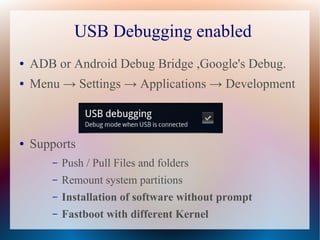
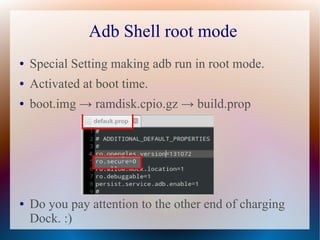
The document discusses security issues related to custom Android ROMs, emphasizing the importance of security reviews due to potential vulnerabilities. It explains the differences between stock and custom ROMs, their advantages, and how to modify them while highlighting security practices such as USB debugging and root access. Additionally, the document provides tips for developers and users to enhance security when using custom ROMs.