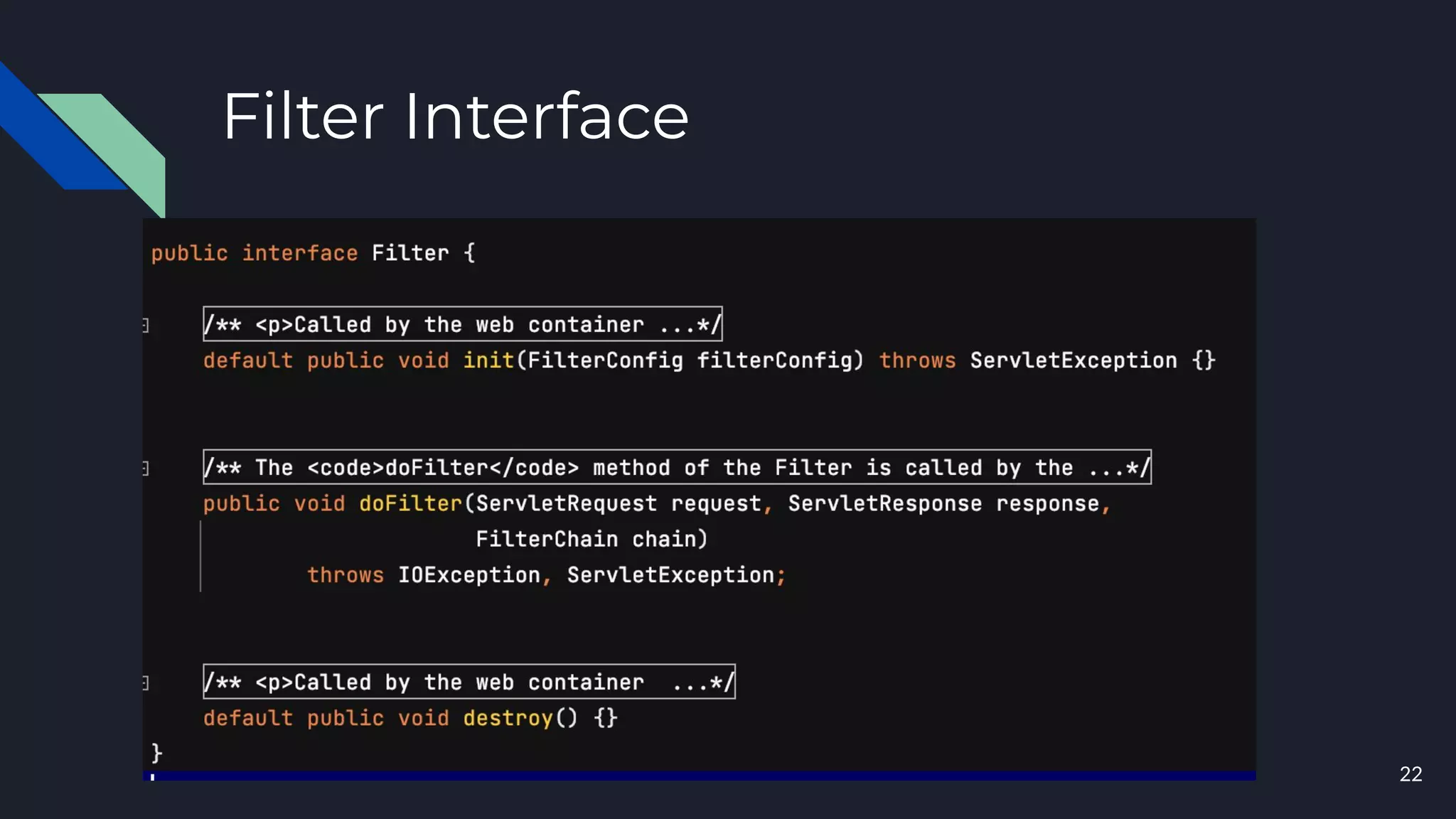
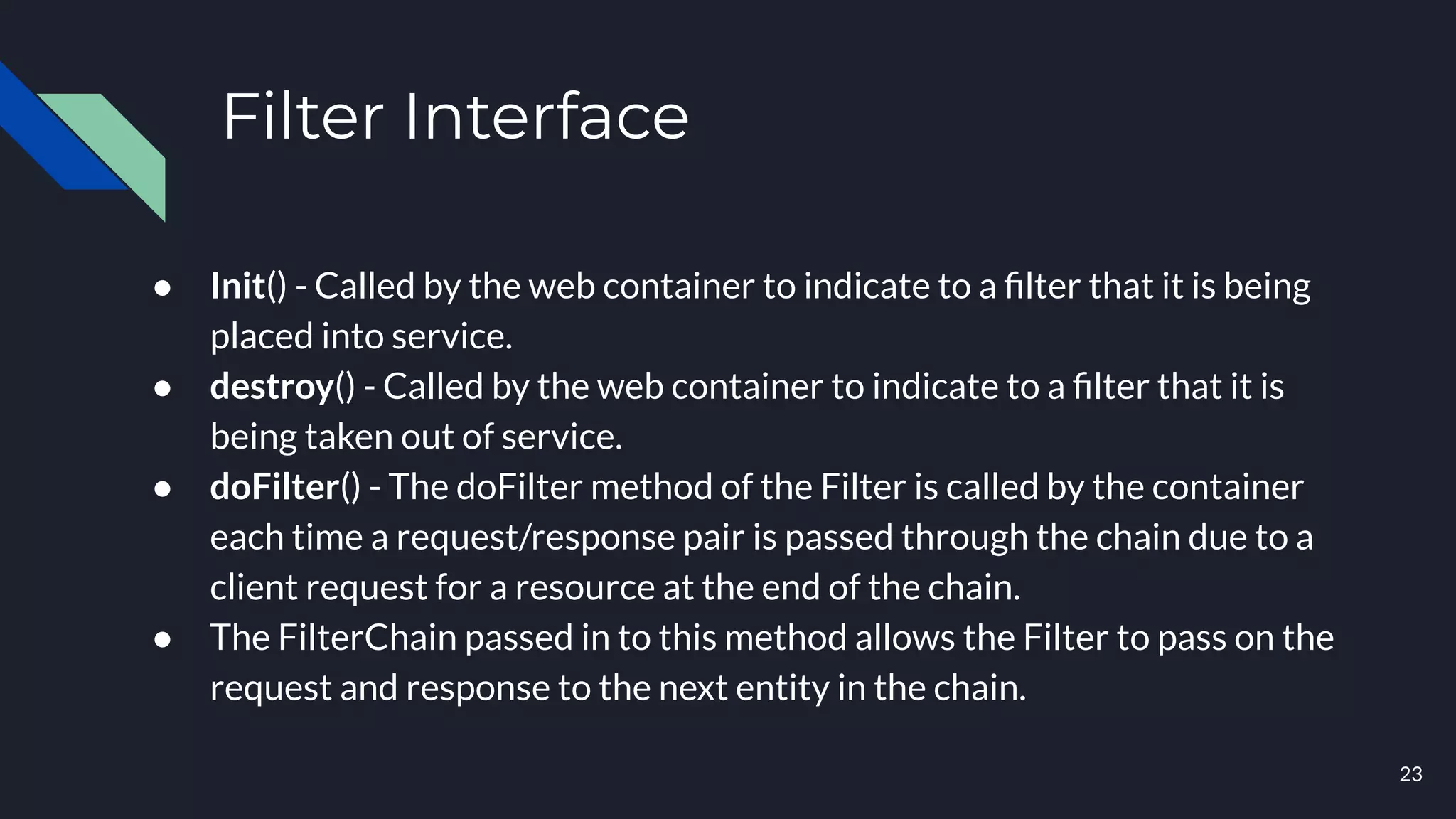
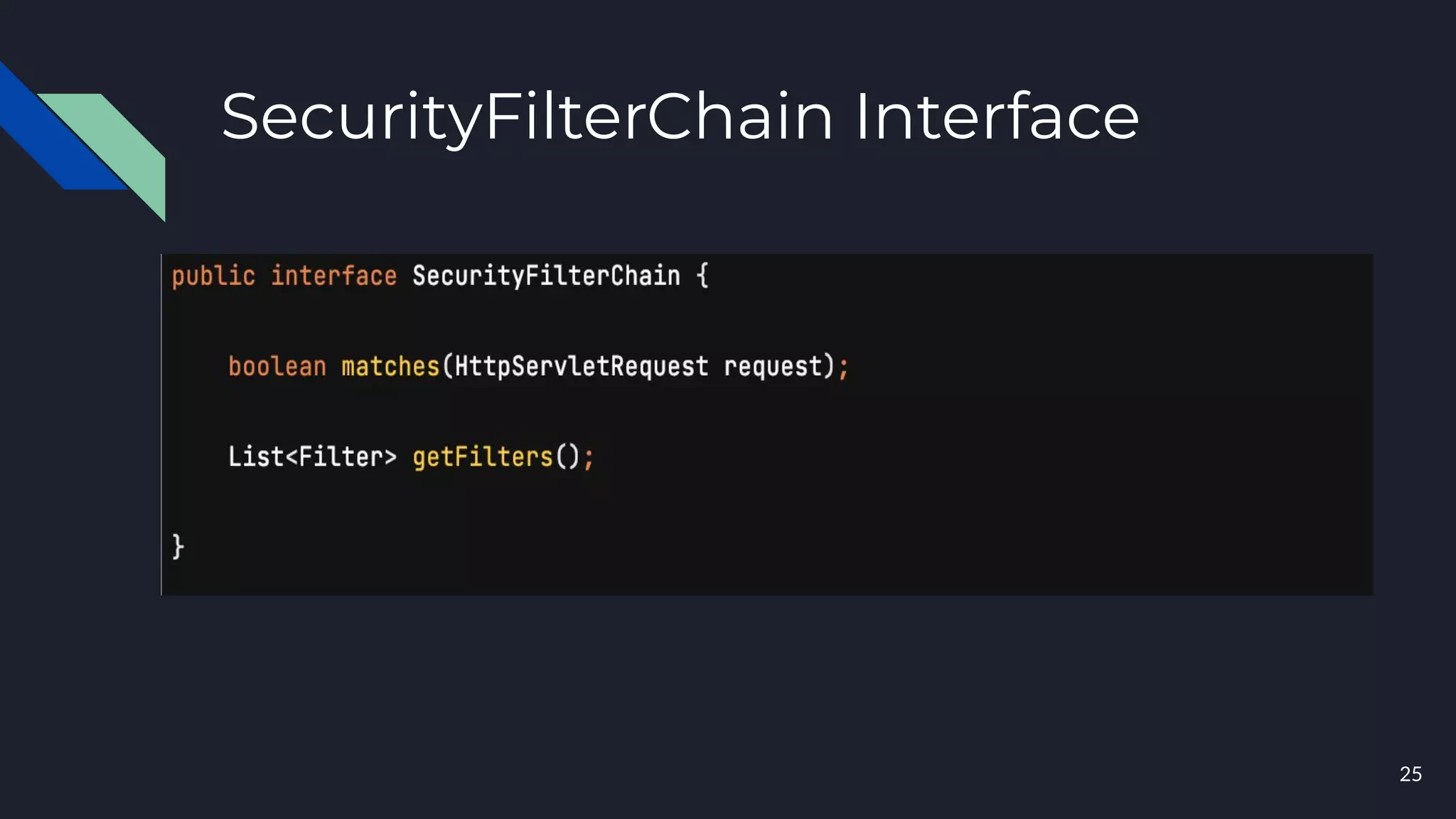
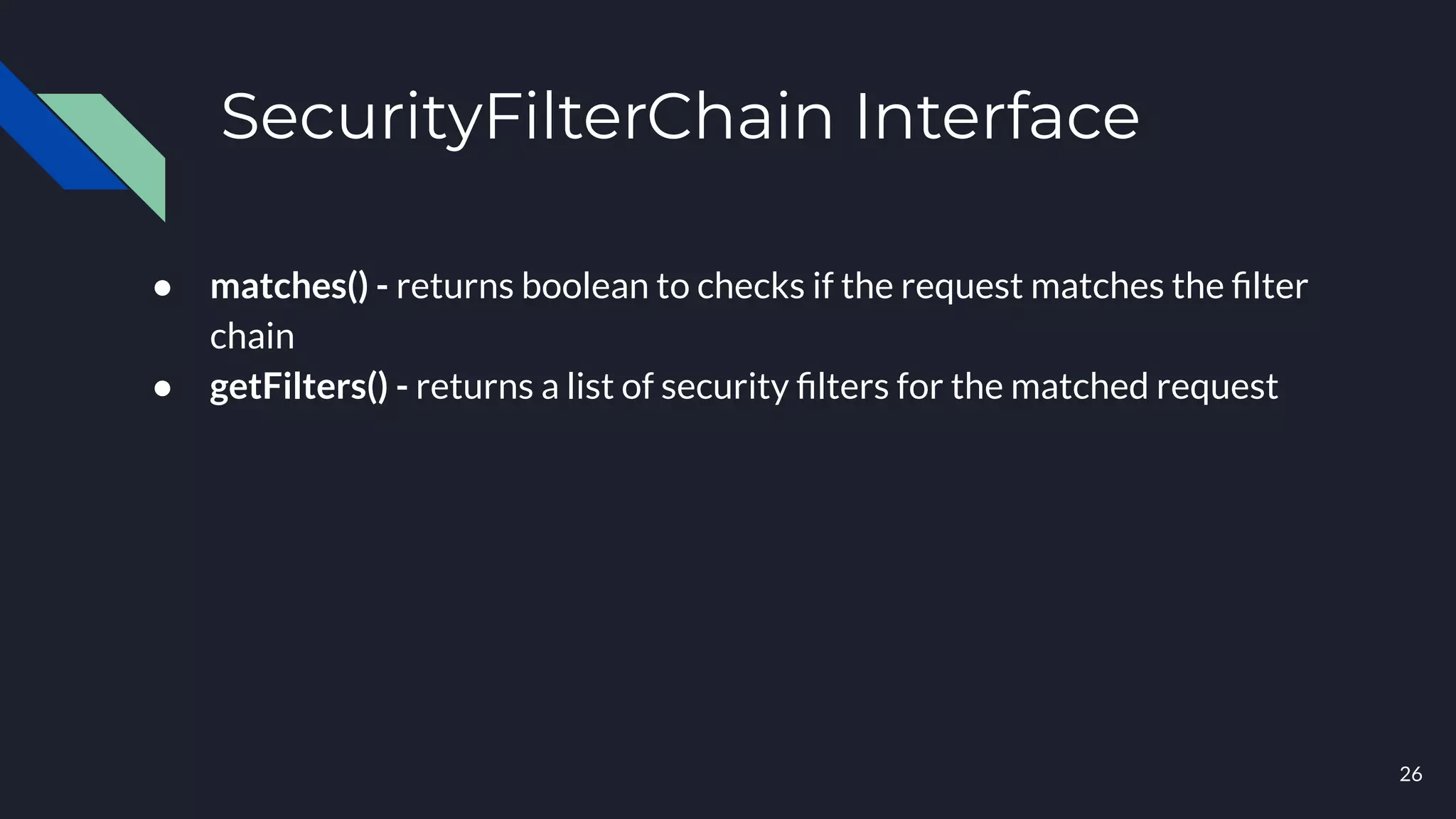
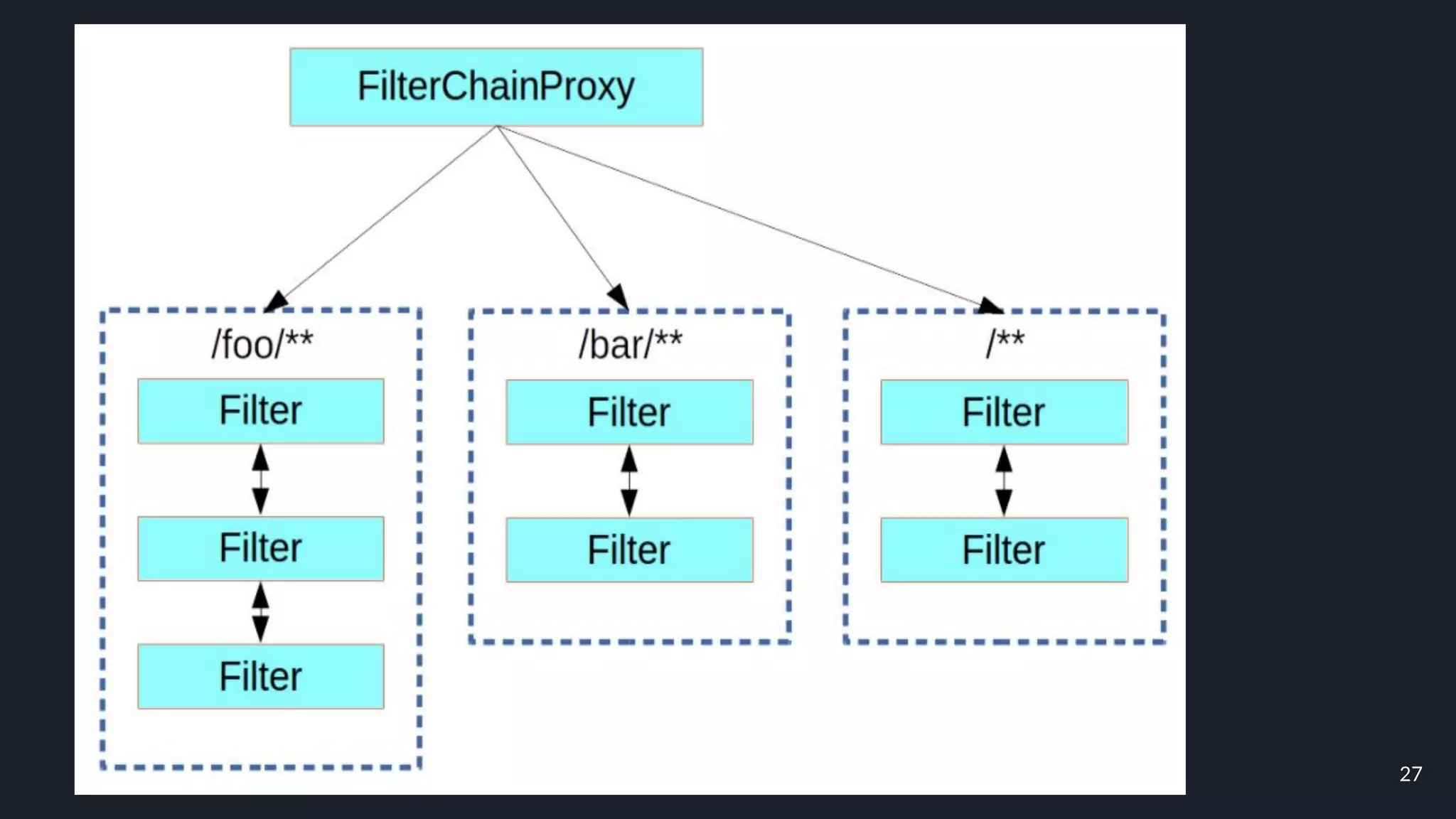
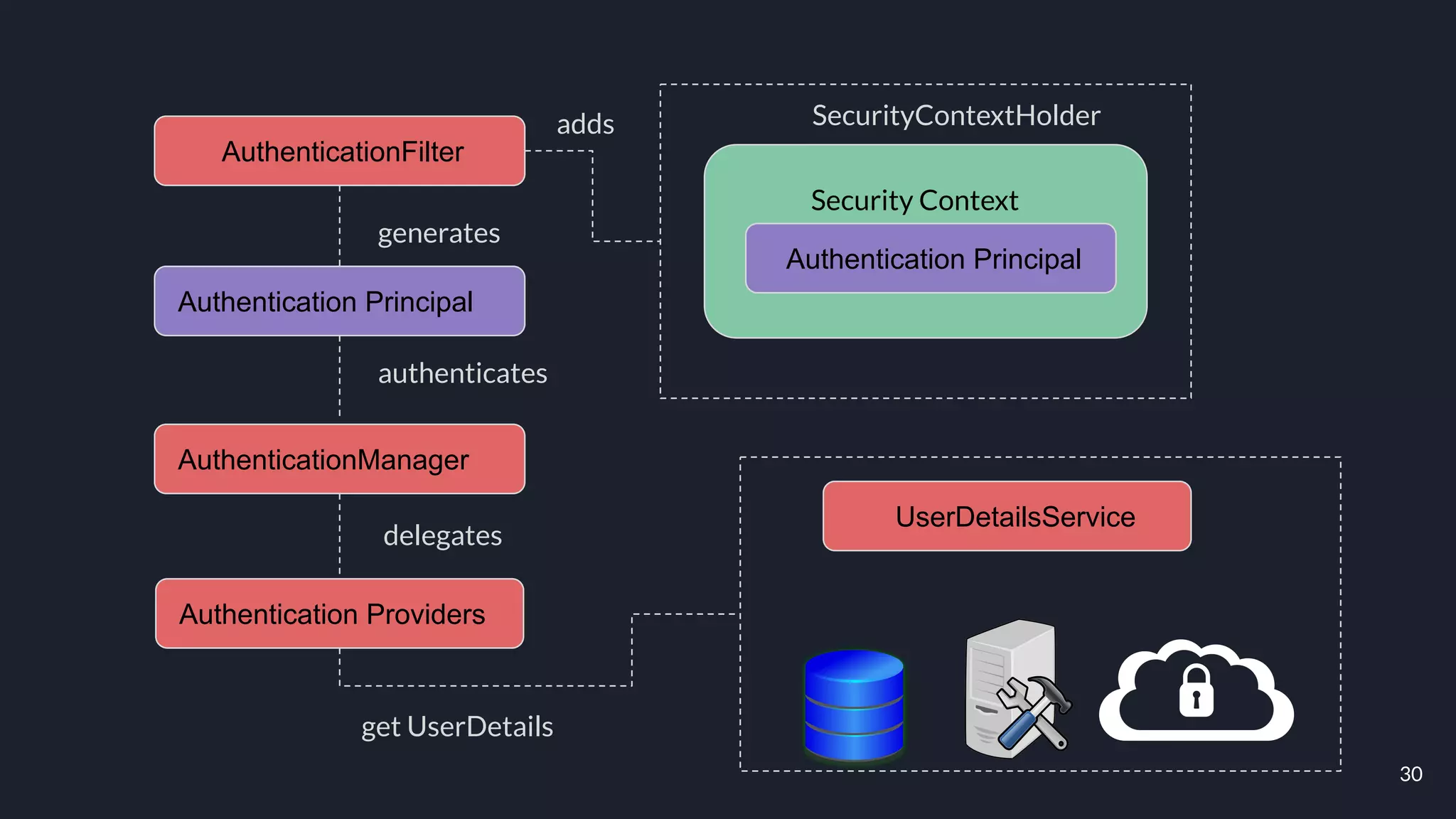
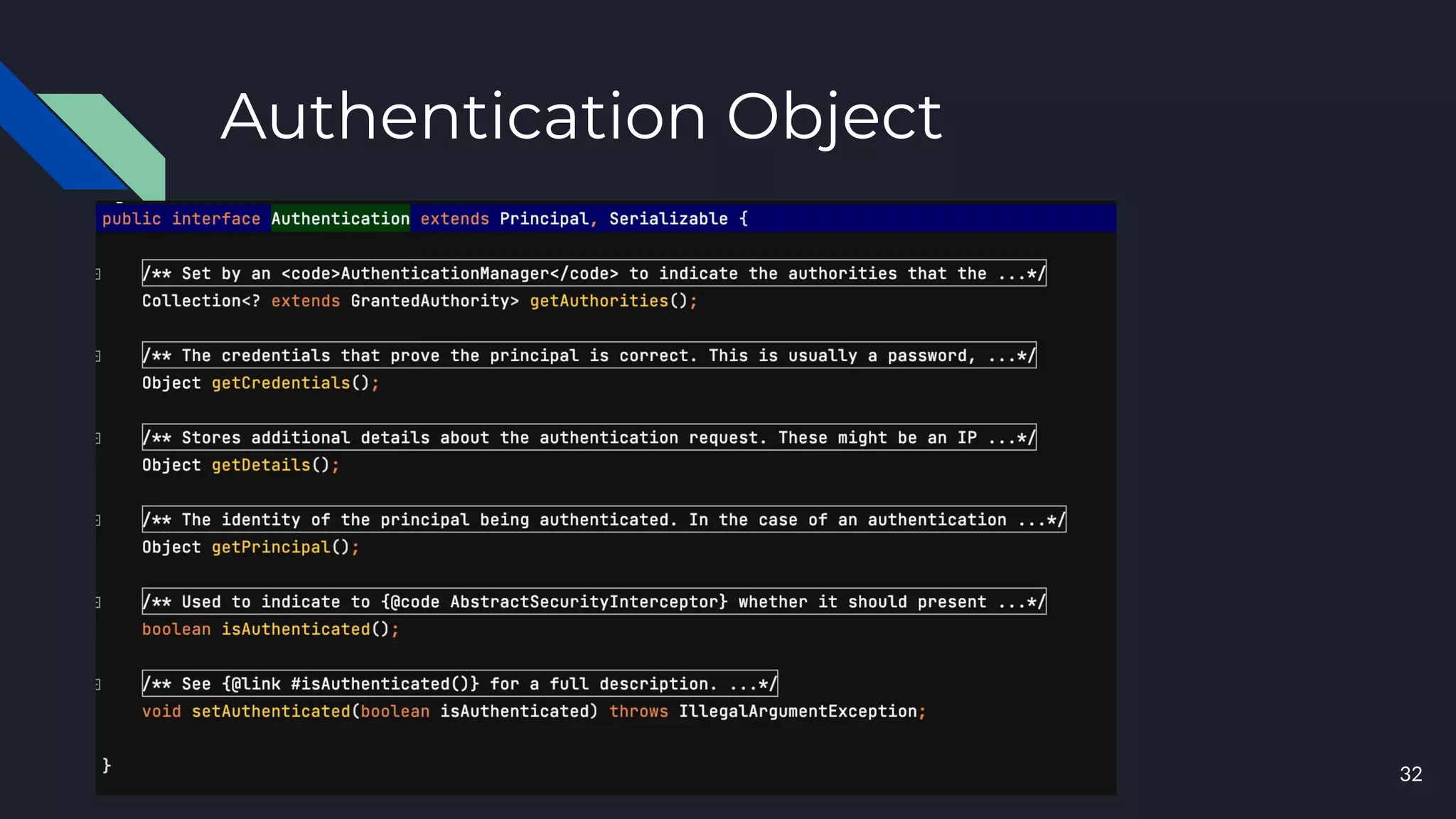
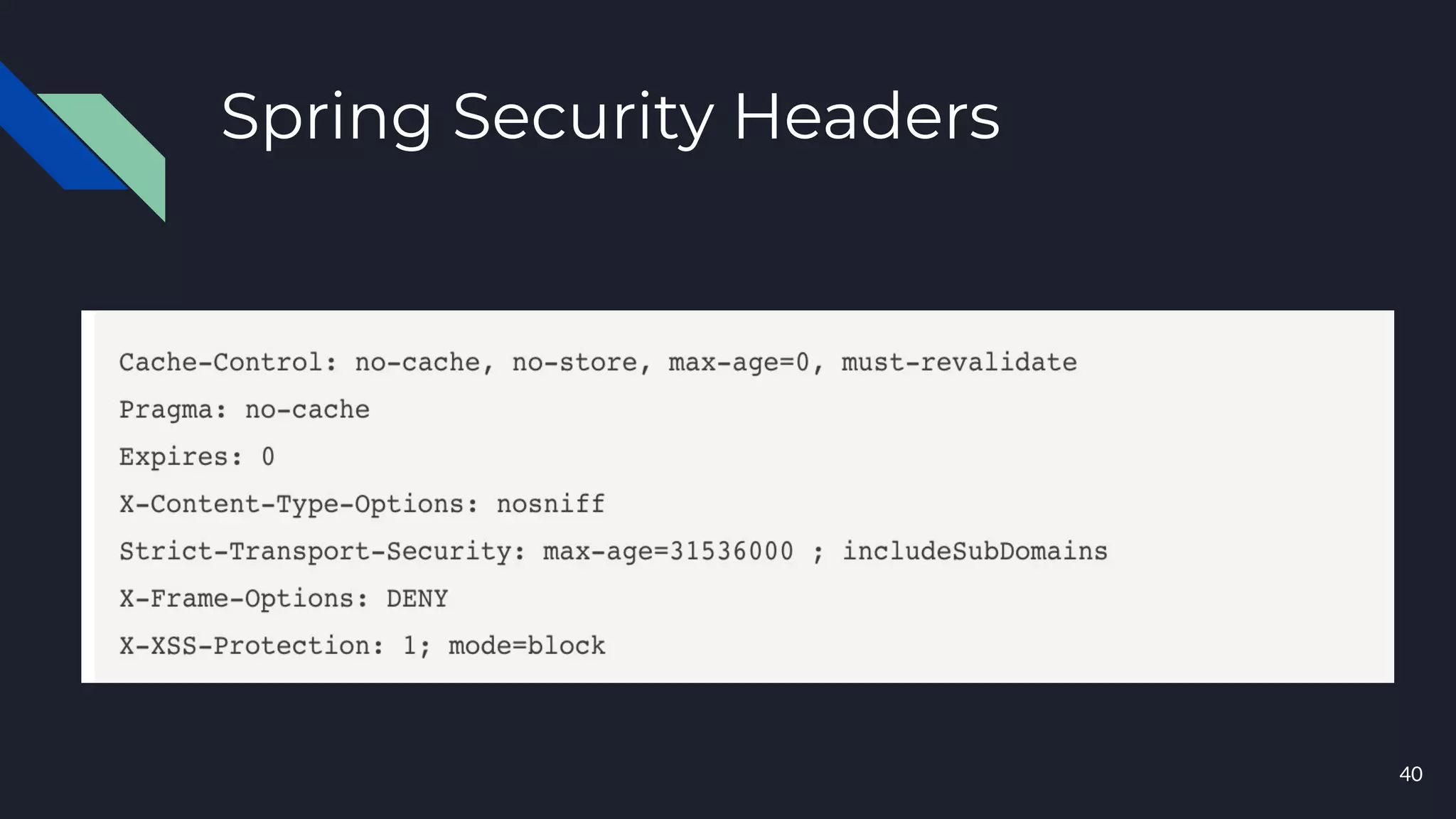
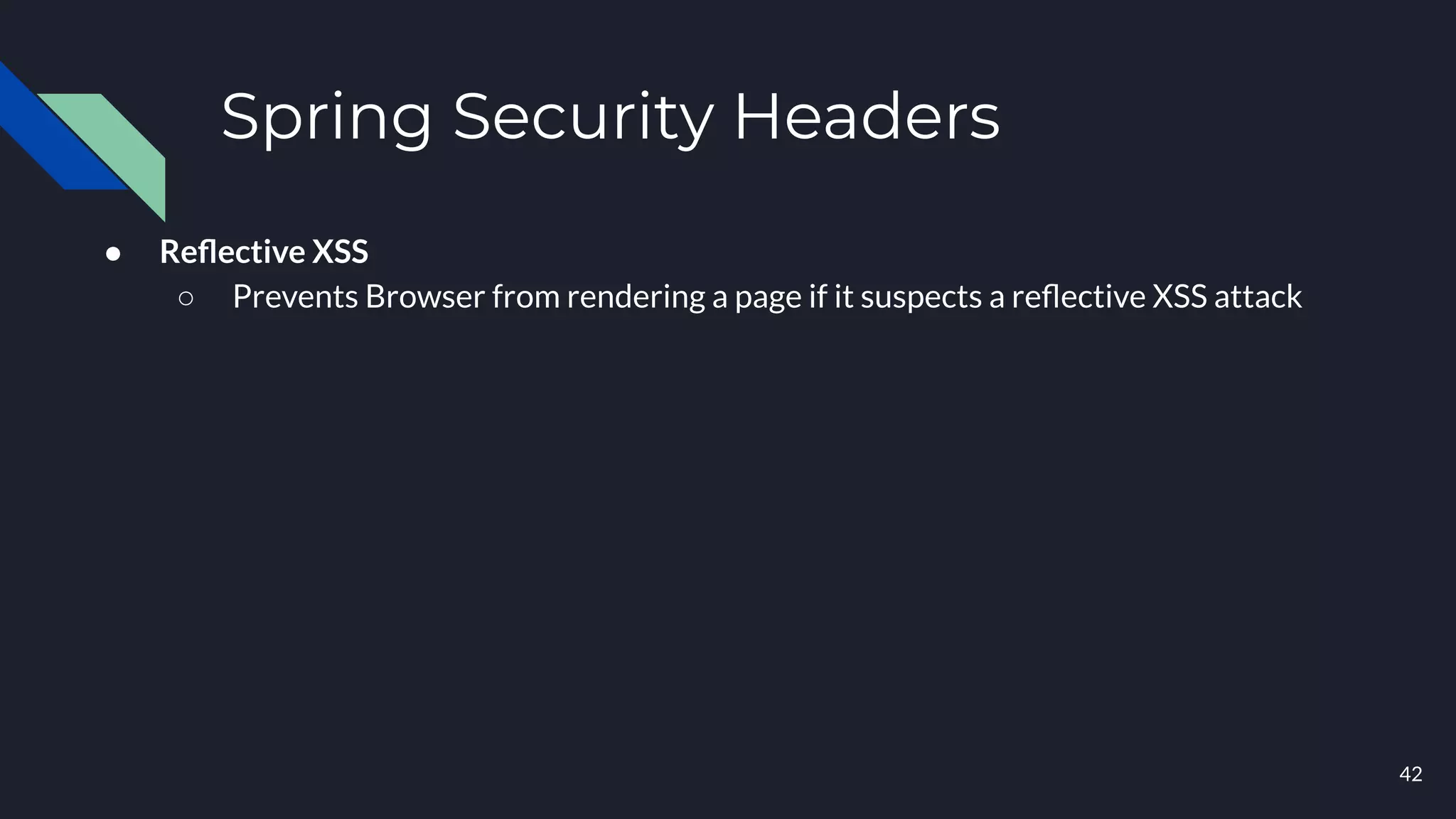
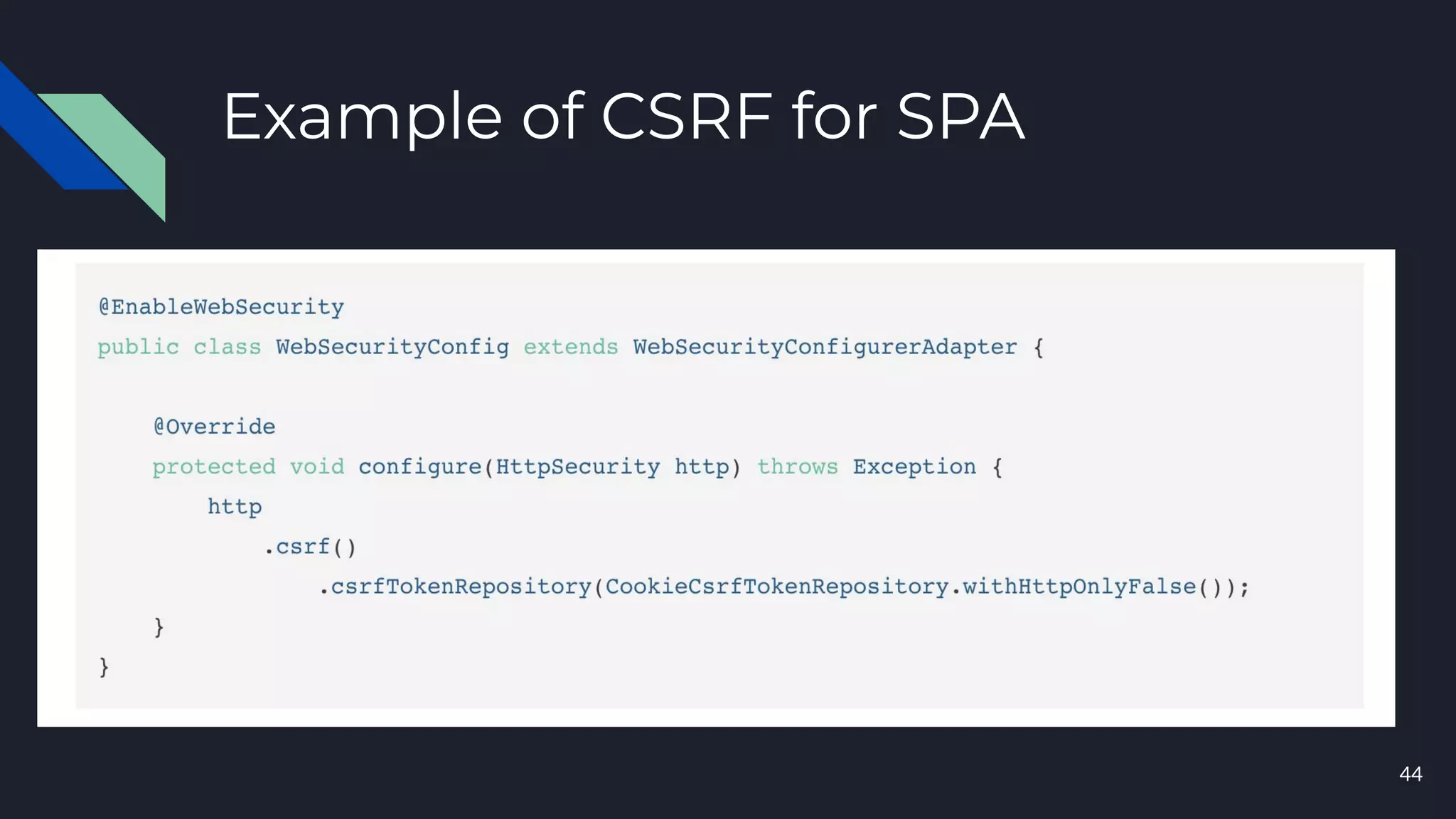
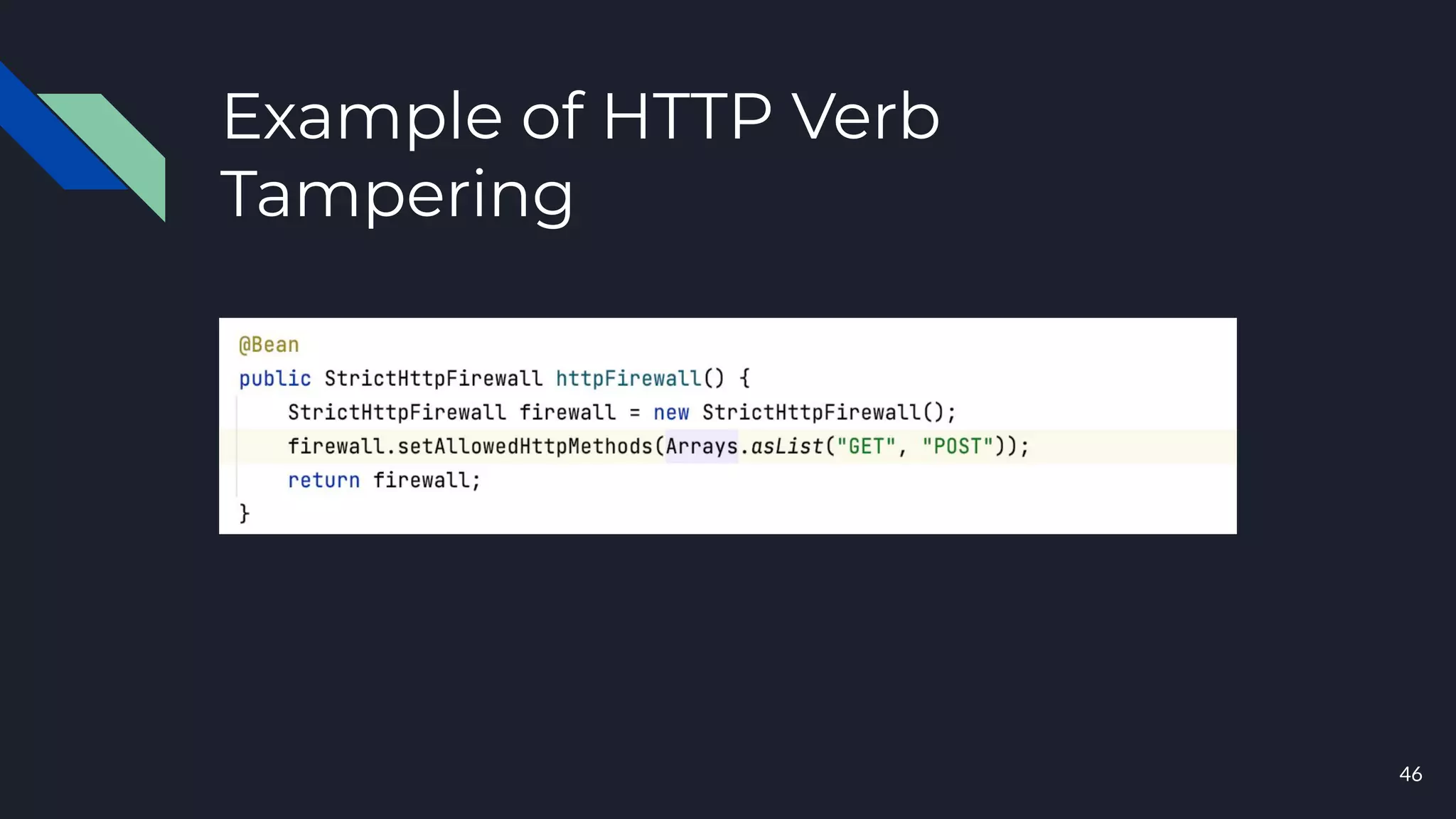
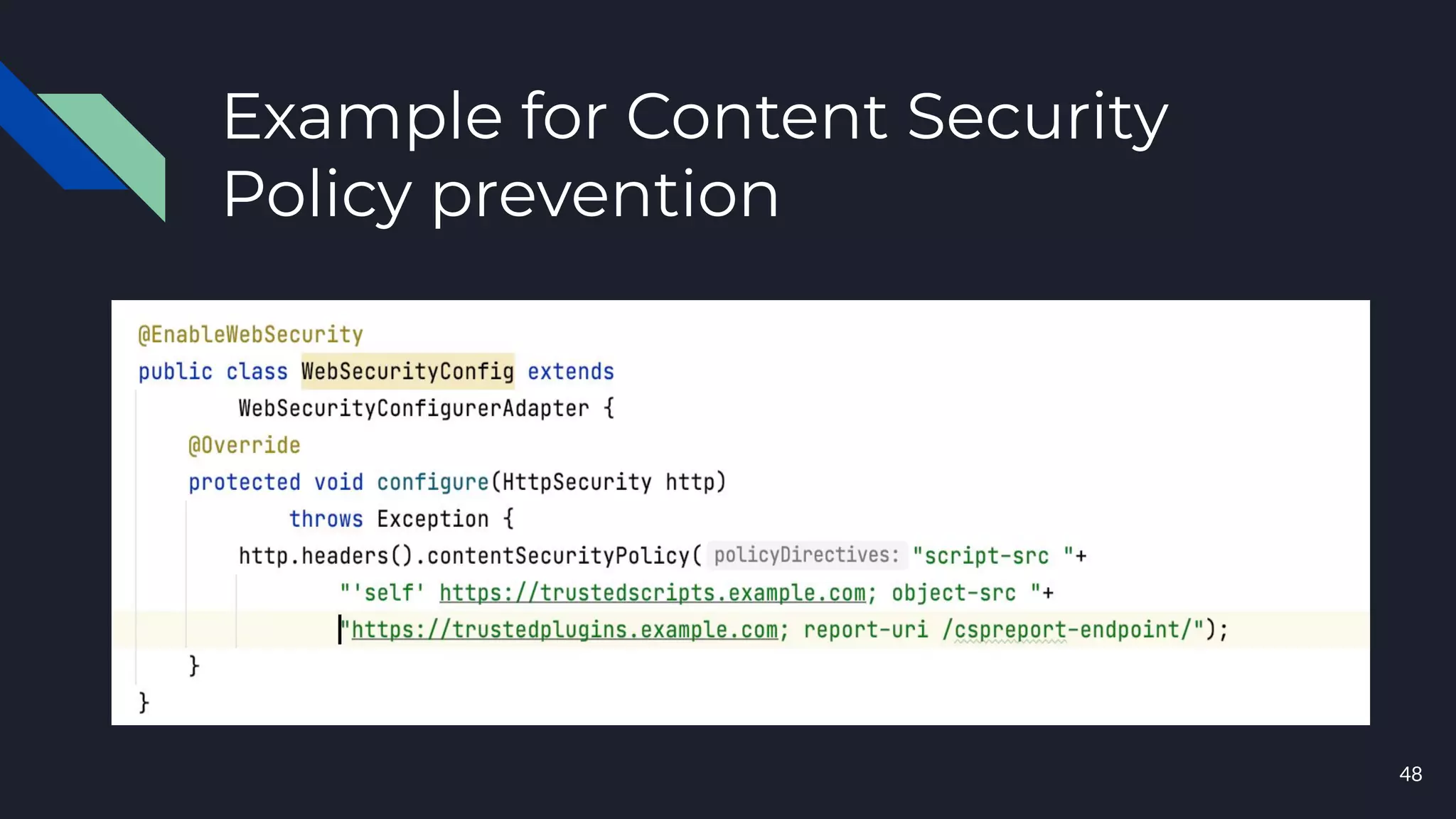
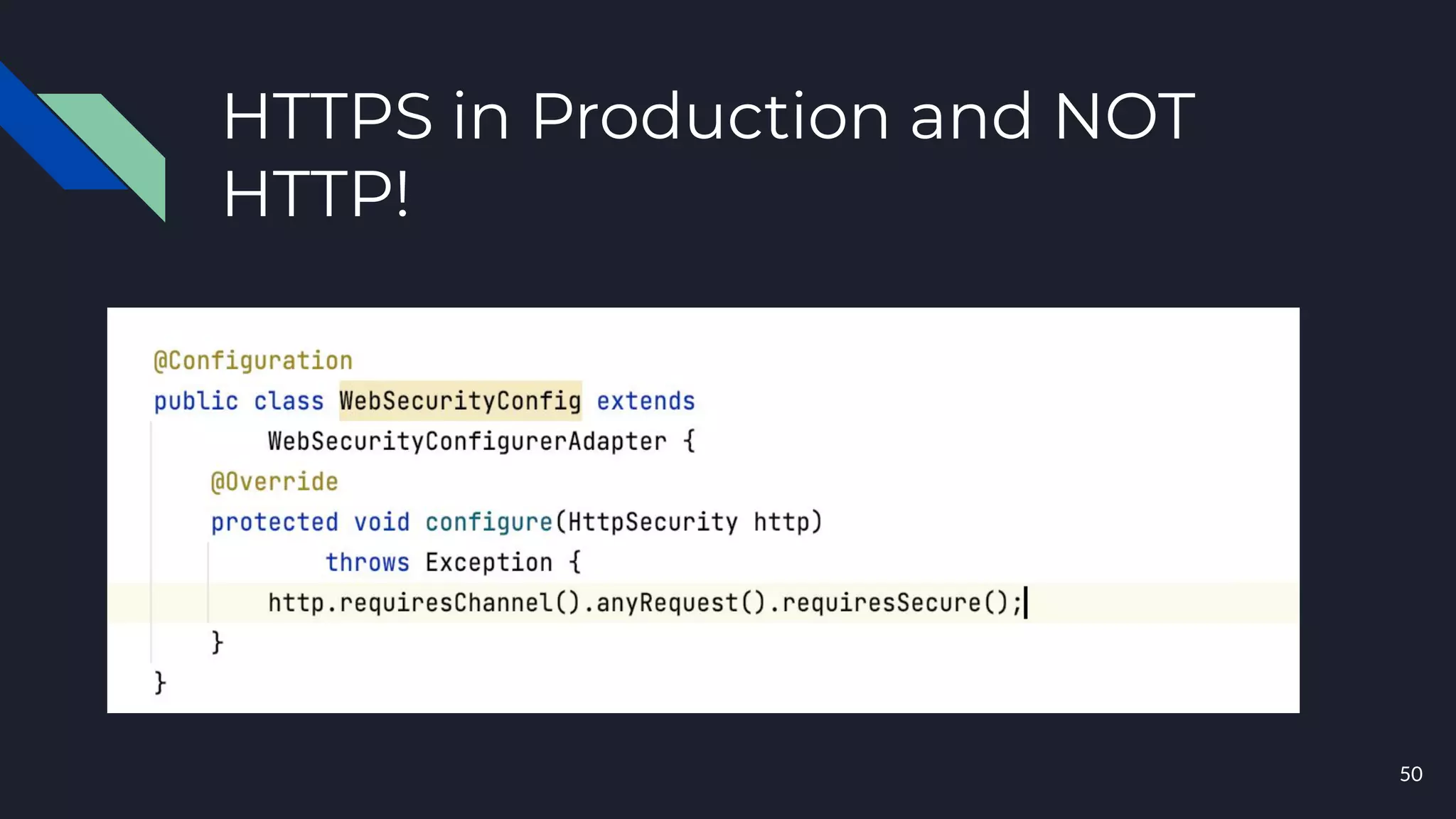
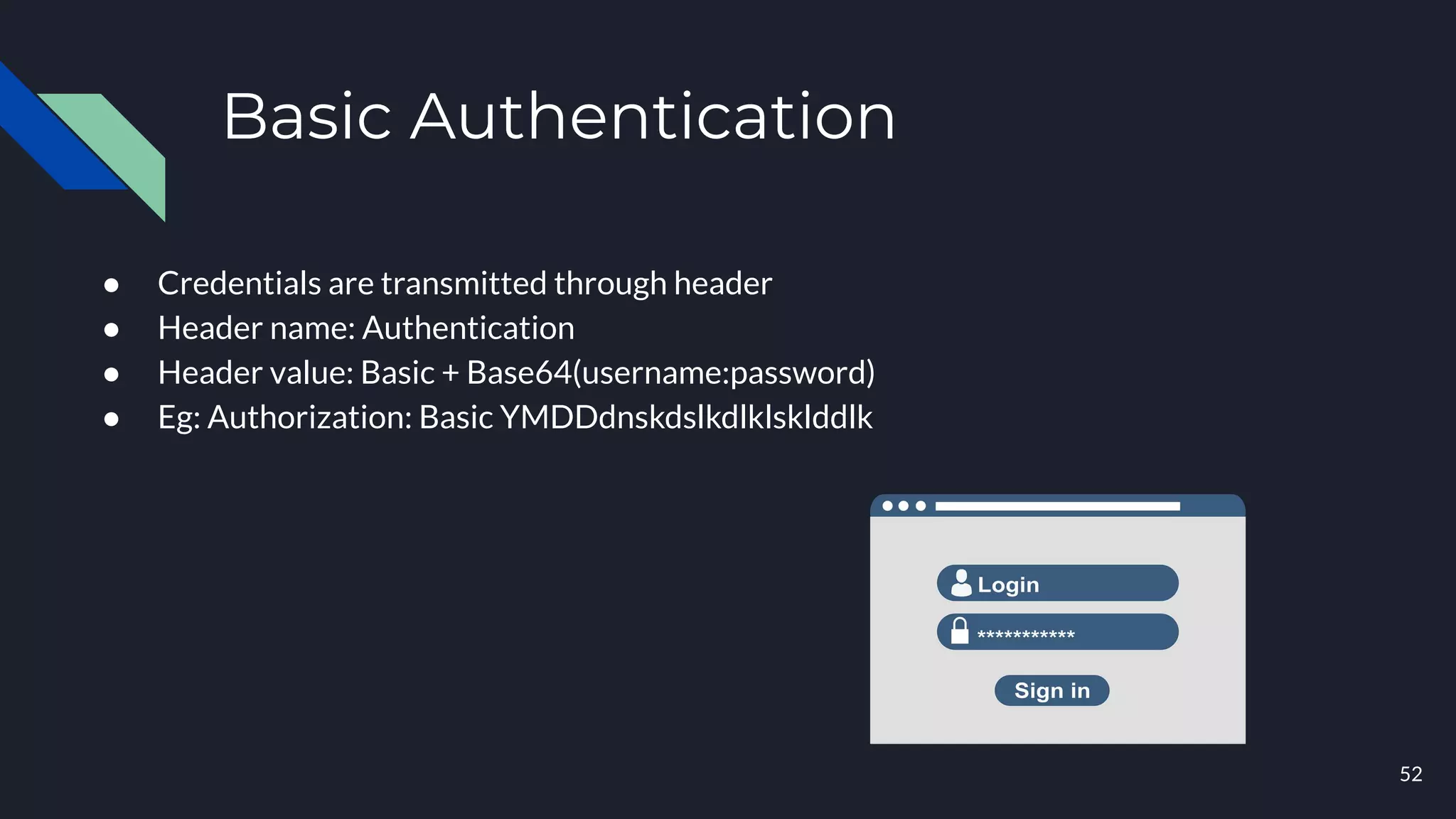
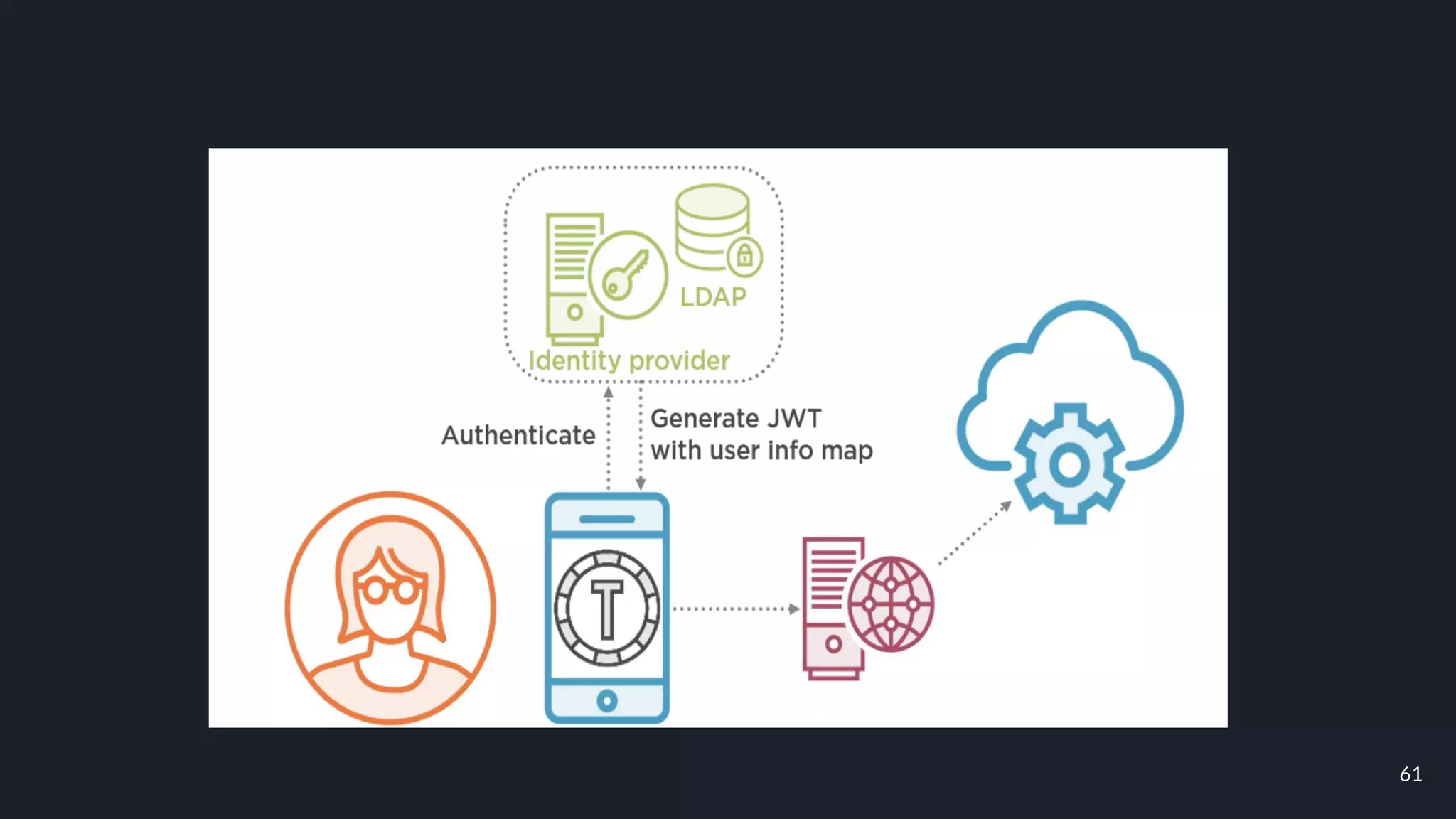
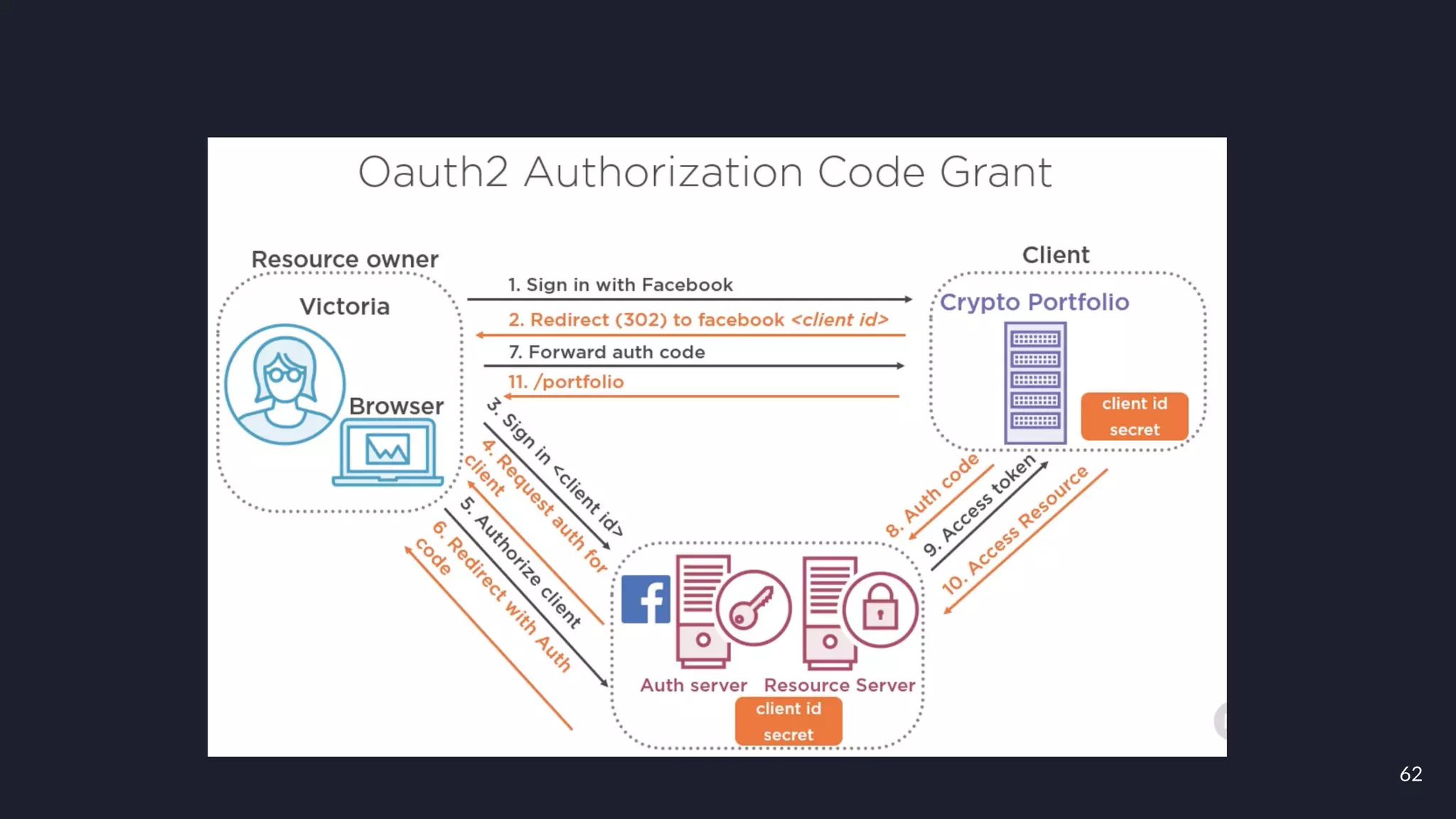
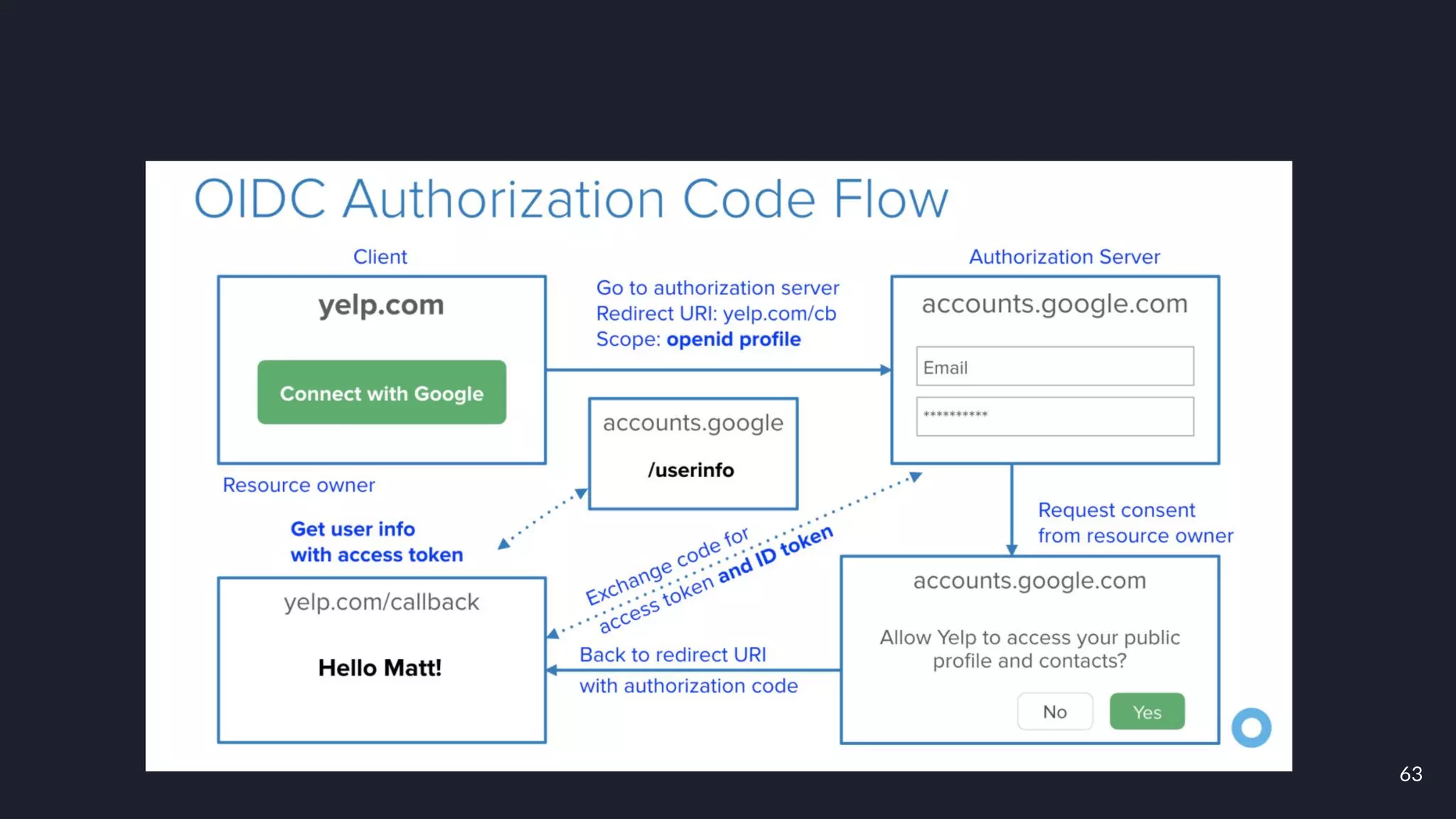
This document discusses building layers of defense for applications using the Spring Security framework. It begins with an introduction to authentication and authorization. It then discusses the layers of defense for a web application and provides an overview of Spring Security, how it works, and how to integrate it. The document outlines common security threats and how Spring Security protects against them. It also covers topics like basic authentication, JWT, OAuth, OpenID Connect, and content security policy. Code examples are provided to demonstrate concepts like CSRF protection, HTTP verb tampering prevention, and session fixation.