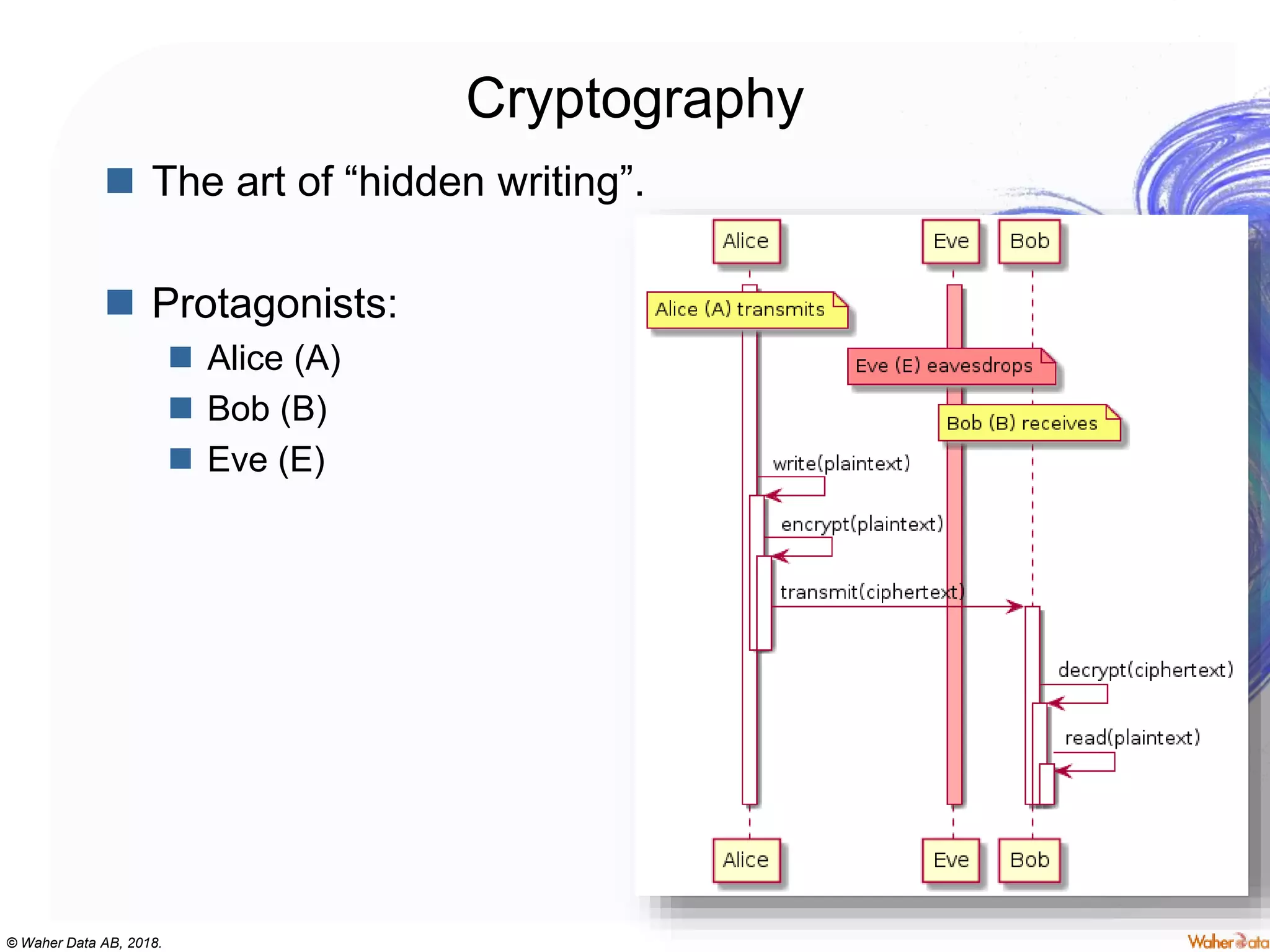
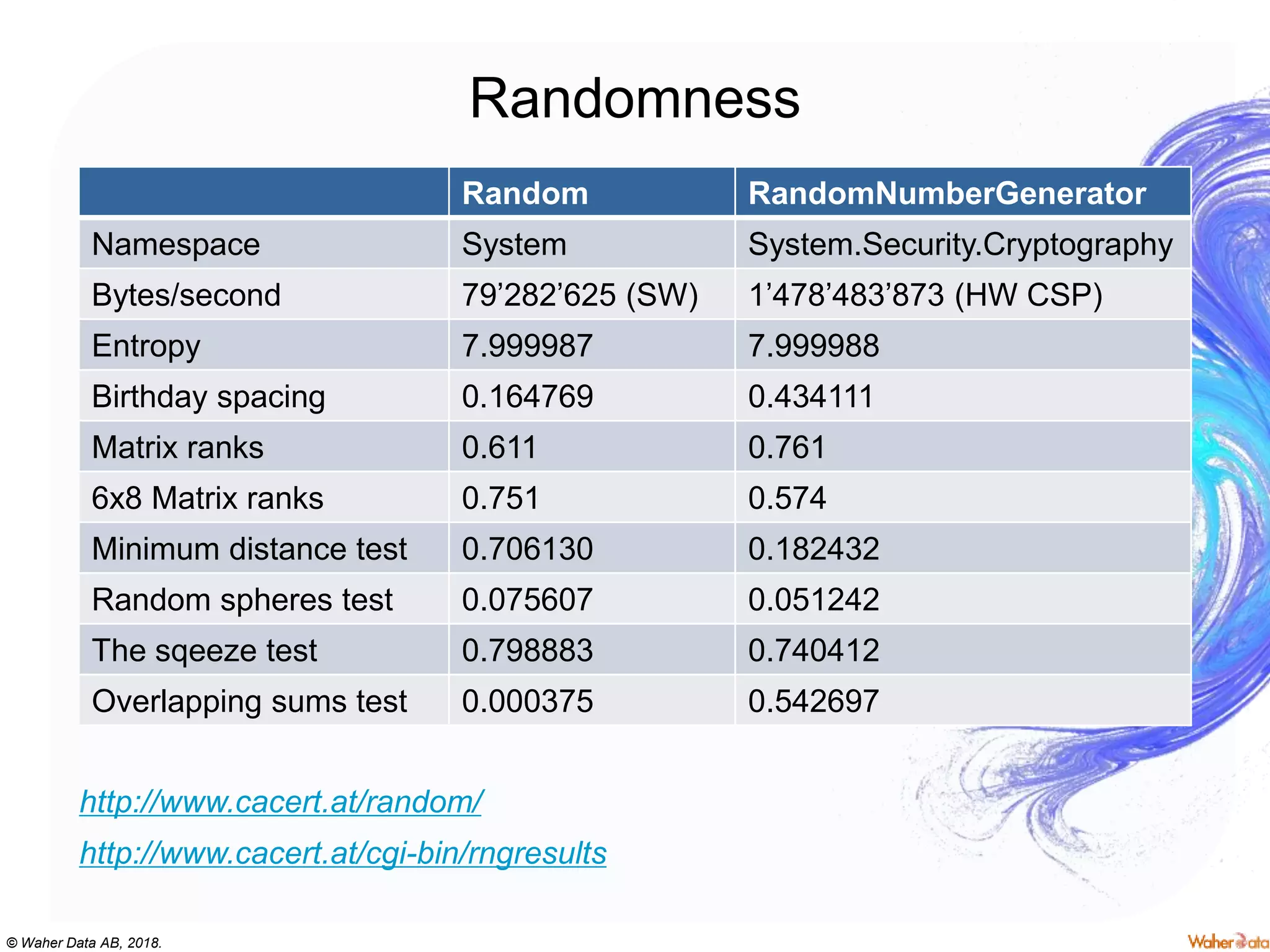
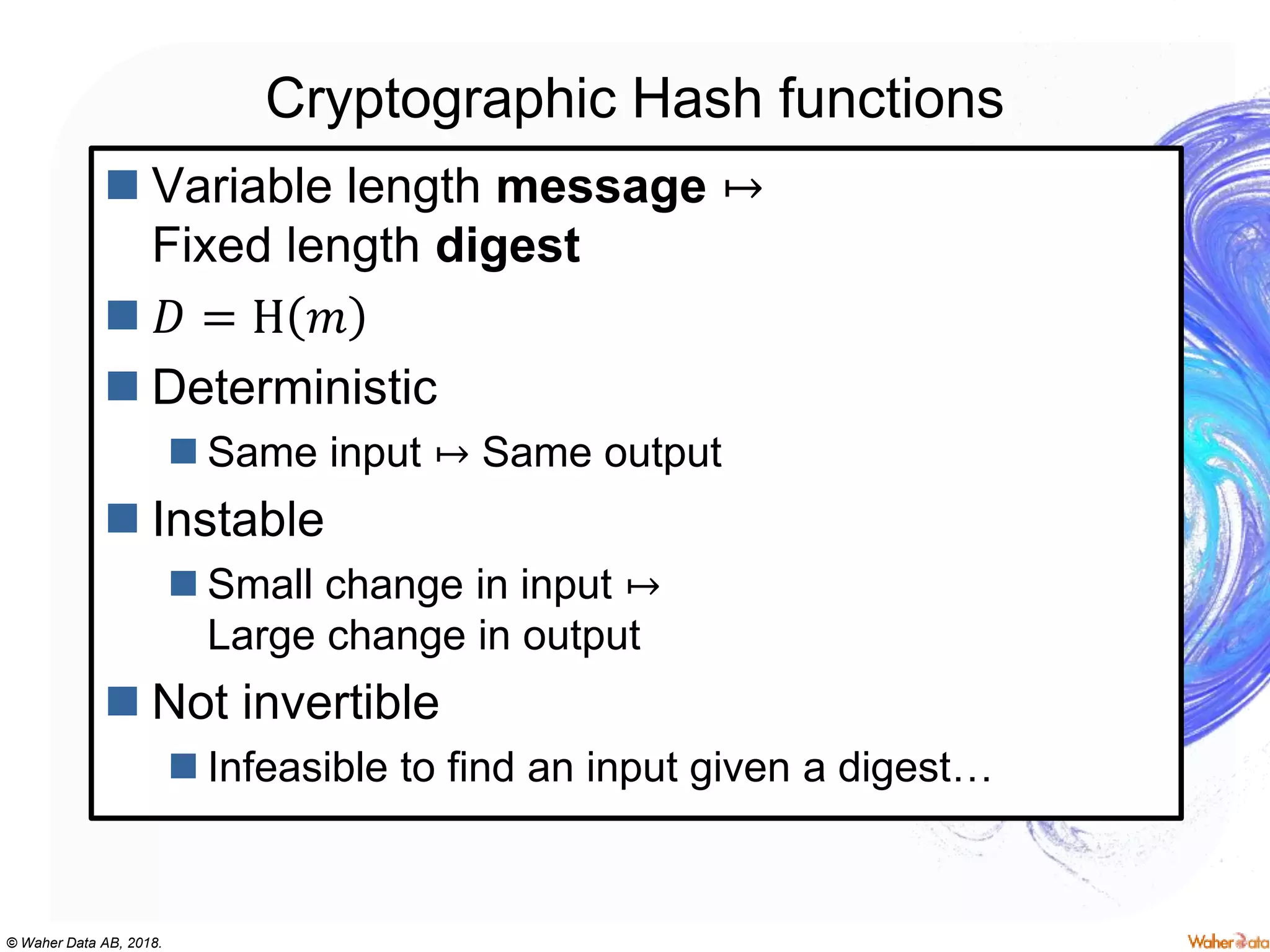
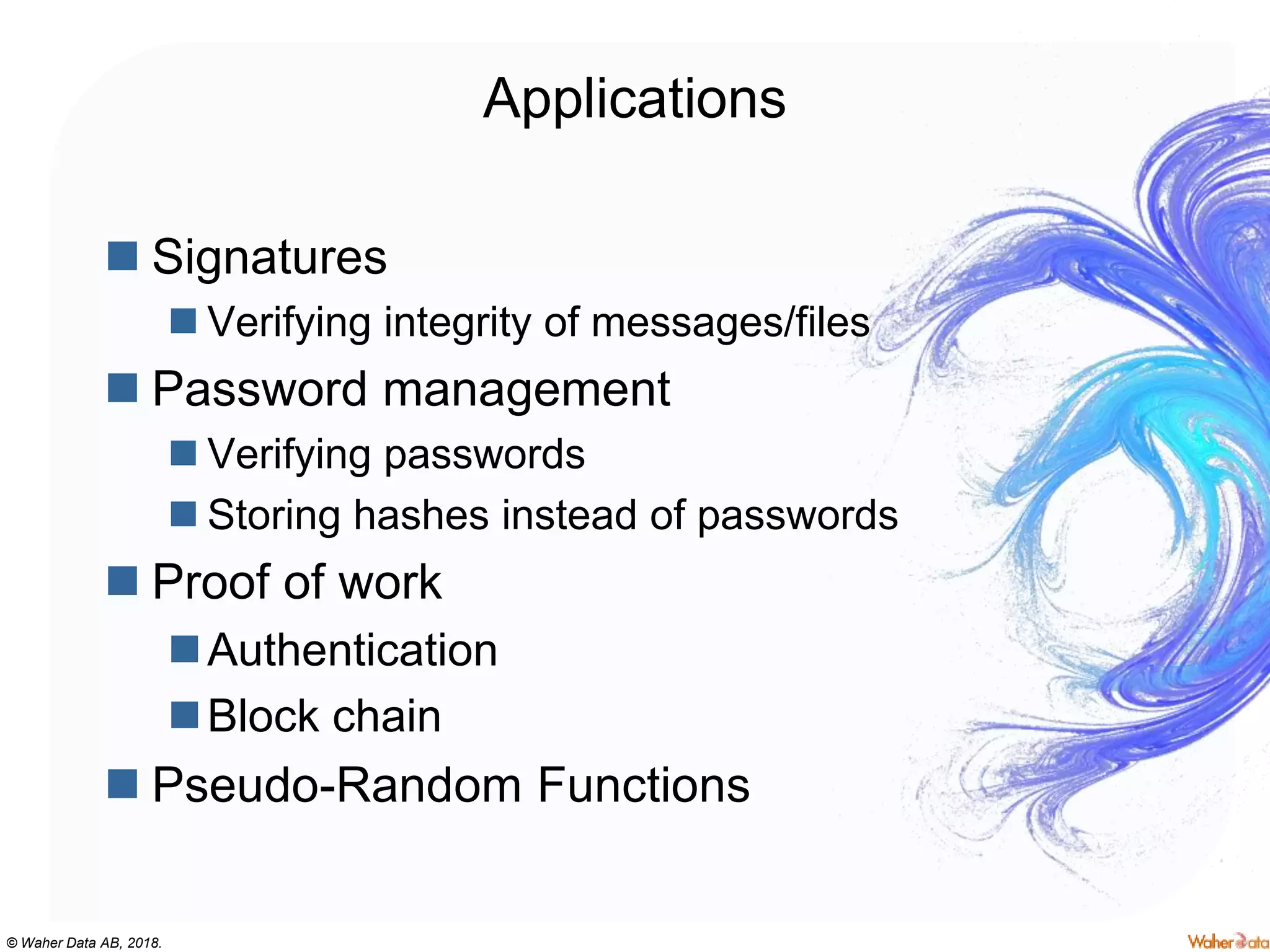
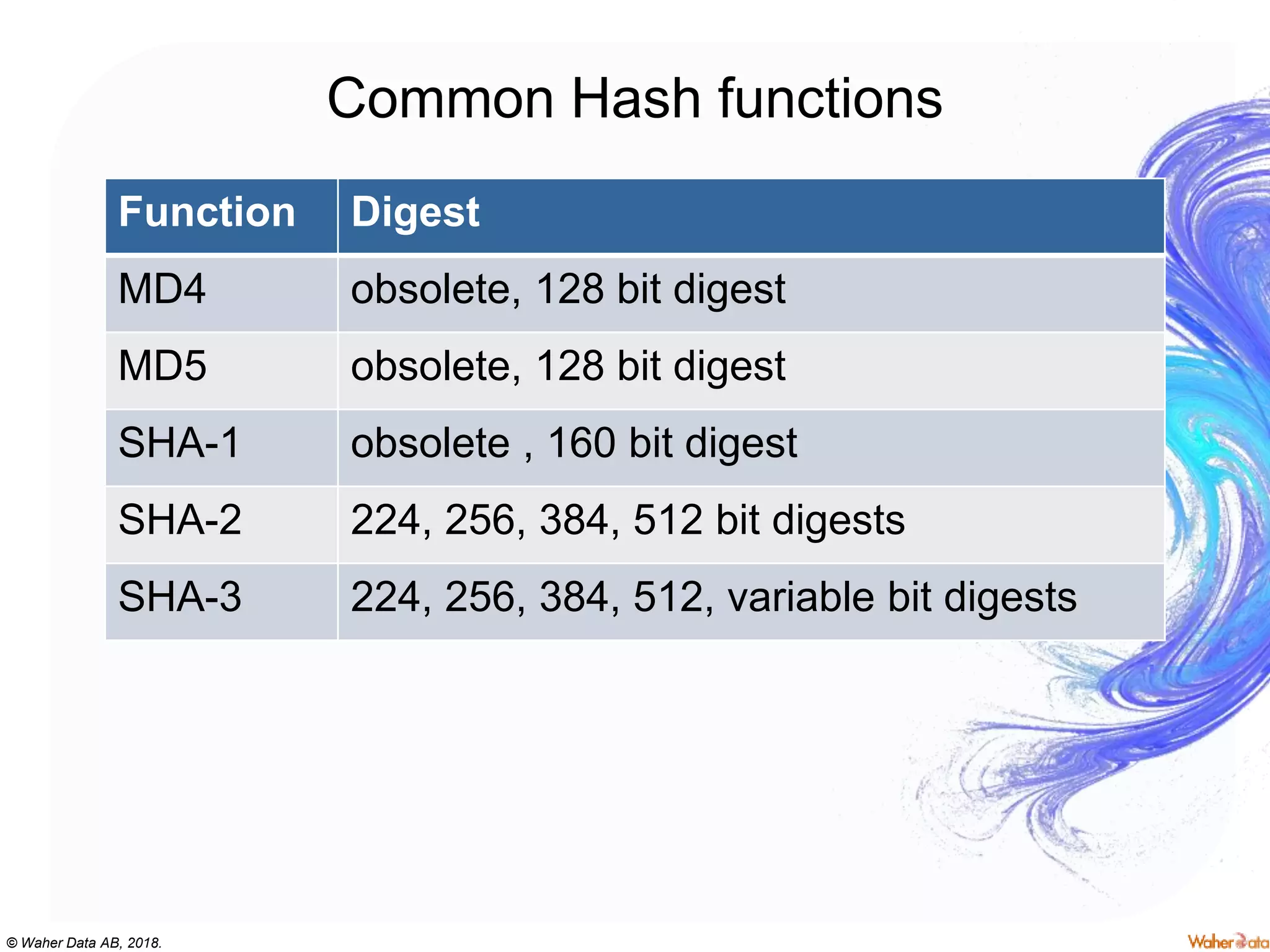
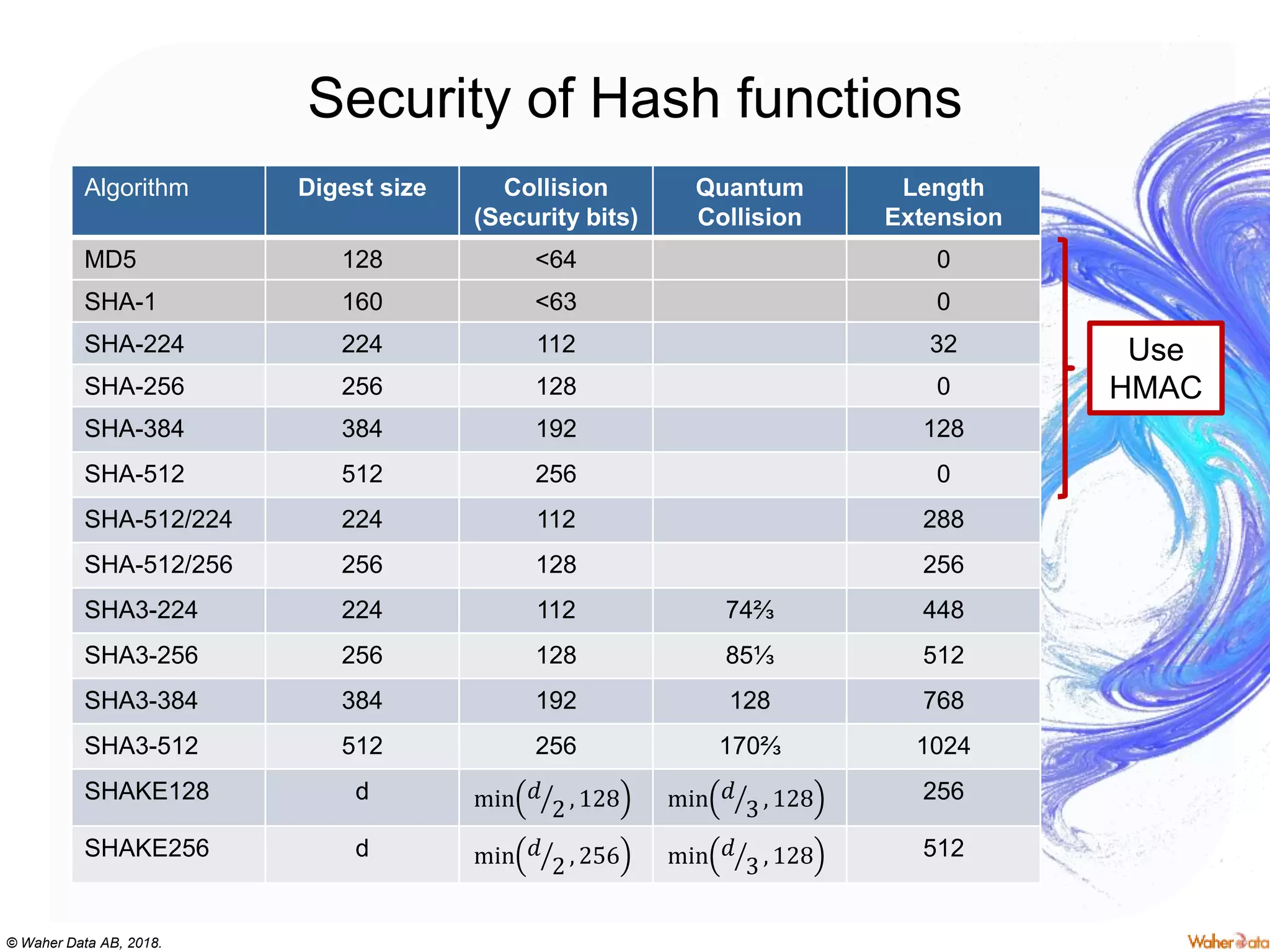
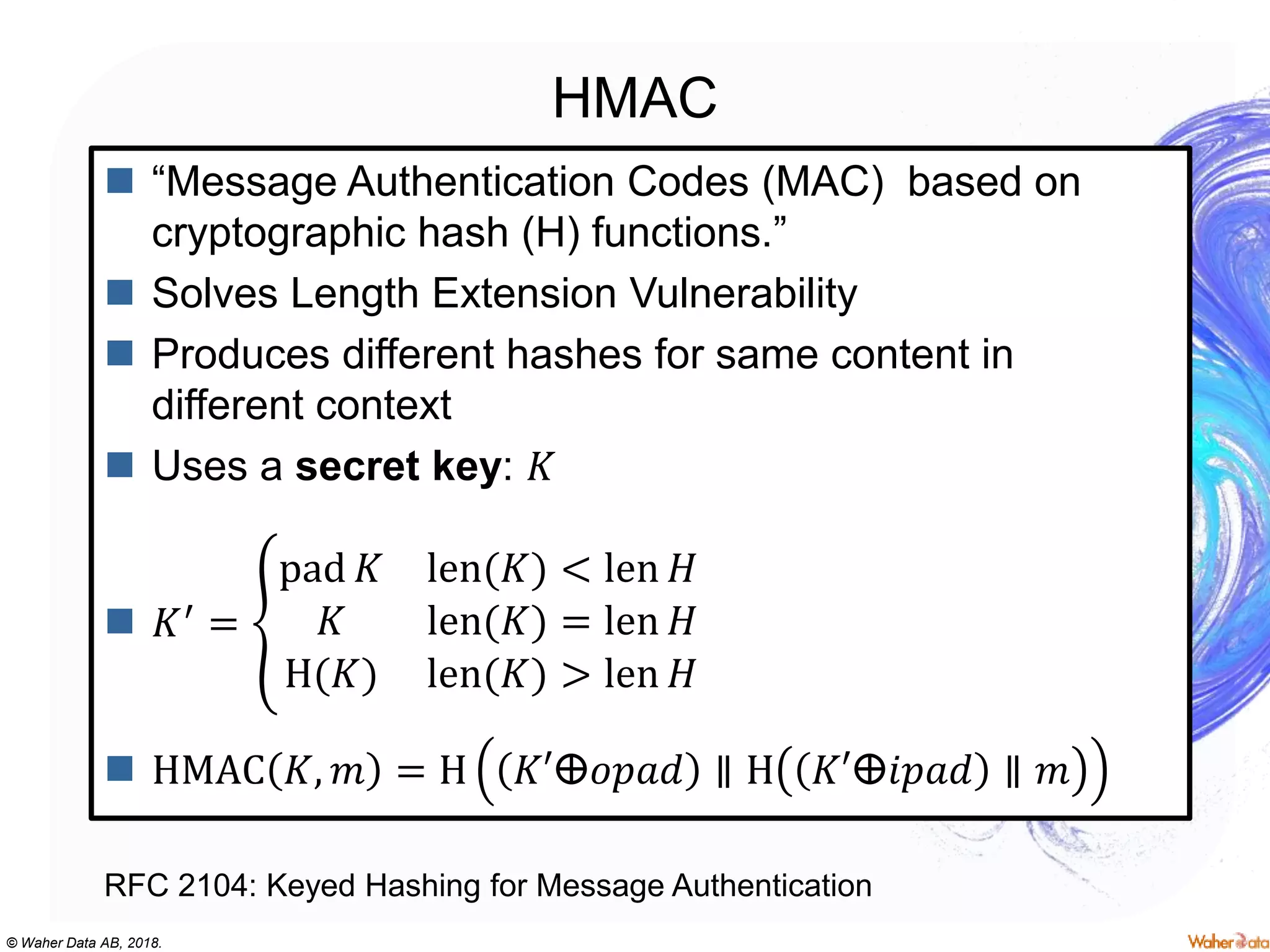
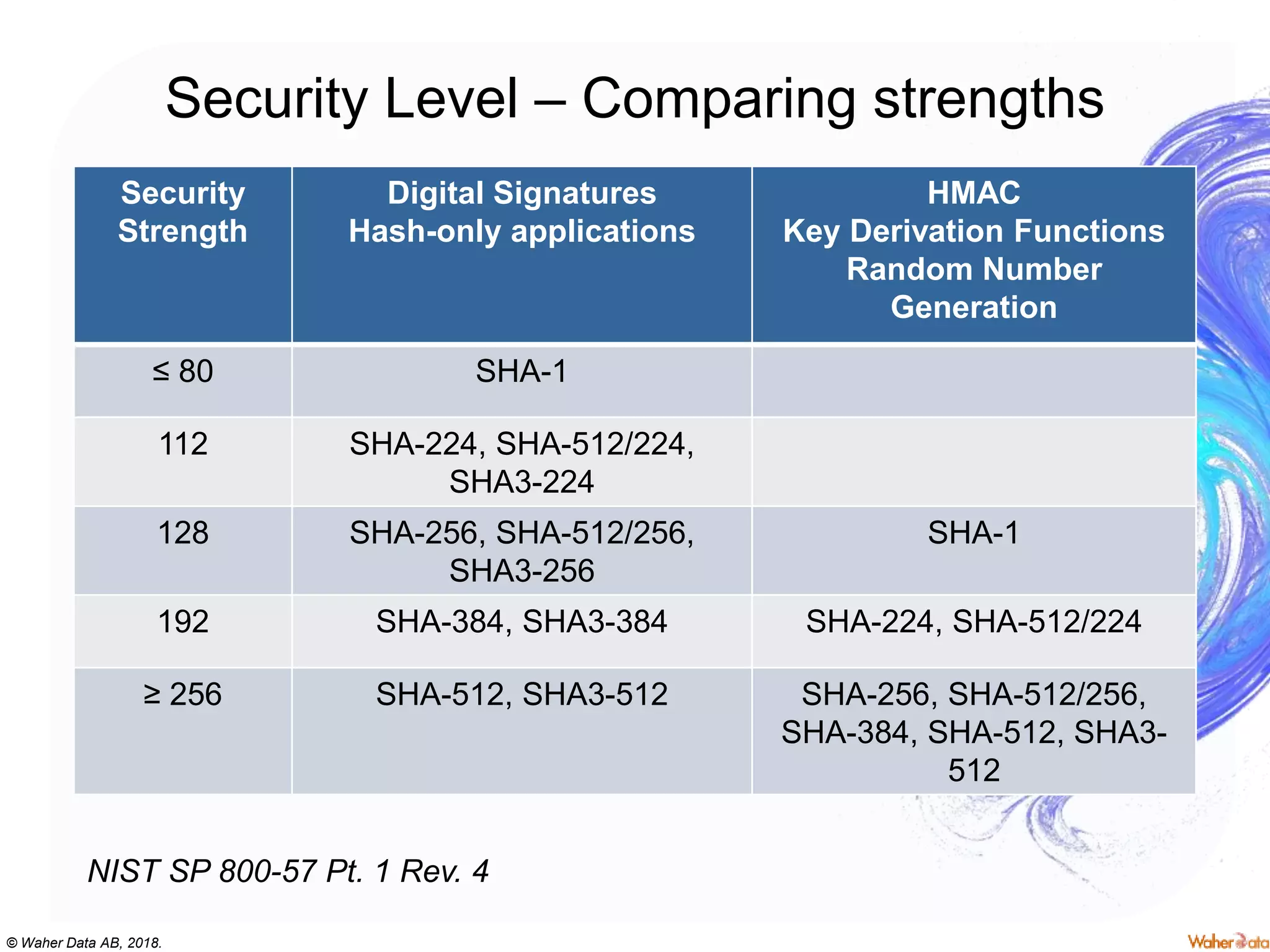
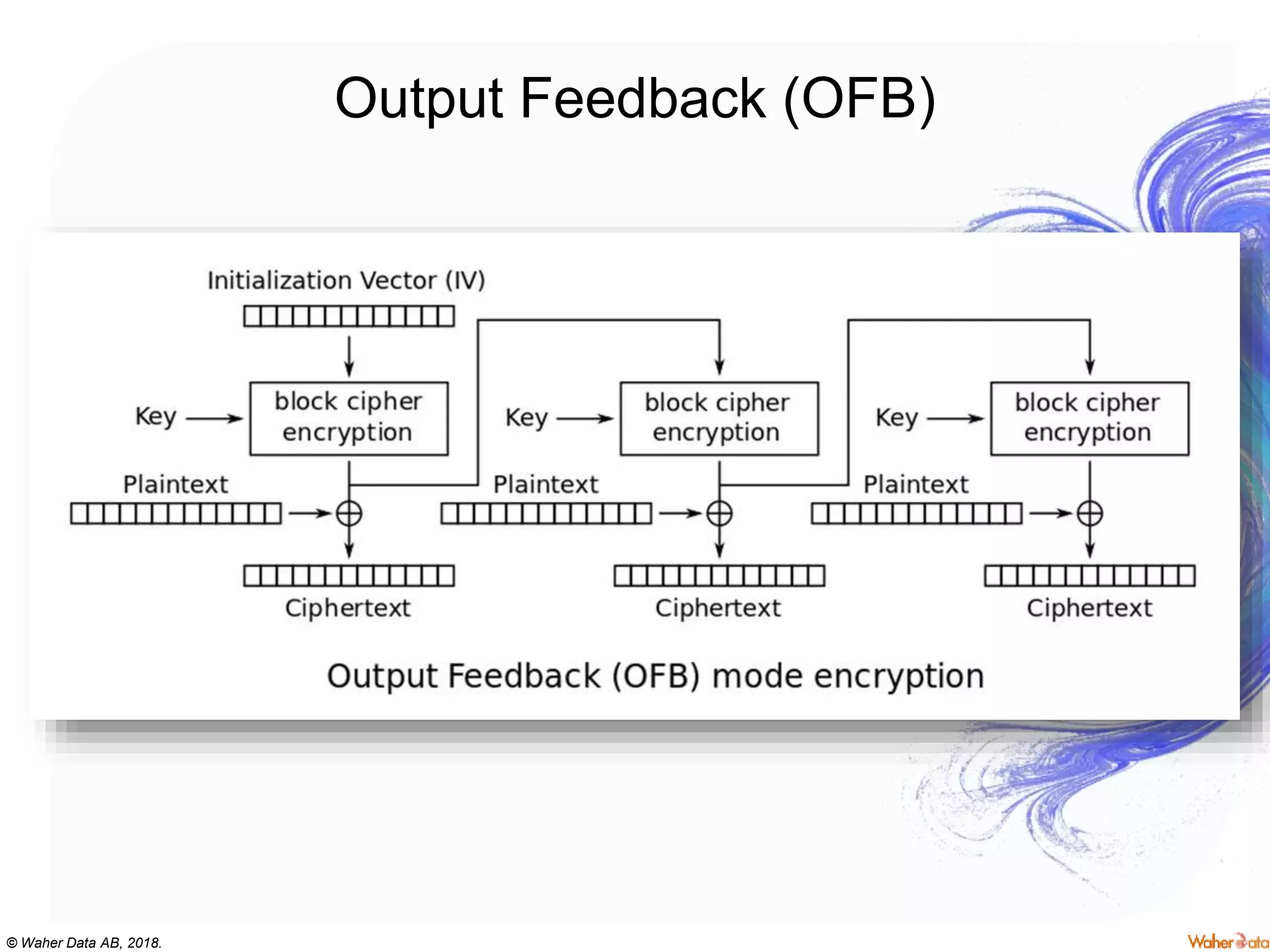
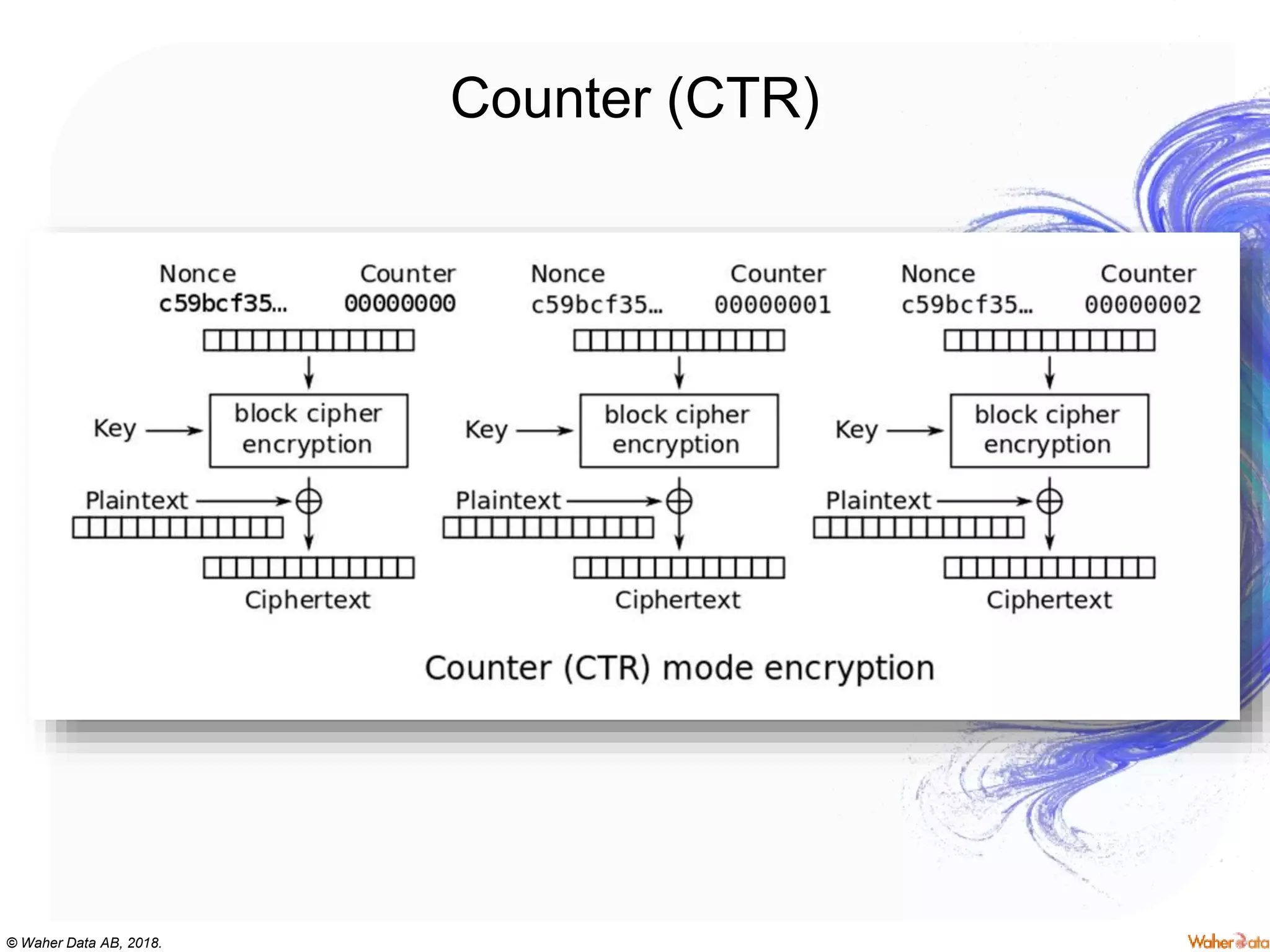
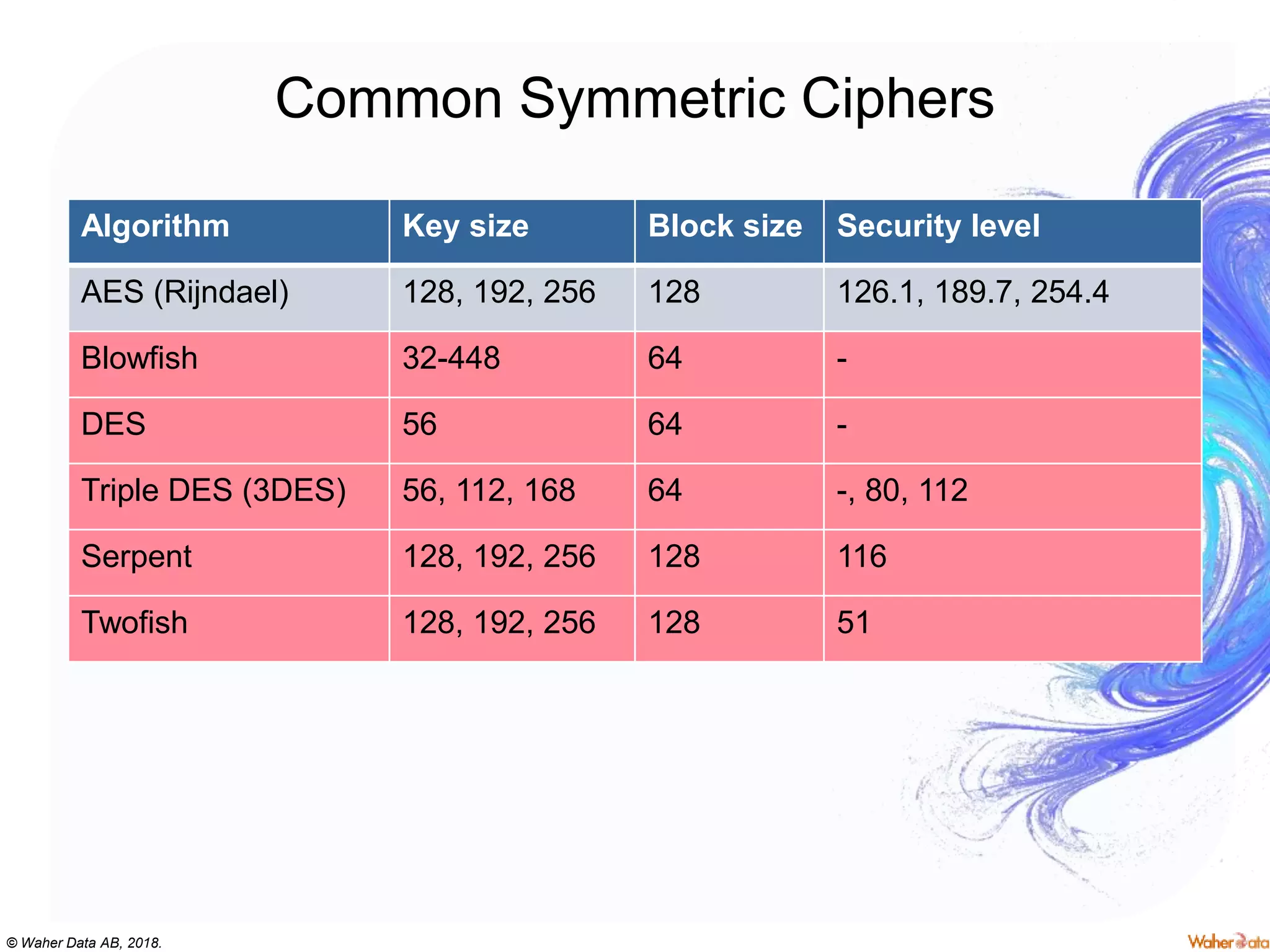
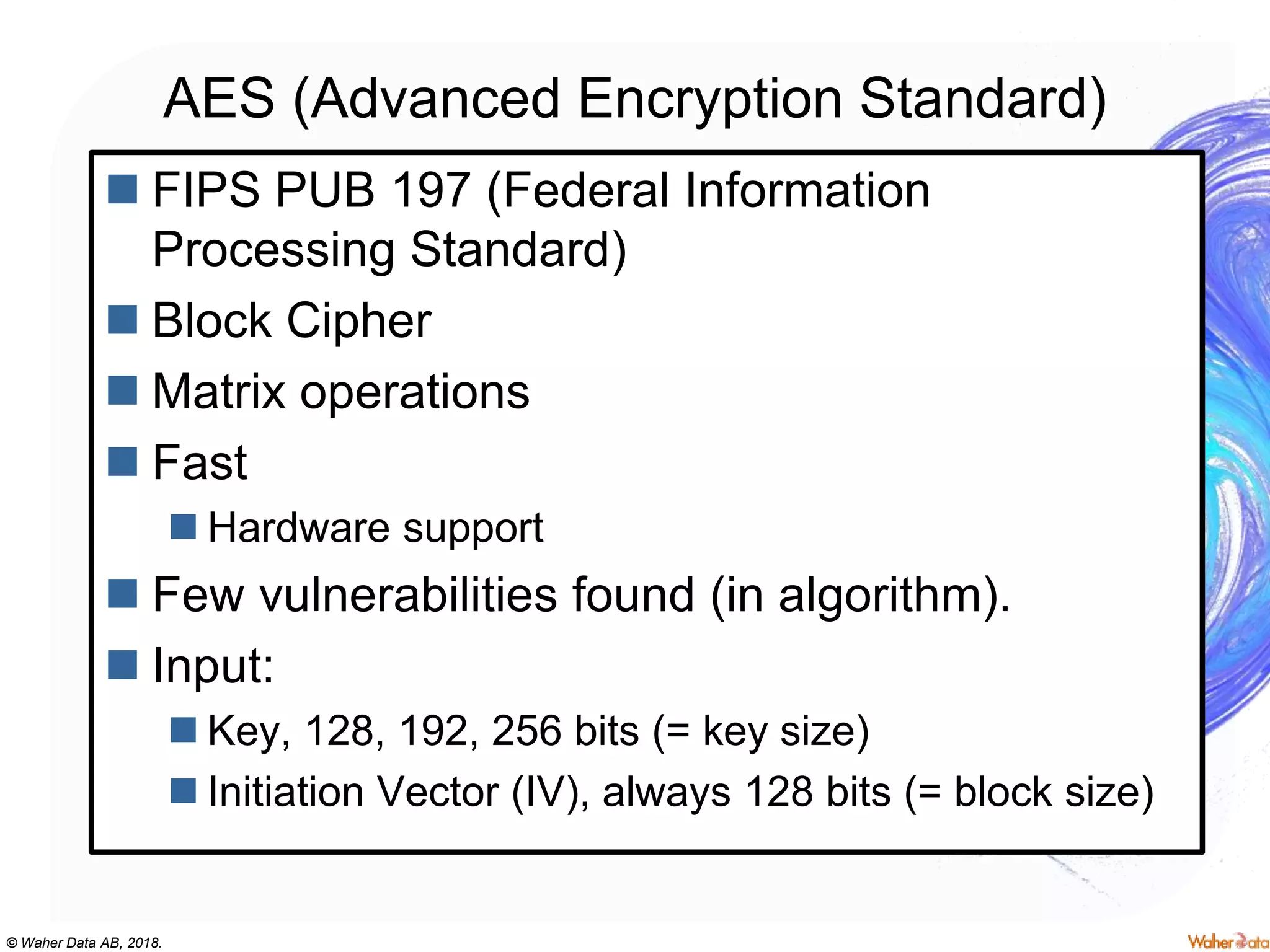
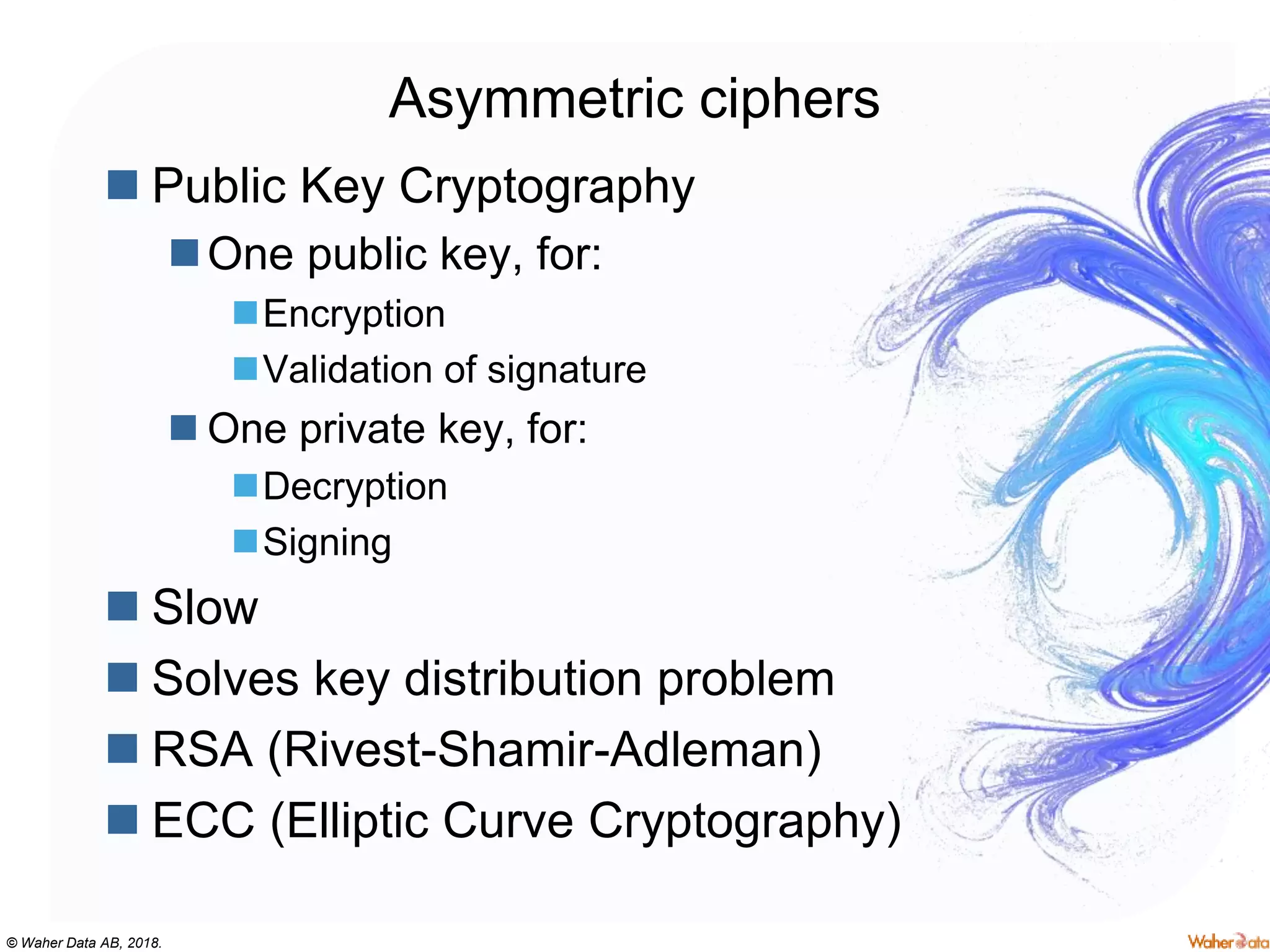
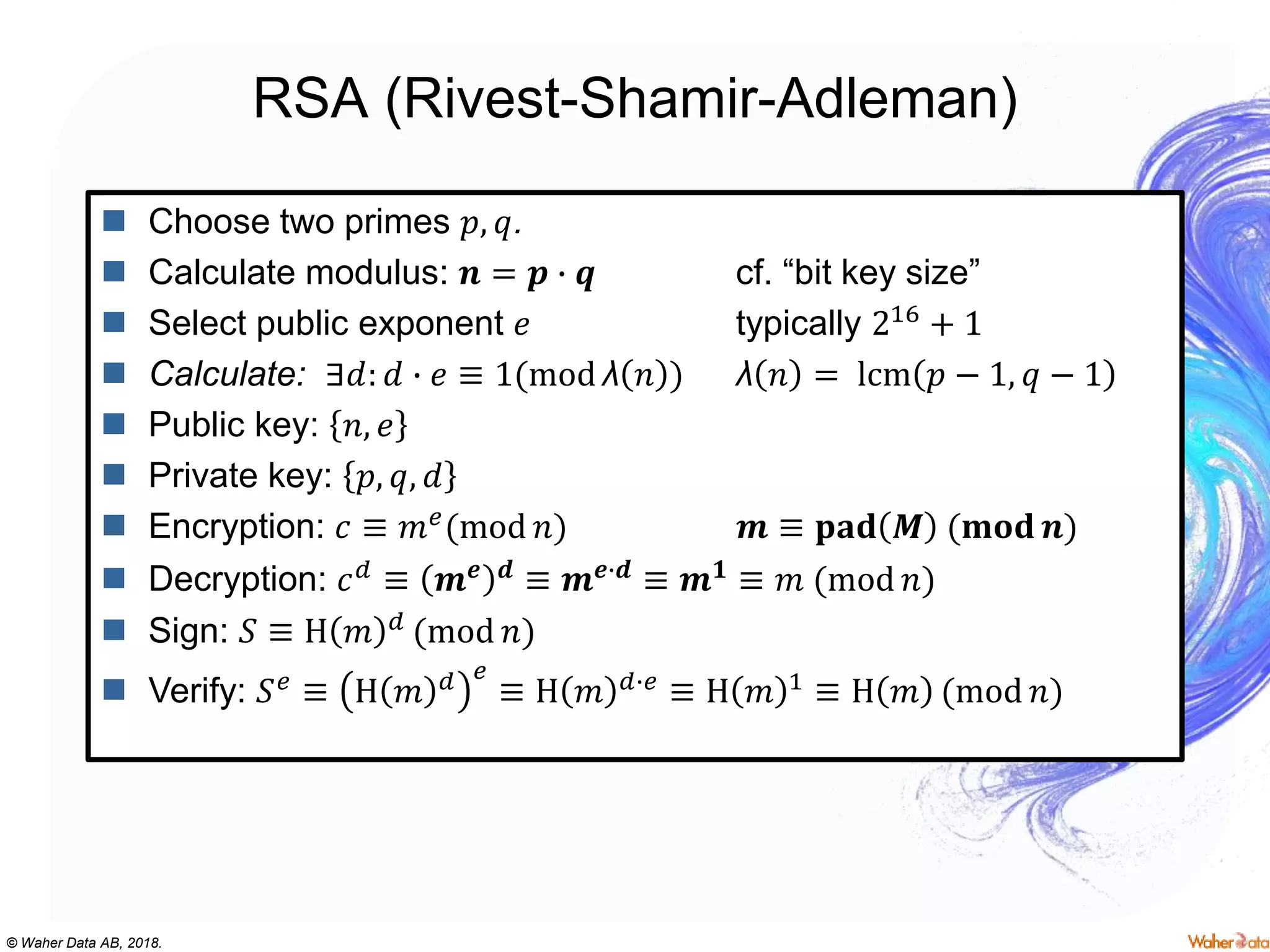
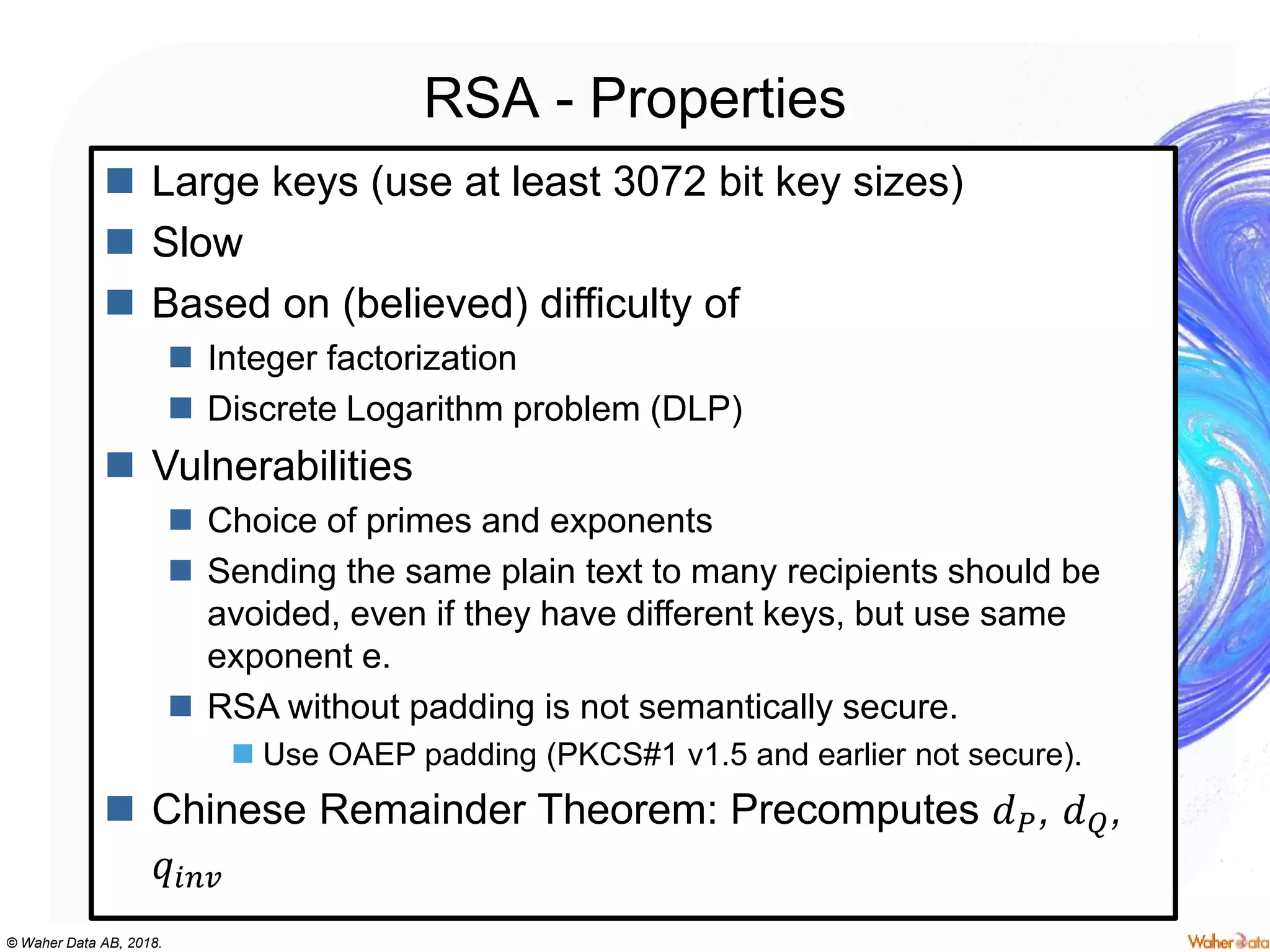
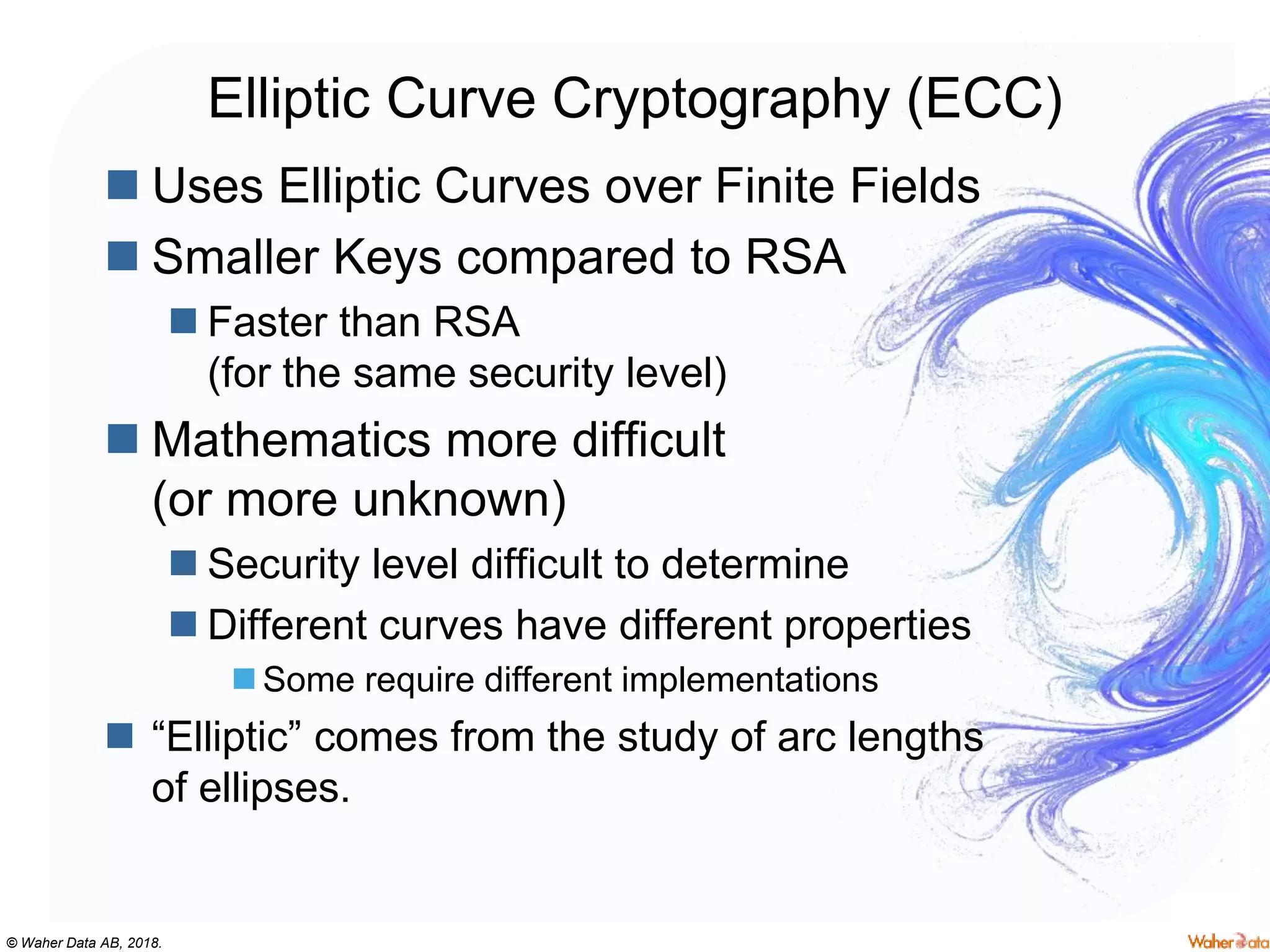
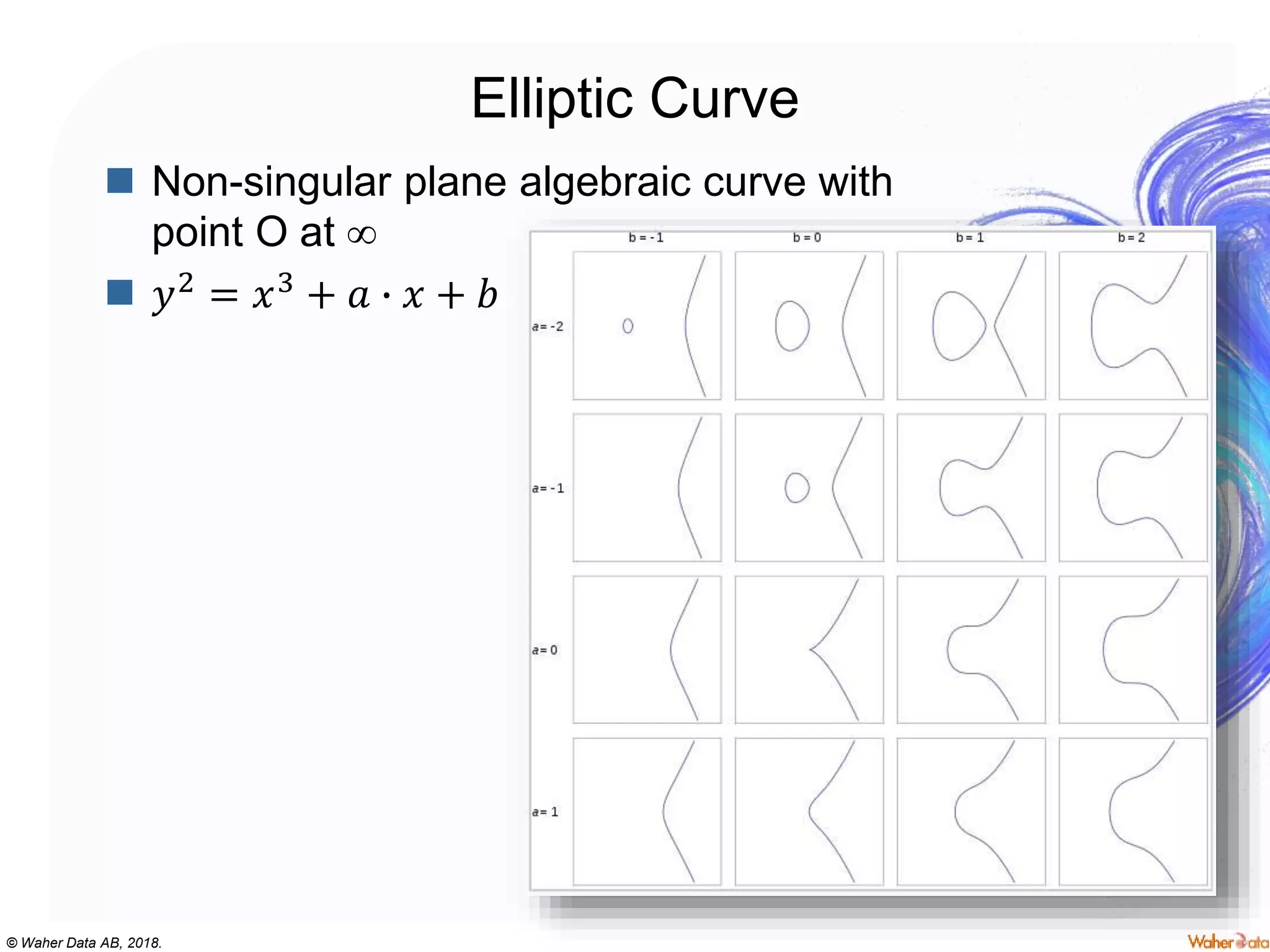
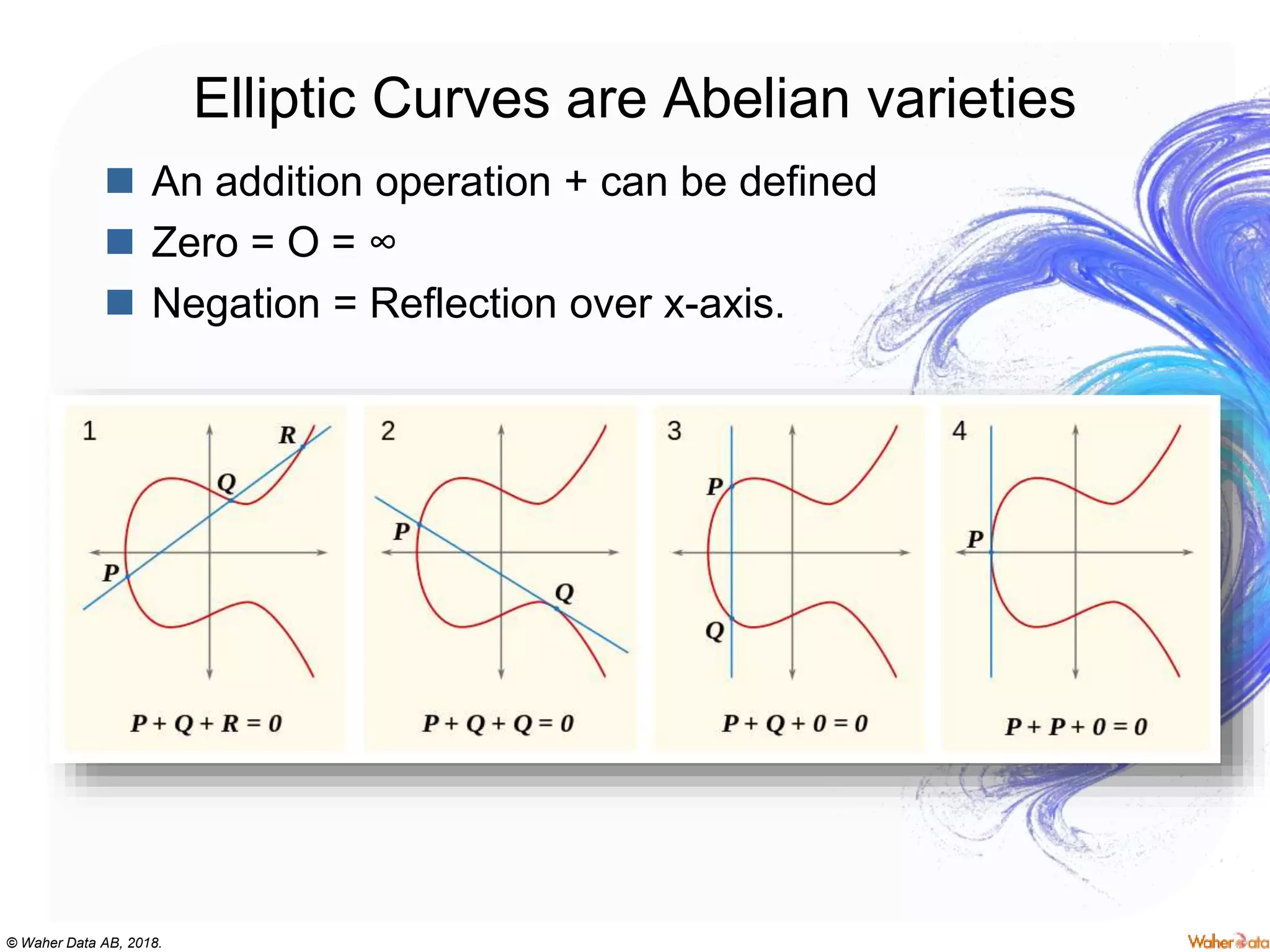
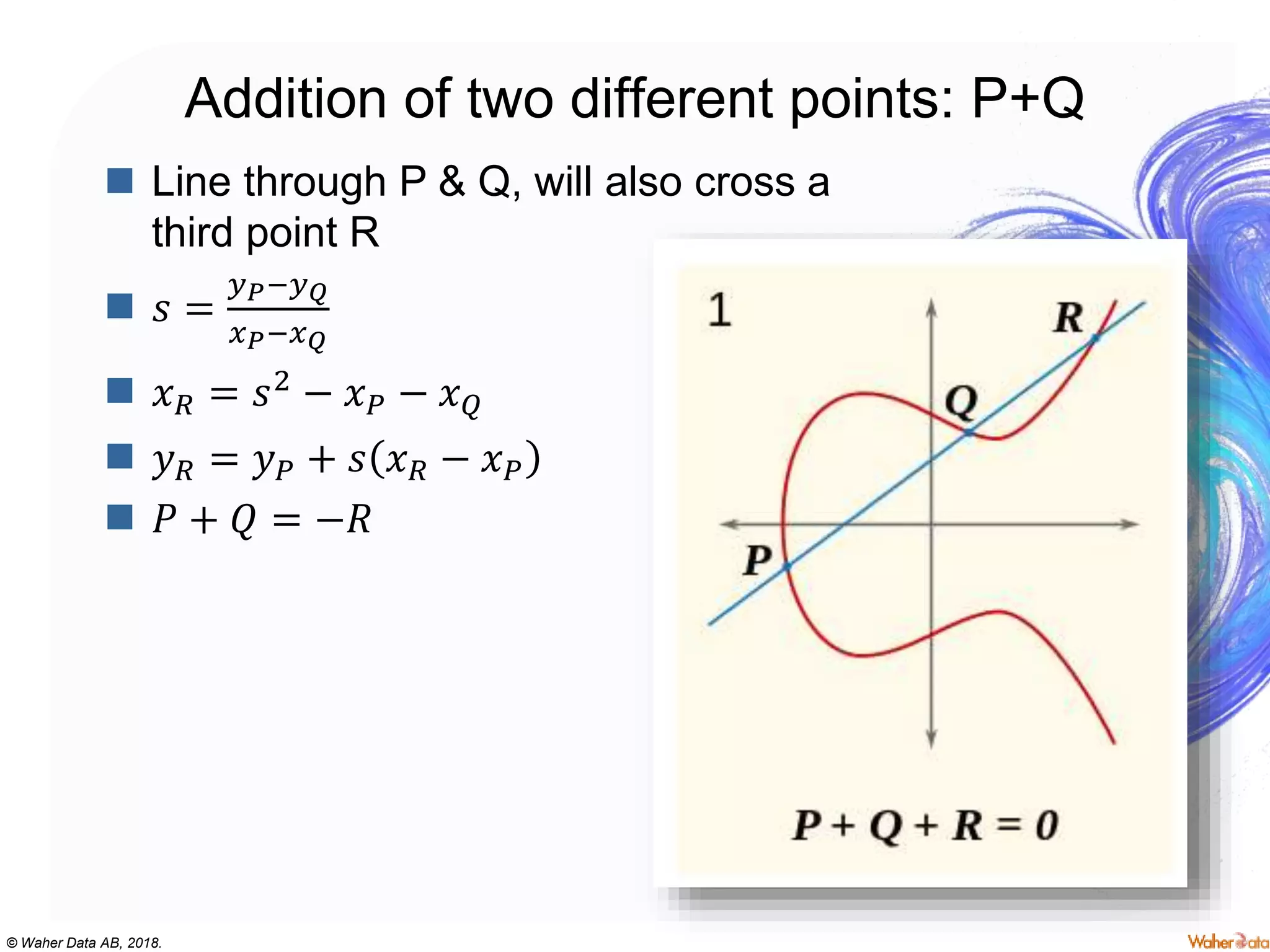
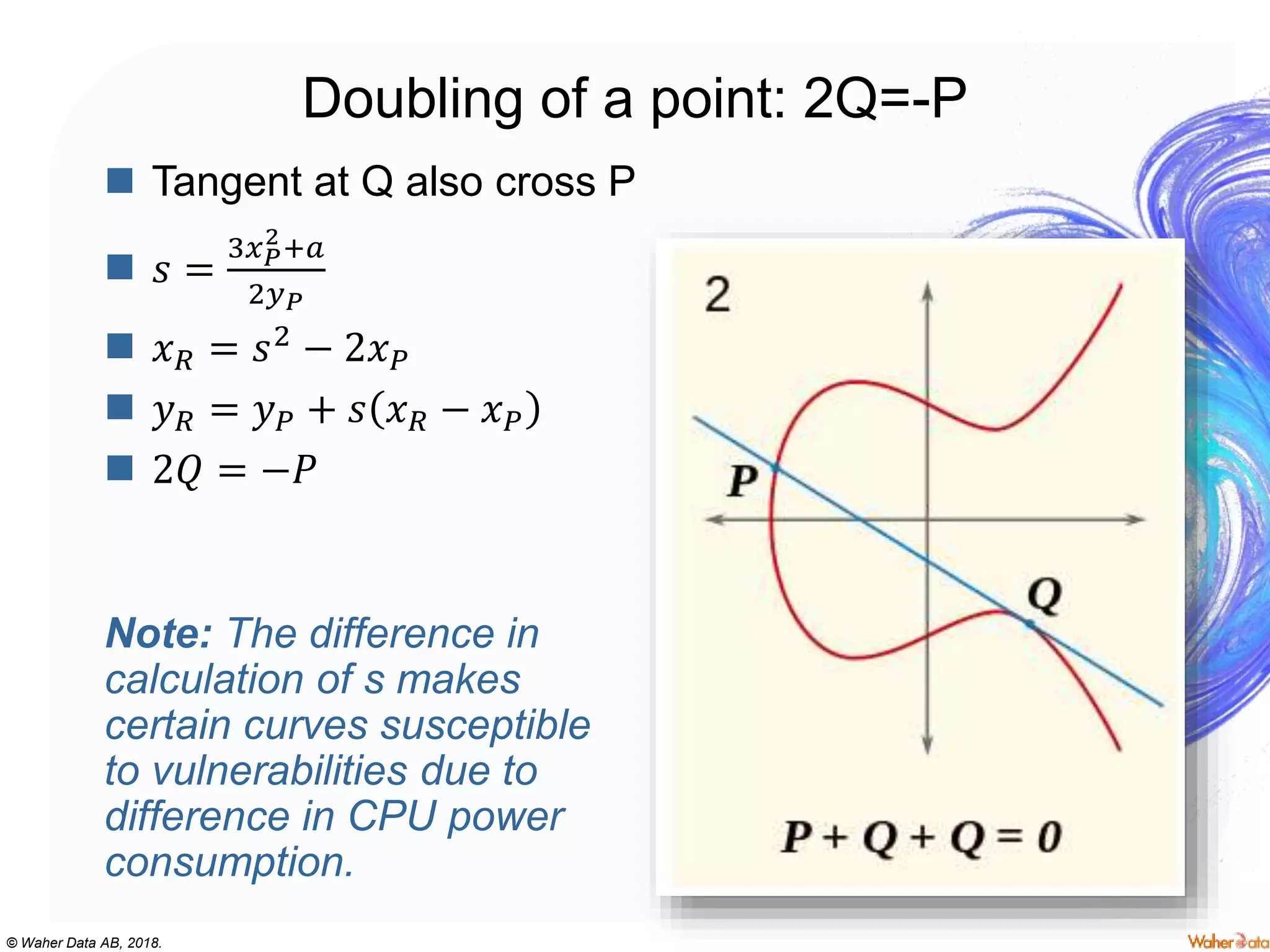
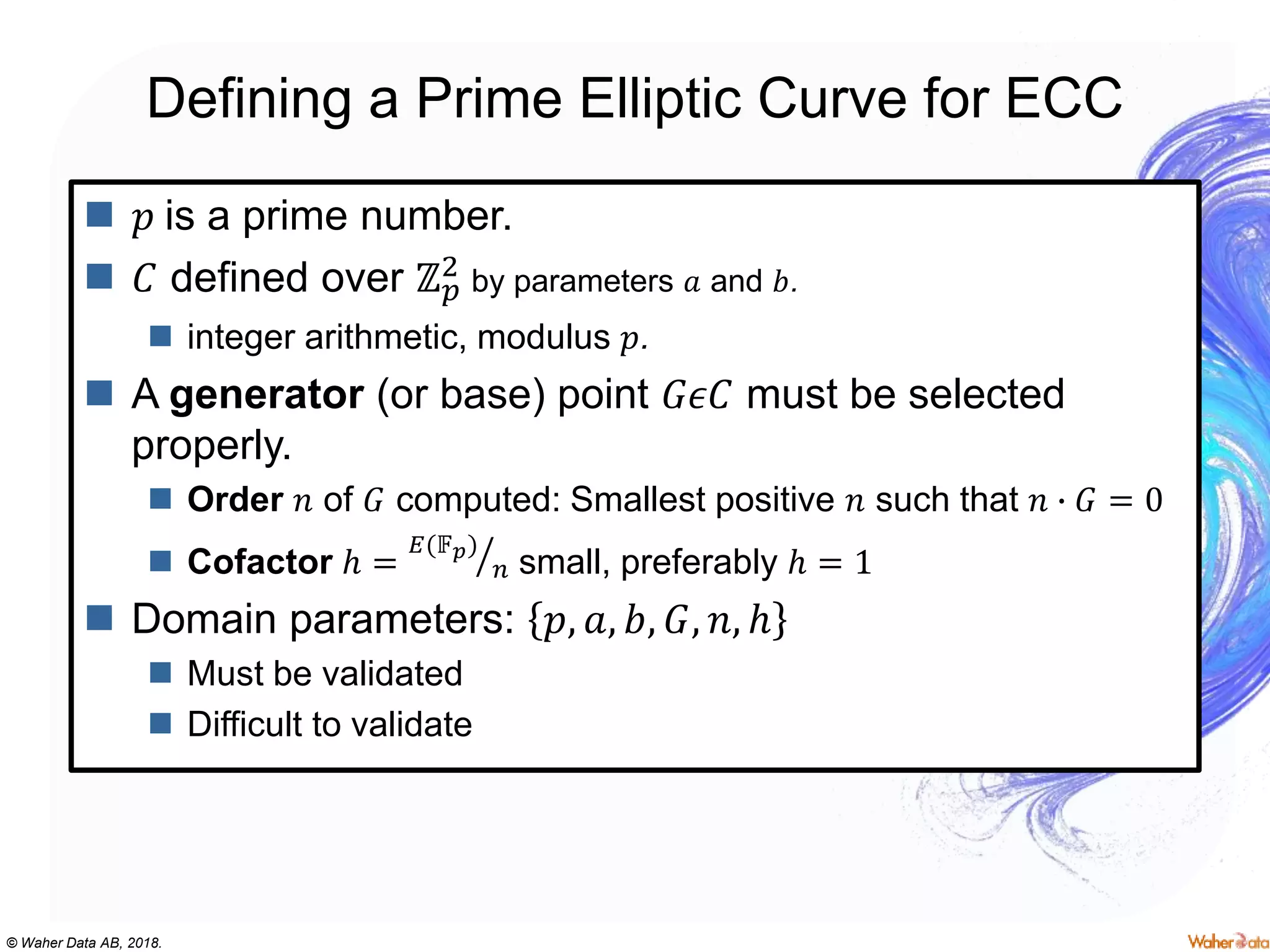
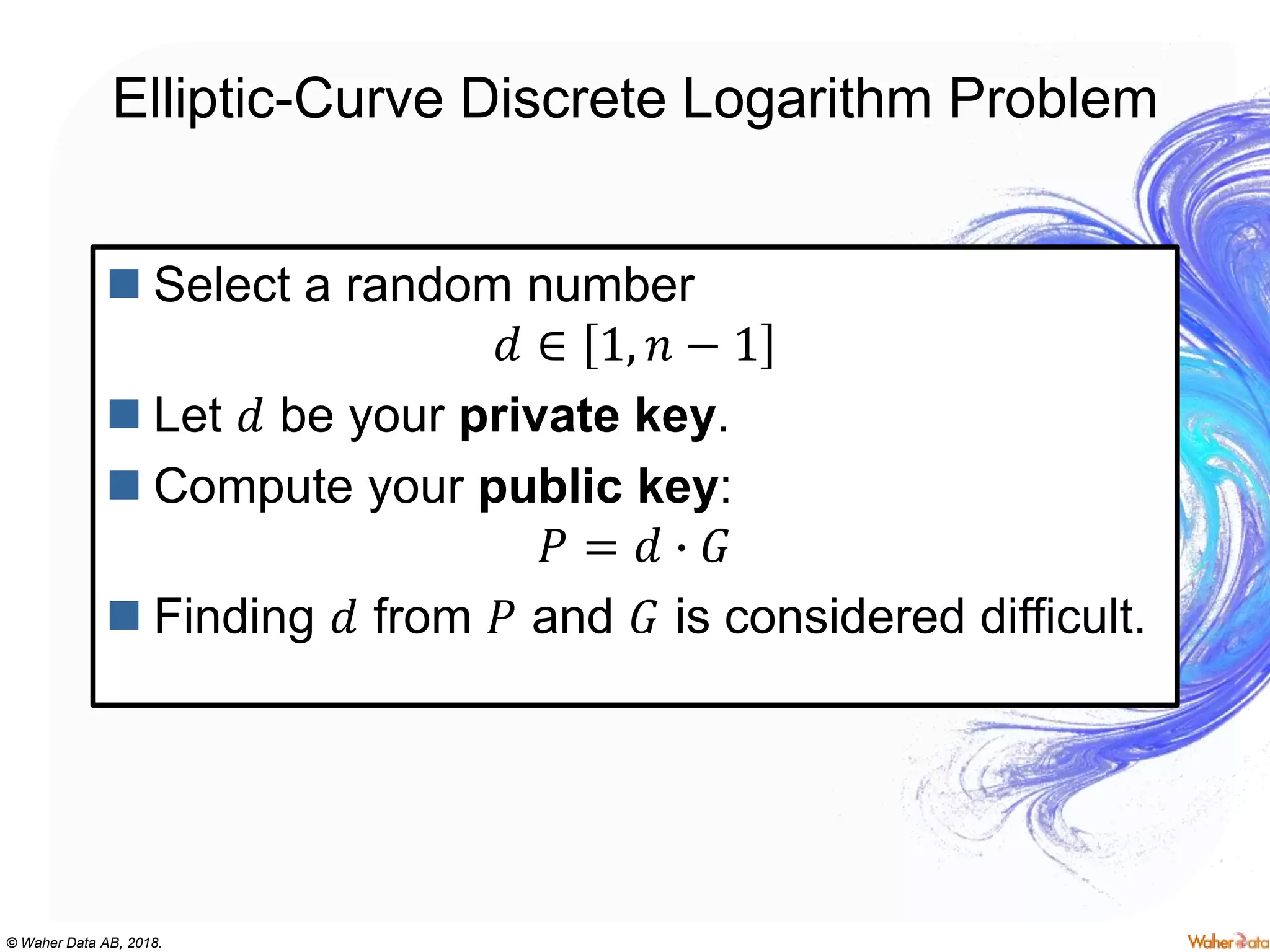
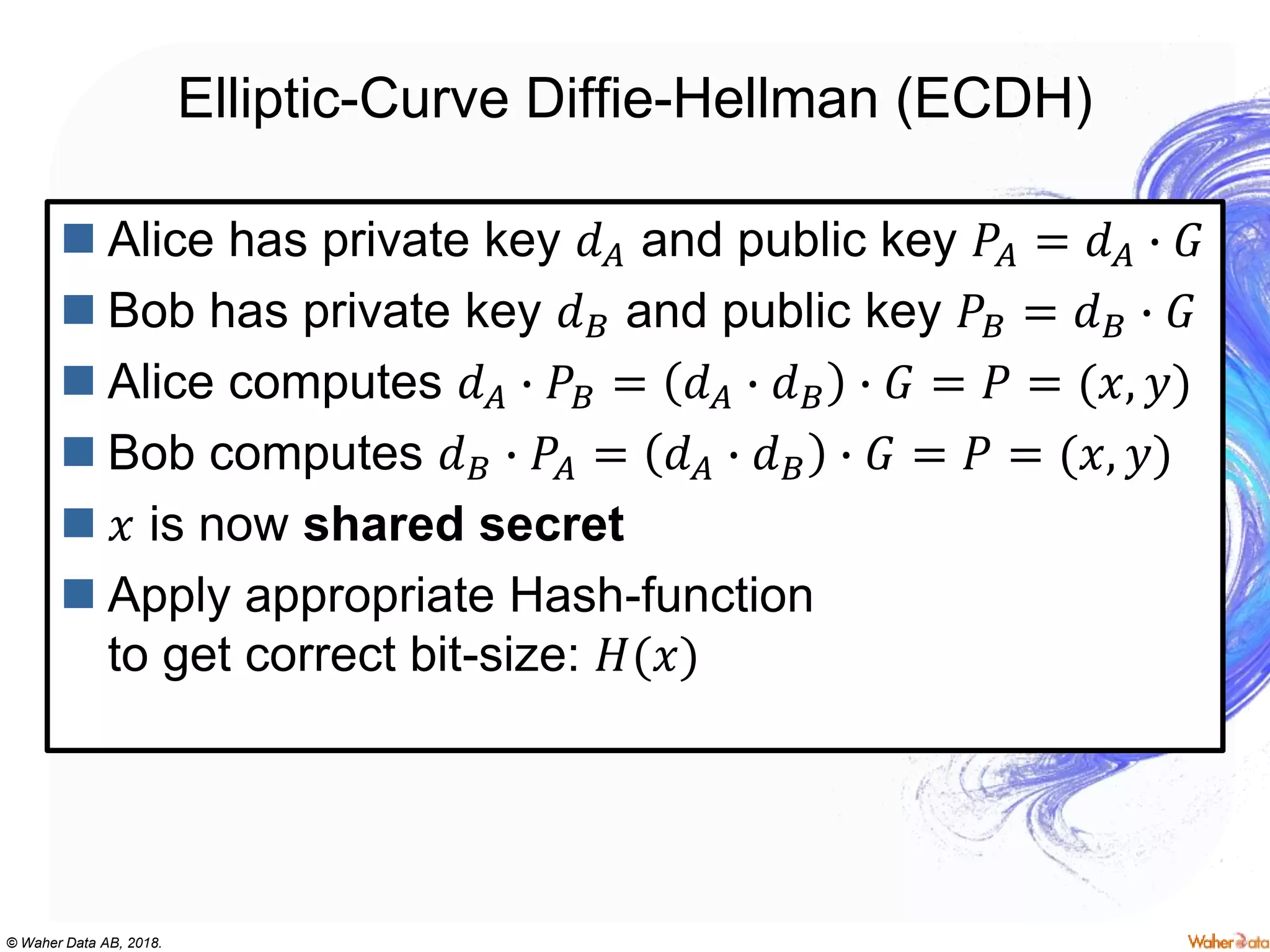
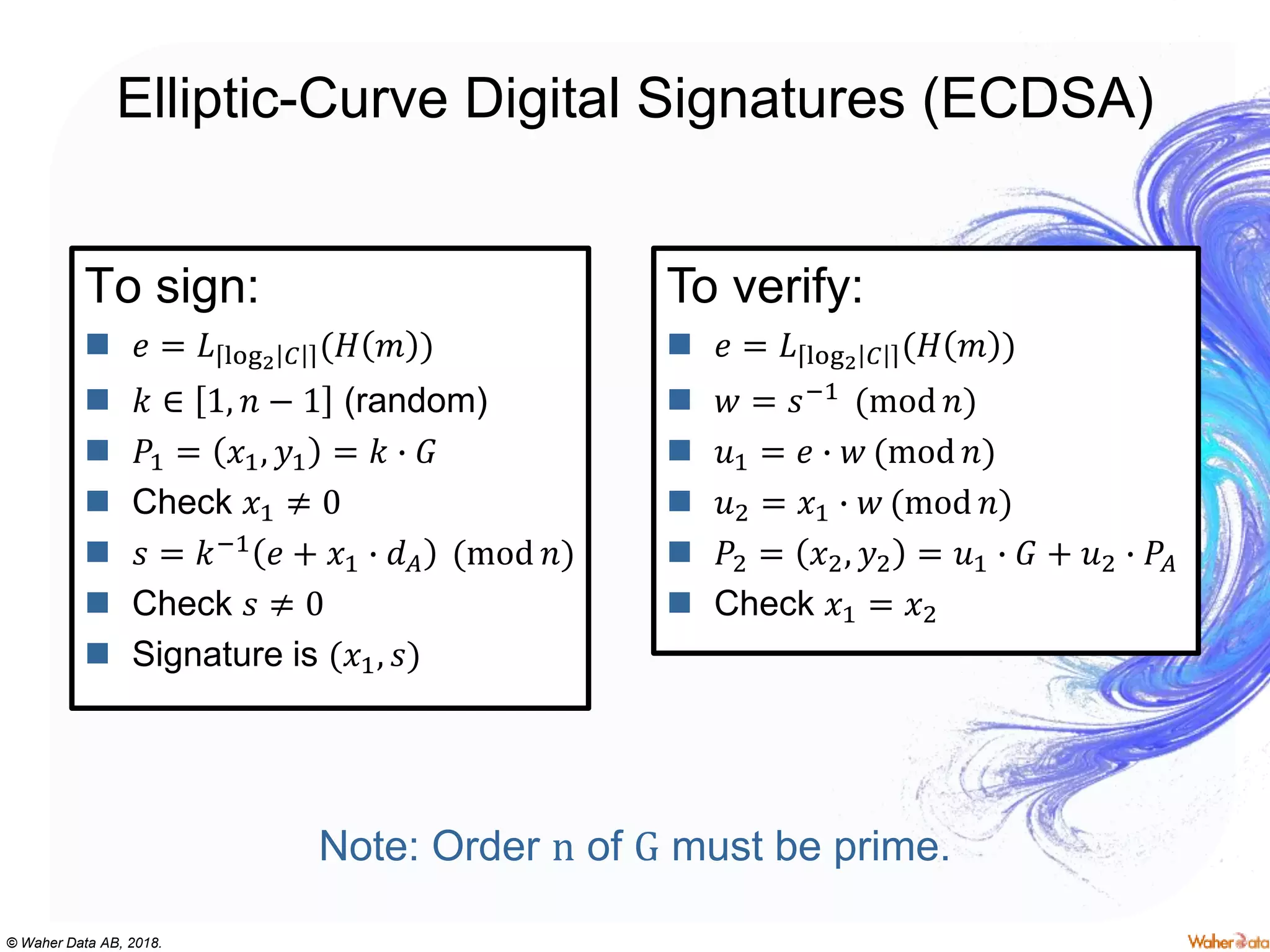
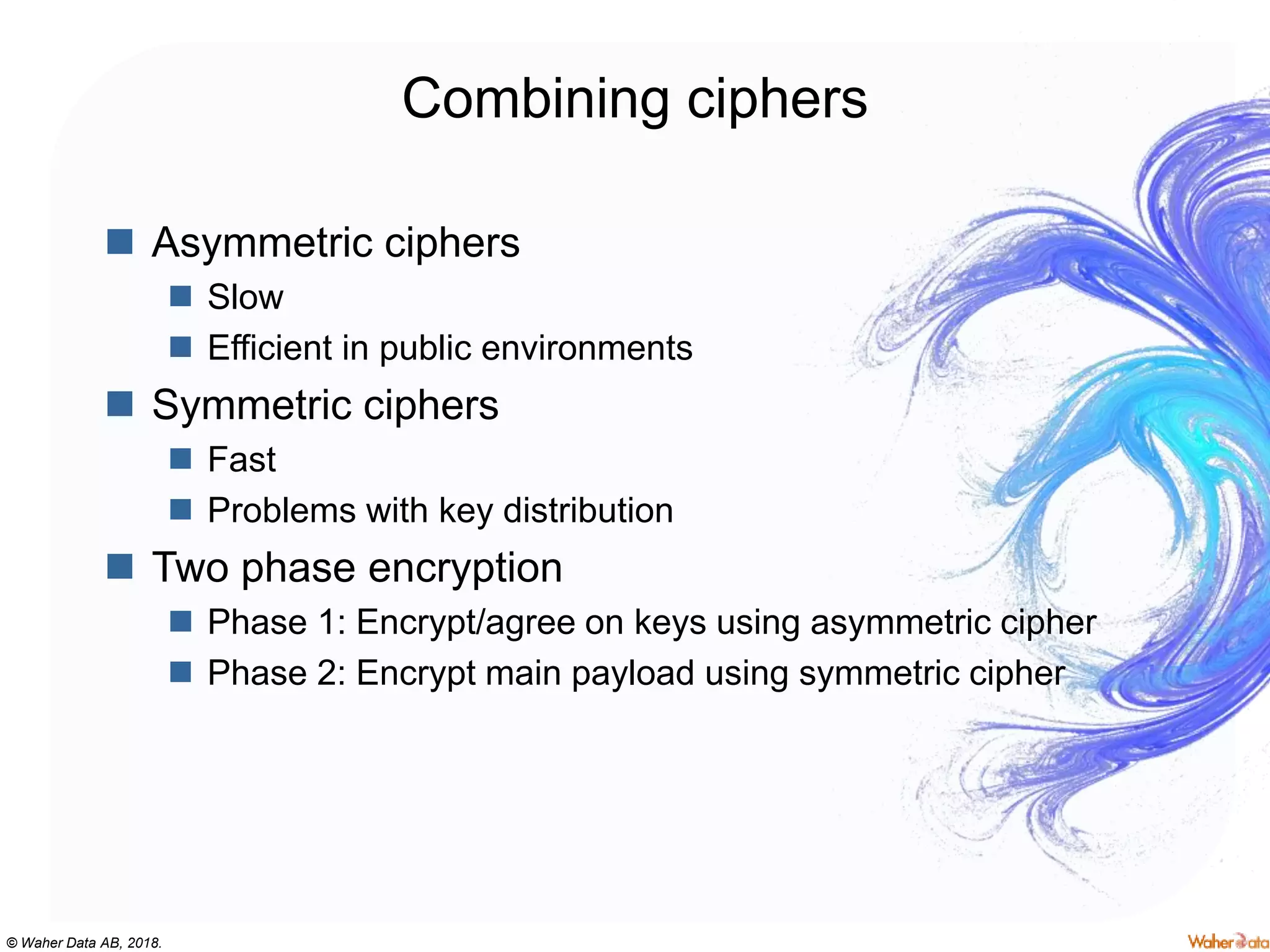
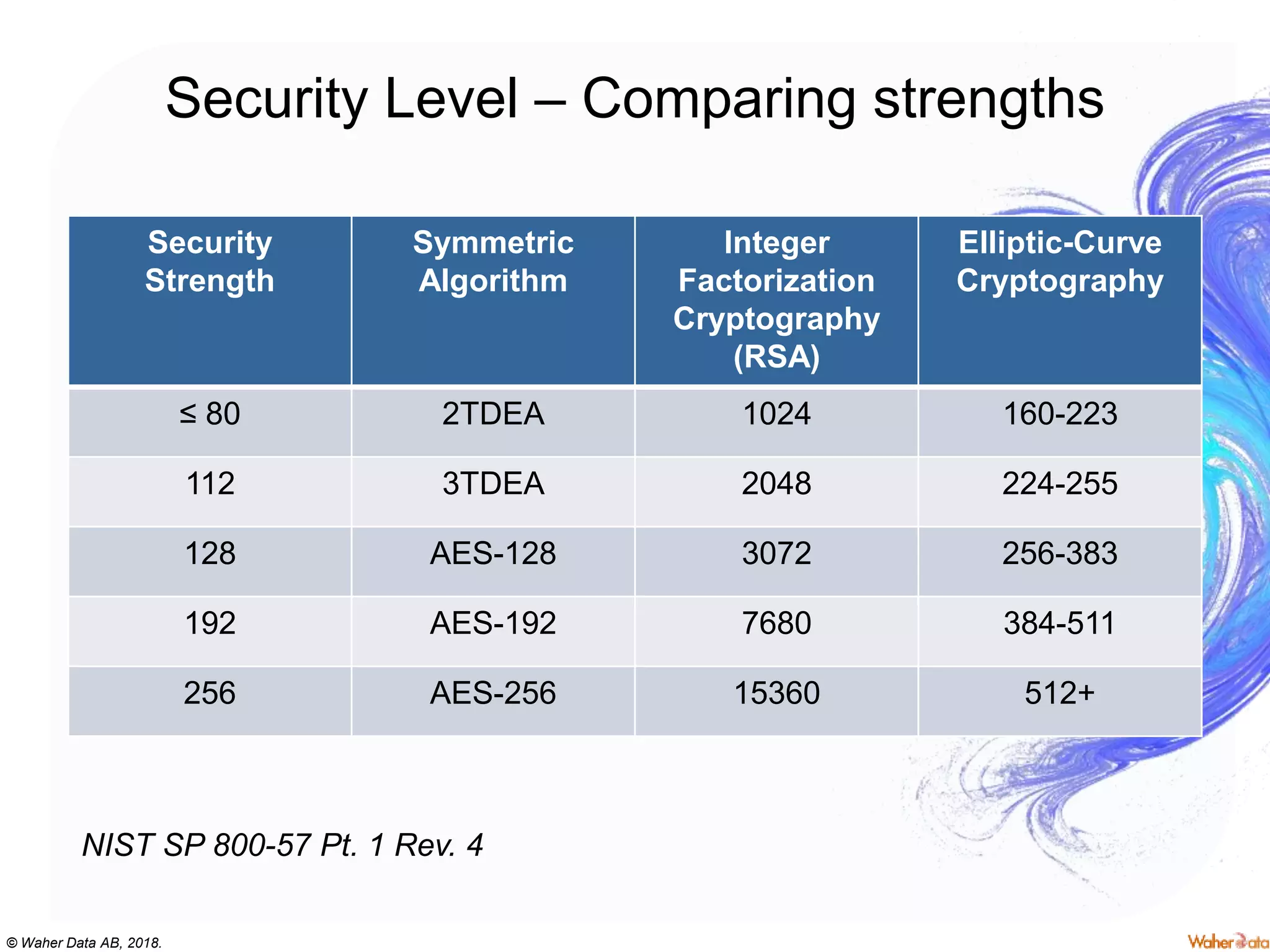
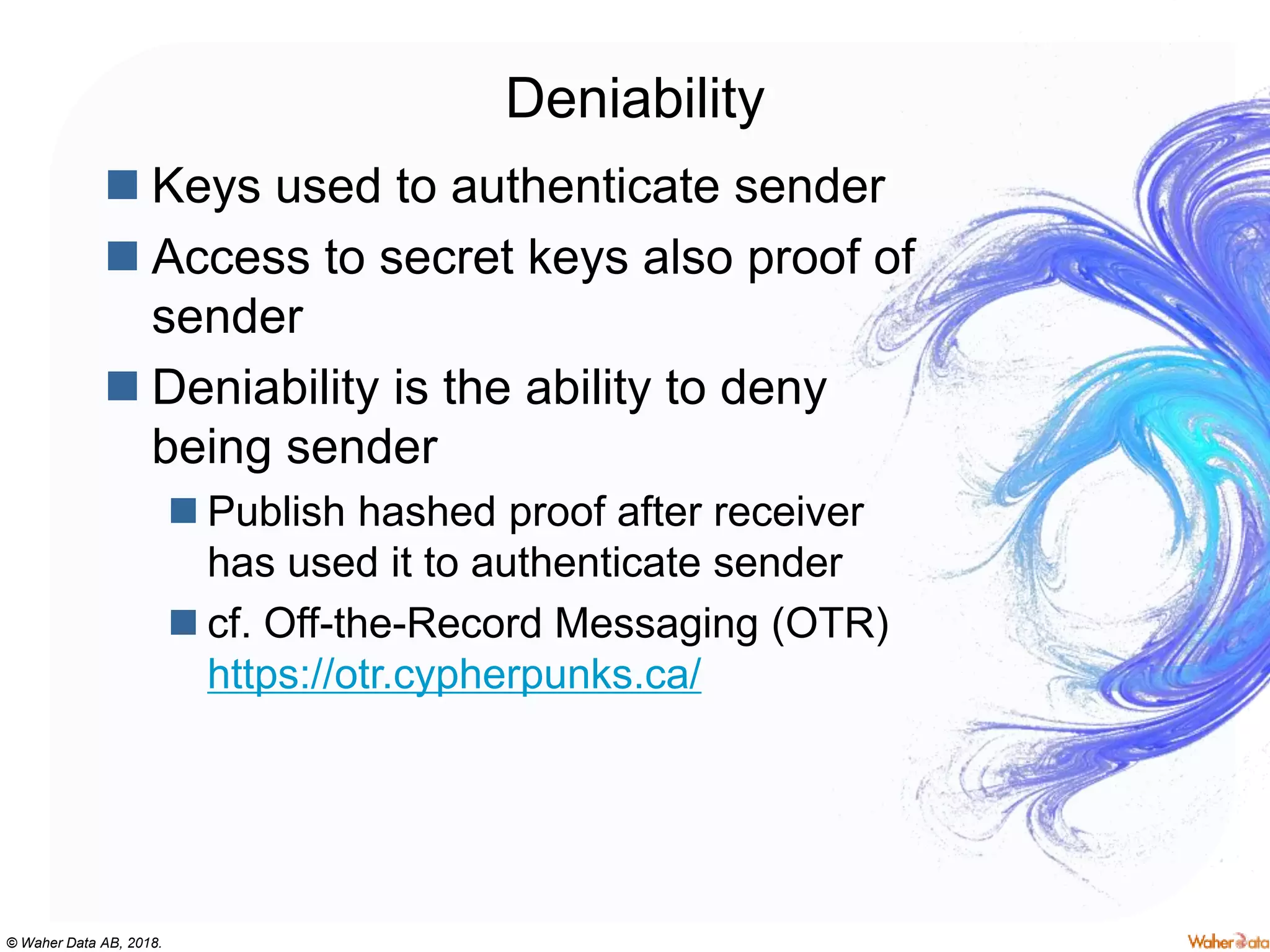
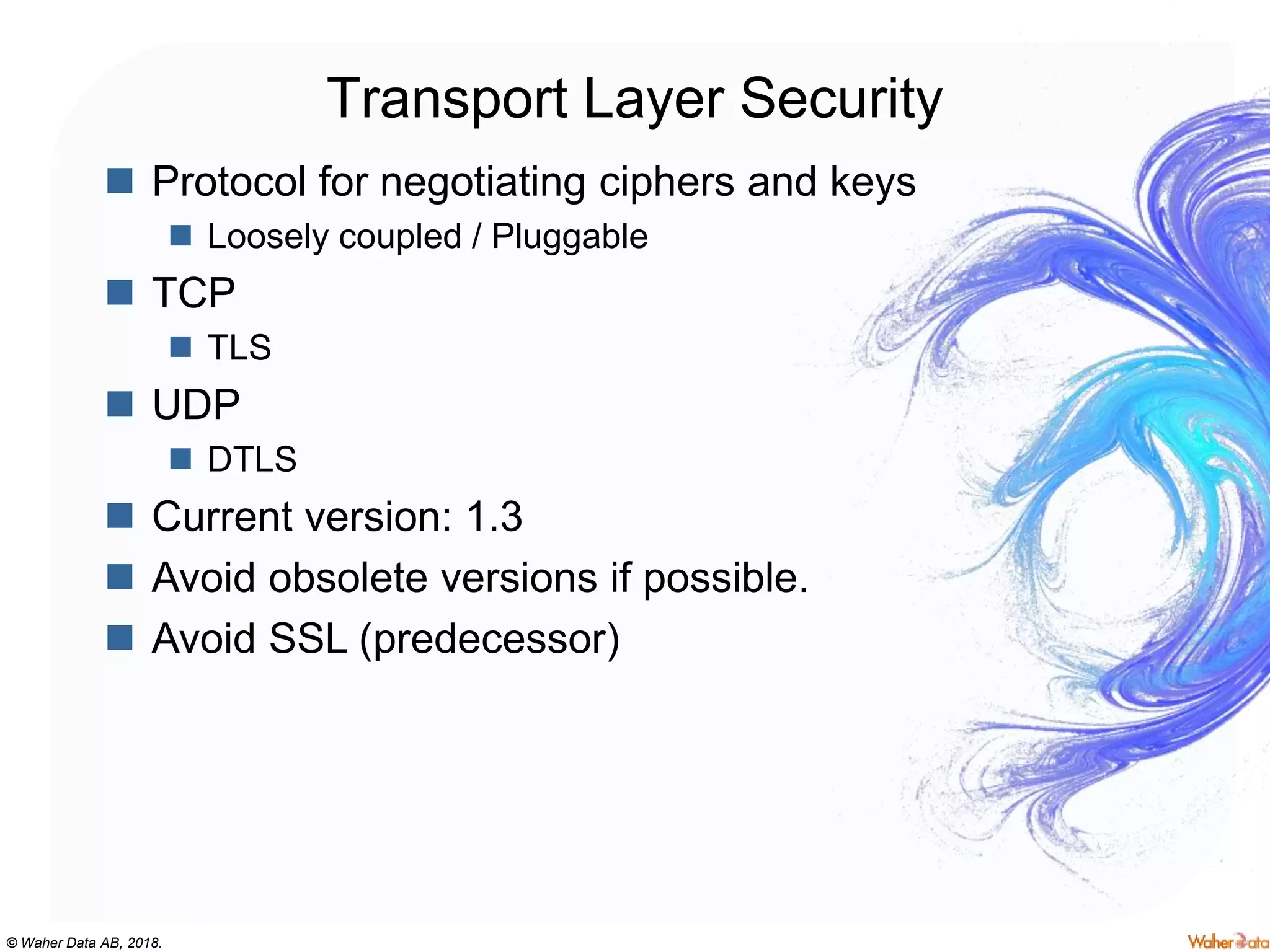
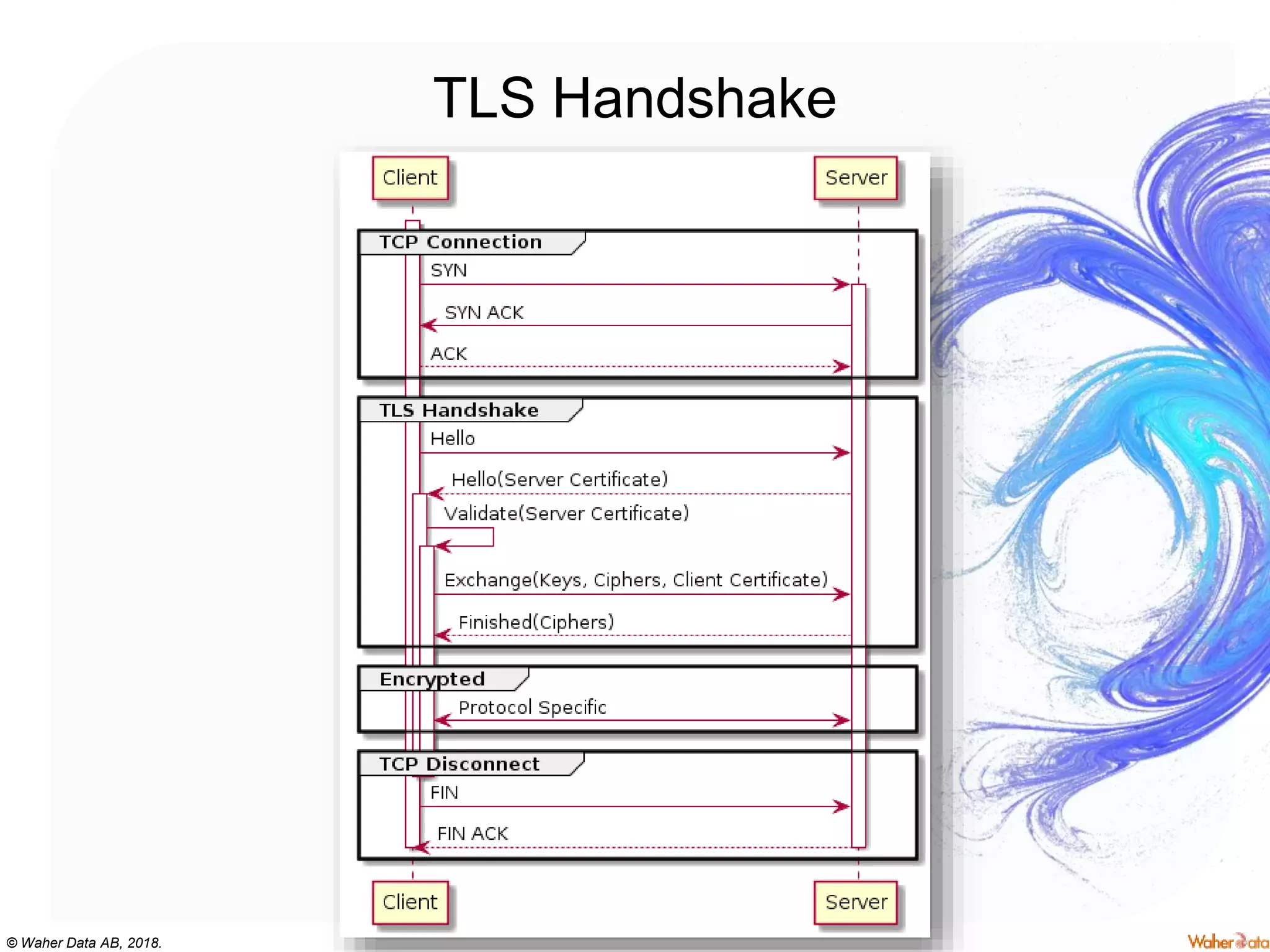
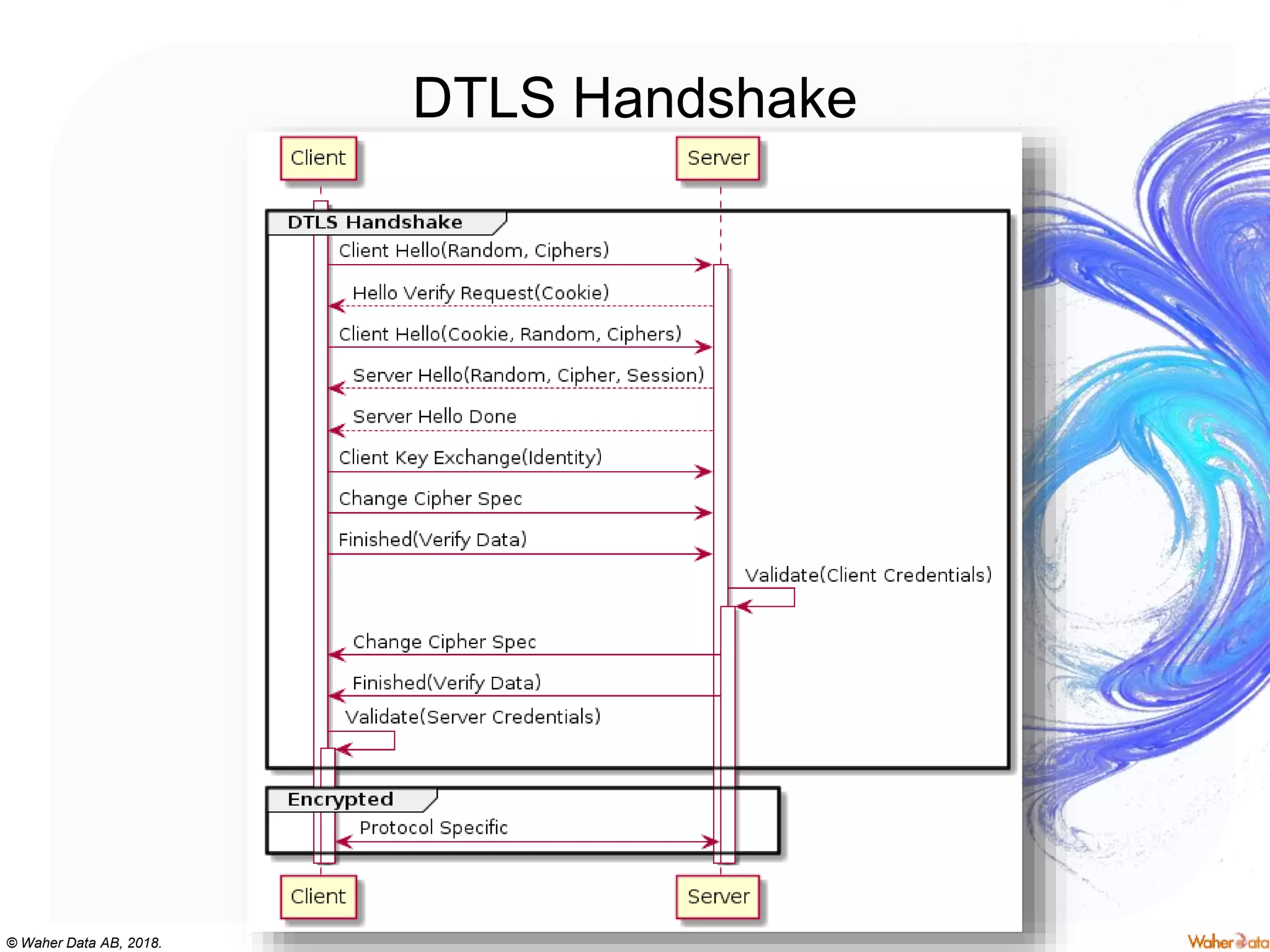
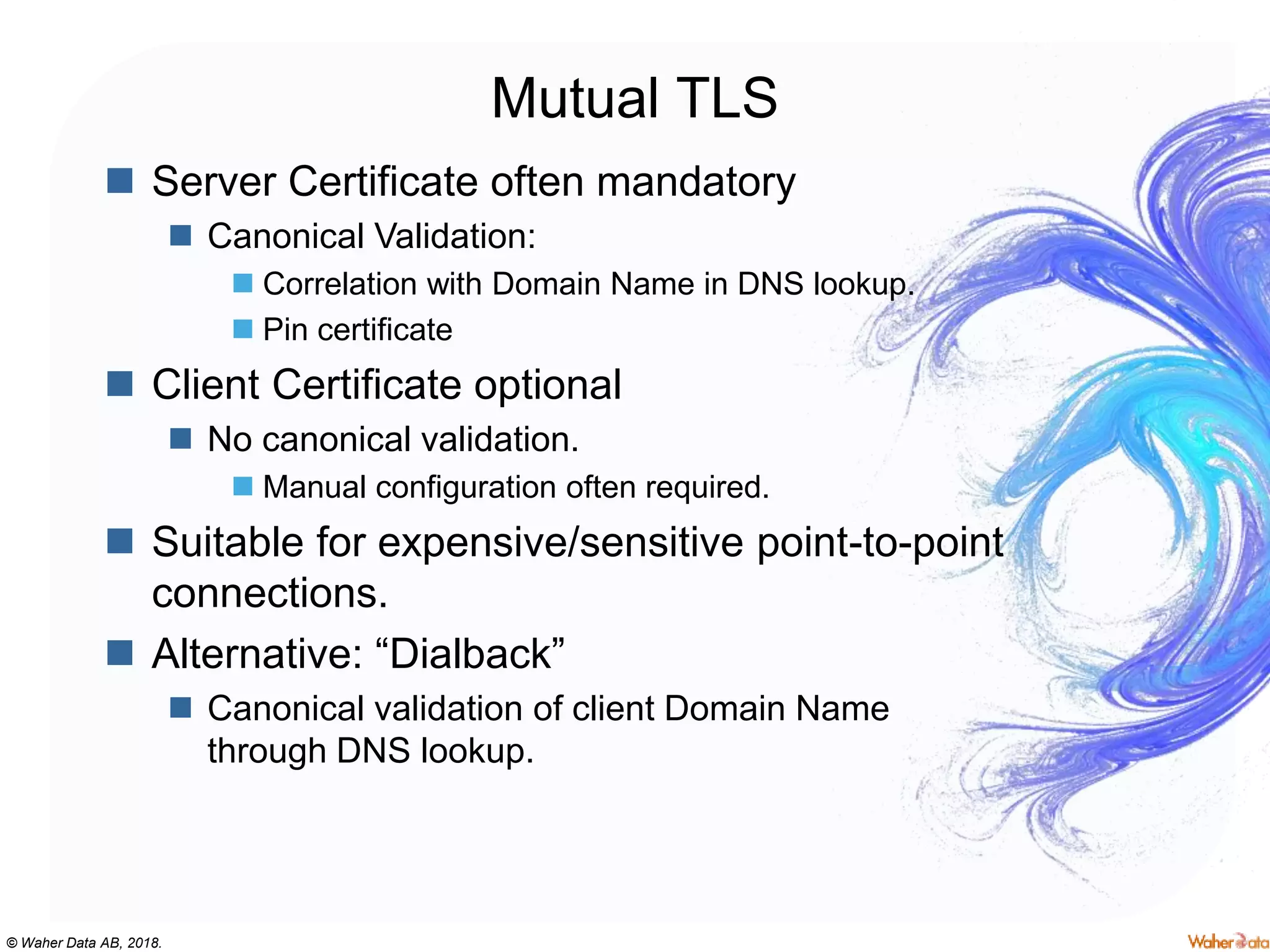
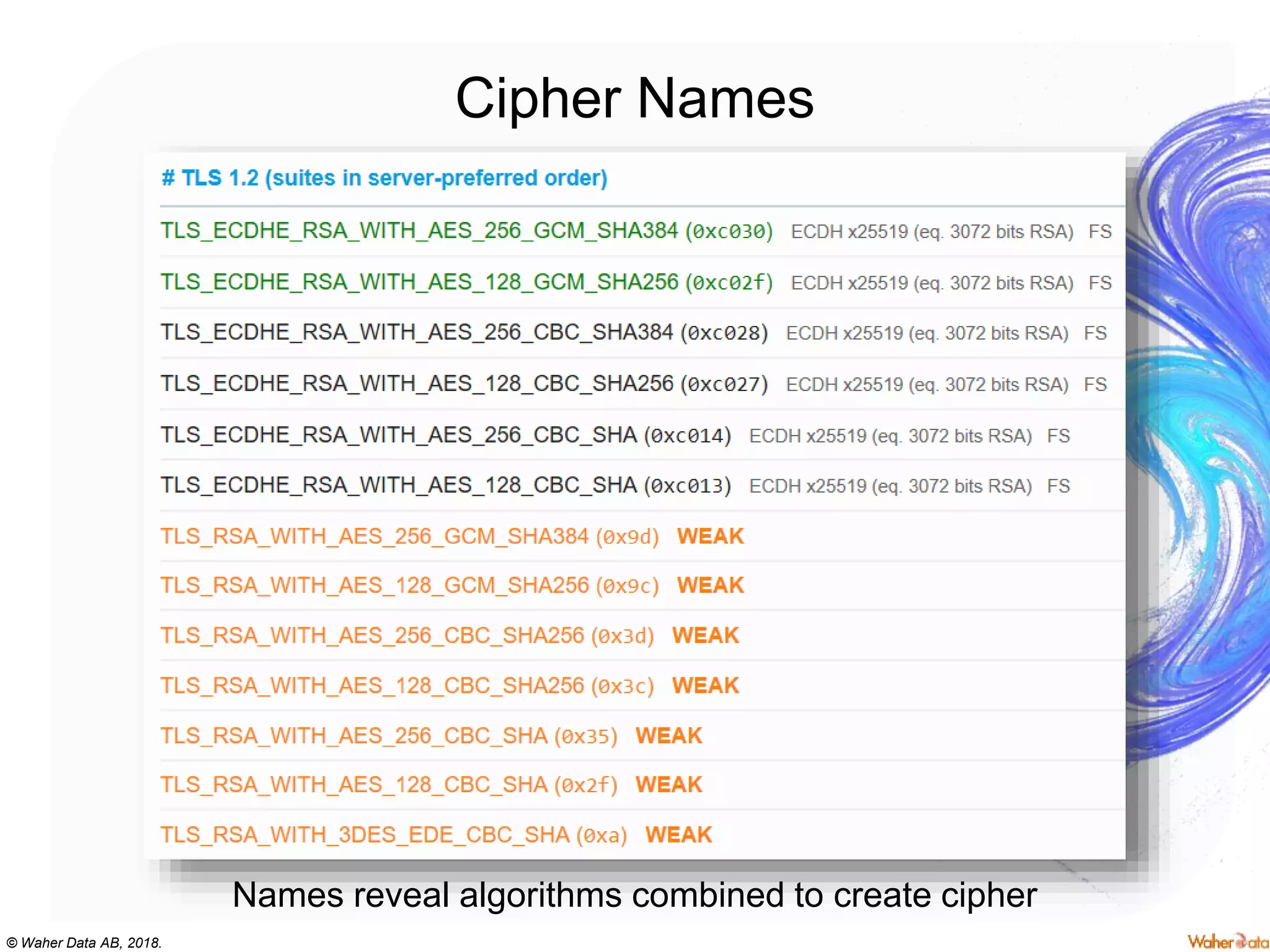
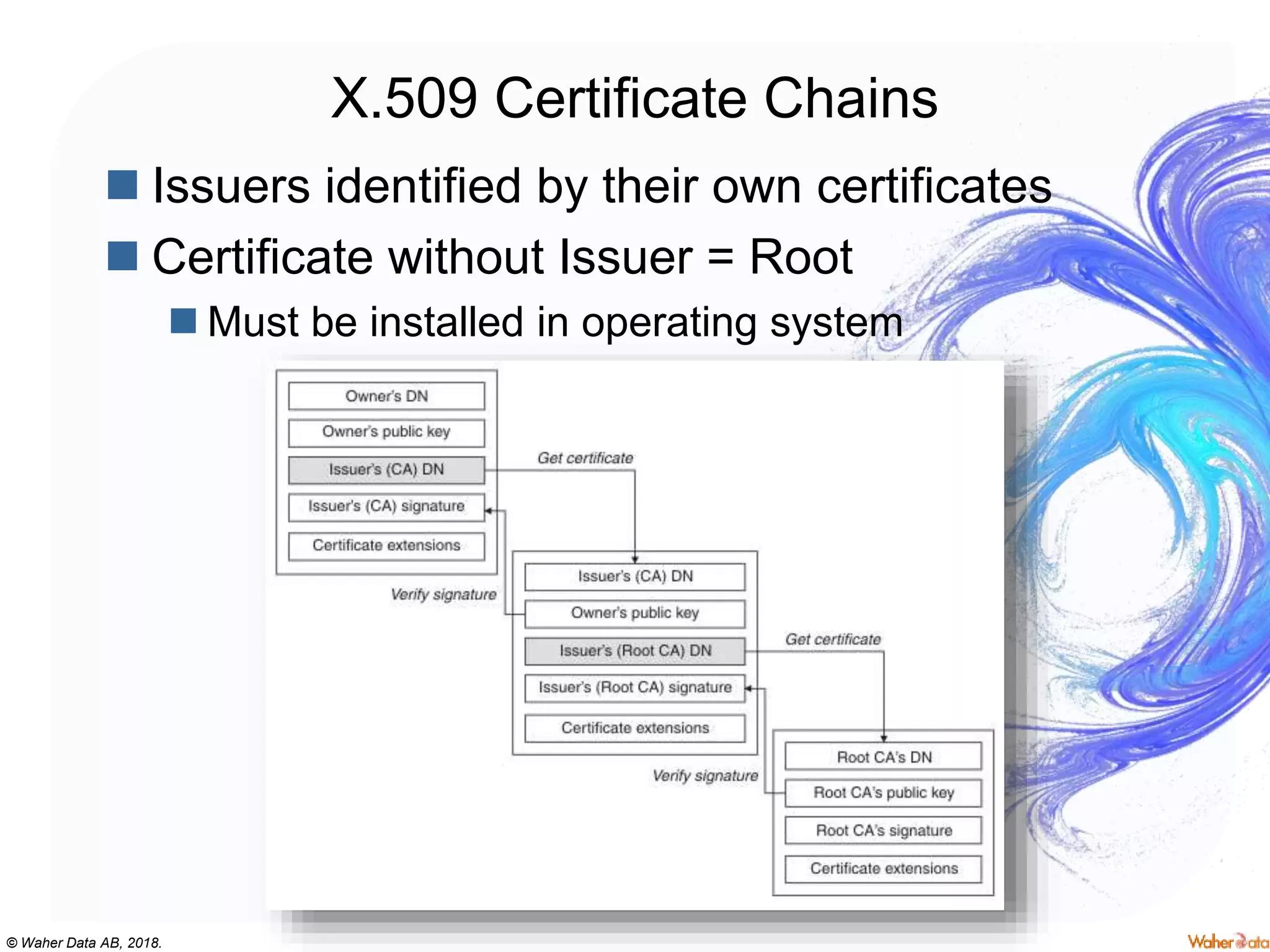
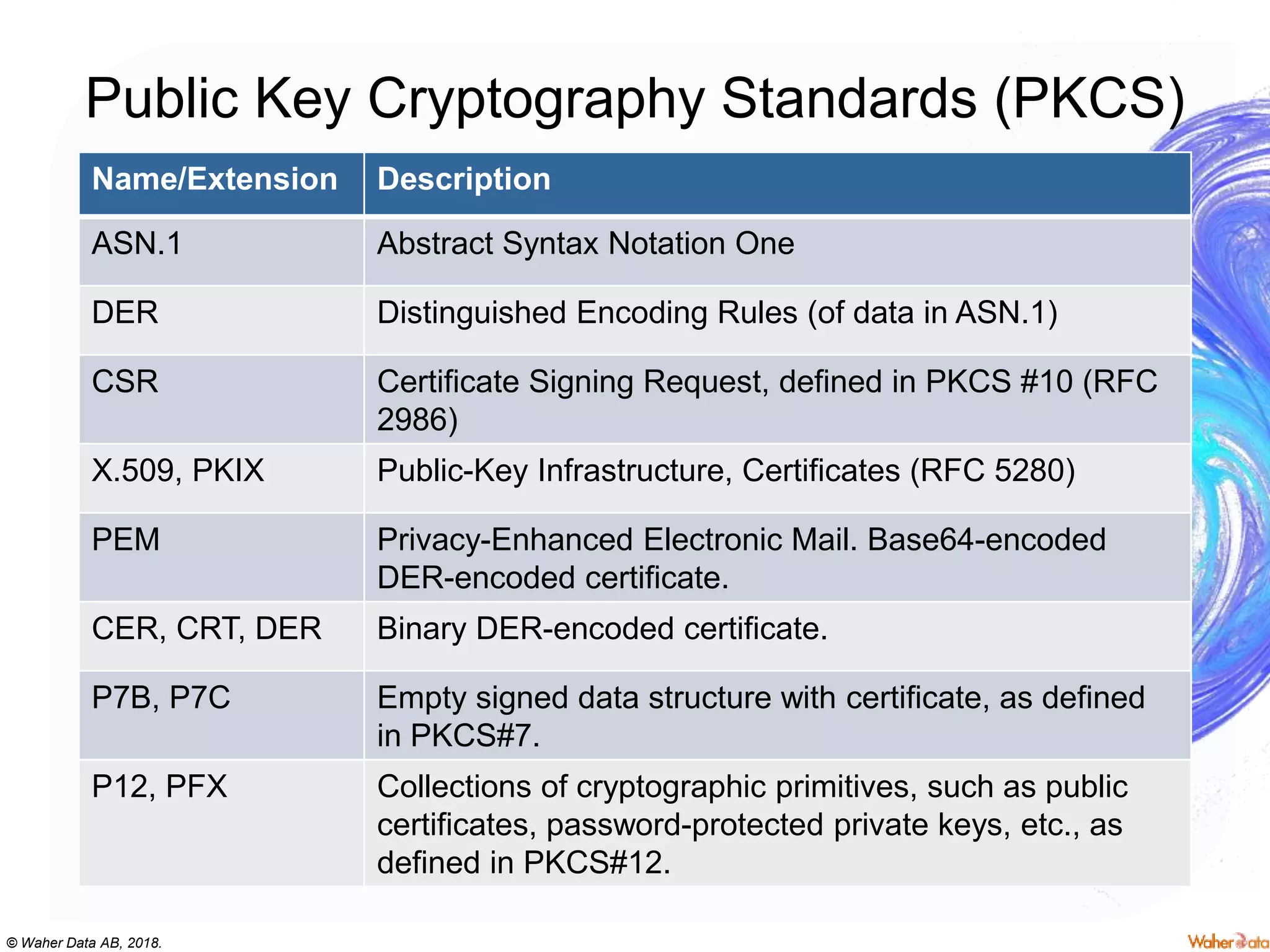
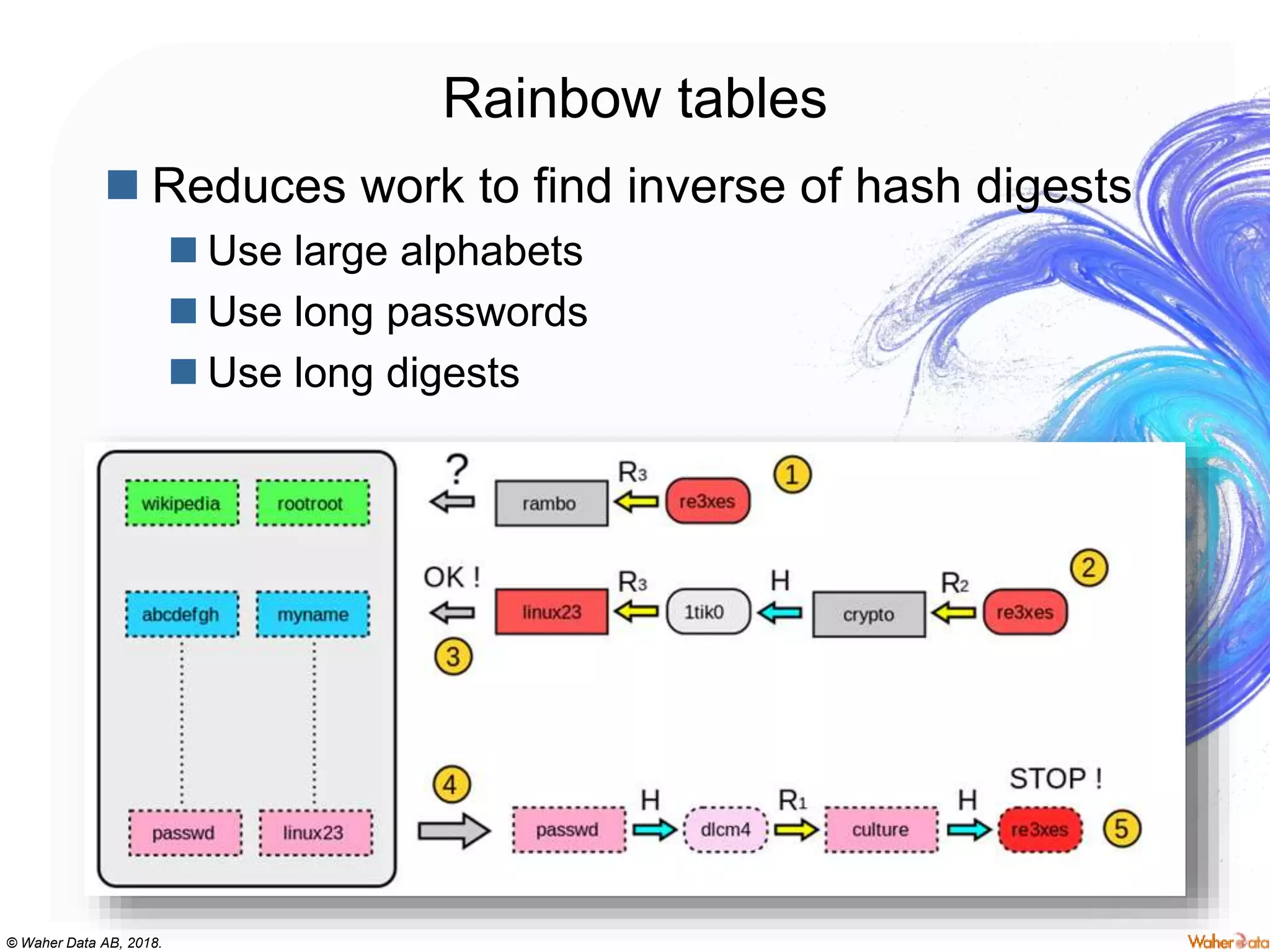
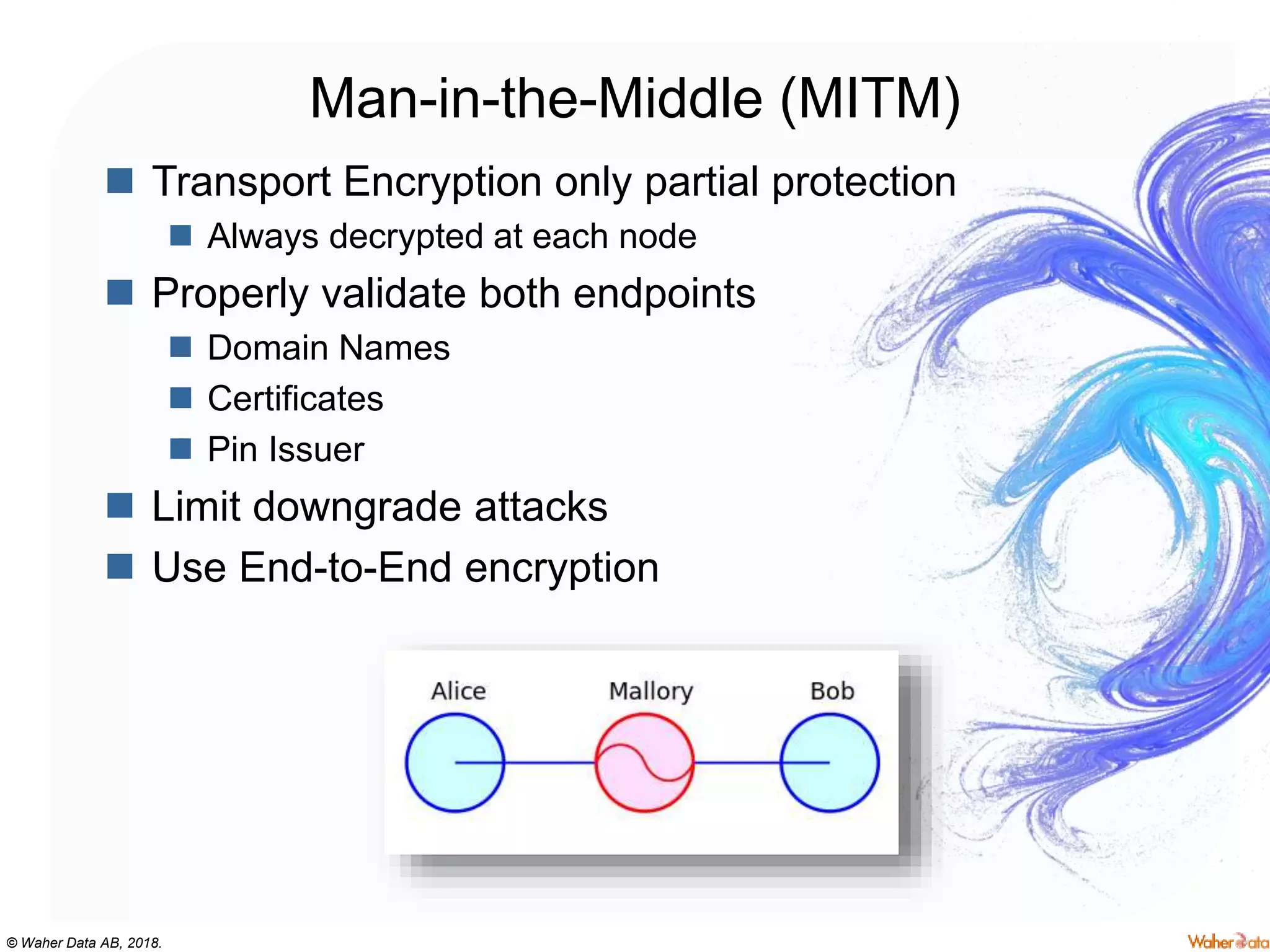
The document provides an extensive overview of cryptography, covering concepts such as symmetric and asymmetric ciphers, hash functions, and their applications in securing communications. It discusses both historic and modern methods, detailing cryptographic operations, random number generation, and the significance of various encryption standards like AES and RSA. Additionally, it highlights key features of Transport Layer Security (TLS) and emphasizes the importance of security protocols in ensuring data integrity and confidentiality.