Embed presentation

























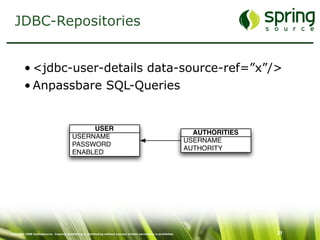
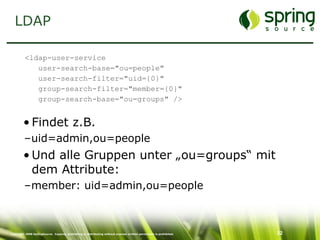










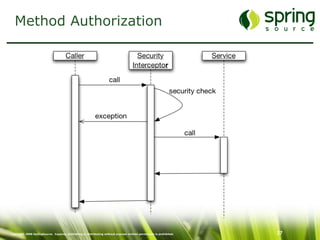
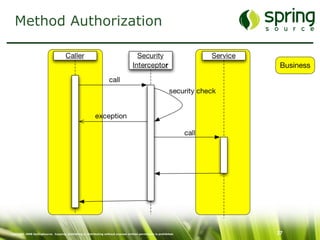
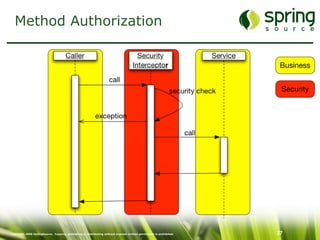
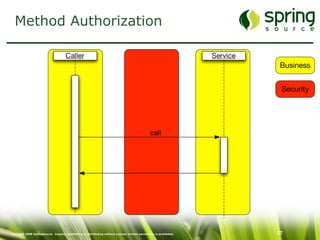
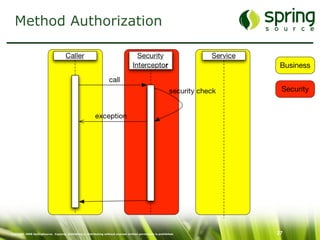

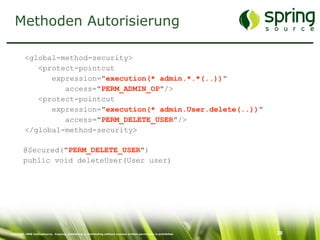





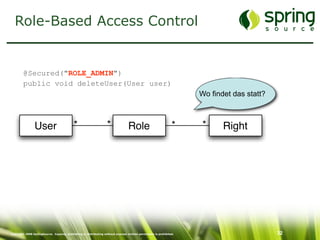
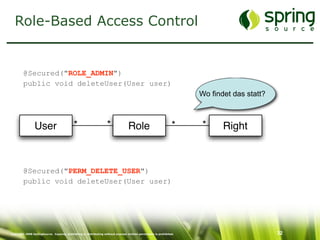




The document discusses Spring Security, a robust and flexible security framework for Java enterprise software development. It covers key concepts such as authentication, authorization, and integration with various tools, along with best practices for securing web applications. Additionally, it highlights features of Spring Security 2, including improved configuration and single sign-on support.





















































