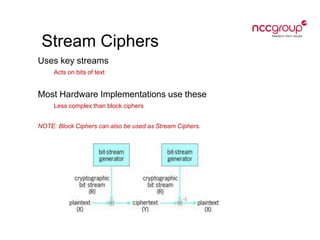
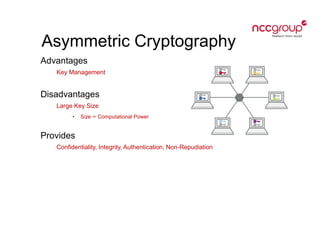
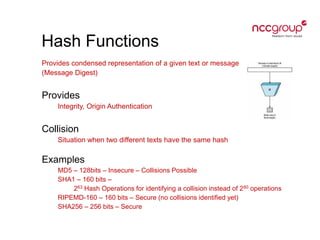
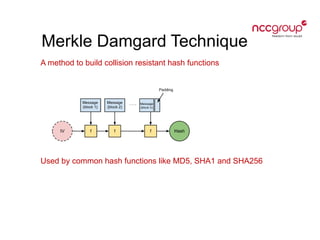
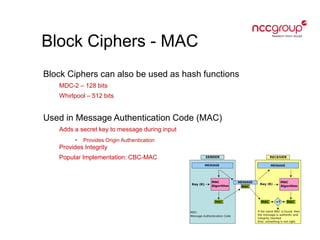
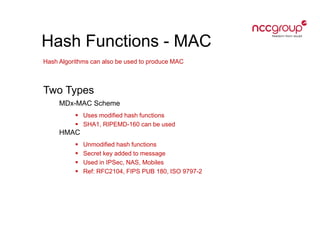
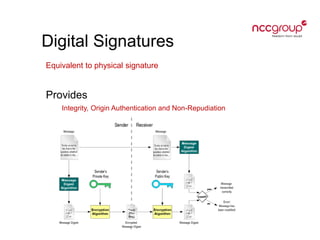
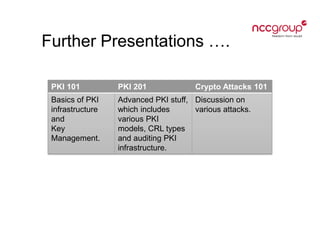
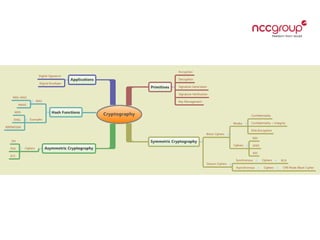
This document provides an introduction to cryptography concepts including symmetric and asymmetric cryptography, block ciphers, stream ciphers, hash functions, digital signatures, and digital envelopes. It defines common terms and describes popular algorithms for each concept. Symmetric cryptography uses a shared key for encryption and decryption while asymmetric cryptography uses public/private key pairs. Block and stream ciphers are the main types of symmetric algorithms. Hash functions and digital signatures provide integrity and authentication. Digital envelopes allow confidential messages with signatures.


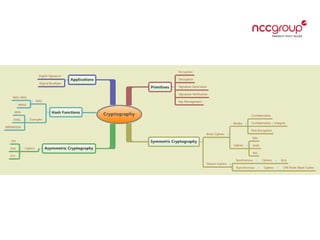


![Symmetric Cryptography
Advantages
Small Key Size
• Size ∞ Computational Power
Disadvantages
Key Management and transfer/sharing
• Number of keys required = n(n-1)/2, where n is the number of
parties involved.
• If there are 5 parties, then number of keys = 10
• If there are 10 parties, then number of keys = 45
• If there are 100 parties, then number of keys = 4950
Provides
Confidentiality, Integrity, Origin Authentication
[based on the Mode used]](https://image.slidesharecdn.com/cryptography101-130903075725-/85/Cryptography101-6-320.jpg)