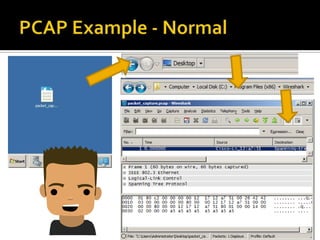
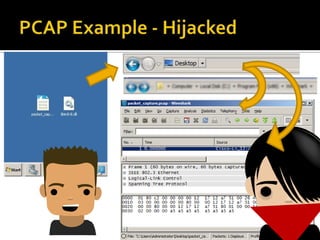
DLL hijacking is a technique that tricks a program into loading a malicious DLL instead of the expected one. It works by placing the malicious DLL in a location the program searches before its expected DLL path. An audit tool was demonstrated that automates detecting exploitable extensions by generating test files and monitoring the program and DLL loading behavior. The document proposes ways to deliver a malicious payload via a hijacked DLL and discusses mitigations like disabling WebDAV/SMB shares and having programs securely load DLLs.