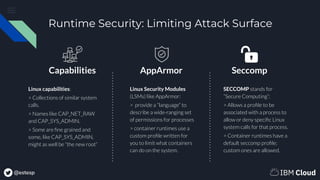
The document is a primer on securing container applications, discussing various aspects including image security, runtime isolation, and limiting attack surfaces. Key topics cover secure coding practices, resource limitations in Kubernetes, the use of Linux capabilities, and best practices for enforcing security policies across container environments. It emphasizes the importance of not running containers with root privileges and utilizing features like pod security policies in Kubernetes to enhance security.











![@estesp
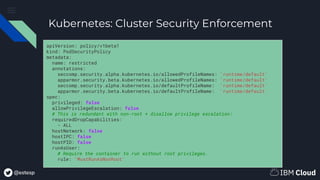
Kubernetes: Reducing Privilege
apiVersion: v1
kind: Pod
metadata:
name: security-context-demo
spec:
securityContext:
runAsUser: 1000
runAsGroup: 3000
fsGroup: 2000
containers:
- name: sec-ctx-demo
image: busybox
command: [ "sh", "-c", "sleep 1h" ]
securityContext:
allowPrivilegeEscalation: false
runAsUser: 2000
capabilities:
add: ["NET_ADMIN", "SYS_TIME"]
● Non-root user
○ Use securityContext for
containers and pod-level control
○ Use PodSecurityPolicy to enforce
restrictions cluster-wide
● Capabilities (privilege related)
○ Also in securityContext; see
example](https://image.slidesharecdn.com/cloudnativetlvsecuringcontainerizedapplications-200128185714/85/Cloud-Native-TLV-Meetup-Securing-Containerized-Applications-Primer-13-320.jpg)