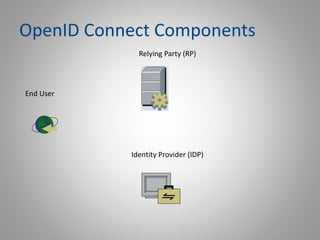
The document provides an overview of the OpenID Connect protocol, its advantages over older protocols like SAML, and features of Keycloak as an identity provider solution. It discusses the components of OpenID Connect, including authentication flows and security measures such as brute force protection and two-factor authentication. Additionally, it highlights the importance of selecting a certified relying party and identity provider for effective implementation.