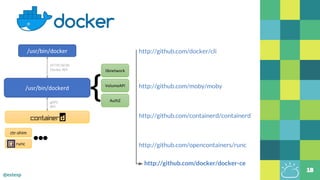
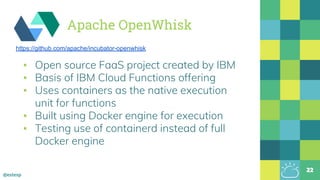
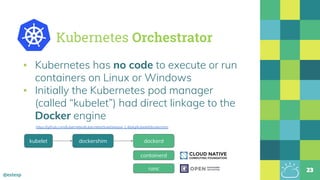
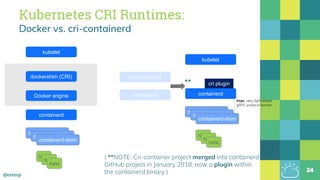
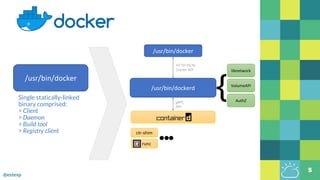
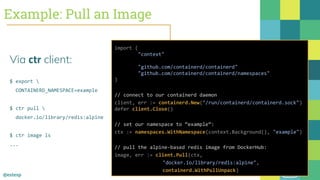
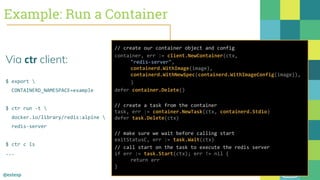
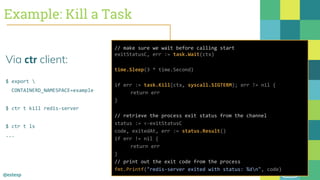
The document outlines the evolution of Docker and its components, emphasizing the development of the Docker engine, runc, and containerd as essential elements in container technology. It details the establishment of the Open Container Initiative (OCI) and runc's role as a standard container execution environment, as well as containerd's function as a core container runtime for various platforms. Use cases for containerd include LinuxKit, BuildKit, and Kubernetes, highlighting its broad applicability and ongoing contributions to open-source projects.





![@estesp
& runC
> Announced June 20th, 2015
> Charter signed on
December 8th, 2015
> 44 member companies
> Both specifications
reached 1.0 June 2017
https://opencontainers.org
https://github.com/opencontainers
> runc is a client wrapper around libcontainer
> libcontainer is the OS level interface for containers
> OCI spec covers Solaris, Linux, & MS Windows
$ docker run -it --read-only
-v /host:/hostpath
alpine sh
/#
{
"ociVersion": "1.0.0",
"platform": {
"os": "linux",
"arch": "amd64"
},
"process": {
"terminal": true,
"args": [
"sh"
],
"env": [
"PATH=/usr/sbin:/usr/local/bin:/bin”
config.json
• A Linux Foundation Collaborative Project
• Free from control by any particular vendor’s specific cloud stack or ecosystem
• Includes a specification, reference runtime* and now, a specified image format
*seeded with runc + libcontainer by Docker
7](https://image.slidesharecdn.com/dockerathenscontainerdusecases2-180605130652/85/Docker-Athens-Docker-Engine-Evolution-Containerd-Use-Cases-7-320.jpg)





![@estesp
Example: Customize OCI Configuration
// WithHtop configures a container to monitor the host via `htop`
func WithHtop(s *specs.Spec) error {
// make sure we are in the host pid namespace
if err := containerd.WithHostNamespace(specs.PIDNamespace)(s); err != nil {
return err
}
// make sure we set htop as our arg
s.Process.Args = []string{"htop"}
// make sure we have a tty set for htop
if err := containerd.WithTTY(s); err != nil {
return err
}
return nil
}
With{func} functions cleanly separate modifiers](https://image.slidesharecdn.com/dockerathenscontainerdusecases2-180605130652/85/Docker-Athens-Docker-Engine-Evolution-Containerd-Use-Cases-16-320.jpg)